nginx利用ModSecurity构建WAF环境
- 发表评论
- 4,918
- A+
所属分类:WEB应用
官网:http://modsecurity.org/download.html
owasp-modsecurity-crs:https://github.com/SpiderLabs/owasp-modsecurity-crs.git
OWASP是一个安全社区,开发和维护着一套免费的应用程序保护规则,这就是所谓OWASP的ModSecurity的核心规则集(即CRS)
安装:nginx之前已经安装过,这里直接添加模块
modsecurity安装:
Shell
cd /usr/local/ wget https://www.modsecurity.org/tarball/2.9.2/modsecurity-2.9.2.tar.gz tar -xf modsecurity-2.9.2.tar.gz cd modsecurity-2.9.2 yum install -y httpd-devel ./configure --enable-standalone-module --disable-mlogc make
1234567 | cd /usr/local/wget https://www.modsecurity.org/tarball/2.9.2/modsecurity-2.9.2.tar.gztar -xf modsecurity-2.9.2.tar.gz cd modsecurity-2.9.2yum install -y httpd-devel./configure --enable-standalone-module --disable-mlogcmake |
|---|
nginx添加模块,先查看以前参数
Shell
cd /usr/local/src/ &&wget http://nginx.org/download/nginx-1.12.2.tar.gz ./configure --user=www --group=www --prefix=/usr/local/nginx --with-http_stub_status_module --with-http_ssl_module --with-http_v2_module --with-http_gzip_static_module --with-ipv6 --with-http_sub_module --with-ld-opt=-ljemalloc --add-module=/usr/local/modsecurity-2.9.2/nginx/modsecurity/ make mv /usr/local/nginx/sbin/nginx /usr/local/nginx/sbin/nginx.old cp -rf objs/nginx /usr/local/nginx/sbin/ make upgrade
123456 | cd /usr/local/src/ &&wget http://nginx.org/download/nginx-1.12.2.tar.gz./configure --user=www --group=www --prefix=/usr/local/nginx --with-http_stub_status_module --with-http_ssl_module --with-http_v2_module --with-http_gzip_static_module --with-ipv6 --with-http_sub_module --with-ld-opt=-ljemalloc --add-module=/usr/local/modsecurity-2.9.2/nginx/modsecurity/makemv /usr/local/nginx/sbin/nginx /usr/local/nginx/sbin/nginx.oldcp -rf objs/nginx /usr/local/nginx/sbin/make upgrade |
|---|
下载OWASP安全规则,放在nginx目录的conf里面
Shell
cd /usr/local/nginx/conf/ git clone https://github.com/SpiderLabs/owasp-modsecurity-crs.git cd owasp-modsecurity-crs/ cp crs-setup.conf.example crs-setup.conf vim crs-setup.conf 修改: 1.默认是只记录日志,不拦截,需要注释下面两行 # SecDefaultAction "phase:1,nolog,auditlog,pass" # SecDefaultAction "phase:2,nolog,auditlog,pass" 2.打开新规则,当触发规则,返回403 SecDefaultAction "phase:1,log,auditlog,deny,status:403" SecDefaultAction "phase:2,log,auditlog,deny,status:403" cd /usr/local/nginx/conf/owasp-modsecurity-crs/rules #进去打开两个规则 cp REQUEST-900-EXCLUSION-RULES-BEFORE-CRS.conf.example REQUEST-900-EXCLUSION-RULES-BEFORE-CRS.conf cp RESPONSE-999-EXCLUSION-RULES-AFTER-CRS.conf.example RESPONSE-999-EXCLUSION-RULES-AFTER-CRS.conf
123456789101112131415 | cd /usr/local/nginx/conf/ git clone https://github.com/SpiderLabs/owasp-modsecurity-crs.gitcd owasp-modsecurity-crs/cp crs-setup.conf.example crs-setup.confvim crs-setup.conf 修改:1.默认是只记录日志,不拦截,需要注释下面两行 # SecDefaultAction "phase:1,nolog,auditlog,pass" # SecDefaultAction "phase:2,nolog,auditlog,pass"2.打开新规则,当触发规则,返回403 SecDefaultAction "phase:1,log,auditlog,deny,status:403" SecDefaultAction "phase:2,log,auditlog,deny,status:403"cd /usr/local/nginx/conf/owasp-modsecurity-crs/rules #进去打开两个规则cp REQUEST-900-EXCLUSION-RULES-BEFORE-CRS.conf.example REQUEST-900-EXCLUSION-RULES-BEFORE-CRS.confcp RESPONSE-999-EXCLUSION-RULES-AFTER-CRS.conf.example RESPONSE-999-EXCLUSION-RULES-AFTER-CRS.conf |
|---|
modsecurity配置:
Shell
拷贝配置文件到nginx conf目录: cp /usr/local/modsecurity-2.9.2/modsecurity.conf-recommended /usr/local/nginx/conf/modsecurity.conf cp /usr/local/modsecurity-2.9.2/unicode.mapping /usr/local/nginx/conf/ vim modsecurity.conf SecRuleEngine On #修改引擎为开启 最后面插入规则:(这个是3.0的,如果有其他更新可以再owasp-modsecurity-crs/rules/查看模板) include owasp-modsecurity-crs/crs-setup.conf include owasp-modsecurity-crs/rules/REQUEST-900-EXCLUSION-RULES-BEFORE-CRS.conf include owasp-modsecurity-crs/rules/REQUEST-901-INITIALIZATION.conf Include owasp-modsecurity-crs/rules/REQUEST-903.9002-WORDPRESS-EXCLUSION-RULES.conf include owasp-modsecurity-crs/rules/REQUEST-905-COMMON-EXCEPTIONS.conf include owasp-modsecurity-crs/rules/REQUEST-910-IP-REPUTATION.conf include owasp-modsecurity-crs/rules/REQUEST-911-METHOD-ENFORCEMENT.conf include owasp-modsecurity-crs/rules/REQUEST-912-DOS-PROTECTION.conf include owasp-modsecurity-crs/rules/REQUEST-913-SCANNER-DETECTION.conf include owasp-modsecurity-crs/rules/REQUEST-920-PROTOCOL-ENFORCEMENT.conf include owasp-modsecurity-crs/rules/REQUEST-921-PROTOCOL-ATTACK.conf include owasp-modsecurity-crs/rules/REQUEST-930-APPLICATION-ATTACK-LFI.conf include owasp-modsecurity-crs/rules/REQUEST-931-APPLICATION-ATTACK-RFI.conf include owasp-modsecurity-crs/rules/REQUEST-932-APPLICATION-ATTACK-RCE.conf include owasp-modsecurity-crs/rules/REQUEST-933-APPLICATION-ATTACK-PHP.conf include owasp-modsecurity-crs/rules/REQUEST-941-APPLICATION-ATTACK-XSS.conf include owasp-modsecurity-crs/rules/REQUEST-942-APPLICATION-ATTACK-SQLI.conf include owasp-modsecurity-crs/rules/REQUEST-943-APPLICATION-ATTACK-SESSION-FIXATION.conf include owasp-modsecurity-crs/rules/REQUEST-949-BLOCKING-EVALUATION.conf include owasp-modsecurity-crs/rules/RESPONSE-950-DATA-LEAKAGES.conf include owasp-modsecurity-crs/rules/RESPONSE-951-DATA-LEAKAGES-SQL.conf include owasp-modsecurity-crs/rules/RESPONSE-952-DATA-LEAKAGES-JAVA.conf include owasp-modsecurity-crs/rules/RESPONSE-953-DATA-LEAKAGES-PHP.conf include owasp-modsecurity-crs/rules/RESPONSE-954-DATA-LEAKAGES-IIS.conf include owasp-modsecurity-crs/rules/RESPONSE-959-BLOCKING-EVALUATION.conf include owasp-modsecurity-crs/rules/RESPONSE-980-CORRELATION.conf include owasp-modsecurity-crs/rules/RESPONSE-999-EXCLUSION-RULES-AFTER-CRS.conf
123456789101112131415161718192021222324252627282930313233 | 拷贝配置文件到nginx conf目录:cp /usr/local/modsecurity-2.9.2/modsecurity.conf-recommended /usr/local/nginx/conf/modsecurity.confcp /usr/local/modsecurity-2.9.2/unicode.mapping /usr/local/nginx/conf/vim modsecurity.conf SecRuleEngine On #修改引擎为开启最后面插入规则:(这个是3.0的,如果有其他更新可以再owasp-modsecurity-crs/rules/查看模板)include owasp-modsecurity-crs/crs-setup.confinclude owasp-modsecurity-crs/rules/REQUEST-900-EXCLUSION-RULES-BEFORE-CRS.confinclude owasp-modsecurity-crs/rules/REQUEST-901-INITIALIZATION.confInclude owasp-modsecurity-crs/rules/REQUEST-903.9002-WORDPRESS-EXCLUSION-RULES.confinclude owasp-modsecurity-crs/rules/REQUEST-905-COMMON-EXCEPTIONS.confinclude owasp-modsecurity-crs/rules/REQUEST-910-IP-REPUTATION.confinclude owasp-modsecurity-crs/rules/REQUEST-911-METHOD-ENFORCEMENT.confinclude owasp-modsecurity-crs/rules/REQUEST-912-DOS-PROTECTION.confinclude owasp-modsecurity-crs/rules/REQUEST-913-SCANNER-DETECTION.confinclude owasp-modsecurity-crs/rules/REQUEST-920-PROTOCOL-ENFORCEMENT.confinclude owasp-modsecurity-crs/rules/REQUEST-921-PROTOCOL-ATTACK.confinclude owasp-modsecurity-crs/rules/REQUEST-930-APPLICATION-ATTACK-LFI.confinclude owasp-modsecurity-crs/rules/REQUEST-931-APPLICATION-ATTACK-RFI.confinclude owasp-modsecurity-crs/rules/REQUEST-932-APPLICATION-ATTACK-RCE.confinclude owasp-modsecurity-crs/rules/REQUEST-933-APPLICATION-ATTACK-PHP.confinclude owasp-modsecurity-crs/rules/REQUEST-941-APPLICATION-ATTACK-XSS.confinclude owasp-modsecurity-crs/rules/REQUEST-942-APPLICATION-ATTACK-SQLI.confinclude owasp-modsecurity-crs/rules/REQUEST-943-APPLICATION-ATTACK-SESSION-FIXATION.confinclude owasp-modsecurity-crs/rules/REQUEST-949-BLOCKING-EVALUATION.confinclude owasp-modsecurity-crs/rules/RESPONSE-950-DATA-LEAKAGES.confinclude owasp-modsecurity-crs/rules/RESPONSE-951-DATA-LEAKAGES-SQL.confinclude owasp-modsecurity-crs/rules/RESPONSE-952-DATA-LEAKAGES-JAVA.confinclude owasp-modsecurity-crs/rules/RESPONSE-953-DATA-LEAKAGES-PHP.confinclude owasp-modsecurity-crs/rules/RESPONSE-954-DATA-LEAKAGES-IIS.confinclude owasp-modsecurity-crs/rules/RESPONSE-959-BLOCKING-EVALUATION.confinclude owasp-modsecurity-crs/rules/RESPONSE-980-CORRELATION.confinclude owasp-modsecurity-crs/rules/RESPONSE-999-EXCLUSION-RULES-AFTER-CRS.conf |
|---|
nginx配置启用规则,在location启用规则
Shell
vim /usr/local/nginx/conf/nginx.conf location / { ModSecurityEnabled on; ModSecurityConfig modsecurity.conf; root html; } /usr/local/nginx/sbin/nginx -t&&/usr/local/nginx/sbin/nginx -s reload
1234567 | vim /usr/local/nginx/conf/nginx.conflocation / { ModSecurityEnabled on; ModSecurityConfig modsecurity.conf; root html;}/usr/local/nginx/sbin/nginx -t&&/usr/local/nginx/sbin/nginx -s reload |
|---|
测试:
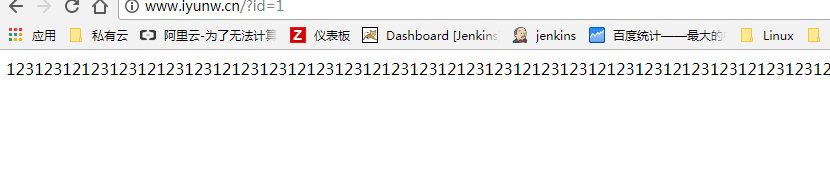
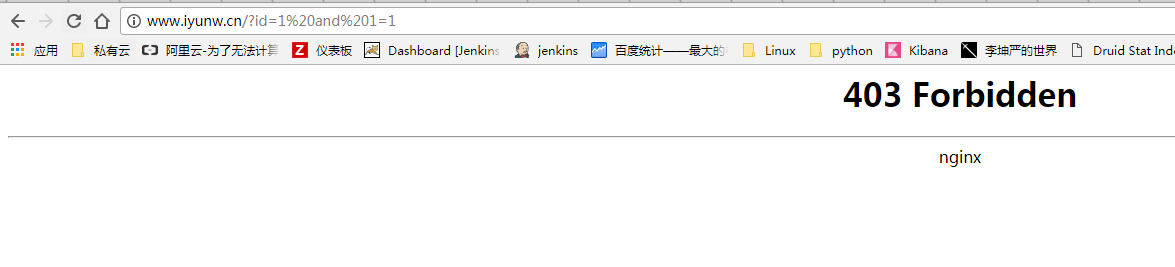
本文参与 腾讯云自媒体同步曝光计划,分享自作者个人站点/博客。
如有侵权请联系 cloudcommunity@tencent.com 删除
评论
登录后参与评论
推荐阅读

