Set up WireGuard Server in OpenWRT
Set up WireGuard Server in OpenWRT

hiplon
发布于 2023-10-18 08:28:29
发布于 2023-10-18 08:28:29
Set up WireGuard Server in OpenWRT
By HKL, on Sunday 2023-08-13 21:12, tagged: 🏷️Networking 🏷️Operating
This article is an AI translation of the original version.
This article is mainly to realize in the OpenWRT router system to build WireGuard server to facilitate remote connection.
Previously, we have been using Openconnect VPN in OpenWRT, because it is SSLVPN, and it is very convenient to use with CISCO’s anyconnect client. Still, because now ISPs can recognize this SSL-based traffic and block the public IP, we have to think about switching to the UDP-based OpenVPN -> WireGuard VPN.
Continued: In the original article sent to the V2EX above, everyone said WireGuard’s performance is better and then looked at the information. If the number of Peers is not a lot of words, realizing Server/Client type of Dial-Up VPN is still feasible, so this side of the tutorials also writes more conveniently for you!
The following two main steps:
(1) Install and configure WireGuard in OpenWRT.
(2) Configure the multi-peers program
So now it starts, the current system is using the latest OpenWRT 19.07.0-rc1, which should also be applicable to OpenWrt 18.06.4
First, let’s post a topology with 2 Peers connected.
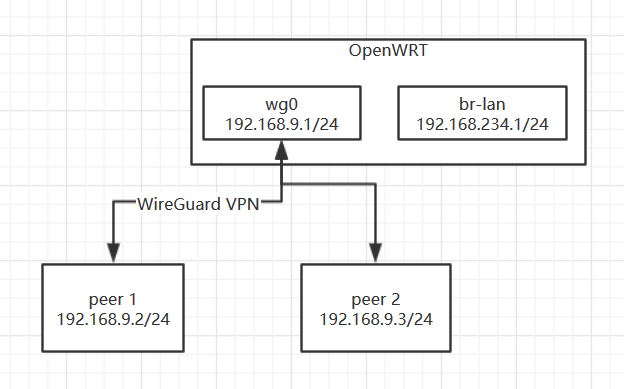
- Install and configure WireGuard in OpenWRT.
First, install all the required packages.
opkg update
opkg install wireguard luci-proto-wireguard luci-app-wireguardPreset WireGuard parameters and network segments
WG_IF="wg0"
WG_PORT="51820"
WG_ADDR="192.168.9.1/24"The network segment defined by WG_ADDR should not conflict with the existing segments on the intranet.
Configure the firewall to open the appropriate ports.
# Configure firewall
uci rename firewall.@zone[0]="lan"
uci rename firewall.@zone[1]="wan"
uci rename firewall.@forwarding[0]="lan_wan"
uci del_list firewall.lan.network="${WG_IF}"
uci add_list firewall.lan.network="${WG_IF}"
uci -q delete firewall.wg
uci set firewall.wg="rule"
uci set firewall.wg.name="Allow-WireGuard"
uci set firewall.wg.src="wan"
uci set firewall.wg.dest_port="${WG_PORT}"
uci set firewall.wg.proto="udp"
uci set firewall.wg.target="ACCEPT"
uci commit firewall
/etc/init.d/firewall restartGenerate server and client certificates.
Generate the client wgclient.pub with the Windows client and transfer it to the router.
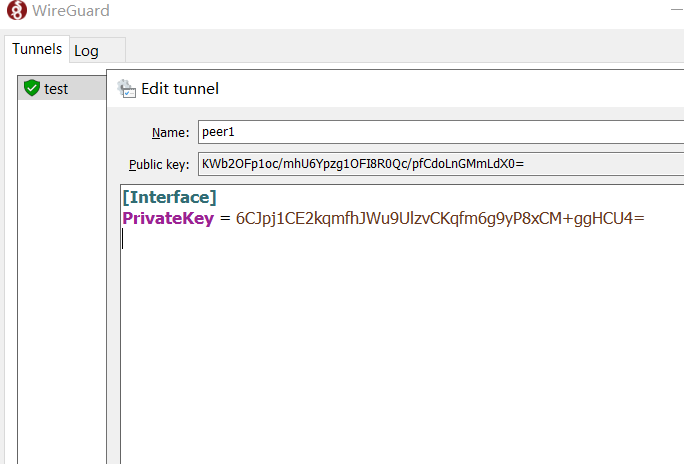
# Rename the pubkey generated by the Windows client as wgclient.pub.
echo KWb2OFp1oc/mhU6Ypzg1OFI8R0Qc/pfCdoLnGMmLdX0= > wgclient.pub
# Generate and exchange the keys
umask u=rw,g=,o=
wg genkey | tee wgserver.key | wg pubkey > wgserver.pub
wg genpsk > wg.psk
WG_KEY="$(cat wgserver.key)"
WG_PSK="$(cat wg.psk)"
WG_PUB="$(cat wgclient.pub)"Configure the OpenWRT server network.
# Configure network
uci -q delete network.${WG_IF}
uci set network.${WG_IF}="interface"
uci set network.${WG_IF}.proto="wireguard"
uci set network.${WG_IF}.private_key="${WG_KEY}"
uci set network.${WG_IF}.listen_port="${WG_PORT}"
uci add_list network.${WG_IF}.addresses="${WG_ADDR}"
# Add VPN peers
uci -q delete network.wgclient
uci set network.wgclient="wireguard_${WG_IF}"
uci set network.wgclient.public_key="${WG_PUB}"
uci set network.wgclient.preshared_key="${WG_PSK}"
uci add_list network.wgclient.allowed_ips="${WG_ADDR%.*}.0/${WG_ADDR#*/}"
uci commit network
/etc/init.d/network restartIn this way, the OpenWRT configuration is complete. Next, modify the configuration of the Windows client.
[Interface]
PrivateKey = 6CJpj1CE2kqmfhJWu9UlzvCKqfm6g9yP8xCM+ggHCU4=
Address = 192.168.9.2/24
[Peer]
PublicKey = EI0o2k+BKTPoVP6e0hbJQSgn3gerwntlsebxLXt1Q3w=
PresharedKey = Ys1gDMulGlZAfW6HVWru5hpxmcQ3BHtWcwYV/pXeW3k=
AllowedIPs = 192.168.9.0/24, 192.168.234.0/24
Endpoint = ddns.example.com:51820Then the normal single Peer will have been passed.
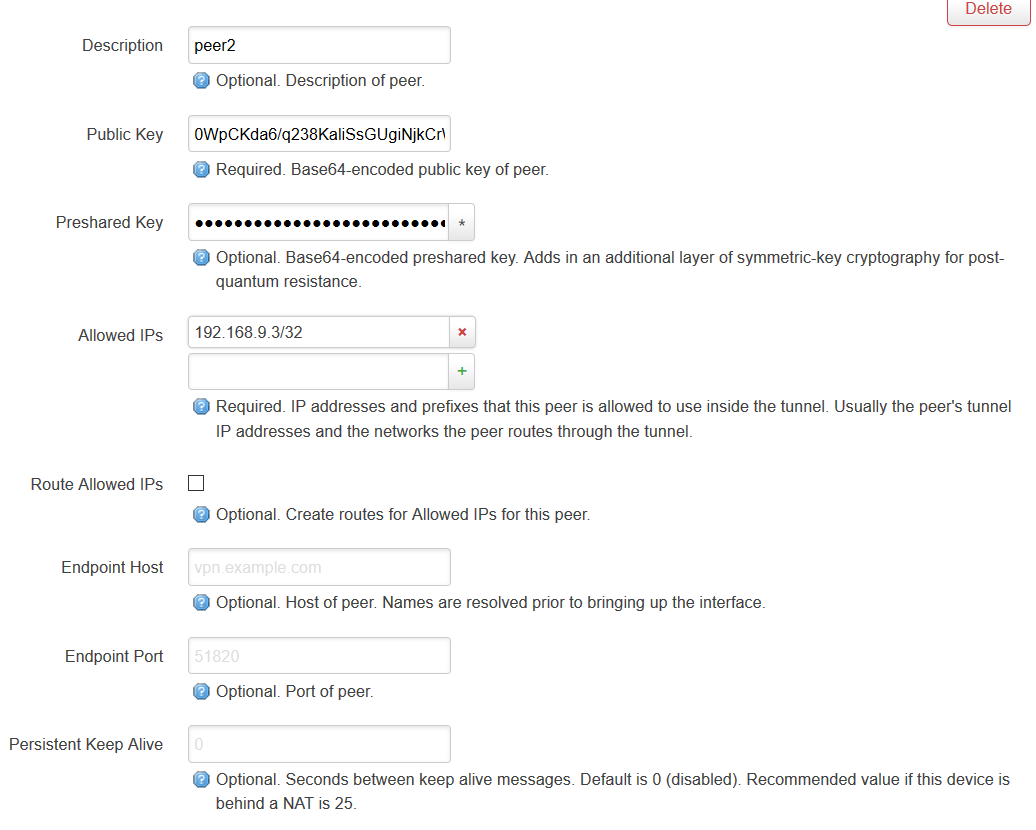
- Configure multi-peers program
Because Dial-Up is convenient for connecting to home, so there is no need to start more than one network segment, multiple Peers with a network segment are the most suitable. Luci can do the following configuration.
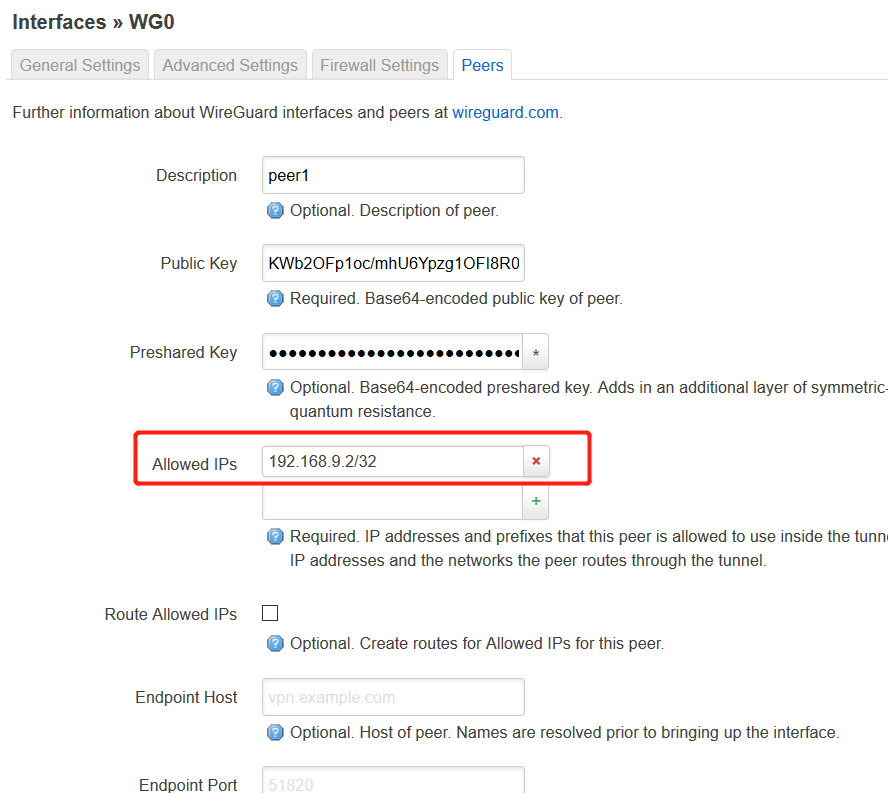
First, modify the Allow-IP setting of the Peers on OpenWRT according to the IP address of the first Peer.
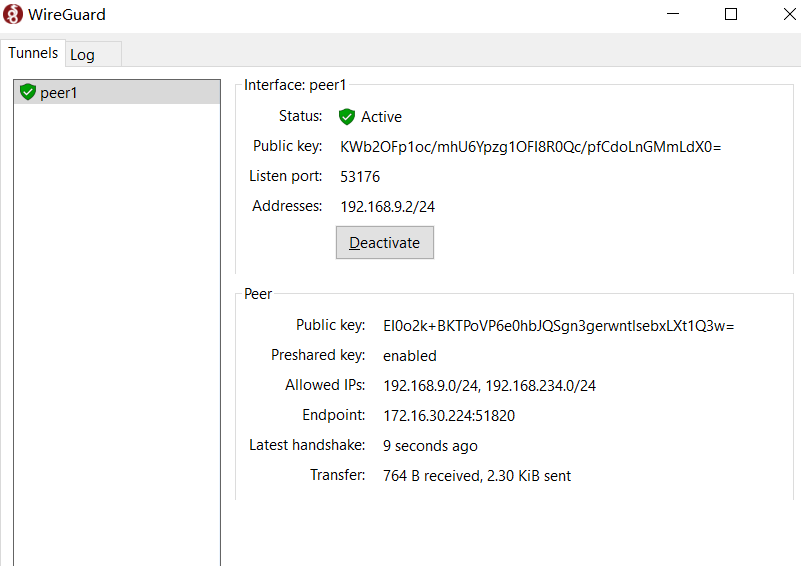
For example, if I set Address = 192.168.9.2/24 on the client side, then change the corresponding Peer Allowed IPs on OpenWRT to 192.168.9.2/32.
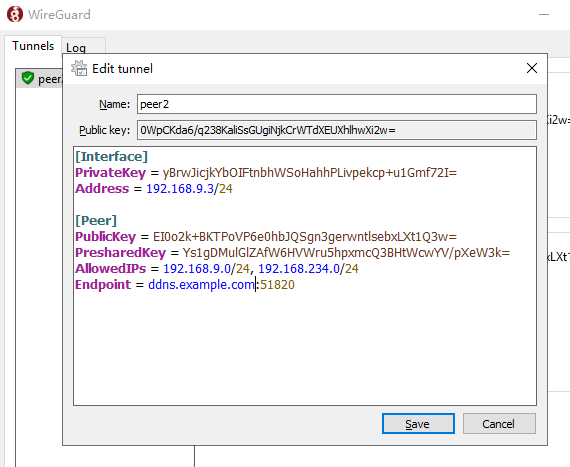
Then add a new Peer, first another terminal WireGuard client to generate a set of keys, and can be configured entirely in advance!
[Interface]
PrivateKey = yBrwJicjkYbOIFtnbhWSoHahhPLivpekcp+u1Gmf72I=
Address = 192.168.9.3/24
[Peer]
PublicKey = EI0o2k+BKTPoVP6e0hbJQSgn3gerwntlsebxLXt1Q3w=
PresharedKey = Ys1gDMulGlZAfW6HVWru5hpxmcQ3BHtWcwYV/pXeW3k=
AllowedIPs = 192.168.9.0/24, 192.168.234.0/24
Endpoint = ddns.example.com:51820Then the generated pubkey through the Web Luci configuration to the OpenWRT above on the line.
This basically completes the two-node WireGuard VPN configuration, if you need more nodes, repeat the second step on it.
refer:
本文参与 腾讯云自媒体同步曝光计划,分享自作者个人站点/博客。
原始发表:2023-08-13 ,如有侵权请联系 cloudcommunity@tencent.com 删除
评论
登录后参与评论
推荐阅读
目录

