MongoDB 用户权限管理
原创MongoDB 用户权限管理
原创
Power
发布于 2025-03-02 00:37:28
发布于 2025-03-02 00:37:28
代码可运行
运行总次数:0
代码可运行
一、MongoDB用户基本角色分配
1.1 MongoDB基本角色
- 数据库用户角色:read、readWrite
- 数据库管理角色:dbAdmin、dbOwner、userAdmin
- 集群管理角色:clusterAdmin、clusterManager、clusterMonitor、hostManager
- 备份恢复角色:backup、restore;
- 所有数据库角色:readAnyDatabase、readWriteAnyDatabase、userAdminAnyDatabase、dbAdminAnyDatabase
- 超级用户角色:root、dbOwner 、userAdmin、userAdminAnyDatabase几个角色间接或直接提供了系统超级用户的访问,其中MongoDB默认是没有开启用户认证的,也就是说游客也拥有超级管理员的权限。userAdminAnyDatabase:有分配角色和用户的权限,但没有查写的权限
- Read:允许用户读取指定数据库
- readwrite:允许用户读写指定数据库
- dbAdmin:允许用户在指定数据库中执行管理函数,如索引创建、删除,查看统计或访问system.profile
- userAdmin:允许用户向system.users集合写入,可以找指定数据库里创建删除和管理用户
- clusterAdmin:只在admin数据库中可用,赋予用户所有分片和复制集相关函数的管理权限
- readAnyDatabase:只在admin数据库中可用,赋予用户所有数据库的读权限readwriteAnyDatabase:只在admin数据库中可用,赋予用户所有数据库的读写权限
- userAdminAnyDatabase:只在admin数据库中可用,赋予用户所有数据库的userAdmin权限
- dbAdminAnyDatabase:只在admin 数据库中可用,赋予用户所有数据库的dbAdmin权限
- root:只在admin数据库中可用。超级账号,超级权限
1.2 MongoDB 内置角色及权限继承关系
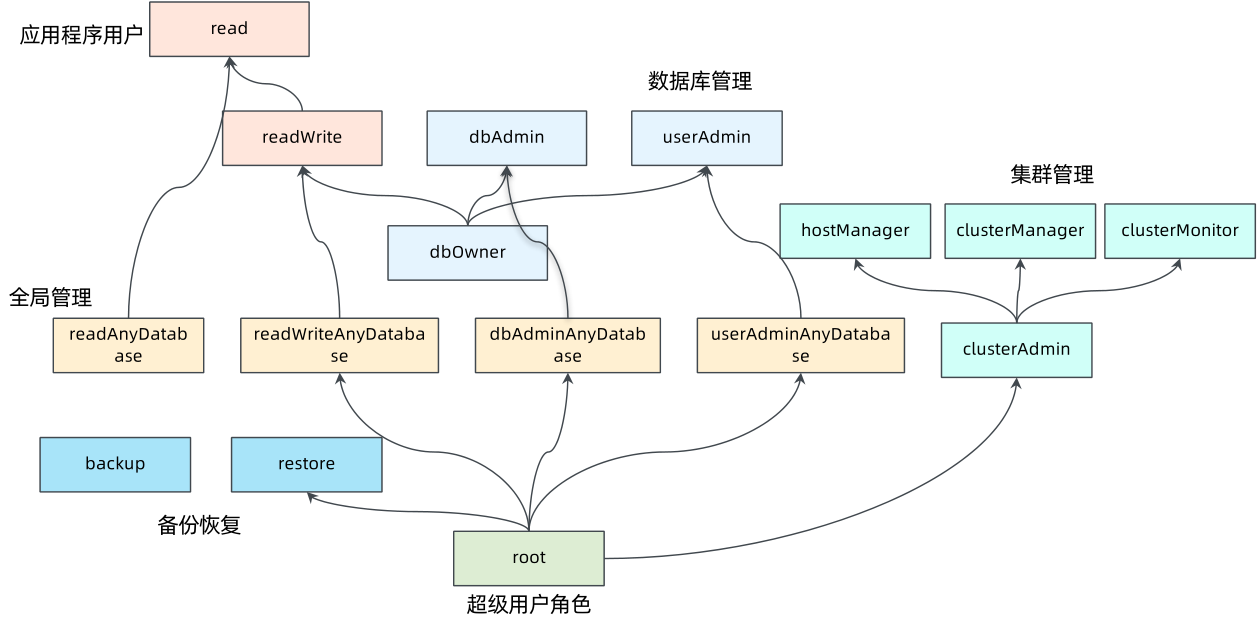
image2022-3-5_15-27-15.png
二、用户管理
2.1 创建管理员用户
(1)在admin库中创建stargao用户,用于远程管理
> use admin
switched to db admin
> db.createUser({user:"stargao",pwd:"123456",roles:[{role:"root",db:"admin"}]})
Successfully added user: {
"user" : "stargao",
"roles" : [
{
"role" : "root",
"db" : "admin"
}
]
}
> db.auth("stargao", "123456")
1(2)访问控制
db.createUser(
{
user:"stargao",
pwd:"123456",
roles:[{role:"root",db:"admin"}],
authenticationRestrictions:[{
clientSource: ["10.25.0.0/16"],
serverAddress: ["192.168.0.0/16"]
}]
}
)authenticationRestrictions:该字段为3.6版本以后的新特性,服务器在创建用户上强制执行的身份验证限制。指定可连接服务器的访问用户的ip地址列表或指定可连接服务器的服务器ip地址列表。(即白名单验证)
字段名称 数据类型 描述
clientSource ip地址数组或CIDR范围 如果存在,则服务器验证客户端的ip地址是否位于给定列表中,或者属于列表中的一个CIDR范围。如果客户端的ip地址不在当前,服务器就不会对用户进行身份验证。
serverAddress ip地址数组或CIDR范围 客户端可以连接的ip地址列表或CIDR范围。如果存在,服务器将验证客户端的连接是否符合给定列表中的ip地址列表或CIDR。如果不符合,则服务器不会对用户进行身份验证经测试authenticationRestrictions参数对MongoDB shell客户端版本有要求,建议4.0+,否则可能会出现参数错误的报错。如下:
MongoDB shell报错:
2021-08-25T18:15:03.628+0800 E QUERY [thread1] Error: couldn't add user: "authenticationRestrictions" is not a valid argument to createUser :
_getErrorWithCode@src/mongo/shell/utils.js:25:13
DB.prototype.createUser@src/mongo/shell/db.js:1437:15
@(shell):1:1图形化执行命令报错:
[Error]Error:"authenticationRestrictions"is not a valid argument to createUser at line2,column 12.2 创建读写权限用户
# 创建拥有test库的读写权限的用户
> use test
switched to db test
> db.createUser({user:"user_dbtest",pwd:"pwd_dbtest",roles:[{role:"readWrite",db:"test"}]})
Successfully added user: {
"user" : "user_dbtest",
"roles" : [
{
"role" : "readWrite",
"db" : "test"
}
]
}2.3 一个用户赋予多个库的操作权限
> db.createUser({user:"user_db1_db2",pwd:"pwd_db1_db2",roles:[{role:"readWrite",db:"db1"},{role:"readWrite",db:"db2"}]})
Successfully added user: {
"user" : "user_db1_db2",
"roles" : [
{
"role" : "readWrite",
"db" : "db1"
},
{
"role" : "readWrite",
"db" : "db2"
}
]
}2.4 查看当前库下的账号
> use admin # 查看admin库用户
switched to db admin
> show users
{
"_id" : "admin.ucloud_super_user",
"user" : "ucloud_super_user",
"db" : "admin",
"roles" : [
{
"role" : "userAdminAnyDatabase",
"db" : "admin"
}
]
}
{
"_id" : "admin.ucloudbackup",
"user" : "ucloudbackup",
"db" : "admin",
"roles" : [
{
"role" : "superuser",
"db" : "admin"
}
]
}
{
"_id" : "admin.root",
"user" : "root",
"db" : "admin",
"roles" : [
{
"role" : "superuser",
"db" : "admin"
}
]
}
{
"_id" : "admin.user_dbtest",
"user" : "user_dbtest",
"db" : "admin",
"roles" : [
{
"role" : "readWrite",
"db" : "admin"
}
]
}
{
"_id" : "admin.stargao",
"user" : "stargao",
"db" : "admin",
"roles" : [
{
"role" : "root",
"db" : "admin"
}
]
}
udb-1ndw2anr:PRIMARY> use test # 查看test库用户
switched to db test
udb-1ndw2anr:PRIMARY> show users
{
"_id" : "test.user_dbtest",
"user" : "user_dbtest",
"db" : "test",
"roles" : [
{
"role" : "readWrite",
"db" : "test"
}
]
}
{
"_id" : "test.user_db1_db2",
"user" : "user_db1_db2",
"db" : "test",
"roles" : [
{
"role" : "readWrite",
"db" : "db1"
},
{
"role" : "readWrite",
"db" : "db2"
}
]
}2.5 连接数查询
> db.serverStatus().connections;
{ "current" : 3, "available" : 19997, "totalCreated" : NumberLong(2032123) }2.6 更改用户密码
> use test
switched to db test
> db.changeUserPassword("user_dbtest","1234567")
> db.auth("user_dbtest","1234567")
12.7 修改用户权限
2.7.1 update更新权限
# 使用update修改权限,update修改方式是替换原来的权限
# 修改用户user_dbtest的权限为只读test库
> db.updateUser("user_dbtest",{roles:[{role:"read",db:"test"}]})
> show users
{
"_id" : "test.user_dbtest",
"user" : "user_dbtest",
"db" : "test",
"roles" : [
{
"role" : "read", # 已经变成了只读权限
"db" : "test"
}
]
}2.7.2 grant增加权限
# 在原有权限的基础上增加别的权限db.grantRolesToUser()
# 给user_dbtest增加对DB1库读写和DB2库的读权限
> db.grantRolesToUser("user_dbtest",[{role:"readWrite",db:"db1"},{role:"read",db:"db2"}])
> show users
{
"_id" : "test.user_dbtest",
"user" : "user_dbtest",
"db" : "test",
"roles" : [
{
"role" : "read", # db2 增加了读权限
"db" : "db2"
},
{
"role" : "readWrite", # db1增加了读写权限
"db" : "db1"
},
{
"role" : "read",
"db" : "test"
}
]
}2.7.3 revoke回收权限
# 删除用户的权限db.revokeRolesFromUser()
# 删除user_dbtest对db2库的读写权限
> db.revokeRolesFromUser("user_dbtest",[{role:"read",db:"db2"}])
> show users
{
"_id" : "test.user_dbtest",
"user" : "user_dbtest",
"db" : "test",
"roles" : [
{
"role" : "readWrite",
"db" : "db1"
}, # 对比2.7.2 db2的读权限已经被回收
{
"role" : "read",
"db" : "test"
}
]
}2.8 删除用户
# 删除user_dbtest
> db.dropUser("user_dbtest")
true原创声明:本文系作者授权腾讯云开发者社区发表,未经许可,不得转载。
如有侵权,请联系 cloudcommunity@tencent.com 删除。
原创声明:本文系作者授权腾讯云开发者社区发表,未经许可,不得转载。
如有侵权,请联系 cloudcommunity@tencent.com 删除。
评论
登录后参与评论
推荐阅读
目录

