未找到Terraform AWS提供程序的有效凭据源
未找到Terraform AWS提供程序的有效凭据源
提问于 2022-02-11 12:13:21
我正在为aws提供者使用shared_cred_file。例如,对于aws提供者3.63版本,terraform计划工作得很好。
当我使用AWSProvider4.0时,它会提示我对shared_credentials_files使用“应用更改”设置。更改后,没有出现错误,但第二个错误仍然存在。
有什么问题吗?
Warning: Argument is deprecated
│
│ with provider[“registry.terraform.io/hashicorp/aws”],
│ on main.tf line 15, in provider “aws”:
│ 15: shared_credentials_file = “~/.aws/credentials”
│
│ Use shared_credentials_files instead.
│
│ (and one more similar warning elsewhere)
╵
╷
│ Error: error configuring Terraform AWS Provider: no valid credential sources for Terraform AWS Provider found.
│
│ Please see https://registry.terraform.io/providers/hashicorp/aws
│ for more information about providing credentials.
│
│ Error: no EC2 IMDS role found, operation error ec2imds: GetMetadata, canceled, context deadline exceeded
│
│
│ with provider[“registry.terraform.io/hashicorp/aws”],
│ on main.tf line 13, in provider “aws”:
│ 13: provider “aws” {
│///////////////////////////////
// Infrastructure init
terraform {
backend "s3" {
bucket = "monitoring-********-infrastructure"
key = "tfstates/********-non-prod-rds-info.tfstate"
profile = "test-prof"
region = "eu-west-2"
shared_credentials_file = "~/.aws/credentials"
}
}
provider "aws" {
profile = "test-prof"
shared_credentials_files = ["~/.aws/credentials"]
region = "eu-west-2"
} Error: error configuring Terraform AWS Provider: no valid credential sources for Terraform AWS Provider found.
│
│ Please see https://registry.terraform.io/providers/hashicorp/aws
│ for more information about providing credentials.
│
│ Error: no EC2 IMDS role found, operation error ec2imds: GetMetadata, canceled, context deadline exceeded
│
│
│ with provider["registry.terraform.io/hashicorp/aws"],
│ on main.tf line 13, in provider "aws":
│ 13: provider "aws" {cat配置
[test-prof]
output = json
region = eu-west-2禁止酷刑委员会证书
[test-prof]
aws_access_key_id = ****************
aws_secret_access_key = ******************回答 3
Stack Overflow用户
回答已采纳
发布于 2022-02-11 18:32:03
改变
provider "aws" {
shared_credentials_file = "$HOME/.aws/credentials"
profile = "default"
region = "us-east-1"
}至
provider "aws" {
shared_credentials_file = "/Users/me/.aws/credentials"
profile = "default"
region = "us-east-1"
}为我工作过。
Stack Overflow用户
发布于 2022-04-12 06:26:33
根据最新的Terraform文档,这就是它的工作方式,
provider "aws" {
region = "us-east-1"
shared_credentials_files = ["C:/Users/tf_user/.aws/credentials"]
profile = "customprofile"
}我也有同样的问题,这件事对我来说很管用。
Stack Overflow用户
发布于 2022-03-01 16:38:41
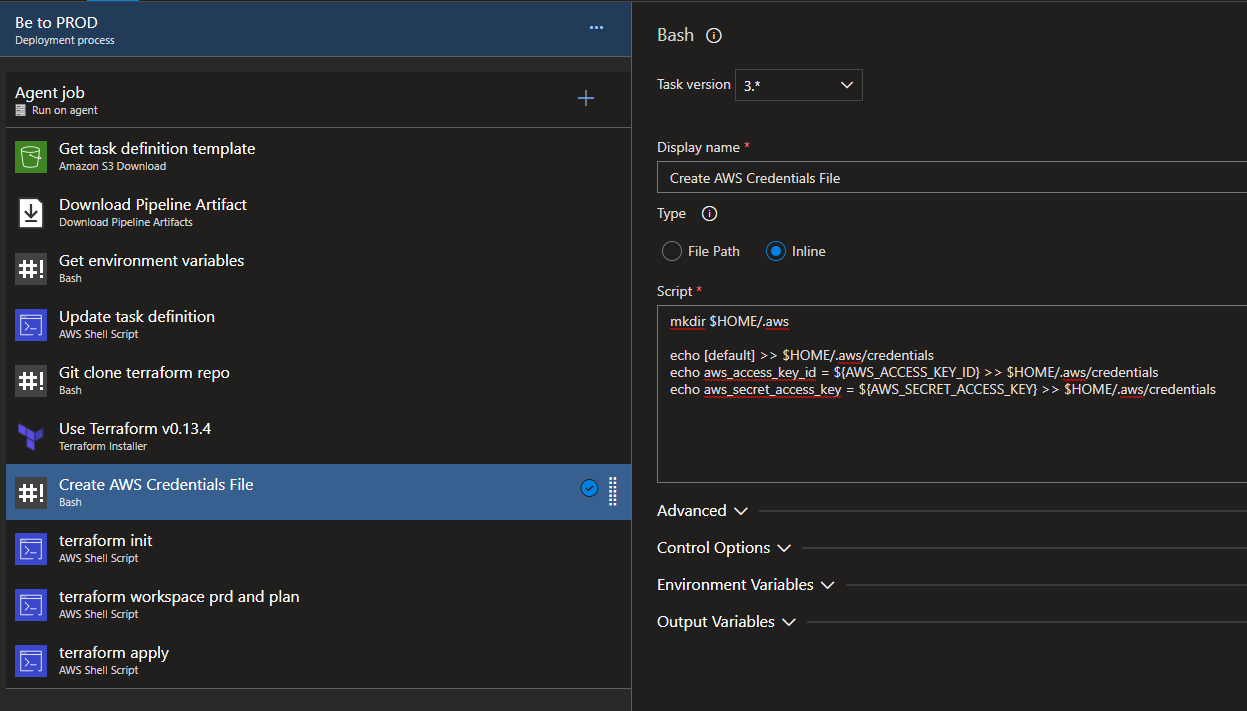
在从版本3 -> 4迁移AWS提供程序之后,我们在管道中遇到了这个问题。
因此,对于任何使用Azure DevOps或其他CI工具的人,修复应该像在管道中添加新步骤和创建共享凭据文件一样简单:
mkdir $HOME/.aws
echo [default] >> $HOME/.aws/credentials
echo aws_access_key_id = ${AWS_ACCESS_KEY_ID} >> $HOME/.aws/credentials
echo aws_secret_access_key = ${AWS_SECRET_ACCESS_KEY} >> $HOME/.aws/credentialsAWS_ACCESS_KEY_ID和AWS_SECRET_ACCESS_KEY应该定义为管道中的一个或多个秘密。
页面原文内容由Stack Overflow提供。腾讯云小微IT领域专用引擎提供翻译支持
原文链接:
https://stackoverflow.com/questions/71079921
复制相关文章
相似问题

