使用用户指定的托管id -无法写入存储队列的azure函数
使用用户指定的托管id -无法写入存储队列的azure函数
提问于 2022-05-13 18:36:28
我一直试图将我的DotNetCore6.0函数应用程序从一个基于连接字符串的函数应用程序更改为使用用户指定的托管标识。我没有建立钥匙库。
现在,当我在本地运行代码时,一切都正常工作(尽管我在local.settings.json中定义了Azure*环境变量,从而在本地使用azure cli凭据)
当我发布这个函数到azure时,当我运行我的web触发器时,我会得到一个http 400错误。完整的错误消息是这样的:
2022-05-13T18:21:21Z [Information] Executing 'CreateWorkspace' (Reason='This function was programmatically called via the host APIs.', Id=asdf-asdf-44a3-asdf-asdfasdf)
2022-05-13T18:21:21Z [Information] Received following payload: {
"name": "May13-Test1",
"readonly": true,
"owners": [
{"name": "peanut@yahoo.com"},
{"name": "butter@yahoo.com"}
]
}
2022-05-13T18:21:21Z [Information] DefaultAzureCredential.GetToken invoked. Scopes: [ https://storage.azure.com/.default ] ParentRequestId: ea21b20f-057b-4f41-a4af-b991133f6e75
2022-05-13T18:21:21Z [Information] EnvironmentCredential.GetToken invoked. Scopes: [ https://storage.azure.com/.default ] ParentRequestId: asdf-057b-asdf-a4af-asdfasdf
2022-05-13T18:21:21Z [Information] EnvironmentCredential.GetToken was unable to retrieve an access token. Scopes: [ https://storage.azure.com/.default ] ParentRequestId: asdf-057b-4f41-a4af-asdf Exception: Azure.Identity.CredentialUnavailableException (0x80131500): EnvironmentCredential authentication unavailable. Environment variables are not fully configured. See the troubleshooting guide for more information. https://aka.ms/azsdk/net/identity/environmentcredential/troubleshoot
2022-05-13T18:21:21Z [Information] ManagedIdentityCredential.GetToken invoked. Scopes: [ https://storage.azure.com/.default ] ParentRequestId: asdf-asdf-asdf-asdf-asdfasdfasdf
2022-05-13T18:21:21Z [Information] Request [asdf-d47d-asdf-a715-asdf] GET http://localhost:8081/msi/token?api-version=2019-08-01&resource=REDACTED
X-IDENTITY-HEADER:REDACTED
x-ms-client-request-id:5ef27cc5-d47d-42b3-a715-b6ffd5cc9dfd
x-ms-return-client-request-id:true
User-Agent:azsdk-net-Identity/1.6.0,(.NET 6.0.0-rtm.21522.10; Linux 5.4.81-microsoft-standard #1 SMP Thu Dec 3 23:47:24 UTC 2020)
client assembly: Azure.Identity
2022-05-13T18:21:22Z [Warning] Error response [5ef27cc5-d47d-42b3-a715-b6ffd5cc9dfd] 400 Bad Request (00.2s)
Date:Fri, 13 May 2022 18:21:19 GMT
Server:Kestrel
Transfer-Encoding:chunked
Content-Type:application/json; charset=utf-8
2022-05-13T18:21:22Z [Information] ManagedIdentityCredential.GetToken was unable to retrieve an access token. Scopes: [ https://storage.azure.com/.default ] ParentRequestId: ea21b20f-057b-4f41-a4af-b991133f6e75 Exception: Azure.Identity.AuthenticationFailedException (0x80131500): ManagedIdentityCredential authentication failed: Service request failed.
Status: 400 (Bad Request)
Content:
Headers:
Date: Fri, 13 May 2022 18:21:19 GMT
Server: Kestrel
Transfer-Encoding: chunked
Content-Type: application/json; charset=utf-8
See the troubleshooting guide for more information. https://aka.ms/azsdk/net/identity/managedidentitycredential/troubleshoot
---> Azure.RequestFailedException (0x80131500): Service request failed.
Status: 400 (Bad Request)
Content:
Headers:
Date: Fri, 13 May 2022 18:21:19 GMT
Server: Kestrel
Transfer-Encoding: chunked
Content-Type: application/json; charset=utf-8
2022-05-13T18:21:22Z [Information] DefaultAzureCredential.GetToken was unable to retrieve an access token. Scopes: [ https://storage.azure.com/.default ] ParentRequestId: ea21b20f-057b-4f41-a4af-b991133f6e75 Exception: Azure.Identity.AuthenticationFailedException (0x80131500): ManagedIdentityCredential authentication failed: Service request failed.
Status: 400 (Bad Request)
Content:
Headers:
Date: Fri, 13 May 2022 18:21:19 GMT
Server: Kestrel
Transfer-Encoding: chunked
Content-Type: application/json; charset=utf-8
See the troubleshooting guide for more information. https://aka.ms/azsdk/net/identity/managedidentitycredential/troubleshoot
---> Azure.RequestFailedException (0x80131500): Service request failed.
Status: 400 (Bad Request)
Content:
Headers:
Date: Fri, 13 May 2022 18:21:19 GMT
Server: Kestrel
Transfer-Encoding: chunked
Content-Type: application/json; charset=utf-8
2022-05-13T18:21:22Z [Information] ManagedIdentityCredential authentication failed: Service request failed.
Status: 400 (Bad Request)
Content:
Headers:
Date: Fri, 13 May 2022 18:21:19 GMT
Server: Kestrel
Transfer-Encoding: chunked
Content-Type: application/json; charset=utf-8
See the troubleshooting guide for more information. https://aka.ms/azsdk/net/identity/managedidentitycredential/troubleshoot
2022-05-13T18:21:22Z [Information] Executed 'CreateWorkspace' (Succeeded, Id=70d3b480-79b5-44a3-a88e-845817c13d12, Duration=761ms)在应用程序配置中,这就是我所拥有的:
[
{
"name": "APPINSIGHTS_INSTRUMENTATIONKEY",
"value": "234234234-asdf-asdf-asdf-asdfasdfas",
"slotSetting": false
},
{
"name": "AzureServicesAuthConnectionString",
"value": "RunAs=App;AppId={managedidentity-clientId}",
"slotSetting": false
},
{
"name": "FUNCTIONS_EXTENSION_VERSION",
"value": "~4",
"slotSetting": false
},
{
"name": "FUNCTIONS_WORKER_RUNTIME",
"value": "dotnet",
"slotSetting": false
},
{
"name": "MANAGEDID_CLIENT_ID",
"value": "{managedidclientid}",
"slotSetting": false
},
{
"name": "ExtServiceBus__fullyQualifiedNamespace",
"value": "myservicebus-bus.servicebus.windows.net",
"slotSetting": false
},
{
"name": "ExtStorageQueue__queueServiceUri",
"value": "https://mystorageaccount.queue.core.windows.net/",
"slotSetting": false
},
{
"name": "ExtStorageTableName",
"value": "provisionedWorkspaces",
"slotSetting": false
},
{
"name": "WEBSITE_MOUNT_ENABLED",
"value": "1",
"slotSetting": false
},
{
"name": "WEBSITE_RUN_FROM_PACKAGE",
"value": "https://mystorageaccount.blob.core.windows.net/function-releases/asdf-asdf-6b1b-asdf-asdf-asdf.zip?sv=2018-03-28&sr=b&sig=asdf%2Fxch%asdf%3D&st=2022-05-13T17%3A17%3A27Z&se=2032-05-13T17%3A22%3A27Z&sp=r",
"slotSetting": false
}
]码
这就是http触发器的样子。
[FunctionName("CreateWorkspace")]
public async Task<IActionResult> CreateWorkspace(
[HttpTrigger(AuthorizationLevel.Anonymous, "post", Route = "widget/workspaces")] HttpRequest req,
[Queue("workspaces"), StorageAccount("ExtStorageQueue")] ICollector<string> messageQueue,
ILogger log)
{
WorkspaceResponse response = new WorkspaceResponse();
try{
var content = await new StreamReader(req.Body).ReadToEndAsync();
log.LogInformation($"Received following payload: {content}");
var workspaceRequest = JsonConvert.DeserializeObject<Workspace>(content);
//this doesn't work messageQueue.Add(JsonConvert.SerializeObject(workspaceRequest));
//write to storage table.
response = await storage.ProvisioningRequest(workspaceRequest, req.HttpContext.Items["MS_AzureFunctionsRequestID"].ToString(), "enqueued");
}
catch(Exception ex)
{
log.LogInformation(ex.Message);
response.status = "Error: Invalid Request";
response.requestId=null;
}
return new OkObjectResult(JsonConvert.SerializeObject(response));
}托管id分配给应用程序:
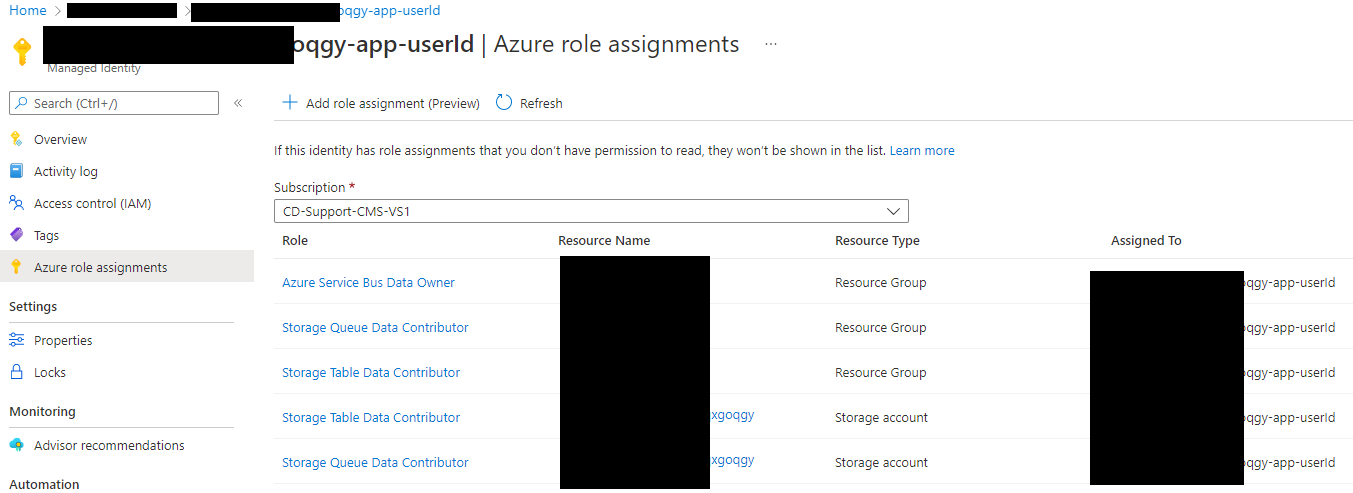
已将下列RBAC角色分配给托管ID:
问题
有任何方法可以手动触发使用这个用户分配的托管ID来获取令牌吗?在试图获取各种类型凭据的令牌时,错误消息似乎表明了它的死亡。
有办法将DefaultAzureCredentialoptions添加到http触发器吗?所以我可以做这样的事:
var clientId = Environment.GetEnvironmentVariable("MANAGEDID_CLIENT_ID");
DefaultAzureCredentialOptions options = new DefaultAzureCredentialOptions()
{
Diagnostics =
{
LoggedHeaderNames = { "x-ms-request-id" },
LoggedQueryParameters = { "api-version" },
IsLoggingContentEnabled = true
},
ExcludeVisualStudioCodeCredential = true,
ExcludeAzureCliCredential = true,
ExcludeManagedIdentityCredential = false,
ExcludeAzurePowerShellCredential = true,
ExcludeSharedTokenCacheCredential = true,
ExcludeInteractiveBrowserCredential = true,
ExcludeVisualStudioCredential = true,
ManagedIdentityClientId = clientId
};
DefaultAzureCredential credential = new DefaultAzureCredential(options);换句话说,有一种方法可以强制http触发器处理程序只尝试一种类型的凭据?
我还能做些什么来排除故障吗?我已经干了几天了,我似乎搞不懂。
回答 1
Stack Overflow用户
发布于 2022-05-15 05:34:21
页面原文内容由Stack Overflow提供。腾讯云小微IT领域专用引擎提供翻译支持
原文链接:
https://stackoverflow.com/questions/72234101
复制相关文章
相似问题

