Azure B2C客户端凭据流抛出invalid_grant AADB2C90085
Azure B2C客户端凭据流抛出invalid_grant AADB2C90085
提问于 2022-08-18 18:54:06
我跟踪了这个资源:CLIENTCREDENTIALSFLOW/OAuth2/v2.0/令牌
- Azure B2C应用程序注册:
- 受保护的web
- 公开api
- 应用ID URI = https://{my租户名称}.onmicrosoft.com/{受保护的web客户机id}/.default
- 公开api
- 受保护的web
- Daemon console app
- API Permissions
- API = protected web api
- Permission = access\_as\_application
- Type = Application
- Admin consent requested = Yes我使用OAuth客户端凭据流获取令牌:
POST https://{my tenant name}.b2clogin.com/{my tenant name}.onmicrosoft.com/{a basic user flow SUSI policy}/oauth2/v2.0/token
scope=https://icareb2cdev.onmicrosoft.com/{protected web api client id}/.default&
grant_type=client_credentials&
client_id={daemon console app client id}&
client_secret={daemon console app client secret}错误响应:
{
"error": "invalid_grant",
"error_description": "AADB2C90085: The service has encountered an internal error. Please reauthenticate and try again.\r\nCorrelation ID: REDACTED\r\nTimestamp: REDACTED\r\n"
}回答 2
Stack Overflow用户
回答已采纳
发布于 2022-08-22 18:42:03
我遇到了同样的问题,请再次检查您的清单,并确保"signInAudience":"AzureADandPersonalMicrosoftAccount“,而不仅仅是您的组织。也要确保您遵循的步骤与其他答案相同。
Stack Overflow用户
发布于 2022-08-19 06:46:15
我尝试在我的环境中复制相同的错误,并得到了如下所示的错误:
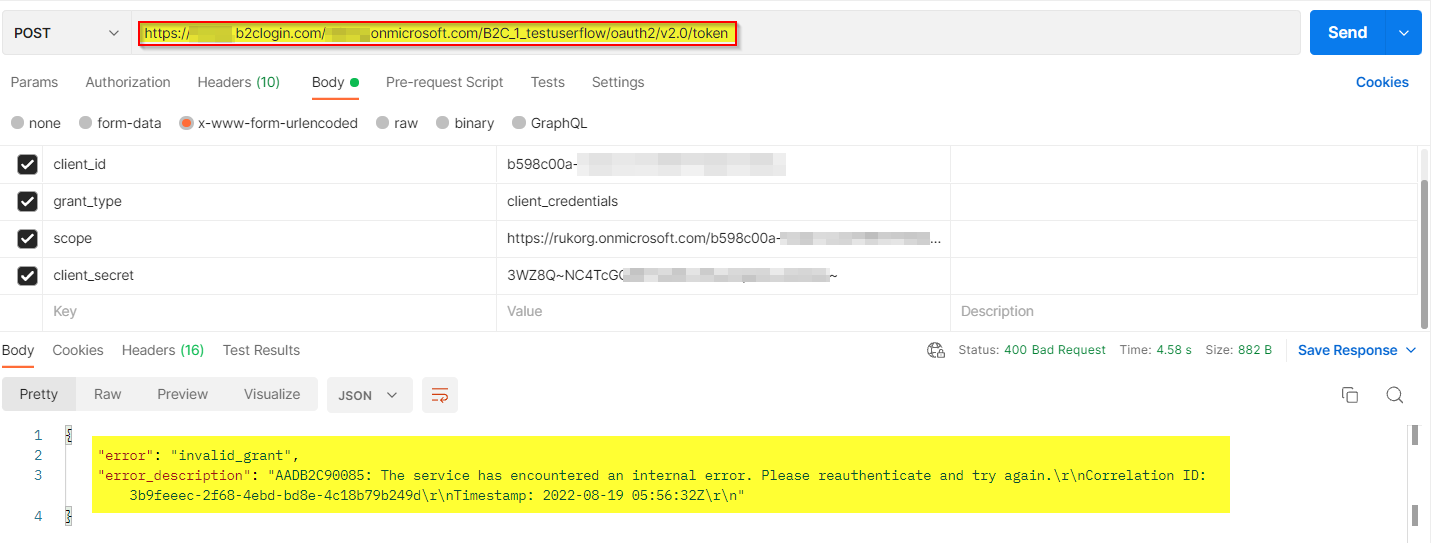
错误通常发生在,如果您在使用客户端凭据流时授予委托权限。
请检查是否在公开API选项卡中添加了作用域,如下所示:
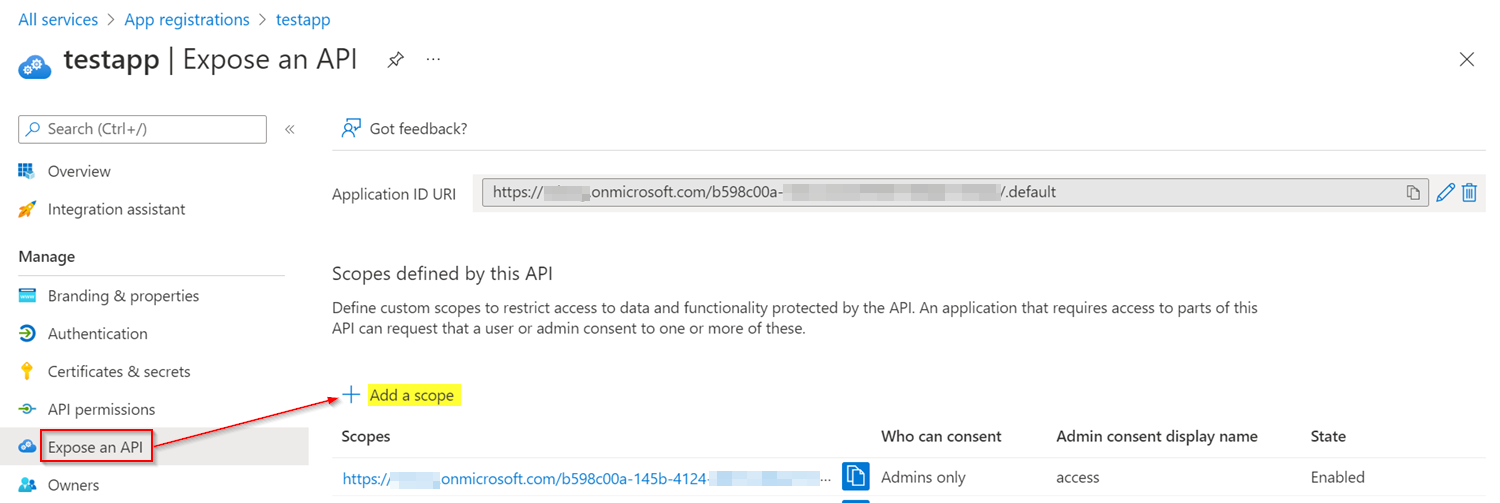
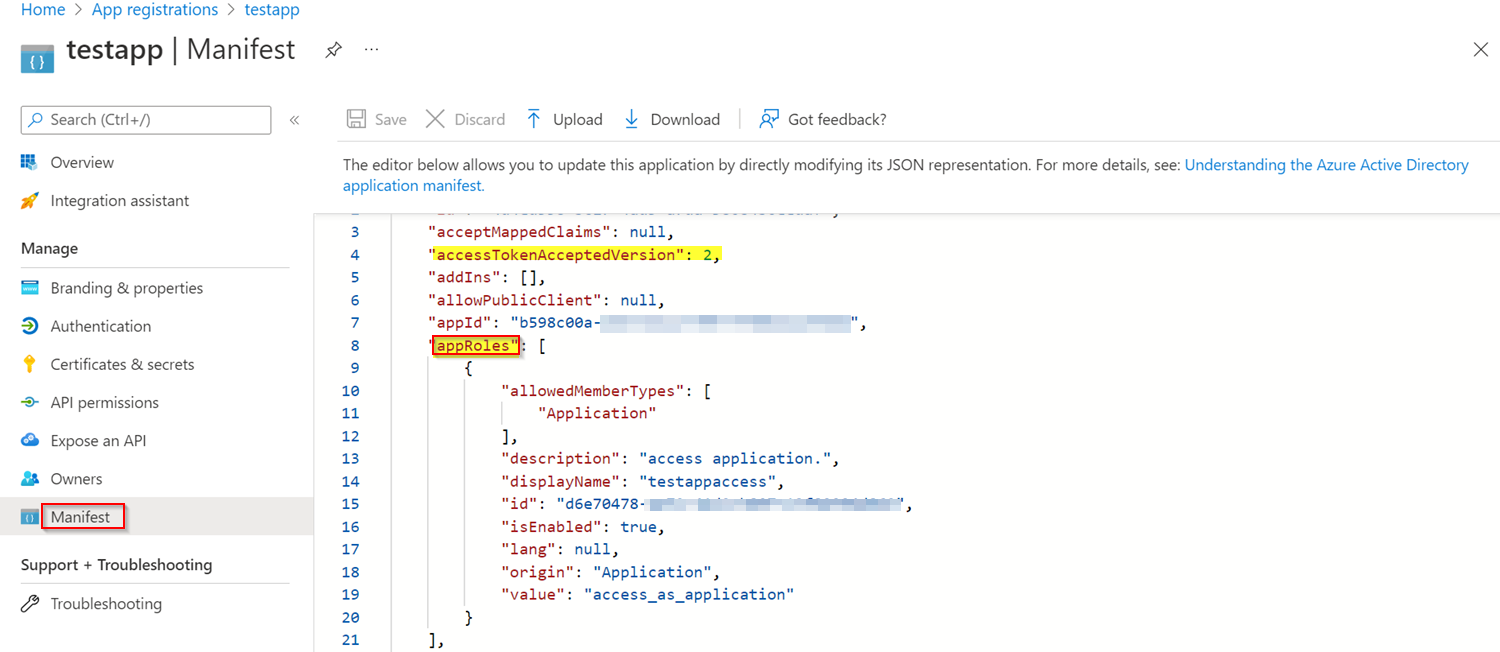
若要解决错误,请删除公开API中的作用域,并通过修改应用程序说明创建app role ,如下所示:
可以通过使用GUID或在线GUID发生器生成PowerShell
"appRoles": [
{
"allowedMemberTypes": [
"Application"
],
"description": "access application.",
"displayName": "testappaccess",
"id": "XXXXXXXX",
"isEnabled": true,
"lang": null,
"origin": "Application",
"value": "access_as_application"
}
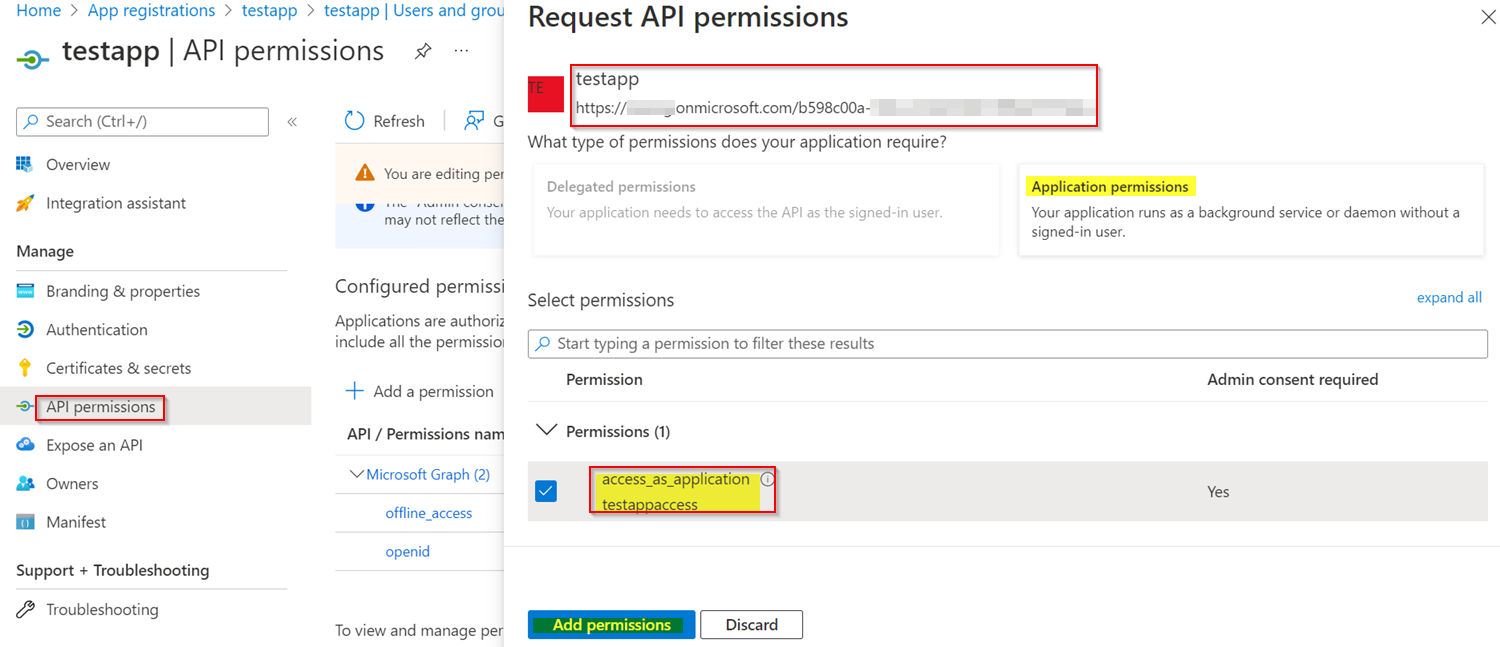
向用户添加角色并授予 Admin ,如下所示:
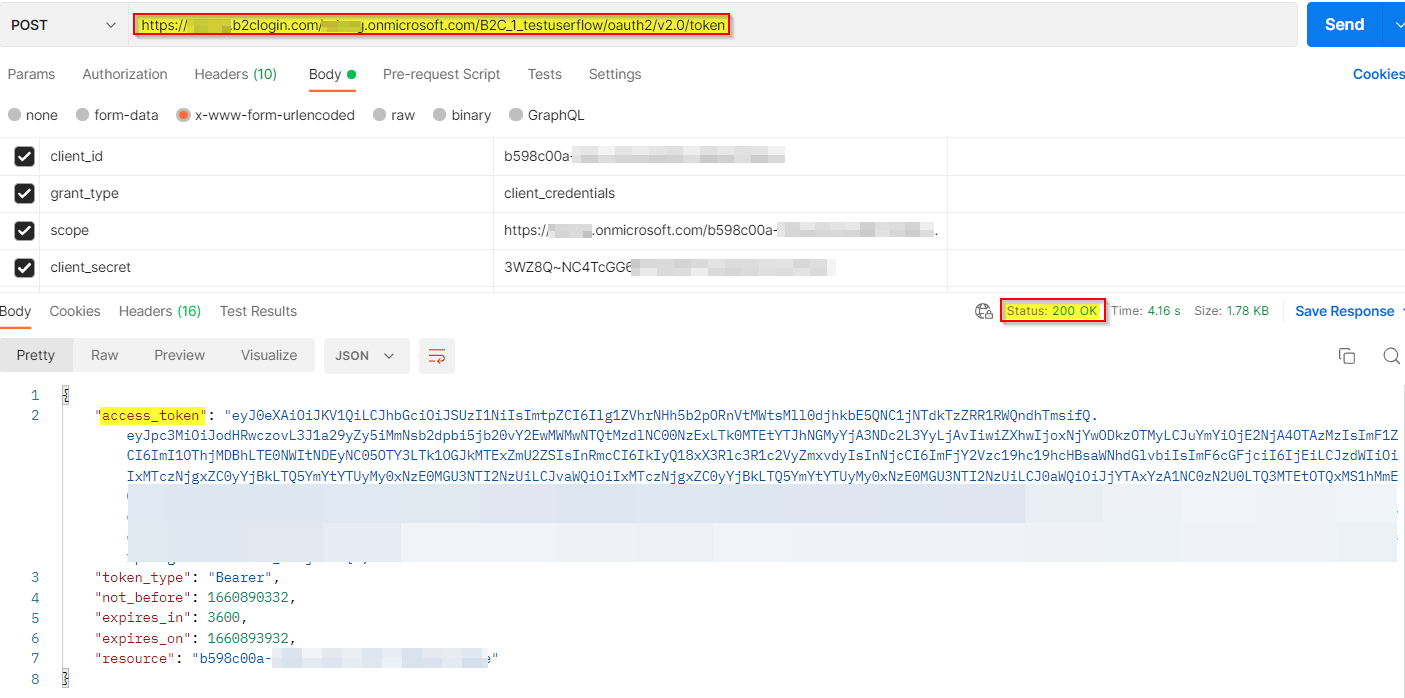
我能够成功地获得访问令牌,如下所示:
参考:
页面原文内容由Stack Overflow提供。腾讯云小微IT领域专用引擎提供翻译支持
原文链接:
https://stackoverflow.com/questions/73408144
复制相关文章
相似问题

