跨帐户DstMultipartUploadNotPermitted复制期间的S3
我有两个S3桶在两个不同的地区,在两个不同的帐户。我希望使用S3复制规则将所有文件(包括现有文件)从桶()复制到桶-b。
桶-a是一个现有的桶中已经有对象,桶-b是一个新的空桶。
我创建了一个复制规则,并运行批处理操作作业来复制现有的对象。作业完成后,63%的对象无法复制,错误为DstPutObjectNotPermitted 或 DstMultipartUploadNotPermitted,没有进一步的信息。谷歌没有针对这些错误提出任何建议。(这些文件来自于完成作业后生成的csv文件)。其余的对象按预期复制。
这是我的配置:
桶-a已启用版本控制,并使用默认的aws托管KMS密钥加密.ACL是启用的,这是桶策略:
{
"Version": "2008-10-17",
"Id": "NoBucketDelete",
"Statement": [
{
"Sid": "NoBucketDeleteStatement",
"Effect": "Deny",
"Principal": "*",
"Action": "s3:DeleteBucket",
"Resource": "arn:aws:s3:::bucket-a"
},
{
"Effect": "Deny",
"Principal": "*",
"Action": "s3:*",
"Resource": [
"arn:aws:s3:::bucket-a/*",
"arn:aws:s3:::bucket-a"
],
"Condition": {
"Bool": {
"aws:SecureTransport": "false"
}
}
}
]
}桶-b还启用了版本控制和ACL,并使用客户管理的密钥进行加密。
水桶政策是:
{
"Version": "2012-10-17",
"Id": "Policy1644945280205",
"Statement": [
{
"Effect": "Deny",
"Principal": "*",
"Action": "s3:*",
"Resource": [
"arn:aws:s3:::bucket-b/*",
"arn:aws:s3:::bucket-b"
],
"Condition": {
"Bool": {
"aws:SecureTransport": "false"
}
}
},
{
"Sid": "Stmt1644945277847",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::12345:role/bucket-replication-role"
},
"Action": [
"s3:ReplicateObject",
"s3:ReplicateTags",
"s3:ObjectOwnerOverrideToBucketOwner",
"s3:ReplicateDelete"
],
"Resource": "arn:aws:s3:::bucket-b/*"
}
]
}...and KMS的关键策略是
{
"Version": "2012-10-17",
"Id": "key-consolepolicy-3",
"Statement": [
{
"Sid": "Allow access through S3 for all principals in the account that are authorized to use S3",
"Effect": "Allow",
"Principal": {
"AWS": "*"
},
"Action": [
"kms:Encrypt",
"kms:Decrypt",
"kms:ReEncrypt*",
"kms:GenerateDataKey*",
"kms:DescribeKey"
],
"Resource": "*",
"Condition": {
"StringEquals": {
"kms:CallerAccount": "12345",
"kms:ViaService": "s3.us-west-2.amazonaws.com"
}
}
},
{
"Sid": "Enable IAM User Permissions",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::12345:root"
},
"Action": "kms:*",
"Resource": "*"
},
{
"Sid": "Allow access for Key Administrators",
"Effect": "Allow",
"Principal": {
"AWS": [
"arn:aws:iam::12345:user/root",
"arn:aws:iam::12345:user/user"
]
},
"Action": [
"kms:Create*",
"kms:Describe*",
"kms:Enable*",
"kms:List*",
"kms:Put*",
"kms:Update*",
"kms:Revoke*",
"kms:Disable*",
"kms:Get*",
"kms:Delete*",
"kms:TagResource",
"kms:UntagResource",
"kms:ScheduleKeyDeletion",
"kms:CancelKeyDeletion"
],
"Resource": "*"
},
{
"Sid": "Allow use of the key",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::12345:user/user"
},
"Action": [
"kms:Encrypt",
"kms:Decrypt",
"kms:ReEncrypt*",
"kms:GenerateDataKey*",
"kms:DescribeKey"
],
"Resource": "*"
},
{
"Sid": "Allow attachment of persistent resources",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::12345:user/user"
},
"Action": [
"kms:CreateGrant",
"kms:ListGrants",
"kms:RevokeGrant"
],
"Resource": "*",
"Condition": {
"Bool": {
"kms:GrantIsForAWSResource": "true"
}
}
}
]
}我在account中有一个角色--一个桶复制角色,它具有一个信任关系,允许S3承担角色和附加策略:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "s3.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}以及附加的政策:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:ReplicateDelete"
],
"Resource": "arn:aws:s3:::bucket-b/*"
},
{
"Effect": "Allow",
"Action": [
"kms:Decrypt",
"kms:GenerateDataKey"
],
"Resource": [
"arn:aws:kms:us-east-1:12345:key/[account-a-kms-key-id]"
]
},
{
"Effect": "Allow",
"Action": [
"kms:GenerateDataKey",
"kms:Encrypt"
],
"Resource": [
"arn:aws:kms:us-west-2:12345:key/[account-b-kms-key-id]"
]
},
{
"Effect": "Allow",
"Action": [
"s3:ObjectOwnerOverrideToBucketOwner"
],
"Resource": "arn:aws:s3:::bucket-b/*"
},
{
"Effect": "Allow",
"Action": [
"s3:GetReplicationConfiguration",
"s3:ListBucket"
],
"Resource": [
"arn:aws:s3:::bucket-a"
]
},
{
"Effect": "Allow",
"Action": [
"s3:GetObjectVersionForReplication",
"s3:GetObjectVersionAcl",
"s3:GetObjectVersionTagging"
],
"Resource": [
"arn:aws:s3:::bucket-a/*"
]
},
{
"Effect": "Allow",
"Action": [
"s3:ReplicateObject",
"s3:ReplicateTags"
],
"Resource": "arn:aws:s3:::bucket-b/*"
}
]
}这是我的复制规则,在桶-a上。
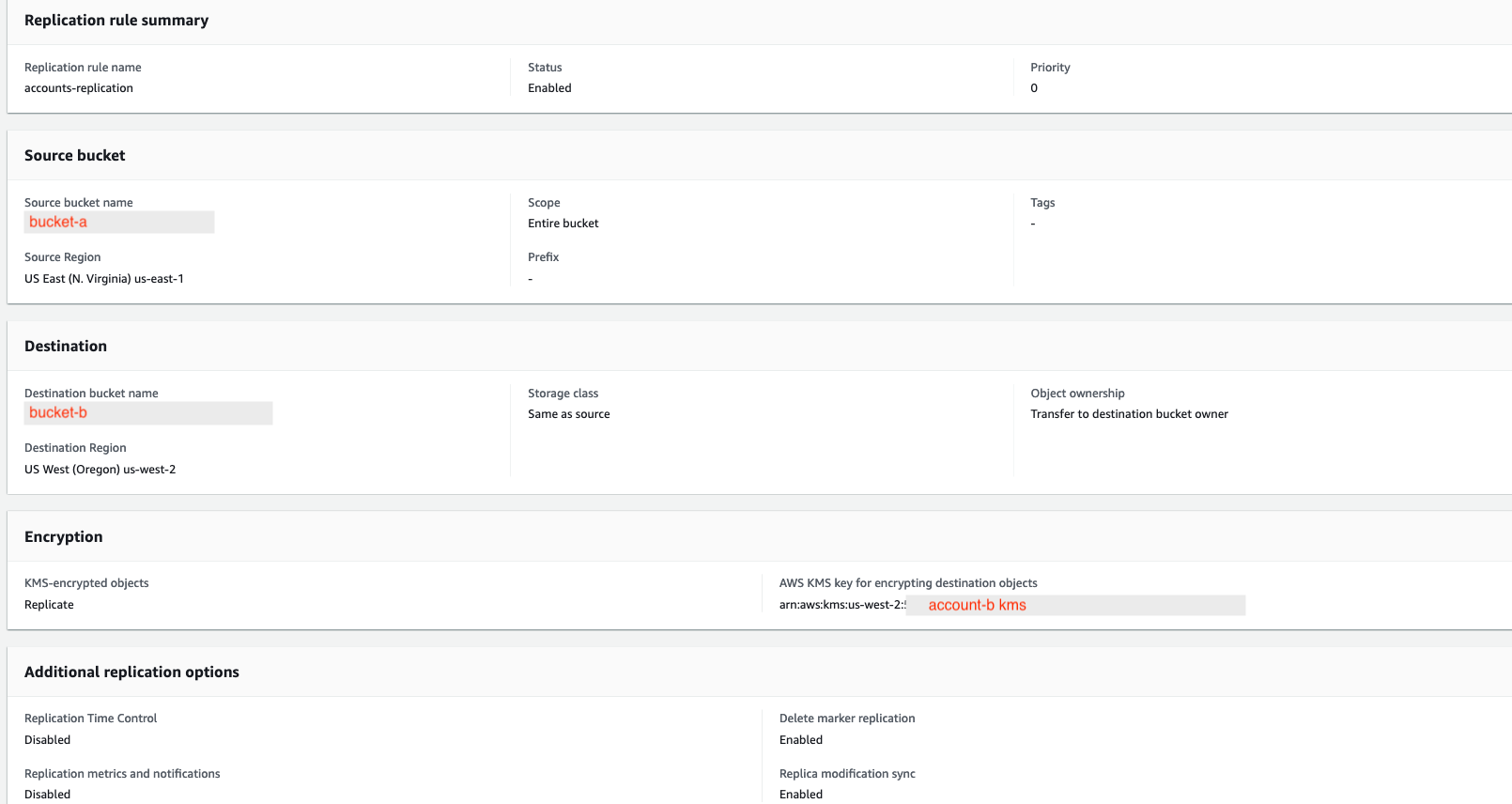
在创造过程中,上述角色也被附加在一起。
批处理操作是在创建复制规则时被提示的默认操作。
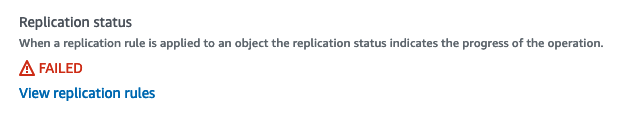
这些文件只是小的png,jsons,html文件等等--里面没有什么奇怪的东西。可以在对象信息中看到复制状态失败。
我的大多数策略规则来自于这个AWS支持页面:https://aws.amazon.com/premiumsupport/knowledge-center/s3-troubleshoot-replication/
更新
我在帐户-b KMS密钥中添加了以下策略:
{
"Sid": "AllowS3ReplicationSourceRoleToUseTheKey",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::12345:role/bucket-replication-role"
},
"Action": ["kms:GenerateDataKey", "kms:Encrypt"],
"Resource": "*"
}DstPutObjectNotPermitted错误已经消失,现在我看到的只是DstMultipartUploadNotPermitted错误。
更新2
我尝试用两个新的桶重新创建这个问题,但是无法重现这个问题,所以我假设这与如何存储桶-a中的一些旧文件有关。
回答 1
Stack Overflow用户
发布于 2022-09-23 20:41:48
这需要AWS支持的一些帮助,这是他们回应的相关要点:
"DstMultipartUploadNotPermitted“状态代码表示源对象是多部分上载,其复制所需的权限未在资源策略中授予。注意,如果一个源对象使用多部分上载上载到源桶,那么IAM复制角色也将使用多部分上载将副本对象上载到目标桶。我想告诉您,在S3桶中允许多部分上传将授予一些额外的权限。在涉及KMS加密时,IAM复制角色执行多部分上载所需的权限列表如下所示。
资源"arn:aws:s3:::DESTINATION-BUCKET/*"
- kms:Decrypt上的
- s3:PutObject和资源"arn:aws:kms:REGION:DESTINATION-ACCOUNT-ID:key/KEY-ID"
上的
...as井
"arn:aws:iam::12345:role/bucket-replication-role".确保目标桶策略将资源“arn:aws:s3::桶-b/*”上的"s3:PutObject“权限授予
复制角色
...and终于
我还请您将目标KMS密钥上的“KMS:
”和"kms:GenerateDataKey“权限授予目标KMS密钥策略中的IAM复制角色"arn:aws:iam::12345:role/bucket-replication-role”。
添加所有这些附加权限后,所有操作都按预期进行。
https://stackoverflow.com/questions/73466230
复制相似问题

