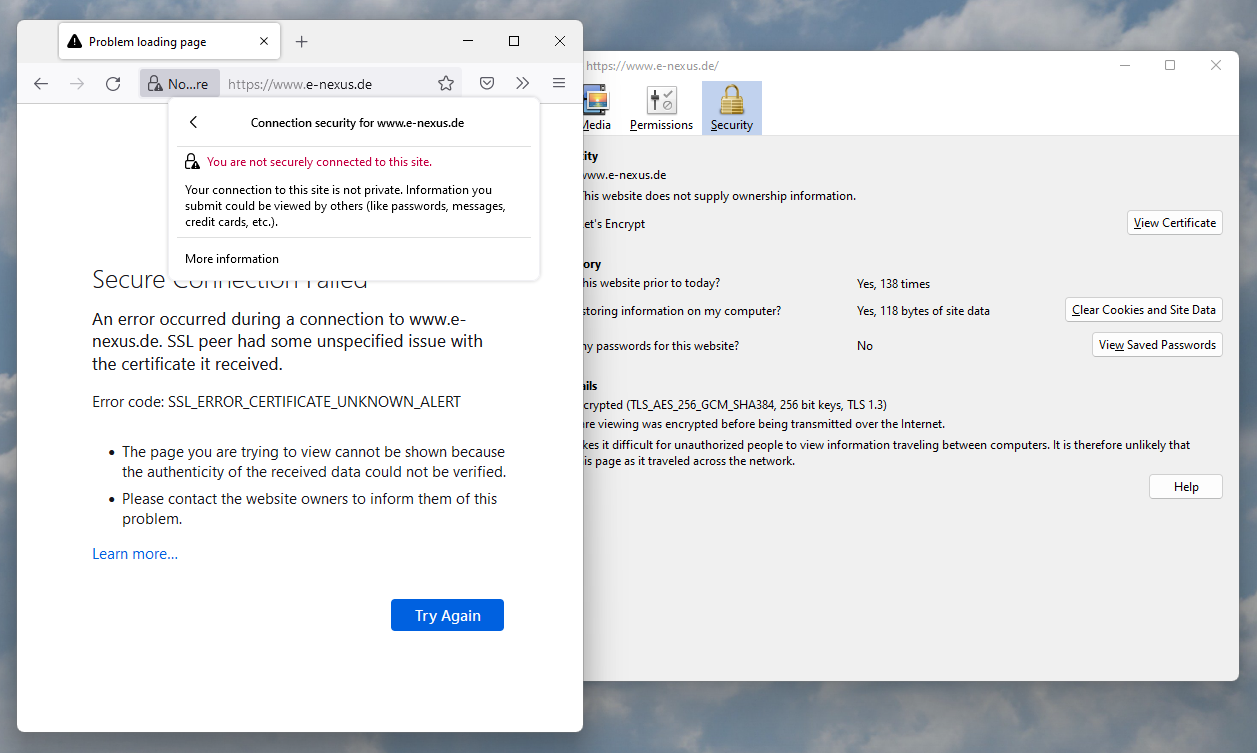
SSL在Chrome和Edge中工作,但在Firefox中不起作用
我有一个网站(http://www.e-nexus.de/),我试图设置一个SSL证书。该证书适用于Chrome和Edge,但在火狐(104.0)中确实出现了一个错误:
我激活了ssl-debug,这是输出(我更改了域名):
[root@rm-2 130 rm2.johndoe.de /usr/local/share/apache-tomcat-8.5.50/logs]# tail -f catalina.out
javax.net.ssl|DEBUG|14|https-jsse-nio2-443-exec-6|2022-08-29 23:07:02.639 CEST|HandshakeContext.java:305|No available cipher suite for TLS10
javax.net.ssl|DEBUG|14|https-jsse-nio2-443-exec-6|2022-08-29 23:07:02.640 CEST|HandshakeContext.java:305|No available cipher suite for TLS13
javax.net.ssl|DEBUG|14|https-jsse-nio2-443-exec-6|2022-08-29 23:07:02.642 CEST|HandshakeContext.java:305|No available cipher suite for TLS11
javax.net.ssl|DEBUG|14|https-jsse-nio2-443-exec-6|2022-08-29 23:07:02.646 CEST|SSLExtensions.java:135|Ignore unknown or unsupported extension (
"unknown extension (34)": {
0000: 00 08 04 03 05 03 06 03 02 03 ..........
}
)
javax.net.ssl|DEBUG|14|https-jsse-nio2-443-exec-6|2022-08-29 23:07:02.647 CEST|SSLExtensions.java:135|Ignore unknown or unsupported extension (
"unknown extension (28)": {
0000: 40 01 @.
}
)
javax.net.ssl|DEBUG|14|https-jsse-nio2-443-exec-6|2022-08-29 23:07:02.647 CEST|SSLExtensions.java:135|Ignore unknown or unsupported extension (
"unknown extension (65,037)": {
0000: 00 00 01 00 01 73 00 20 7E E0 E2 0A 3D 5F C1 07 .....s. ....=_..
(cut)
0130: F7 F2 23 E4 18 05 62 88 C5 ..#...b..
}
)
javax.net.ssl|DEBUG|14|https-jsse-nio2-443-exec-6|2022-08-29 23:07:02.657 CEST|ClientHello.java:808|Consuming ClientHello handshake message (
"ClientHello": {
"client version" : "TLSv1.2",
"random" : "D2 14 7F AA BE 53 DC 45 28 1E F1 DE CE 5C 47 E9 74 AA B6 4D 71 77 05 90 D6 E5 15 E3 47 09 D1 4C",
"session id" : "2C 40 BF 69 27 7A 56 9B C3 E1 D2 B0 7E DA 21 0A 7E 28 DE 2B 9C 13 18 A8 7E 63 78 5B A2 AB 7C C8",
"cipher suites" : "[TLS_AES_128_GCM_SHA256(0x1301), TLS_CHACHA20_POLY1305_SHA256(0x1303), TLS_AES_256_GCM_SHA384(0x1302), TLS_ECDHE_ECDSA_WITH_AES_12 8_GCM_SHA256(0xC02B), TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256(0xC02F), TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305_SHA256(0xCCA9), TLS_ECDHE_RSA_WITH_CHACHA20_POLY1 305_SHA256(0xCCA8), TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384(0xC02C), TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384(0xC030), TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA(0xC0 0A), TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA(0xC009), TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA(0xC013), TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA(0xC014), TLS_RSA_WITH_AES_1 28_GCM_SHA256(0x009C), TLS_RSA_WITH_AES_256_GCM_SHA384(0x009D), TLS_RSA_WITH_AES_128_CBC_SHA(0x002F), TLS_RSA_WITH_AES_256_CBC_SHA(0x0035)]",
"compression methods" : "00",
"extensions" : [
"server_name (0)": {
type=host_name (0), value=www.johndoe.de
},
"extended_master_secret (23)": {
<empty>
},
"renegotiation_info (65,281)": {
"renegotiated connection": [<no renegotiated connection>]
},
"supported_groups (10)": {
"versions": [x25519, secp256r1, secp384r1, secp521r1, ffdhe2048, ffdhe3072]
},
"ec_point_formats (11)": {
"formats": [uncompressed]
},
"session_ticket (35)": {
<empty>
},
"application_layer_protocol_negotiation (16)": {
[h2, http/1.1]
},
"status_request (5)": {
"certificate status type": ocsp
"OCSP status request": {
"responder_id": <empty>
"request extensions": {
<empty>
}
}
},
"unknown extension (34)": {
0000: 00 08 04 03 05 03 06 03 02 03 ..........
},
"key_share (51)": {
"client_shares": [
{
"named group": x25519
"key_exchange": {
0000: 34 E2 D6 33 A8 F1 32 BD 77 B3 17 9C DC DB C4 40 4..3..2.w......@
0010: EC 49 D3 05 93 5A 6D 5A CA A1 96 2B 45 C2 C6 08 .I...ZmZ...+E...
}
},
{
"named group": secp256r1
"key_exchange": {
0000: 04 BB 10 DA E8 84 94 DC 5A 20 EC 1B 99 40 68 85 ........Z ...@h.
0010: C2 1E 82 AA E5 F7 C0 9A 8A 98 9C 6E 30 CF 87 34 ...........n0..4
0020: 35 C7 12 B8 DB 43 BB 4E 64 28 83 9B 95 6E 76 31 5....C.Nd(...nv1
0030: EE AA 71 77 7F 58 B5 96 7C 14 75 B4 83 C5 95 42 ..qw.X....u....B
0040: F3
}
},
]
},
"supported_versions (43)": {
"versions": [TLSv1.3, TLSv1.2]
},
"signature_algorithms (13)": {
"signature schemes": [ecdsa_secp256r1_sha256, ecdsa_secp384r1_sha384, ecdsa_secp521r1_sha512, rsa_pss_rsae_sha256, rsa_pss_rsae_sha384, rsa_pss_rsae_sh a512, rsa_pkcs1_sha256, rsa_pkcs1_sha384, rsa_pkcs1_sha512, ecdsa_sha1, rsa_pkcs1_sha1]
},
"psk_key_exchange_modes (45)": {
"ke_modes": [psk_dhe_ke]
},
"unknown extension (28)": {
0000: 40 01 @.
},
"unknown extension (65,037)": {
0000: 00 00 01 00 01 73 00 20 7E E0 E2 0A 3D 5F C1 07 .....s. ....=_..
(cut)
0130: F7 F2 23 E4 18 05 62 88 C5 ..#...b..
}
]
}
)
(I cut the dates here)
58 CEST|SSLExtensions.java:192|Consumed extension: supported_versions
58 CEST|ClientHello.java:838|Negotiated protocol version: TLSv1.2
58 CEST|SessionTicketExtension.java:457|Client accepts session tickets.
58 CEST|SSLExtensions.java:192|Consumed extension: session_ticket
61 CEST|ClientHello.java:1069|Session not resumed.
61 CEST|ServerNameExtension.java:329|no server name matchers, ignore server name indic ation
61 CEST|SSLExtensions.java:192|Consumed extension: server_name
61 CEST|SSLExtensions.java:173|Ignore unavailable extension: max_fragment_length
61 CEST|SSLExtensions.java:192|Consumed extension: status_request
61 CEST|SSLExtensions.java:192|Consumed extension: supported_groups
61 CEST|SSLExtensions.java:192|Consumed extension: ec_point_formats
62 CEST|SSLExtensions.java:192|Consumed extension: signature_algorithms
62 CEST|SSLExtensions.java:173|Ignore unavailable extension: signature_algorithms_cert
62 CEST|AlpnExtension.java:281|Ignore server unenabled extension: application_layer_pr otocol_negotiation
62 CEST|SSLExtensions.java:192|Consumed extension: application_layer_protocol_negotiat ion
62 CEST|SSLExtensions.java:173|Ignore unavailable extension: status_request_v2
62 CEST|SSLExtensions.java:192|Consumed extension: extended_master_secret
62 CEST|SSLExtensions.java:192|Consumed extension: supported_versions
62 CEST|SSLExtensions.java:163|Ignore unsupported extension: cookie
62 CEST|SSLExtensions.java:163|Ignore unsupported extension: psk_key_exchange_modes
62 CEST|SSLExtensions.java:163|Ignore unsupported extension: certificate_authorities
62 CEST|SSLExtensions.java:163|Ignore unsupported extension: key_share
62 CEST|SSLExtensions.java:192|Consumed extension: renegotiation_info
62 CEST|SSLExtensions.java:163|Ignore unsupported extension: pre_shared_key
64 CEST|SSLExtensions.java:215|Ignore impact of unsupported extension: server_name
64 CEST|SSLExtensions.java:207|Ignore unavailable extension: max_fragment_length
66 CEST|SSLExtensions.java:215|Ignore impact of unsupported extension: status_reques t
66 CEST|SSLExtensions.java:215|Ignore impact of unsupported extension: supported_gro ups
66 CEST|SSLExtensions.java:215|Ignore impact of unsupported extension: ec_point_form ats
68 CEST|SSLExtensions.java:224|Populated with extension: signature_algorithms
68 CEST|SSLExtensions.java:207|Ignore unavailable extension: signature_algorithms_cert
68 CEST|SSLExtensions.java:215|Ignore impact of unsupported extension: application_l ayer_protocol_negotiation
68 CEST|SSLExtensions.java:207|Ignore unavailable extension: status_request_v2
68 CEST|SSLExtensions.java:215|Ignore impact of unsupported extension: extended_mast er_secret
68 CEST|SSLExtensions.java:215|Ignore impact of unsupported extension: session_ticke t
68 CEST|SSLExtensions.java:215|Ignore impact of unsupported extension: supported_ver sions
68 CEST|SSLExtensions.java:215|Ignore impact of unsupported extension: renegotiation _info
76 CEST|ServerHello.java:450|use cipher suite TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
77 CEST|StatusResponseManager.java:763|Staping disabled or is a resumed session
CEST|ServerNameExtension.java:454|No expected server name indication response
77 CEST|SSLExtensions.java:260|Ignore, context unavailable extension: server_name
CEST|MaxFragExtension.java:292|Ignore unavailable max_fragment_length extension
77 CEST|SSLExtensions.java:260|Ignore, context unavailable extension: max_fragment_len gth
77 CEST|SSLExtensions.java:260|Ignore, context unavailable extension: status_request
77 CEST|SSLExtensions.java:246|Ignore, no extension producer defined: ec_point_forma ts
77 CEST|AlpnExtension.java:364|Ignore unavailable extension: application_layer_protoco l_negotiation
77 CEST|SSLExtensions.java:260|Ignore, context unavailable extension: application_laye r_protocol_negotiation
77 CEST|SSLExtensions.java:260|Ignore, context unavailable extension: status_request_v 2
77 CEST|ServerHello.java:375|Produced ServerHello handshake message (
"ServerHello": {
"server version" : "TLSv1.2",
"random" : "5F 2C A6 44 25 82 05 4C 46 4A 6D F8 1C 53 E6 93 7A E9 8C F9 AB 30 43 72 4B 7B 7D 2C 4B 91 96 B1",
"session id" : "69 E5 26 55 D8 FE 83 ED 42 EB 24 C9 8C CC 50 C2 0A 5A 0D EB 8E BC CA C3 E0 EE 72 2E 78 19 D3 34",
"cipher suite" : "TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256(0xC02F)",
"compression methods" : "00",
"extensions" : [
"extended_master_secret (23)": {
<empty>
},
"session_ticket (35)": {
<empty>
},
"renegotiation_info (65,281)": {
"renegotiated connection": [<no renegotiated connection>]
}
]
}
)
javax.net.ssl|DEBUG|14|https-jsse-nio2-443-exec-6|2022-08-29 23:07:02.680 CEST|CertificateMessage.java:271|Produced server Certificate handshake message (
"Certificates": [
"certificate" : {
"version" : "v3",
"serial number" : "04 9B FE B0 17 03 95 B8 8F 89 AA 2B AD 04 25 EE 03 22",
"signature algorithm": "SHA256withRSA",
"issuer" : "CN=R3, O=Let's Encrypt, C=US",
"not before" : "2022-08-05 11:32:31.000 CEST",
"not after" : "2022-11-03 10:32:30.000 CET",
"subject" : "CN=www.johndoe.de",
"subject public key" : "RSA",
"extensions" : [
{
ObjectId: 1.3.6.1.4.1.11129.2.4.2 Criticality=false
},
{
ObjectId: 1.3.6.1.5.5.7.1.1 Criticality=false
AuthorityInfoAccess [
[
accessMethod: ocsp
accessLocation: URIName: http://r3.o.lencr.org
,
accessMethod: caIssuers
accessLocation: URIName: http://r3.i.lencr.org/
]
]
},
{
ObjectId: 2.5.29.35 Criticality=false
AuthorityKeyIdentifier [
KeyIdentifier [
0000: 14 2E B3 17 B7 58 56 CB AE 50 09 40 E6 1F AF 9D .....XV..P.@....
0010: 8B 14 C2 C6 ....
]
]
},
{
ObjectId: 2.5.29.19 Criticality=true
BasicConstraints:[
CA:false
PathLen: undefined
]
},
{
ObjectId: 2.5.29.32 Criticality=false
CertificatePolicies [
[CertificatePolicyId: [2.23.140.1.2.1]
[] ]
[CertificatePolicyId: [1.3.6.1.4.1.44947.1.1.1]
[PolicyQualifierInfo: [
qualifierID: 1.3.6.1.5.5.7.2.1
qualifier: 0000: 16 1A 68 74 74 70 3A 2F 2F 63 70 73 2E 6C 65 74 ..http://cps.let
0010: 73 65 6E 63 72 79 70 74 2E 6F 72 67 sencrypt.org
]] ]
]
},
{
ObjectId: 2.5.29.37 Criticality=false
ExtendedKeyUsages [
serverAuth
clientAuth
]
},
{
ObjectId: 2.5.29.15 Criticality=true
KeyUsage [
DigitalSignature
Key_Encipherment
]
},
{
ObjectId: 2.5.29.17 Criticality=false
SubjectAlternativeName [
DNSName: 1.de
DNSName: 2.de
DNSName: 3.de
DNSName: 4.de
DNSName: 5.de
DNSName: 6.de
DNSName: 7.de
DNSName: 8.de
DNSName: 9.de
DNSName: 10.de
DNSName: 11.de
DNSName: www.1.de
DNSName: www.2.de
DNSName: www.3.de
DNSName: www.4.de
DNSName: www.5.de
DNSName: www.6.de
DNSName: www.7.de
DNSName: www.8.de
DNSName: www.9.de
]
},
{
ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: 79 4B FF A1 9A F9 0D 05 F0 06 E2 15 99 93 36 AA yK............6.
0010: 86 E9 14 38 ...8
]
]
}
]},
"certificate" : {
"version" : "v3",
"serial number" : "00 91 2B 08 4A CF 0C 18 A7 53 F6 D6 2E 25 A7 5F 5A",
"signature algorithm": "SHA256withRSA",
"issuer" : "CN=ISRG Root X1, O=Internet Security Research Group, C=US",
"not before" : "2020-09-04 02:00:00.000 CEST",
"not after" : "2025-09-15 18:00:00.000 CEST",
"subject" : "CN=R3, O=Let's Encrypt, C=US",
"subject public key" : "RSA",
"extensions" : [
{
ObjectId: 1.3.6.1.5.5.7.1.1 Criticality=false
AuthorityInfoAccess [
[
accessMethod: caIssuers
accessLocation: URIName: http://x1.i.lencr.org/
]
]
},
{
ObjectId: 2.5.29.35 Criticality=false
AuthorityKeyIdentifier [
KeyIdentifier [
0000: 79 B4 59 E6 7B B6 E5 E4 01 73 80 08 88 C8 1A 58 y.Y......s.....X
0010: F6 E9 9B 6E ...n
]
]
},
{
ObjectId: 2.5.29.19 Criticality=true
BasicConstraints:[
CA:true
PathLen:0
]
},
{
ObjectId: 2.5.29.31 Criticality=false
CRLDistributionPoints [
[DistributionPoint:
[URIName: http://x1.c.lencr.org/]
]]
},
{
ObjectId: 2.5.29.32 Criticality=false
CertificatePolicies [
[CertificatePolicyId: [2.23.140.1.2.1]
[] ]
[CertificatePolicyId: [1.3.6.1.4.1.44947.1.1.1]
[] ]
]
},
{
ObjectId: 2.5.29.37 Criticality=false
ExtendedKeyUsages [
clientAuth
serverAuth
]
},
{
ObjectId: 2.5.29.15 Criticality=true
KeyUsage [
DigitalSignature
Key_CertSign
Crl_Sign
]
},
{
ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: 14 2E B3 17 B7 58 56 CB AE 50 09 40 E6 1F AF 9D .....XV..P.@....
0010: 8B 14 C2 C6 ....
]
]
}
]},
"certificate" : {
"version" : "v3",
"serial number" : "40 01 77 21 37 D4 E9 42 B8 EE 76 AA 3C 64 0A B7",
"signature algorithm": "SHA256withRSA",
"issuer" : "CN=DST Root CA X3, O=Digital Signature Trust Co.",
"not before" : "2021-01-20 20:14:03.000 CET",
"not after" : "2024-09-30 20:14:03.000 CEST",
"subject" : "CN=ISRG Root X1, O=Internet Security Research Group, C=US",
"subject public key" : "RSA",
"extensions" : [
{
ObjectId: 1.3.6.1.5.5.7.1.1 Criticality=false
AuthorityInfoAccess [
[
accessMethod: caIssuers
accessLocation: URIName: http://apps.identrust.com/roots/dstrootcax3.p7c
]
]
},
{
ObjectId: 2.5.29.35 Criticality=false
AuthorityKeyIdentifier [
KeyIdentifier [
0000: C4 A7 B1 A4 7B 2C 71 FA DB E1 4B 90 75 FF C4 15 .....,q...K.u...
0010: 60 85 89 10 `...
]
]
},
{
ObjectId: 2.5.29.19 Criticality=true
BasicConstraints:[
CA:true
PathLen:2147483647
]
},
{
ObjectId: 2.5.29.31 Criticality=false
CRLDistributionPoints [
[DistributionPoint:
[URIName: http://crl.identrust.com/DSTROOTCAX3CRL.crl]
]]
},
{
ObjectId: 2.5.29.32 Criticality=false
CertificatePolicies [
[CertificatePolicyId: [2.23.140.1.2.1]
[] ]
[CertificatePolicyId: [1.3.6.1.4.1.44947.1.1.1]
[PolicyQualifierInfo: [
qualifierID: 1.3.6.1.5.5.7.2.1
qualifier: 0000: 16 22 68 74 74 70 3A 2F 2F 63 70 73 2E 72 6F 6F ."http://cps.roo
0010: 74 2D 78 31 2E 6C 65 74 73 65 6E 63 72 79 70 74 t-x1.letsencrypt
0020: 2E 6F 72 67 .org
]] ]
]
},
{
ObjectId: 2.5.29.15 Criticality=true
KeyUsage [
Key_CertSign
Crl_Sign
]
},
{
ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: 79 B4 59 E6 7B B6 E5 E4 01 73 80 08 88 C8 1A 58 y.Y......s.....X
0010: F6 E9 9B 6E ...n
]
]
}
]}
]
)
javax.net.ssl|DEBUG|14|https-jsse-nio2-443-exec-6|2022-08-29 23:07:02.698 CEST|ECDHServerKeyExchange.java:478|Produced ECDH ServerKeyExchange handshake messa ge (
"ECDH ServerKeyExchange": {
"parameters": {
"named group": "x25519"
"ecdh public": {
0000: 55 2B 68 13 54 7F C8 A8 68 9A 11 D9 5A 07 98 1C U+h.T...h...Z...
0010: D7 33 A1 94 C5 8D A6 D4 97 42 CB E3 E4 C2 71 6D .3.......B....qm
},
},
"digital signature": {
"signature algorithm": "rsa_pss_rsae_sha256"
"signature": {
0000: 5F 8E 31 E3 AE 4A 48 55 F6 15 39 64 CC 52 DA DE _.1..JHU..9d.R..
(cut)
00F0: C6 64 E4 BC 59 99 A4 A1 F3 0A 0D B9 4A C3 45 72 .d..Y.......J.Er
},
}
}
)
javax.net.ssl|DEBUG|14|https-jsse-nio2-443-exec-6|2022-08-29 23:07:02.707 CEST|CertificateRequest.java:618|Produced CertificateRequest handshake message (
"CertificateRequest": {
"certificate types": [ecdsa_sign, rsa_sign, dss_sign]
"supported signature algorithms": [ecdsa_secp256r1_sha256, ecdsa_secp384r1_sha384, ecdsa_secp521r1_sha512, rsa_pss_rsae_sha256, rsa_pss_rsae_sha384, rsa_ps s_rsae_sha512, rsa_pss_pss_sha256, rsa_pss_pss_sha384, rsa_pss_pss_sha512, rsa_pkcs1_sha256, rsa_pkcs1_sha384, rsa_pkcs1_sha512, dsa_sha256, ecdsa_sha224, rs a_sha224, dsa_sha224, ecdsa_sha1, rsa_pkcs1_sha1, dsa_sha1]
"certificate authorities": [CN=USERTrust RSA Certification Authority, O=The USERTRUST Network, L=Jersey City, ST=New Jersey, C=US, CN=admin, OU="[Committer , Admins, Developer, Architect, Wiki editor]", O="[johndoe.de]", C=EN, CN=1.com, OU=Access, O=www.johndoe.de, C=DE, CN=SSL.com DV CA , OU=www.ssl.com, O=SSL.com, C=US, CN=root, OU="[Committer, Developer, Architect]", O="[johndoe.de]", C=EN]
}
)
javax.net.ssl|DEBUG|14|https-jsse-nio2-443-exec-6|2022-08-29 23:07:02.707 CEST|ServerHelloDone.java:97|Produced ServerHelloDone handshake message (
<empty>
)
javax.net.ssl|DEBUG|15|https-jsse-nio2-443-exec-7|2022-08-29 23:07:02.743 CEST|CertificateMessage.java:372|Consuming client Certificate handshake message (
"Certificates": [
"certificate" : {
"version" : "v3",
"serial number" : "1E 30 B0 3C",
"signature algorithm": "SHA256withRSA",
"issuer" : "CN=johndoe.com, OU=Access, O=www.johndoe.com, C=DE",
"not before" : "2000-11-10 24:00:00.000 CET",
"not after" : "2100-11-10 24:00:00.000 CET",
"subject" : "CN=root, OU=[], O=[], C=",
"subject public key" : "RSA",
"extensions" : [
{
ObjectId: 2.5.29.37 Criticality=true
ExtendedKeyUsages [
clientAuth
]
},
{
ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: C7 B9 03 C1 93 32 B4 A0 7B 53 B8 E1 03 E4 4B 37 .....2...S....K7
0010: 20 FA 9E DF ...
]
]
}
]}
]
)
javax.net.ssl|ERROR|15|https-jsse-nio2-443-exec-7|2022-08-29 23:07:02.746 CEST|TransportContext.java:361|Fatal (CERTIFICATE_UNKNOWN): PKIX path validation fa iled: java.security.cert.CertPathValidatorException: signature check failed (
"throwable" : {
sun.security.validator.ValidatorException: PKIX path validation failed: java.security.cert.CertPathValidatorException: signature check failed
at java.base/sun.security.validator.PKIXValidator.doValidate(PKIXValidator.java:369)
at java.base/sun.security.validator.PKIXValidator.engineValidate(PKIXValidator.java:275)
at java.base/sun.security.validator.Validator.validate(Validator.java:264)
at java.base/sun.security.ssl.X509TrustManagerImpl.checkTrusted(X509TrustManagerImpl.java:285)
Caused by: java.security.cert.CertPathValidatorException: signature check failed
at java.base/sun.security.provider.certpath.PKIXMasterCertPathValidator.validate(PKIXMasterCertPathValidator.java:135)
... 29 more
Caused by: java.security.SignatureException: Signature does not match.
at java.base/sun.security.x509.X509CertImpl.verify(X509CertImpl.java:412)
at java.base/sun.security.provider.certpath.BasicChecker.verifySignature(BasicChecker.java:166)
... 34 more}
)
javax.net.ssl|WARNING|15|https-jsse-nio2-443-exec-7|2022-08-29 23:07:02.746 CEST|SSLEngineOutputRecord.java:173|outbound has closed, ignore outbound applicat ion data有趣的是:在一个匿名标签上,它就像一种魅力!
以下是我的服务器配置:配置
回答 3
Stack Overflow用户
发布于 2022-09-06 15:14:11
正如评论中所述,这个问题不再是可再生的了。因此,我将尝试分析一些可能的原因,问题与我的知识,当然也是有关张贴日志。
让我们从日志的第一行开始,从这一点我们可以看出,有些东西有点奇怪,因为rm2.johndoe.de是机器的$HOSTNAME,机器是为www.e-nexus.de服务的。但是,这既不能直接影响SSL证书过程,也不能影响Linux服务器(我不知道Windows服务器)上的DNS记录,而systemd和systemd解析为DNS解析服务器。根据man systemd-resolvd.service,$HOSTNAME被解析为127.0.0.1。
[root@rm-2 130 rm2.johndoe.de /usr/local/share/apache-tomcat-8.5.50/logs]# tail -f catalina.out一切看起来都很好,它使用的是TLS1.2和一些不支持的TLS扩展。我们必须在这里注意到,相关问题中的屏幕截图表明firefox试图使用TLS1.3,并且它正确地协商了一个密码套件,这可能意味着我们看到的日志与截图的tls连接不同。我们将主要关注服务器端,因为我们没有太多关于客户端的信息。
javax.net.ssl|DEBUG|14|https-jsse-nio2-443-exec-6|2022-08-29 23:07:02.639 CEST|HandshakeContext.java:305|No available cipher suite for TLS10
javax.net.ssl|DEBUG|14|https-jsse-nio2-443-exec-6|2022-08-29 23:07:02.640 CEST|HandshakeContext.java:305|No available cipher suite for TLS13
javax.net.ssl|DEBUG|14|https-jsse-nio2-443-exec-6|2022-08-29 23:07:02.642 CEST|HandshakeContext.java:305|No available cipher suite for TLS11
javax.net.ssl|DEBUG|14|https-jsse-nio2-443-exec-6|2022-08-29 23:07:02.646 CEST|SSLExtensions.java:135|Ignore unknown or unsupported extension (
"unknown extension (34)": {
0000: 00 08 04 03 05 03 06 03 02 03 ..........
}
)
javax.net.ssl|DEBUG|14|https-jsse-nio2-443-exec-6|2022-08-29 23:07:02.647 CEST|SSLExtensions.java:135|Ignore unknown or unsupported extension (
"unknown extension (28)": {
0000: 40 01 @.
}
)
javax.net.ssl|DEBUG|14|https-jsse-nio2-443-exec-6|2022-08-29 23:07:02.647 CEST|SSLExtensions.java:135|Ignore unknown or unsupported extension (
"unknown extension (65,037)": {
0000: 00 00 01 00 01 73 00 20 7E E0 E2 0A 3D 5F C1 07 .....s. ....=_..
(cut)
0130: F7 F2 23 E4 18 05 62 88 C5 ..#...b..
}
)现在我们开始发现第一个问题,server_name是来自客户端的www.johndoe.de。如果客户端请求www.e-nexus.de,则server_name不匹配。据我理解,这与DNS缓存是否过时无关。我还认为,这有可能是与Firefox浏览器的缓存相关的客户端错误,正如刷新用户配置文件的注释中所指出的那样,该漏洞修复了问题。
javax.net.ssl|DEBUG|14|https-jsse-nio2-443-exec-6|2022-08-29 23:07:02.657 CEST|ClientHello.java:808|Consuming ClientHello handshake message (
"ClientHello": {
"client version" : "TLSv1.2",
"random" : "D2 14 7F AA BE 53 DC 45 28 1E F1 DE CE 5C 47 E9 74 AA B6 4D 71 77 05 90 D6 E5 15 E3 47 09 D1 4C",
"session id" : "2C 40 BF 69 27 7A 56 9B C3 E1 D2 B0 7E DA 21 0A 7E 28 DE 2B 9C 13 18 A8 7E 63 78 5B A2 AB 7C C8",
"cipher suites" : "[TLS_AES_128_GCM_SHA256(0x1301), TLS_CHACHA20_POLY1305_SHA256(0x1303), TLS_AES_256_GCM_SHA384(0x1302), TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256(0xC02B), TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256(0xC02F), TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305_SHA256(0xCCA9), TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256(0xCCA8), TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384(0xC02C), TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384(0xC030), TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA(0xC00A), TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA(0xC009), TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA(0xC013), TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA(0xC014)TLS_RSA_WITH_AES_128_GCM_SHA256(0x009C), TLS_RSA_WITH_AES_256_GCM_SHA384(0x009D), TLS_RSA_WITH_AES_128_CBC_SHA(0x002F), TLS_RSA_WITH_AES_256_CBC_SHA(0x0035)]",
"compression methods" : "00",
"extensions" : [
"server_name (0)": {
type=host_name (0), value=www.johndoe.de
},
"extended_master_secret (23)": {
<empty>
},
"renegotiation_info (65,281)": {
"renegotiated connection": [<no renegotiated connection>]
},
"supported_groups (10)": {
"versions": [x25519, secp256r1, secp384r1, secp521r1, ffdhe2048, ffdhe3072]
},
"ec_point_formats (11)": {
"formats": [uncompressed]
},
"session_ticket (35)": {
<empty>
},
"application_layer_protocol_negotiation (16)": {
[h2, http/1.1]
},
"status_request (5)": {
"certificate status type": ocsp
"OCSP status request": {
"responder_id": <empty>
"request extensions": {
<empty>
}
}
},
"unknown extension (34)": {
0000: 00 08 04 03 05 03 06 03 02 03 ..........
},
"key_share (51)": {
"client_shares": [
{
"named group": x25519
"key_exchange": {
0000: 34 E2 D6 33 A8 F1 32 BD 77 B3 17 9C DC DB C4 40 4..3..2.w......@
0010: EC 49 D3 05 93 5A 6D 5A CA A1 96 2B 45 C2 C6 08 .I...ZmZ...+E...
}
},
{
"named group": secp256r1
"key_exchange": {
0000: 04 BB 10 DA E8 84 94 DC 5A 20 EC 1B 99 40 68 85 ........Z ...@h.
0010: C2 1E 82 AA E5 F7 C0 9A 8A 98 9C 6E 30 CF 87 34 ...........n0..4
0020: 35 C7 12 B8 DB 43 BB 4E 64 28 83 9B 95 6E 76 31 5....C.Nd(...nv1
0030: EE AA 71 77 7F 58 B5 96 7C 14 75 B4 83 C5 95 42 ..qw.X....u....B
0040: F3
}
},
]
},
"supported_versions (43)": {
"versions": [TLSv1.3, TLSv1.2]
},
"signature_algorithms (13)": {
"signature schemes": [ecdsa_secp256r1_sha256, ecdsa_secp384r1_sha384, ecdsa_secp521r1_sha512, rsa_pss_rsae_sha256, rsa_pss_rsae_sha384, rsa_pss_rsae_sh a512, rsa_pkcs1_sha256, rsa_pkcs1_sha384, rsa_pkcs1_sha512, ecdsa_sha1, rsa_pkcs1_sha1]
},
"psk_key_exchange_modes (45)": {
"ke_modes": [psk_dhe_ke]
},
"unknown extension (28)": {
0000: 40 01 @.
},
"unknown extension (65,037)": {
0000: 00 00 01 00 01 73 00 20 7E E0 E2 0A 3D 5F C1 07 .....s. ....=_..
(cut)
0130: F7 F2 23 E4 18 05 62 88 C5 ..#...b..
}
]
}
)在日志的下一部分,一切看起来都很好。请注意,TLS1.2是协商的。
(I cut the dates here)
58 CEST|SSLExtensions.java:192|Consumed extension: supported_versions
58 CEST|ClientHello.java:838|Negotiated protocol version: TLSv1.2
58 CEST|SessionTicketExtension.java:457|Client accepts session tickets.
58 CEST|SSLExtensions.java:192|Consumed extension: session_ticket
61 CEST|ClientHello.java:1069|Session not resumed.
61 CEST|ServerNameExtension.java:329|no server name matchers, ignore server name indication
61 CEST|SSLExtensions.java:192|Consumed extension: server_name
61 CEST|SSLExtensions.java:173|Ignore unavailable extension: max_fragment_length
61 CEST|SSLExtensions.java:192|Consumed extension: status_request
61 CEST|SSLExtensions.java:192|Consumed extension: supported_groups
61 CEST|SSLExtensions.java:192|Consumed extension: ec_point_formats
62 CEST|SSLExtensions.java:192|Consumed extension: signature_algorithms
62 CEST|SSLExtensions.java:173|Ignore unavailable extension: signature_algorithms_cert
62 CEST|AlpnExtension.java:281|Ignore server unenabled extension: application_layer_protocol_negotiation
62 CEST|SSLExtensions.java:192|Consumed extension: application_layer_protocol_negotiation
62 CEST|SSLExtensions.java:173|Ignore unavailable extension: status_request_v2
62 CEST|SSLExtensions.java:192|Consumed extension: extended_master_secret
62 CEST|SSLExtensions.java:192|Consumed extension: supported_versions
62 CEST|SSLExtensions.java:163|Ignore unsupported extension: cookie
62 CEST|SSLExtensions.java:163|Ignore unsupported extension: psk_key_exchange_modes
62 CEST|SSLExtensions.java:163|Ignore unsupported extension: certificate_authorities
62 CEST|SSLExtensions.java:163|Ignore unsupported extension: key_share
62 CEST|SSLExtensions.java:192|Consumed extension: renegotiation_info
62 CEST|SSLExtensions.java:163|Ignore unsupported extension: pre_shared_key
64 CEST|SSLExtensions.java:215|Ignore impact of unsupported extension: server_name
64 CEST|SSLExtensions.java:207|Ignore unavailable extension: max_fragment_length
66 CEST|SSLExtensions.java:215|Ignore impact of unsupported extension: status_request
66 CEST|SSLExtensions.java:215|Ignore impact of unsupported extension: supported_groups
66 CEST|SSLExtensions.java:215|Ignore impact of unsupported extension: ec_point_formats
68 CEST|SSLExtensions.java:224|Populated with extension: signature_algorithms
68 CEST|SSLExtensions.java:207|Ignore unavailable extension: signature_algorithms_cert
68 CEST|SSLExtensions.java:215|Ignore impact of unsupported extension: application_layer_protocol_negotiation
68 CEST|SSLExtensions.java:207|Ignore unavailable extension: status_request_v2
68 CEST|SSLExtensions.java:215|Ignore impact of unsupported extension: extended_master_secret
68 CEST|SSLExtensions.java:215|Ignore impact of unsupported extension: session_ticket
68 CEST|SSLExtensions.java:215|Ignore impact of unsupported extension: supported_versions
68 CEST|SSLExtensions.java:215|Ignore impact of unsupported extension: renegotiation_info
76 CEST|ServerHello.java:450|use cipher suite TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
77 CEST|StatusResponseManager.java:763|Staping disabled or is a resumed session
CEST|ServerNameExtension.java:454|No expected server name indication response
77 CEST|SSLExtensions.java:260|Ignore, context unavailable extension: server_name
CEST|MaxFragExtension.java:292|Ignore unavailable max_fragment_length extension
77 CEST|SSLExtensions.java:260|Ignore, context unavailable extension: max_fragment_length
77 CEST|SSLExtensions.java:260|Ignore, context unavailable extension: status_request
77 CEST|SSLExtensions.java:246|Ignore, no extension producer defined: ec_point_formats
77 CEST|AlpnExtension.java:364|Ignore unavailable extension: application_layer_protocol_negotiation
77 CEST|SSLExtensions.java:260|Ignore, context unavailable extension: application_layer_protocol_negotiation
77 CEST|SSLExtensions.java:260|Ignore, context unavailable extension: status_request_v2
77 CEST|ServerHello.java:375|Produced ServerHello handshake message (
"ServerHello": {
"server version" : "TLSv1.2",
"random" : "5F 2C A6 44 25 82 05 4C 46 4A 6D F8 1C 53 E6 93 7A E9 8C F9 AB 30 43 72 4B 7B 7D 2C 4B 91 96 B1",
"session id" : "69 E5 26 55 D8 FE 83 ED 42 EB 24 C9 8C CC 50 C2 0A 5A 0D EB 8E BC CA C3 E0 EE 72 2E 78 19 D3 34",
"cipher suite" : "TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256(0xC02F)",
"compression methods" : "00",
"extensions" : [
"extended_master_secret (23)": {
<empty>
},
"session_ticket (35)": {
<empty>
},
"renegotiation_info (65,281)": {
"renegotiated connection": [<no renegotiated connection>]
}
]
}
)这里有很多问题,因为服务器发送了错误的证书,也许旧的证书在配置中被遗忘了。证书链的其余部分似乎是合法的。
javax.net.ssl|DEBUG|14|https-jsse-nio2-443-exec-6|2022-08-29 23:07:02.680 CEST|CertificateMessage.java:271|Produced server Certificate handshake message (
"Certificates": [
"certificate" : {
"version" : "v3",
"serial number" : "04 9B FE B0 17 03 95 B8 8F 89 AA 2B AD 04 25 EE 03 22",
"signature algorithm": "SHA256withRSA",
"issuer" : "CN=R3, O=Let's Encrypt, C=US",
"not before" : "2022-08-05 11:32:31.000 CEST",
"not after" : "2022-11-03 10:32:30.000 CET",
"subject" : "CN=www.johndoe.de",
"subject public key" : "RSA",
"extensions" : [
{
ObjectId: 1.3.6.1.4.1.11129.2.4.2 Criticality=false
},
{
ObjectId: 1.3.6.1.5.5.7.1.1 Criticality=false
AuthorityInfoAccess [
[
accessMethod: ocsp
accessLocation: URIName: http://r3.o.lencr.org
,
accessMethod: caIssuers
accessLocation: URIName: http://r3.i.lencr.org/
]
]
},
{
ObjectId: 2.5.29.35 Criticality=false
AuthorityKeyIdentifier [
KeyIdentifier [
0000: 14 2E B3 17 B7 58 56 CB AE 50 09 40 E6 1F AF 9D .....XV..P.@....
0010: 8B 14 C2 C6 ....
]
]
},
{
ObjectId: 2.5.29.19 Criticality=true
BasicConstraints:[
CA:false
PathLen: undefined
]
},
{
ObjectId: 2.5.29.32 Criticality=false
CertificatePolicies [
[CertificatePolicyId: [2.23.140.1.2.1]
[] ]
[CertificatePolicyId: [1.3.6.1.4.1.44947.1.1.1]
[PolicyQualifierInfo: [
qualifierID: 1.3.6.1.5.5.7.2.1
qualifier: 0000: 16 1A 68 74 74 70 3A 2F 2F 63 70 73 2E 6C 65 74 ..http://cps.let
0010: 73 65 6E 63 72 79 70 74 2E 6F 72 67 sencrypt.org
]] ]
]
},
{
ObjectId: 2.5.29.37 Criticality=false
ExtendedKeyUsages [
serverAuth
clientAuth
]
},
{
ObjectId: 2.5.29.15 Criticality=true
KeyUsage [
DigitalSignature
Key_Encipherment
]
},
{
ObjectId: 2.5.29.17 Criticality=false
SubjectAlternativeName [
DNSName: 1.de
DNSName: 2.de
DNSName: 3.de
DNSName: 4.de
DNSName: 5.de
DNSName: 6.de
DNSName: 7.de
DNSName: 8.de
DNSName: 9.de
DNSName: 10.de
DNSName: 11.de
DNSName: www.1.de
DNSName: www.2.de
DNSName: www.3.de
DNSName: www.4.de
DNSName: www.5.de
DNSName: www.6.de
DNSName: www.7.de
DNSName: www.8.de
DNSName: www.9.de
]
},
{
ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: 79 4B FF A1 9A F9 0D 05 F0 06 E2 15 99 93 36 AA yK............6.
0010: 86 E9 14 38 ...8
]
]
}
]},
"certificate" : {
"version" : "v3",
"serial number" : "00 91 2B 08 4A CF 0C 18 A7 53 F6 D6 2E 25 A7 5F 5A",
"signature algorithm": "SHA256withRSA",
"issuer" : "CN=ISRG Root X1, O=Internet Security Research Group, C=US",
"not before" : "2020-09-04 02:00:00.000 CEST",
"not after" : "2025-09-15 18:00:00.000 CEST",
"subject" : "CN=R3, O=Let's Encrypt, C=US",
"subject public key" : "RSA",
"extensions" : [
{
ObjectId: 1.3.6.1.5.5.7.1.1 Criticality=false
AuthorityInfoAccess [
[
accessMethod: caIssuers
accessLocation: URIName: http://x1.i.lencr.org/
]
]
},
{
ObjectId: 2.5.29.35 Criticality=false
AuthorityKeyIdentifier [
KeyIdentifier [
0000: 79 B4 59 E6 7B B6 E5 E4 01 73 80 08 88 C8 1A 58 y.Y......s.....X
0010: F6 E9 9B 6E ...n
]
]
},
{
ObjectId: 2.5.29.19 Criticality=true
BasicConstraints:[
CA:true
PathLen:0
]
},
{
ObjectId: 2.5.29.31 Criticality=false
CRLDistributionPoints [
[DistributionPoint:
[URIName: http://x1.c.lencr.org/]
]]
},
{
ObjectId: 2.5.29.32 Criticality=false
CertificatePolicies [
[CertificatePolicyId: [2.23.140.1.2.1]
[] ]
[CertificatePolicyId: [1.3.6.1.4.1.44947.1.1.1]
[] ]
]
},
{
ObjectId: 2.5.29.37 Criticality=false
ExtendedKeyUsages [
clientAuth
serverAuth
]
},
{
ObjectId: 2.5.29.15 Criticality=true
KeyUsage [
DigitalSignature
Key_CertSign
Crl_Sign
]
},
{
ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: 14 2E B3 17 B7 58 56 CB AE 50 09 40 E6 1F AF 9D .....XV..P.@....
0010: 8B 14 C2 C6 ....
]
]
}
]},
"certificate" : {
"version" : "v3",
"serial number" : "40 01 77 21 37 D4 E9 42 B8 EE 76 AA 3C 64 0A B7",
"signature algorithm": "SHA256withRSA",
"issuer" : "CN=DST Root CA X3, O=Digital Signature Trust Co.",
"not before" : "2021-01-20 20:14:03.000 CET",
"not after" : "2024-09-30 20:14:03.000 CEST",
"subject" : "CN=ISRG Root X1, O=Internet Security Research Group, C=US",
"subject public key" : "RSA",
"extensions" : [
{
ObjectId: 1.3.6.1.5.5.7.1.1 Criticality=false
AuthorityInfoAccess [
[
accessMethod: caIssuers
accessLocation: URIName: http://apps.identrust.com/roots/dstrootcax3.p7c
]
]
},
{
ObjectId: 2.5.29.35 Criticality=false
AuthorityKeyIdentifier [
KeyIdentifier [
0000: C4 A7 B1 A4 7B 2C 71 FA DB E1 4B 90 75 FF C4 15 .....,q...K.u...
0010: 60 85 89 10 `...
]
]
},
{
ObjectId: 2.5.29.19 Criticality=true
BasicConstraints:[
CA:true
PathLen:2147483647
]
},
{
ObjectId: 2.5.29.31 Criticality=false
CRLDistributionPoints [
[DistributionPoint:
[URIName: http://crl.identrust.com/DSTROOTCAX3CRL.crl]
]]
},
{
ObjectId: 2.5.29.32 Criticality=false
CertificatePolicies [
[CertificatePolicyId: [2.23.140.1.2.1]
[] ]
[CertificatePolicyId: [1.3.6.1.4.1.44947.1.1.1]
[PolicyQualifierInfo: [
qualifierID: 1.3.6.1.5.5.7.2.1
qualifier: 0000: 16 22 68 74 74 70 3A 2F 2F 63 70 73 2E 72 6F 6F ."http://cps.roo
0010: 74 2D 78 31 2E 6C 65 74 73 65 6E 63 72 79 70 74 t-x1.letsencrypt
0020: 2E 6F 72 67 .org
]] ]
]
},
{
ObjectId: 2.5.29.15 Criticality=true
KeyUsage [
Key_CertSign
Crl_Sign
]
},
{
ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: 79 B4 59 E6 7B B6 E5 E4 01 73 80 08 88 C8 1A 58 y.Y......s.....X
0010: F6 E9 9B 6E ...n
]
]
}
]}
]
)ECDH参数是从服务器发送的,一切看起来都很好。
javax.net.ssl|DEBUG|14|https-jsse-nio2-443-exec-6|2022-08-29 23:07:02.698 CEST|ECDHServerKeyExchange.java:478|Produced ECDH ServerKeyExchange handshake message (
"ECDH ServerKeyExchange": {
"parameters": {
"named group": "x25519"
"ecdh public": {
0000: 55 2B 68 13 54 7F C8 A8 68 9A 11 D9 5A 07 98 1C U+h.T...h...Z...
0010: D7 33 A1 94 C5 8D A6 D4 97 42 CB E3 E4 C2 71 6D .3.......B....qm
},
},
"digital signature": {
"signature algorithm": "rsa_pss_rsae_sha256"
"signature": {
0000: 5F 8E 31 E3 AE 4A 48 55 F6 15 39 64 CC 52 DA DE _.1..JHU..9d.R..
(cut)
00F0: C6 64 E4 BC 59 99 A4 A1 F3 0A 0D B9 4A C3 45 72 .d..Y.......J.Er
},
}
}
)现在,服务器向客户端请求客户端证书,这可能是由certificateVerification of 配置引起的。格式有点奇怪,但我不认为他把自己列为CA。然后服务器就完成了他的部分。
javax.net.ssl|DEBUG|14|https-jsse-nio2-443-exec-6|2022-08-29 23:07:02.707 CEST|CertificateRequest.java:618|Produced CertificateRequest handshake message (
"CertificateRequest": {
"certificate types": [ecdsa_sign, rsa_sign, dss_sign]
"supported signature algorithms": [ecdsa_secp256r1_sha256, ecdsa_secp384r1_sha384, ecdsa_secp521r1_sha512, rsa_pss_rsae_sha256, rsa_pss_rsae_sha384,rsa_pss_rsae_sha512, rsa_pss_pss_sha256, rsa_pss_pss_sha384, rsa_pss_pss_sha512, rsa_pkcs1_sha256, rsa_pkcs1_sha384, rsa_pkcs1_sha512, dsa_sha256, ecdsa_sha224, rsa_sha224, dsa_sha224, ecdsa_sha1, rsa_pkcs1_sha1, dsa_sha1]
"certificate authorities": [CN=USERTrust RSA Certification Authority, O=The USERTRUST Network, L=Jersey City, ST=New Jersey, C=US, CN=admin, OU="[Committer, Admins, Developer, Architect, Wiki editor]", O="[johndoe.de]", C=EN, CN=1.com, OU=Access, O=www.johndoe.de, C=DE, CN=SSL.com DV CA, OU=www.ssl.com, O=SSL.com, C=US, CN=root, OU="[Committer, Developer, Architect]", O="[johndoe.de]", C=EN]
}
)
javax.net.ssl|DEBUG|14|https-jsse-nio2-443-exec-6|2022-08-29 23:07:02.707 CEST|ServerHelloDone.java:97|Produced ServerHelloDone handshake message (
<empty>
)客户端将证书发回。据我所知,证书可能是自签名的,但证书颁发机构的DistinguishedName与服务器可以接受的证书certificate authorities不匹配,并且在这异常情况下失败,这异常信息不多,表明证书链不受信任。甚至CN=johndoe.com而不是johndoe.de。
javax.net.ssl|DEBUG|15|https-jsse-nio2-443-exec-7|2022-08-29 23:07:02.743 CEST|CertificateMessage.java:372|Consuming client Certificate handshake message (
"Certificates": [
"certificate" : {
"version" : "v3",
"serial number" : "1E 30 B0 3C",
"signature algorithm": "SHA256withRSA",
"issuer" : "CN=johndoe.com, OU=Access, O=www.johndoe.com, C=DE",
"not before" : "2000-11-10 24:00:00.000 CET",
"not after" : "2100-11-10 24:00:00.000 CET",
"subject" : "CN=root, OU=[], O=[], C=",
"subject public key" : "RSA",
"extensions" : [
{
ObjectId: 2.5.29.37 Criticality=true
ExtendedKeyUsages [
clientAuth
]
},
{
ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: C7 B9 03 C1 93 32 B4 A0 7B 53 B8 E1 03 E4 4B 37 .....2...S....K7
0010: 20 FA 9E DF ...
]
]
}
]}
]
)
javax.net.ssl|ERROR|15|https-jsse-nio2-443-exec-7|2022-08-29 23:07:02.746 CEST|TransportContext.java:361|Fatal (CERTIFICATE_UNKNOWN): PKIX path validation failed: java.security.cert.CertPathValidatorException: signature check failed (
"throwable" : {
sun.security.validator.ValidatorException: PKIX path validation failed: java.security.cert.CertPathValidatorException: signature check failed
at java.base/sun.security.validator.PKIXValidator.doValidate(PKIXValidator.java:369)
at java.base/sun.security.validator.PKIXValidator.engineValidate(PKIXValidator.java:275)
at java.base/sun.security.validator.Validator.validate(Validator.java:264)
at java.base/sun.security.ssl.X509TrustManagerImpl.checkTrusted(X509TrustManagerImpl.java:285)
Caused by: java.security.cert.CertPathValidatorException: signature check failed
at java.base/sun.security.provider.certpath.PKIXMasterCertPathValidator.validate(PKIXMasterCertPathValidator.java:135)
... 29 more
Caused by: java.security.SignatureException: Signature does not match.
at java.base/sun.security.x509.X509CertImpl.verify(X509CertImpl.java:412)
at java.base/sun.security.provider.certpath.BasicChecker.verifySignature(BasicChecker.java:166)
... 34 more}
)
javax.net.ssl|WARNING|15|https-jsse-nio2-443-exec-7|2022-08-29 23:07:02.746 CEST|SSLEngineOutputRecord.java:173|outbound has closed, ignore outbound application dataTLDR :虽然客户端没有太多关于这个问题的信息,而且OP可能也在尝试连接到发布的屏幕截图中服务器的不同配置。根据发布的日志,服务器的行为是正确的,因此客户端可能有问题,而且很可能与Firefox缓存有关,但我们没有更多的信息需要解决。
Stack Overflow用户
发布于 2022-09-06 10:04:34
看来你的证书没什么问题。证明:https://www.ssllabs.com/ssltest/analyze.html?d=www.e-nexus.de
该问题与为http请求提供页面有关。(没有https的"s“。)
当您试图导航到http://www.e-nexus.de/时,所有浏览器都会通知连接不安全。另一方面,当您尝试使用*//www.e-necus.de/时,它会如您所期望的那样工作。
所以浏览器的行为都是正确的。(全部适用于Chrome、Edge和Firefox,而且都具有正常/匿名模式。)
作为一种解决方案,在您的web服务器中,将所有http调用定向到https (除了重定向响应之外,永远不提供http页面)就足够了。
Stack Overflow用户
发布于 2022-09-05 17:11:18
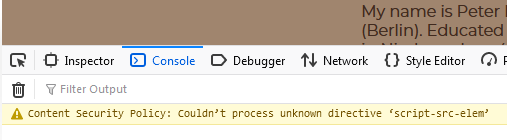
使用Firefox104.0.1与https://www.e-nexus.de,火狐的检查“控制台”选项卡显示这条消息。这个页面错误和其他页面错误可能需要解决,这样才能在Firefox浏览器中工作。
Content Security Policy: Couldn't process unknown directive 'script-src-elem'
https://stackoverflow.com/questions/73535019
复制相似问题

