解析AssumeRoleWithWebIdentity
解析AssumeRoleWithWebIdentity
提问于 2022-11-08 19:52:05
在本指南之后,我无法解决最后的第五步,该步骤在以下情况下失败:
An error occurred (AccessDenied) when calling the AssumeRoleWithWebIdentity operation: Not authorized to perform sts:AssumeRoleWithWebIdentity
command terminated with exit code 254我的最终目标是让特定名称空间中的boto3客户机执行EC2操作。我认为我的角色,RBAC,或者我使用的arn是不正确的。我的舱单在底部。
编辑:我在舱内得到AWS env,见图。
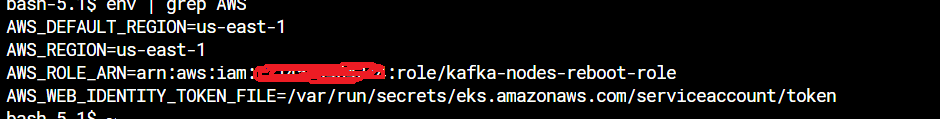
我的角色:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Federated": "arn:aws:iam::<account_number>:oidc-provider/oidc.eks.us-east-1.amazonaws.com/id/<oidc_number>"
},
"Action": "sts:AssumeRoleWithWebIdentity",
"Condition": {
"StringEquals": {
"oidc.eks.us-east-1.amazonaws.com/id/<oidc_number>:sub": "system:serviceaccount:reporting-analytics-services-kafka-tools:",
"oidc.eks.us-east-1.amazonaws.com/id/<oidc_number>:aud": "sts.amazonaws.com"
}
}
}
]
}我的政策(附在这个角色上,我知道现在太过分了):
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ssm:*",
"sts:*",
"ec2:describeInstances",
"ec2:stopInstances",
"ec2:startInstances",
"iam:ListRoles"
],
"Resource": "*"
}
]
}这就是我的部署文件的样子。
---
# Source: kafka-tools-pod/templates/service.yaml
apiVersion: v1
kind: Service
metadata:
labels:
app: test-pod
name: test-pod
namespace: reporting-analytics-services-kafka-tools
spec:
ports:
- port: 8080
selector:
app: test-pod
---
# Source: kafka-tools-pod/templates/deployment.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
labels:
app: test-pod
name: test-pod
namespace: reporting-analytics-services-kafka-tools
spec:
replicas: 3
revisionHistoryLimit: 3
selector:
matchLabels:
app: test-pod
strategy:
rollingUpdate:
maxSurge: 0
maxUnavailable: 1
template:
metadata:
labels:
app: test-pod
annotations:
Error: "invalid character '$' looking for beginning of value"
spec:
serviceAccountName: kafka-tools-pod-service-account
containers:
- envFrom:
- configMapRef:
name: kafka-tools-pod-env
image: <somenumber>.dkr.ecr.us-east-1.amazonaws.com/kafka-testing:latest
imagePullPolicy: IfNotPresent
name: test-pod
ports:
- containerPort: 8080
resources:
limits:
cpu: 1500m
memory: 3Gi
requests:
cpu: 350m
memory: 128Mi
---
# Source: kafka-tools-pod/templates/ingress-internal.yaml
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
annotations:
kubernetes.io/ingress.class: internal-nginx
name: kafka-tools-pod-internal
namespace: reporting-analytics-services-kafka-tools
spec:
rules:
- host: mycompany.use1.develop.percipio.aws
http:
paths:
- backend:
service:
name: test-pod
port:
number: 8080
path: /
pathType: Prefix
---
# Source: kafka-tools-pod/templates/verticalpodautoscaler.yaml
apiVersion: autoscaling.k8s.io/v1
kind: VerticalPodAutoscaler
metadata:
labels:
app: test-pod
name: test-pod
namespace: reporting-analytics-services-kafka-tools
spec:
targetRef:
apiVersion: apps/v1
kind: Deployment
name: test-pod
updatePolicy:
updateMode: 'Off'
---
apiVersion: v1
kind: ServiceAccount
metadata:
name: kafka-tools-pod-service-account
namespace: reporting-analytics-services-kafka-tools
annotations:
eks.amazonaws.com/role-arn: arn:aws:iam::<myaccount>:role/kafka-nodes-reboot-role
---
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
name: kakfa-tools-pod-role
rules:
- apiGroups: [""]
resources: ["*"]
verbs: ["*"]
- apiGroups: ["extensions"]
resources: ["*"]
verbs: ["*"]
- apiGroups: ["apps"]
resources: ["*"]
verbs: ["*"]
---
kind: RoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: kakfa-tools-pod-role-binding
subjects:
- kind: ServiceAccount
name: kafka-tools-pod-service-account
namespace: reporting-analytics-services-kafka-tools
roleRef:
kind: Role
name: kakfa-tools-pod-role
apiGroup: rbac.authorization.k8s.io回答 1
Stack Overflow用户
回答已采纳
发布于 2022-11-10 17:35:32
有几样东西帮助解决了这个问题。
- 将
"sts:AssumeRole"添加到策略中。 - 正如@jordanm所建议的那样,将arn编辑到精确的吊舱。
- 角色和roleBinding配置错误:
---
apiVersion: v1
kind: ServiceAccount
metadata:
name: kafka-tools-pod-service-account
namespace: reporting-analytics-services-kafka-tools
annotations:
eks.amazonaws.com/role-arn: arn:aws:iam::<accountnumber>:role/KafkaRebootRole
eks.amazonaws.com/audience: "sts.amazonaws.com"
---
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
name: kafka-role
namespace: reporting-analytics-services-kafka-tools
rules:
- apiGroups:
- ""
- apps
- autoscaling
- batch
- extensions
- policy
- rbac.authorization.k8s.io
resources:
- pods
- componentstatuses
- configmaps
- daemonsets
- deployments
- events
- endpoints
- horizontalpodautoscalers
- ingress
- jobs
- limitranges
- namespaces
- nodes
- pods
- persistentvolumes
- persistentvolumeclaims
- resourcequotas
- replicasets
- replicationcontrollers
- serviceaccounts
- services
verbs: ["get", "list", "watch", "create", "update", "patch", "delete"]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: kafka-rolebinding
namespace: reporting-analytics-services-kafka-tools
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: kafka-role
subjects:
- namespace: reporting-analytics-services-kafka-tools
kind: ServiceAccount
name: kafka-tools-pod-service-account在此之后,在吊舱中运行aws sts get-caller-identity或使用boto3客户端完成我需要它的一切工作。
页面原文内容由Stack Overflow提供。腾讯云小微IT领域专用引擎提供翻译支持
原文链接:
https://stackoverflow.com/questions/74366391
复制相关文章
相似问题

