服务器hello完成后的TLS握手错误
服务器hello完成后的TLS握手错误
提问于 2020-05-10 12:30:18
我有一个python应用程序正在连接到一个java应用程序,两者都使用相同的证书。此证书也在双方的可信证书中导入。
使用自签名证书验证了整个TLS握手过程的功能。
但是,当我想要使用全局CA签名的证书时,遇到握手错误:
这是我通过在服务器端(java应用程序)上启用-Djavax.net.debug=ssl,handshake获得的SSL日志:
.
.
.
***
update handshake state: certificate[11]
upcoming handshake states: server_key_exchange[12](optional)
upcoming handshake states: certificate_request[13](optional)
upcoming handshake states: server_hello_done[14]
upcoming handshake states: client certificate[11](optional)
upcoming handshake states: client_key_exchange[16]
upcoming handshake states: certificate_verify[15](optional)
upcoming handshake states: client change_cipher_spec[-1]
upcoming handshake states: client finished[20]
upcoming handshake states: server change_cipher_spec[-1]
upcoming handshake states: server finished[20]
*** ECDH ServerKeyExchange
Signature Algorithm SHA256withRSA
Server key: Sun EC public key, 256 bits
public x coord: xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
public y coord: xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
parameters: secp256r1 [NIST P-256, X9.62 prime256v1] (1.2.840.10045.3.1.7)
update handshake state: server_key_exchange[12]
upcoming handshake states: certificate_request[13](optional)
upcoming handshake states: server_hello_done[14]
upcoming handshake states: client certificate[11](optional)
upcoming handshake states: client_key_exchange[16]
upcoming handshake states: certificate_verify[15](optional)
upcoming handshake states: client change_cipher_spec[-1]
upcoming handshake states: client finished[20]
upcoming handshake states: server change_cipher_spec[-1]
upcoming handshake states: server finished[20]
*** ServerHelloDone
update handshake state: server_hello_done[14]
upcoming handshake states: client certificate[11](optional)
upcoming handshake states: client_key_exchange[16]
upcoming handshake states: certificate_verify[15](optional)
upcoming handshake states: client change_cipher_spec[-1]
upcoming handshake states: client finished[20]
upcoming handshake states: server change_cipher_spec[-1]
upcoming handshake states: server finished[20]
Thread-54, WRITE: TLSv1.2 Handshake, length = 2075
Thread-54, READ: TLSv1.2 Alert, length = 2
Thread-54, RECV TLSv1.2 ALERT: fatal, unknown_ca
%% Invalidated: [Session-2, SSL_NULL_WITH_NULL_NULL]
%% Invalidated: [Session-4, TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384]
Thread-54, called closeSocket()
Thread-54, handling exception: javax.net.ssl.SSLHandshakeException: Received fatal alert: unknown_ca最后一行aftrer ServerHelloDone,表示错误:
Thread-54, WRITE: TLSv1.2 Handshake, length = 2075
Thread-54, READ: TLSv1.2 Alert, length = 2
Thread-54, RECV TLSv1.2 ALERT: fatal, unknown_ca
%% Invalidated: [Session-2, SSL_NULL_WITH_NULL_NULL]
%% Invalidated: [Session-4, TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384]
Thread-54, called closeSocket()
Thread-54, handling exception: javax.net.ssl.SSLHandshakeException: Received fatal alert: unknown_ca下一步显然是client_key_exchange.这与客户的私钥有任何关系吗?
unknown_ca是什么意思?在客户端的trust_cert或服务器的证书中缺少证书吗?
下面的图像也是使用Wireshark捕获的通信量,主行使用自签名证书,最后3行用于问题证书,上面讨论了:
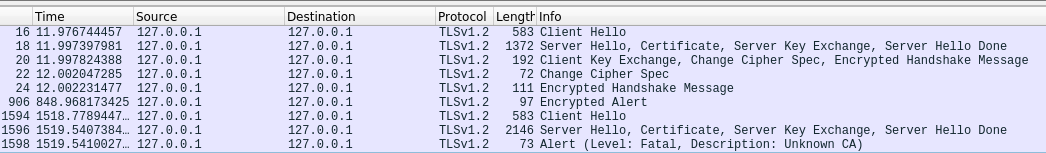
回答 1
Stack Overflow用户
发布于 2020-05-10 12:50:06
unknown_ca是什么意思?在客户端的trust_cert或服务器的证书中缺少证书吗?
unknown_ca意味着由于信任存储中缺少CA,证书不受信任。由于警报是由客户端发送的,这意味着客户端不信任颁发服务器证书的CA。这可能是因为信任存储中缺少根CA,但也可能是服务器没有发送必要的中间证书,以便客户端可以将信任链构建到本地根CA。
页面原文内容由Stack Overflow提供。腾讯云小微IT领域专用引擎提供翻译支持
原文链接:
https://stackoverflow.com/questions/61711998
复制相关文章
相似问题

