在Windows中存储密码的安全方法
我试图保护包含敏感信息的本地数据库(类似于这个问题,只有for Delphi2010)
我使用的是DISQLite组件,它确实支持AES加密,但我仍然需要保护用于解密和读取数据库的密码。
我最初的想法是生成一个随机密码,使用类似DPAPI (在Crypt32.dll中找到的CryptProtectData和CryptUnprotectData函数)来存储它,但是我找不到德尔菲的任何例子。
我的问题是:如何安全地存储随机生成的密码?或者,假设DPAPI道路是安全的,我如何在Delphi中实现这个DPAPI?
回答 3
Stack Overflow用户
发布于 2012-10-30 19:14:29
最好使用Windows的DPAPI。它比使用其他方法安全得多:
- CryptProtectData / CryptProtectMemory
- CryptUnprotectData / CryptUnprotectMemory
CryptProtectMemory / CryptUnprotectMemory提供了更多的灵活性:
- CRYPTPROTECTMEMORY_SAME_PROCESS:只有您的进程才能解密您的数据
- CRYPTPROTECTMEMORY_CROSS_PROCESS:任何进程都可以解码您的数据
- CRYPTPROTECTMEMORY_SAME_LOGON:只有在同一个用户和会话中运行的进程才能解密数据。
优点:
- 不需要有密钥- 窗户帮你做的
- 粒度控制:每个进程/每个会话/每个登录/每台机器
- CryptProtectData存在于Windows2000及更高版本中
- DPAPI比使用你、我和那些相信随机数的人编写的“安全”相关代码更安全:)事实上,微软在安全领域有几十年的经验,拥有有史以来攻击最多的操作系统:o)
缺点:
- 在CRYPTPROTECTMEMORY_SAME_PROCESS的情况下,一个*可以在进程中注入一个新线程,这个线程可以解密您的数据
- 如果有人重置用户密码(而不是更改),您将无法解密您的数据
- 在CRYPTPROTECTMEMORY_SAME_LOGON:如果用户*运行黑客进程,它可以解密您的数据
- 如果您使用CRYPTPROTECT_LOCAL_MACHINE --机器上的每个用户*都可以解密数据。这就是不建议将密码保存在.RDP文件中的原因
- 已知问题
注:“每个用户”是指拥有使用DPAPI的工具或技能的用户。
总之-你有选择。
注意@是对的--计算机上存储的任何东西都可以解密--从内存中读取它,在进程中注入线程等等。
另一方面..。为什么我们不让饼干的生活更艰难呢?)
经验法则:使用后清除包含敏感数据的所有缓冲区。这并不能使事情变得非常安全,但是减少了内存包含敏感数据的可能性。当然,这并不能解决另一个主要问题:其他Delphi组件如何处理传递给它们的敏感数据:)
绝地保安图书馆为DPAPI提供了面向对象的方法。绝地项目还包含DPAPI的翻译窗口头(JWA IIRC)
更新:这里的示例代码使用DPAPI (使用绝地API):
Uses SysUtils, jwaWinCrypt, jwaWinBase, jwaWinType;
function dpApiProtectData(var fpDataIn: tBytes): tBytes;
var
dataIn, // Input buffer (clear-text/data)
dataOut: DATA_BLOB; // Output buffer (encrypted)
begin
// Initializing variables
dataOut.cbData := 0;
dataOut.pbData := nil;
dataIn.cbData := length(fpDataIn); // How much data (in bytes) we want to encrypt
dataIn.pbData := @fpDataIn[0]; // Pointer to the data itself - the address of the first element of the input byte array
if not CryptProtectData(@dataIn, nil, nil, nil, nil, 0, @dataOut) then
RaiseLastOSError; // Bad things happen sometimes
// Copy the encrypted bytes to RESULT variable
setLength(result, dataOut.cbData);
move(dataOut.pbData^, result[0], dataOut.cbData);
LocalFree(HLOCAL(dataOut.pbData)); // http://msdn.microsoft.com/en-us/library/windows/desktop/aa380261(v=vs.85).aspx
// fillChar(fpDataIn[0], length(fpDataIn), #0); // Eventually erase input buffer i.e. not to leave sensitive data in memory
end;
function dpApiUnprotectData(fpDataIn: tBytes): tBytes;
var
dataIn, // Input buffer (clear-text/data)
dataOut: DATA_BLOB; // Output buffer (encrypted)
begin
dataOut.cbData := 0;
dataOut.pbData := nil;
dataIn.cbData := length(fpDataIn);
dataIn.pbData := @fpDataIn[0];
if not CryptUnprotectData(
@dataIn,
nil,
nil,
nil,
nil,
0, // Possible flags: http://msdn.microsoft.com/en-us/library/windows/desktop/aa380261%28v=vs.85%29.aspx
// 0 (zero) means only the user that encrypted the data will be able to decrypt it
@dataOut
) then
RaiseLastOSError;
setLength(result, dataOut.cbData); // Copy decrypted bytes in the RESULT variable
move(dataOut.pbData^, result[0], dataOut.cbData);
LocalFree(HLOCAL(dataOut.pbData)); // http://msdn.microsoft.com/en-us/library/windows/desktop/aa380882%28v=vs.85%29.aspx
end;
procedure testDpApi;
var
bytesClearTextIn, // Holds input bytes
bytesClearTextOut, // Holds output bytes
bytesEncrypted: tBytes; // Holds the resulting encrypted bytes
strIn, strOut: string; // Input / Output strings
begin
// *** ENCRYPT STRING TO BYTE ARRAY
strIn := 'Some Secret Data Here';
// Copy string contents to bytesClearTextIn
// NB: this works for STRING type only!!! (AnsiString / UnicodeString)
setLength(bytesClearTextIn, length(strIn) * sizeOf(char));
move(strIn[1], bytesClearTextIn[0], length(strIn) * sizeOf(char));
bytesEncrypted := dpApiProtectData(bytesClearTextIn); // Encrypt data
// *** DECRYPT BYTE ARRAY TO STRING
bytesClearTextOut := dpApiUnprotectData(bytesEncrypted); // Decrypt data
// Copy decrypted bytes (bytesClearTextOut) to the output string variable
// NB: this works for STRING type only!!! (AnsiString / UnicodeString)
setLength(strOut, length(bytesClearTextOut) div sizeOf(char));
move(bytesClearTextOut[0], strOut[1], length(bytesClearTextOut));
assert(strOut = strIn, 'Boom!'); // Boom should never booom :)
end;备注:
- 该示例是使用CryptProtectData /CryptUnprotectData的轻量级版本;
- 加密是面向字节的,因此更容易使用tBytes (tBytes =字节数组);
- 如果输入和输出字符串为UTF8String,则删除"* sizeOf( char )",因为UTF8String的字符仅为1字节
- CryptProtectMemory / CryptUnProtectMemory的用法类似。
Stack Overflow用户
发布于 2016-10-02 18:24:45
如果您的问题只是为了避免用户每次输入密码,您应该知道Windows已经有了密码存储系统。
如果转到控制面板 -> 凭据管理器。从那里,您正在寻找Windows凭据->通用凭据。
从这里您可以看到,存储远程桌面密码的地方是同一个地方:
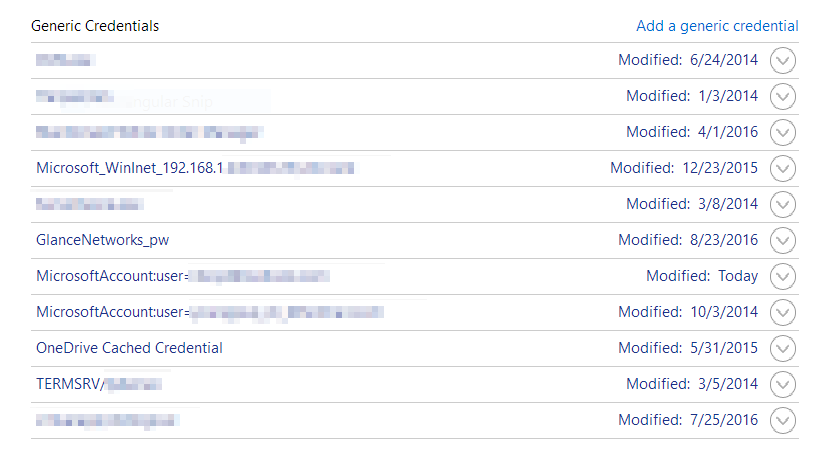
公开此功能的API是CredRead、CredWrite和CredDelete。
我将这些功能封装为三个功能:
function CredReadGenericCredentials(const Target: UnicodeString; var Username, Password: UnicodeString): Boolean;
function CredWriteGenericCredentials(const Target, Username, Password: UnicodeString): Boolean;
function CredDeleteGenericCredentials(const Target: UnicodeString): Boolean;目标是识别信用所需要的东西。我通常使用应用程序的名称。
String target = ExtractFilename(ParamStr(0)); //e.g. 'Contoso.exe'所以简单地说:
CredWriteGenericCredentials(ExtractFilename(ParamStr(0)), username, password);然后您可以在凭据管理器中看到它们:

当你想把它们读回来的时候:
CredReadGenericCredentials(ExtractFilename(ParamStr(0)), {var}username, {var}password);还有一项额外的UI工作,您必须:
- 检测没有存储的凭据,并提示用户提供凭据。
- 检测保存的用户名/密码不起作用,并提示输入新的/正确的凭据,尝试连接并保存新的正确凭据
读取存储的凭据:
function CredReadGenericCredentials(const Target: UnicodeString; var Username, Password: UnicodeString): Boolean;
var
credential: PCREDENTIALW;
le: DWORD;
s: string;
begin
Result := False;
credential := nil;
if not CredReadW(Target, CRED_TYPE_GENERIC, 0, {var}credential) then
begin
le := GetLastError;
s := 'Could not get "'+Target+'" generic credentials: '+SysErrorMessage(le)+' '+IntToStr(le);
OutputDebugString(PChar(s));
Exit;
end;
try
username := Credential.UserName;
password := WideCharToWideString(PWideChar(Credential.CredentialBlob), Credential.CredentialBlobSize div 2); //By convention blobs that contain strings do not have a trailing NULL.
finally
CredFree(Credential);
end;
Result := True;
end;编写存储的凭据:
function CredWriteGenericCredentials(const Target, Username, Password: UnicodeString): Boolean;
var
persistType: DWORD;
Credentials: CREDENTIALW;
le: DWORD;
s: string;
begin
ZeroMemory(@Credentials, SizeOf(Credentials));
Credentials.TargetName := PWideChar(Target); //cannot be longer than CRED_MAX_GENERIC_TARGET_NAME_LENGTH (32767) characters. Recommended format "Company_Target"
Credentials.Type_ := CRED_TYPE_GENERIC;
Credentials.UserName := PWideChar(Username);
Credentials.Persist := CRED_PERSIST_LOCAL_MACHINE;
Credentials.CredentialBlob := PByte(Password);
Credentials.CredentialBlobSize := 2*(Length(Password)); //By convention no trailing null. Cannot be longer than CRED_MAX_CREDENTIAL_BLOB_SIZE (512) bytes
Credentials.UserName := PWideChar(Username);
Result := CredWriteW(Credentials, 0);
end;
end;然后删除:
function CredDeleteGenericCredentials(const Target: UnicodeString): Boolean;
begin
Result := CredDelete(Target, CRED_TYPE_GENERIC);
end;CredRead是CryptProtectData的包装器
应该注意的是,CredW区/CredRead内部使用CryptProtectData。
- 它只是选择将凭证存储在某个地方。
- 它还为用户提供了一个用户界面,用于查看、管理甚至手动输入和更改保存的凭据。
自己使用CryptProtectData的不同之处在于,您只获得了一个blob。这取决于你把它藏在某个地方,然后再把它拿回来。
在存储密码时,CryptProtectData和CryptUnprotectData有很好的包装:
function EncryptString(const Plaintext: UnicodeString; const AdditionalEntropy: UnicodeString): TBytes;
function DecryptString(const Blob: TBytes; const AdditionalEntropy: UnicodeString): UnicodeString;它非常容易使用:
procedure TForm1.TestStringEncryption;
var
encryptedBlob: TBytes;
plainText: UnicodeString;
const
Salt = 'Salt doesn''t have to be secret; just different from the next application';
begin
encryptedBlob := EncryptString('correct battery horse staple', Salt);
plainText := DecryptString(encryptedBlob, salt);
if plainText <> 'correct battery horse staple' then
raise Exception.Create('String encryption self-test failed');
end;实际的肠子是:
type
DATA_BLOB = record
cbData: DWORD;
pbData: PByte;
end;
PDATA_BLOB = ^DATA_BLOB;
const
CRYPTPROTECT_UI_FORBIDDEN = $1;
function CryptProtectData(const DataIn: DATA_BLOB; szDataDescr: PWideChar; OptionalEntropy: PDATA_BLOB; Reserved: Pointer; PromptStruct: Pointer{PCRYPTPROTECT_PROMPTSTRUCT}; dwFlags: DWORD; var DataOut: DATA_BLOB): BOOL; stdcall; external 'Crypt32.dll' name 'CryptProtectData';
function CryptUnprotectData(const DataIn: DATA_BLOB; szDataDescr: PPWideChar; OptionalEntropy: PDATA_BLOB; Reserved: Pointer; PromptStruct: Pointer{PCRYPTPROTECT_PROMPTSTRUCT}; dwFlags: DWORD; var DataOut: DATA_BLOB): Bool; stdcall; external 'Crypt32.dll' name 'CryptUnprotectData';
function EncryptString(const Plaintext: UnicodeString; const AdditionalEntropy: UnicodeString): TBytes;
var
blobIn: DATA_BLOB;
blobOut: DATA_BLOB;
entropyBlob: DATA_BLOB;
pEntropy: Pointer;
bRes: Boolean;
begin
blobIn.pbData := Pointer(PlainText);
blobIn.cbData := Length(PlainText)*SizeOf(WideChar);
if AdditionalEntropy <> '' then
begin
entropyBlob.pbData := Pointer(AdditionalEntropy);
entropyBlob.cbData := Length(AdditionalEntropy)*SizeOf(WideChar);
pEntropy := @entropyBlob;
end
else
pEntropy := nil;
bRes := CryptProtectData(
blobIn,
nil, //data description (PWideChar)
pentropy, //optional entropy (PDATA_BLOB)
nil, //reserved
nil, //prompt struct
CRYPTPROTECT_UI_FORBIDDEN, //flags
{var}blobOut);
if not bRes then
RaiseLastOSError;
//Move output blob into resulting TBytes
SetLength(Result, blobOut.cbData);
Move(blobOut.pbData^, Result[0], blobOut.cbData);
// When you have finished using the DATA_BLOB structure, free its pbData member by calling the LocalFree function
LocalFree(HLOCAL(blobOut.pbData));
end;解密:
function DecryptString(const blob: TBytes; const AdditionalEntropy: UnicodeString): UnicodeString;
var
dataIn: DATA_BLOB;
entropyBlob: DATA_BLOB;
pentropy: PDATA_BLOB;
dataOut: DATA_BLOB;
bRes: BOOL;
begin
dataIn.pbData := Pointer(blob);
dataIn.cbData := Length(blob);
if AdditionalEntropy <> '' then
begin
entropyBlob.pbData := Pointer(AdditionalEntropy);
entropyBlob.cbData := Length(AdditionalEntropy)*SizeOf(WideChar);
pentropy := @entropyBlob;
end
else
pentropy := nil;
bRes := CryptUnprotectData(
DataIn,
nil, //data description (PWideChar)
pentropy, //optional entropy (PDATA_BLOB)
nil, //reserved
nil, //prompt struct
CRYPTPROTECT_UI_FORBIDDEN,
{var}dataOut);
if not bRes then
RaiseLastOSError;
SetLength(Result, dataOut.cbData div 2);
Move(dataOut.pbData^, Result[1], dataOut.cbData);
LocalFree(HLOCAL(DataOut.pbData));
end;Stack Overflow用户
发布于 2012-10-30 18:55:42
好的,下面是一个使用TurboPower Lockbox (version 2)的示例
uses LbCipher, LbString;
TaAES = class
private
Key: TKey256;
FPassword: string;
public
constructor Create;
function Code(AString: String): String;
function Decode(AString: String): String;
property Password: string read FPassword write FPassword;
end;
function TaAES.Code(AString: String): String;
begin
try
RESULT := RDLEncryptStringCBCEx(AString, Key, SizeOf(Key), False);
except
RESULT := '';
end;
end;
constructor TaAES.Create;
begin
GenerateLMDKey(Key, SizeOf(Key), Password);
end;
function TaAES.Decode(AString: String): String;
begin
RESULT := RDLEncryptStringCBCEx(AString, Key, SizeOf(Key), True);
end;您可以将密码保存为应用程序中的变量。不需要保存到文件示例,但可以使用TFileStream保存加密(code)密码,然后用decode读取密码:-)
https://stackoverflow.com/questions/13145112
复制相似问题

