AWSSecurityTokenServiceException: Acced拒绝。未授权用户执行sts:AssumeRole
我是aws的新手。我想为aws呼叫生成临时凭证。为此,我使用了来自使用IAM用户临时凭据( AWS )发出请求的示例
我经过的地方
String clientRegion = "<specific region>";
String roleARN = "<ARN from role>";
String roleSessionName = "Just random string"; //<-- maybe I should pass specific SessionName?
String bucketName = "<specific bucket name>";在尝试扮演角色的时候
stsClient.assumeRole(roleRequest);犯错误
com.amazonaws.services.securitytoken.model.AWSSecurityTokenServiceException:用户:arn:aws:iam:user/未被授权执行: 资源上的AssumeRole:arn:aws:iam::角色/(服务: AWSSecurityTokenService;状态代码: 403;错误代码: AccessDenied;请求ID:)
我有一个认知角色。我认为角色信任关系设置中的问题。看起来是这样的:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::<iam user ID>:user/<USER_NAME>",
"Federated": "cognito-identity.amazonaws.com"
},
"Action": "sts:AssumeRoleWithWebIdentity",
"Condition": {
"StringEquals": {
"cognito-identity.amazonaws.com:aud": "<user pool ID>"
},
"ForAnyValue:StringLike": {
"cognito-identity.amazonaws.com:amr": "authenticated"
}
}
}
]
}和用户策略(此用户策略也是附加于此角色的):
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "<sidId1>",
"Effect": "Allow",
"Action": [
"s3:PutObject",
"s3:PutObjectAcl"
],
"Resource": [
"arn:aws:s3:::<path>*"
]
},
{
"Sid": "sidId2",
"Effect": "Allow",
"Action": [
"sts:AssumeRole",
"sts:AssumeRoleWithWebIdentity"
],
"Resource": [
"arn:aws:iam::<ID>:role/<ROLE_NAME>"
]
}
]
}用户策略有两个警告:
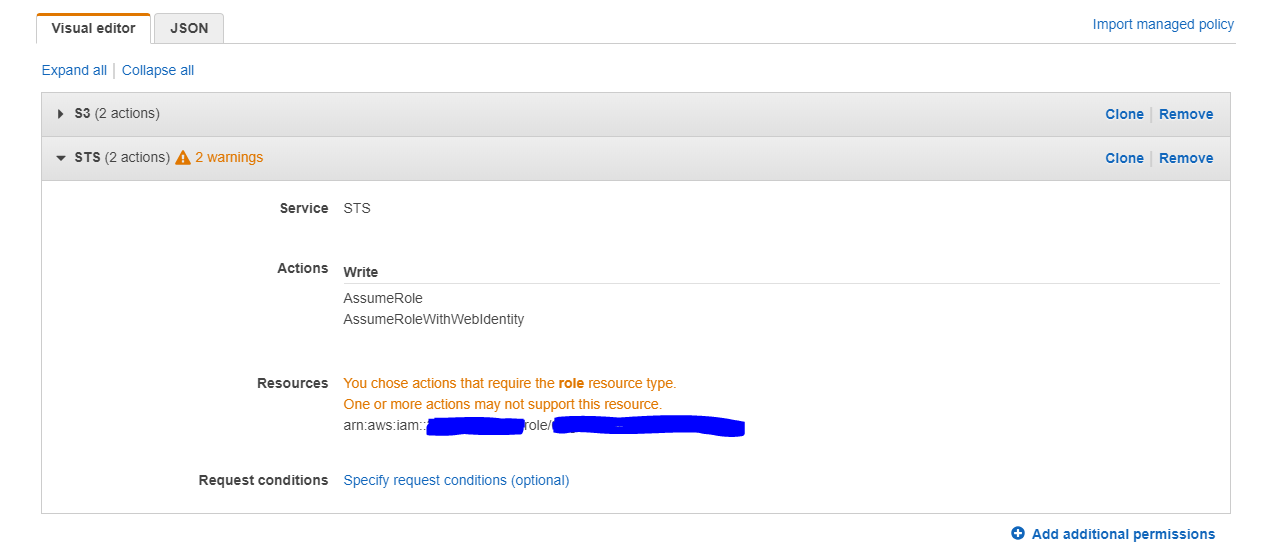
我做错什么了?
UPD I更改角色Trust relationship,只需删除条件
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Federated": "cognito-identity.amazonaws.com",
"AWS": "arn:aws:iam::<ID>:user/<USER>"
},
"Action": [
"sts:AssumeRole",
"sts:AssumeRoleWithWebIdentity"
]
}
]
}现在,访问被拒绝的错误发生在另一行代码上:
// Verify that assuming the role worked and the permissions are set correctly
// by getting a set of object keys from the bucket.
ObjectListing objects = s3Client.listObjects(bucketName);接收到的错误响应:拒绝com.amazonaws.services.s3.model.AmazonS3Exception:访问(服务: S3;状态代码: 403;错误代码: AccessDenied;请求ID:),S3扩展请求ID:
回答 1
Stack Overflow用户
发布于 2021-12-10 15:57:30
为了能够承担一个IAM角色,简单地说,IAM角色承担角色策略或信任关系必须显式地允许主体承担角色,在这种情况下,它不允许。它允许sts:AssumeRoleWithWebIdentity,并且有一些不适用于您的情况的条件。
关于另一个错误,正如@ your 818510所提到的,您的角色没有对s3:ListBucket操作的权限。
https://stackoverflow.com/questions/50694683
复制相似问题

