无法从Ldapmain验证您,因为“user.name的无效凭据”
我使用
- debian 9
- gitlab-ce 11.10.4-ce.0
- 通过apt安装总括
- openldap 2.4.44
ldap配置
配置的/etc/ldap/ldap.conf:
BASE dc=serverX,dc=lan
URI ldap://serverX.lan
TLS_CACERT /etc/ssl/certs/ca-certificates.crt配置的/etc/gitlab/gitlab.rb:
gitlab_rails['ldap_enabled'] = true
gitlab_rails['ldap_servers'] = YAML.load <<-EOS
label: 'Gitlab LDAP'
host: '10.0.0.1'
port: 389
uid: 'sAMAccountName'
method: 'plain' # "tls" or "ssl" or "plain"
bind_dn: 'cn=admin,ou=users,dc=serverX,dc=lan'
password: 'xxxx'
encryption: 'plain'
active_directory: false
allow_username_or_email_login: true
block_auto_created_users: false
base: 'ou=users,dc=serverX,dc=lan'
EOSgitlab-rake gitlab:ldap:check的输出没有问题:
# gitlab-rake gitlab:ldap:check
Checking LDAP ...
LDAP: ... Server: ldapmain
LDAP authentication... Success
LDAP users with access to your GitLab server (only showing the first 100 results)
Checking LDAP ... Finished从phpldapadmin创建的用户:
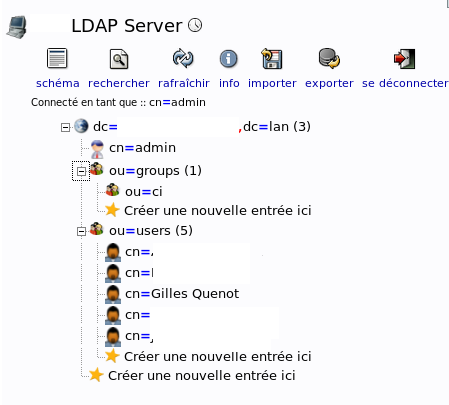
搜索了大量的web资源,但我无法找到创建LDAP用户或使用现有用户的方法。
我不知道问题是什么,也不知道为什么我会得到Invalid credentials for user.name:我通过phpladmin编辑了Password属性(md5),并在LDAP登录页面中输入了相同的内容:
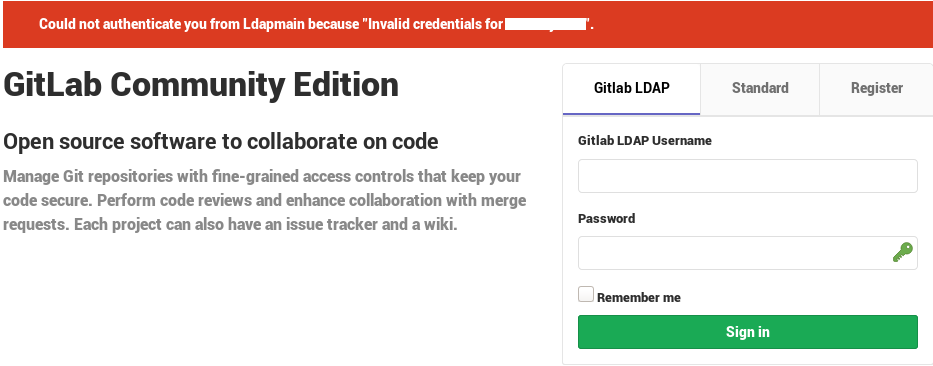
Gitlab日志:
==> /var/log/gitlab/gitlab-rails/production.log <==
Started POST "/users/auth/ldapmain/callback" for 10.0.0.1 at 2019-05-16 07:56:16 +0200
Processing by OmniauthCallbacksController#failure as HTML
Parameters: {"utf8"=>"✓", "authenticity_token"=>"[FILTERED]", "username"=>"user.name", "password"=>"[FILTERED]"}
Redirected to http://domainX.lan/users/sign_in
Completed 302 Found in 411ms (ActiveRecord: 23.1ms)
Started GET "/users/sign_in" for 10.0.0.1 at 2019-05-16 07:56:17 +0200
Processing by SessionsController#new as HTML
Completed 200 OK in 119ms (Views: 104.6ms | ActiveRecord: 7.5ms)
==> /var/log/gitlab/unicorn/unicorn_stdout.log <==
I, [2019-05-16T07:56:16.907169 #3996] INFO -- omniauth: (ldapmain) Callback phase initiated.
E, [2019-05-16T07:56:16.917884 #3996] ERROR -- omniauth: (ldapmain) Authentication failure! invalid_credentials: OmniAuth::Strategies::LDAP::InvalidCredentialsError, Invalid credentials for user.name带有要登录的目标用户的slapcat输出:
dn: uuid=gquenot,ou=users,dc=serverX,dc=lan
cn:: abcdef123456789==
sn: Foo Bar
objectClass: inetOrgPerson
objectClass: top
structuralObjectClass: inetOrgPerson
entryUUID: 5133fc-0be-2039-9825-cd7
creatorsName: cn=admin,dc=serverX,dc=lan
createTimestamp: 20190516045340Z
userPassword:: xxxxxxxx
mail: me@example.com
entryCSN: 20190516101837.136599Z#000000#000#000000
modifiersName: cn=admin,dc=serverX,dc=lan
modifyTimestamp: 20190516101837Z有人知道怎么回事吗?
也许有人能给我一个样本ldiff和一个工作配置?
编辑:
slapadd通过slapadd -f file.ldiff尝试使用这个ldiff:
dn: cn=admin,dc=serverX,dc=lan
objectClass: inetOrgPerson
objectClass: organizationalPerson
objectClass: person
objectClass: top
cn: Firstname Lastname
givenName: Gilles
sn: Quenot
uid: gquenot
mail: me@example.com
userPassword: {MD5}xxxxxxxxxxxxxx错误:
5cdd8fe4 slapcat_so.txt: line 1: unknown directive <dn:> outside backend info and database definitions.
slapadd: bad configuration file!编辑2
固定于:
ldapadd -x -H ldap://serverX:389 -D 'cn=admin,dc=serverX,dc=lan' -W -f stuff.ldiff和phpldapadmin中更新的密码
回答 3
Stack Overflow用户
发布于 2019-05-16 10:05:18
在使用OpenLDAP对用户进行身份验证时,Gitlab配置的目标是Active Directory,因此首先要做的是在/etc/gitlab/gitlab.rb中修复以下参数
uid: 'uid'
active_directory: false我不知道attributes在身份验证上下文中的用途是什么(编辑:attributes用于将用户数据从ldap同步到其Gitlab帐户,这对身份验证本身并不重要)。
可能还有其他问题,例如用户的uid不是'user.name',或者基的范围太窄(例如,user.name条目可能不在ou=people下面),如果您不知道使用基本dn作为基本搜索,或者通过运行带有/不包含'ou‘部分的搜索来进行检查:
ldapsearch -H ldap://10.0.0.1:389 -D cn=admin,dc=serverX,dc=lan -W -b ou=people,dc=serverX,dc=lan uid=user.name \*我还会直接根据ldap检查凭据,即。不是通过Gitlab执行大致相同的查询,而是使用user.name绑定,这里实际上测试了他是否可以绑定和读取它自己的条目:
ldapsearch -H ldap://10.0.0.1:389 -D <user.name dn> -W -b <user.name dn> -s base \*此外,GitLab文档坚持这样一个事实,即LDAP用户必须拥有一个电子邮件地址集,而不管它是否用于登录。
一个典型的ldif文件包含要使用user.name创建的ldapadd -f条目(前提是在其可分辨名称中提到的ou和dc)如下所示:
# user.name entry
dn: uid=user.name,ou=users,dc=serverX,dc=lan
objectClass: inetOrgPerson
objectClass: organizationalPerson
objectClass: person
objectClass: top
cn: Firstname Lastname
givenName: Firstname
sn: Lastname
uid: user.name
mail: user.name@domain.com
userPassword: {MD5}<base64EncodedHash>不过,我不知道GitLab是否/如何知道密码加密方案(似乎没有配置,或者我错过了它)。
您可以创建一个测试用例条目:
- 将
<base64EncodedHash>替换为{MD5}CY9rzUYh03PK3k6DJie09g==(它表示密码test,如果您需要一个脚本来生成它们)。 - 别忘了用dn中真正的dc替换dc
- 注意ldif文件中的空行和\t,因为它会破坏ldap添加/修改操作。
- 运行
ldapadd -x -H ldap://10.0.0.1:389 -D cn=admin,dc=serverX,dc=lan -W -f ldifFilename创建用户条目。 - 运行上面的第一个ldapsearch cmd,您应该会看到这个新条目的结果。
- 运行第二个选项,绑定到用户凭据'test‘并搜索它自己的条目(因此-b基参数指向自己,以避免搜索期间出现权限问题),您将再次看到相同的结果。
在gitlab.rb中:
gitlab_rails['ldap_servers'] = YAML.load <<-EOS
label: 'Gitlab LDAP'
host: '10.0.0.1'
port: 389
uid: 'uid'
bind_dn: 'cn=admin,ou=users,dc=serverX,dc=lan'
password: 'xxxx'
encryption: 'plain'
active_directory: false
allow_username_or_email_login: false
block_auto_created_users: false
base: 'ou=users,dc=serverX,dc=lan'如果您可以与此用户绑定,但不能通过gitlab绑定,这可能意味着它不处理{MD5}身份验证方案。
Stack Overflow用户
发布于 2021-09-22 11:26:48
我也面临着同样的问题--无效的凭据,即使我输入了正确的凭据。这个解决方案对我有效--我的gitlab.rb必须以下面的方式进行更改。以前,我没有更改设置为'sAMAccountName‘的'uid’的值,正如您可以看到的那样,我对它进行了注释,并将值更改为'uid‘本身。所以'uid‘=> 'uid’就是设置。在执行此设置之前,即使在运行命令- gitlab: LDAP :check之前,用于显示-LDAP身份验证的输出.成功,但没有显示ldap用户的列表。当我如上更改uid值时,rake命令就顺利地工作,并向我展示了dc中所有ldap用户的列表。发布这篇文章,我也可以通过UI登录到应用程序中。
注意-用你自己的值替换所有XXX。
gitlab_rails['ldap_enabled'] = true
gitlab_rails['prevent_ldap_sign_in'] = false
gitlab_rails['ldap_servers'] = {
'main' => {
'label' => 'LDAP',
'host' => '10.XXX.XX.XX',
'port' => 389,
# 'uid' => 'sAMAccountName',
'uid' => 'uid',#mandatory need to keep the value as 'uid' only
'encryption' => 'plain',
'verify_certificates' => false,
'bind_dn' => 'cn=XXX,dc=XXXX,dc=XXX',
'password' => 'XXX',
'verify_certificates' => false,
# 'tls_options' => {
# 'ca_file' => '',
# 'ssl_version' => '',
# 'ciphers' => '',
# 'cert' => '',
# 'key' => ''
# },
'timeout' => 10,
'active_directory' => false,
'allow_username_or_email_login' => false,
'block_auto_created_users' => false,
'base' => 'dc=XXX,dc=XX',
# 'user_filter' => '',
# 'attributes' => {
# 'username' => ['uid', 'userid', 'sAMAccountName'],
# 'email' => ['mail', 'email', 'userPrincipalName'],
# 'name' => 'cn',
# 'first_name' => 'givenName',
# 'last_name' => 'sn'
# },
'lowercase_usernames' => true,
# EE Only
# 'group_base' => '',
# 'admin_group' => '',
# 'external_groups' => [],
# 'sync_ssh_keys' => false
}
}Stack Overflow用户
发布于 2022-06-13 15:40:00
我使用Docker https://docs.gitlab.com/ee/install/docker.html安装https://docs.gitlab.com/ee/install/docker.html
LDAP配置https://docs.gitlab.com/ee/administration/auth/ldap/#integrate-ldap-with-gitlab
数独码头主管-it gitlab nano /etc/gitlab/gitlab.rb
## LDAP Settings
##! Docs: https://docs.gitlab.com/omnibus/settings/ldap.html
##! **Be careful not to break the indentation in the ldap_servers block. It is
##! in yaml format and the spaces must be retained. Using tabs will not work.**
gitlab_rails['ldap_enabled'] = true
gitlab_rails['prevent_ldap_sign_in'] = false
##! **remember to close this block with 'EOS' below**
gitlab_rails['ldap_servers'] = YAML.load <<-'EOS'
main: # 'main' is the GitLab 'provider ID' of this LDAP server
label: 'LDAP'
host: 'ipa.example.com'
port: 636
uid: 'uid'
bind_dn: 'uid=gitlab,cn=users,cn=accounts,dc=example,dc=com'
password: 'gitlabpassword'
encryption: 'simple_tls' # "start_tls" or "simple_tls" or "plain"
verify_certificates: false
smartcard_auth: false
active_directory: false
allow_username_or_email_login: false
lowercase_usernames: false
block_auto_created_users: false
base: 'cn=users,cn=accounts,dc=example,dc=com'
user_filter: ''
EOS保存配置,而不是重新配置GitLab:
sudo docker exec -it gitlab /bin/bash
root@gitlab:/# gitlab-ctl reconfigure
root@gitlab:/# gitlab-ctl restart检查LDAP集成是否有效:
root@gitlab:/# gitlab-rake gitlab:ldap:check
Checking LDAP ...
LDAP: ... Server: ldapmain
not verifying SSL hostname of LDAPS server 'ipa.example.com:636'
LDAP authentication... Success
LDAP users with access to your GitLab server (only showing the first 100 results)
DN: uid=admin,cn=users,cn=accounts,dc=example,dc=com uid: admin
DN: uid=gitlab,cn=users,cn=accounts,dc=example,dc=com uid: gitlab
Checking LDAP ... Finishedhttps://stackoverflow.com/questions/56161699
复制相似问题

