默认情况下腾讯云无法登录集群进行问题排障,如果您需要腾讯云售后协助进行运维排障,请参考以下步骤授予腾讯云运维权限。您有权随时吊销回收授予腾讯云的运维排障权限。
通过控制台授予腾讯云权限
1. 登录 容器服务控制台。
2. 在集群管理中选择需要腾讯云协助的集群。
3. 在集群详情页,选择授权管理 > 授权腾讯云运维。
4. 在集群RBAC设置中,选择赋予腾讯云的操作权限。如下图所示:
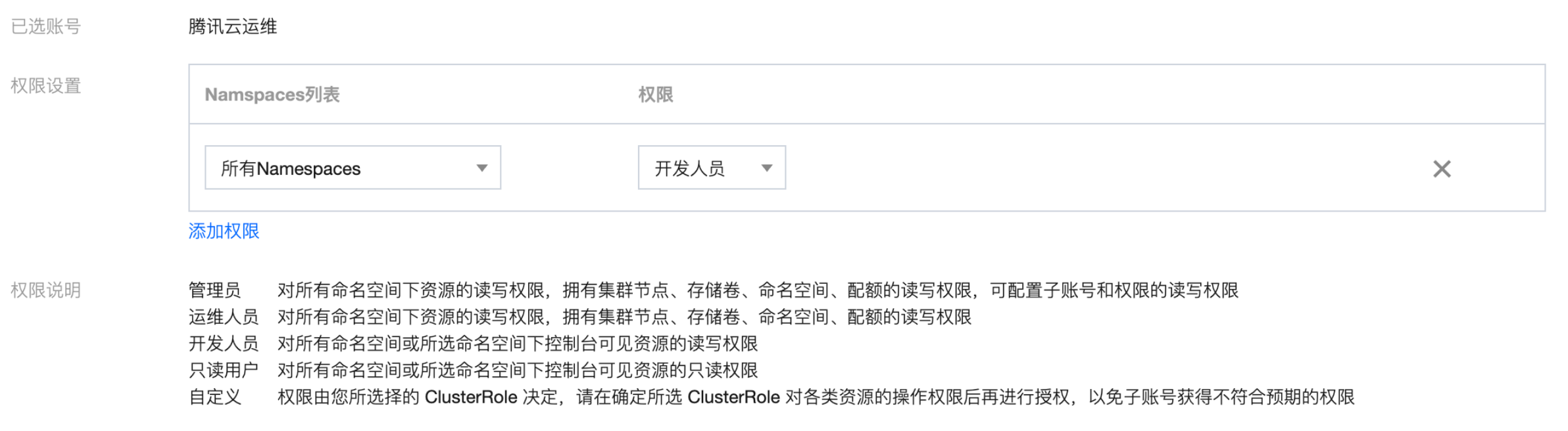

5. 设置完成后,您可在 我的工单 中查看问题处理进度。
注意
默认情况下腾讯云无法登录集群进行问题排障,如果您需要腾讯云售后协助进行运维排障,您可以授予腾讯云指定的运维权限,同时您有权随时吊销回收授予腾讯云的运维排障权限。
您可以通过删除相关资源(ClusterRoleBinding/tkeopsaccount-ClusterRole、ServiceAccount/tkeopsaccount、Sercet/tkeopsaccount-token-xxxx)吊销腾讯云运维权限。
通过 Kubernetes API 授予腾讯云权限
您可以通过创建以下 Kubernetes 资源授予腾讯云指定权限。
ServiceAccount 授予腾讯云访问集群凭证
kind: ServiceAccountapiVersion: v1metadata:name: tkeopsaccountnamespace: kube-systemlabels:cloud.tencent.com/tke-ops-account: tkeops
ClusterRoleBinding/RoleBing 授予腾讯云的操作权限规则
说明
1. 名称和 label 需按如下规则创建。
2. roleRef 可替换为您期望授权腾讯云的权限。
apiVersion: rbac.authorization.k8s.io/v1beta1kind: ClusterRoleBindingmetadata:annotations:cloud.tencent.com/tke-ops-account: tkeopslabels:cloud.tencent.com/tke-ops-account: tkeopsname: tkeopsaccount-ClusterRoleroleRef:apiGroup: rbac.authorization.k8s.iokind: ClusterRolename: tke:adminsubjects:- kind: ServiceAccountname: tkeopsaccountnamespace: kube-system
(可选)ClusterRole/Role 授予腾讯云的操作权限
如集群内有相关 ClusterRole/Role 可直接使用 ClusterRoleBinding/RoleBinding 关联。通过控制台授权,将自动创建策略,无需单独创建。
apiVersion: rbac.authorization.k8s.io/v1beta1kind: ClusterRolemetadata:labels:cloud.tencent.com/tke-rbac-generated: "true"name: tke:adminrules:- apiGroups:- '*'resources:- '*'verbs:- '*'- nonResourceURLs:- '*'verbs:- '*'
apiVersion: rbac.authorization.k8s.io/v1beta1kind: ClusterRolemetadata:labels:cloud.tencent.com/tke-rbac-generated: "true"name: tke:rorules:- apiGroups:- ""resources:- pods- pods/attach- pods/exec- pods/portforward- pods/proxyverbs:- get- list- watch- apiGroups:- ""resources:- configmaps- endpoints- persistentvolumeclaims- replicationcontrollers- replicationcontrollers/scale- secrets- serviceaccounts- services- services/proxyverbs:- get- list- watch- apiGroups:- ""resources:- nodes- persistentvolumesverbs:- get- list- watch- apiGroups:- ""resources:- events- replicationcontrollers/status- pods/log- pods/status- componentstatusesverbs:- get- list- watch- apiGroups:- appsresources:- daemonsets- deployments- deployments/rollback- deployments/scale- replicasets- replicasets/scale- statefulsetsverbs:- get- list- watch- apiGroups:- autoscalingresources:- horizontalpodautoscalersverbs:- get- list- watch- apiGroups:- storage.k8s.ioresources:- storageclassesverbs:- get- list- watch- apiGroups:- batchresources:- cronjobs- jobsverbs:- get- list- watch- apiGroups:- extensions- networking.k8s.ioresources:- daemonsets- deployments- deployments/rollback- deployments/scale- ingresses- replicasets- replicasets/scale- replicationcontrollers/scaleverbs:- get- list- watch- apiGroups:- servicecatalog.k8s.ioresources:- clusterserviceclasses- clusterserviceplans- clusterservicebrokers- serviceinstances- servicebindingsverbs:- get- list- watch- apiGroups:- policyresources:- poddisruptionbudgetsverbs:- get- list- apiGroups:- networking.istio.io- config.istio.io- rbac.istio.io- authentication.istio.io- security.istio.io- install.istio.ioresources:- '*'verbs:- get- list- watch- apiGroups:- apiextensions.k8s.ioresources:- customresourcedefinitionsverbs:- get- list- watch- apiGroups:- networking.tke.cloud.tencent.comresources:- '*'verbs:- get- list- watch- apiGroups:- cloud.tencent.comresources:- '*'verbs:- get- list- watch- apiGroups:- ccs.cloud.tencent.comresources:- '*'verbs:- get- list- watch- apiGroups:- cls.cloud.tencent.comresources:- '*'verbs:- get- list- watch