DHCP欺骗实验操作及防护措施
DHCP欺骗实验操及防护措施
实验操作
1、实验拓扑搭建
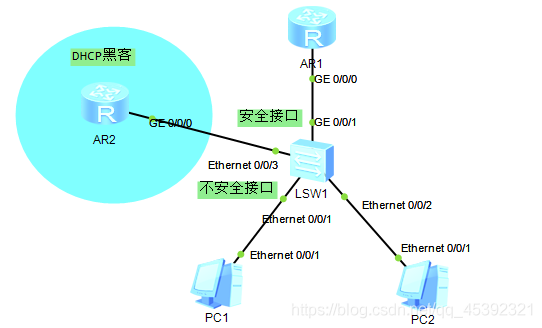
在这里插入图片描述
2、配置参数
(1)PC1
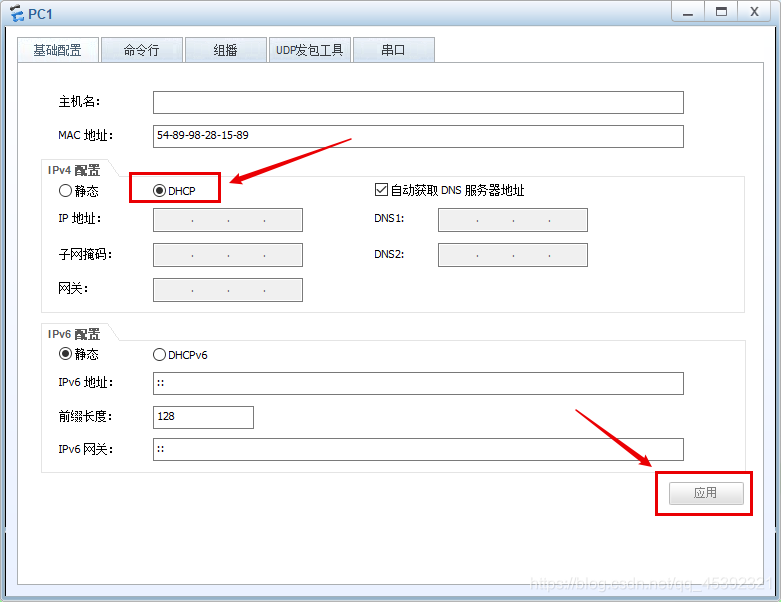
在这里插入图片描述
(2)PC2
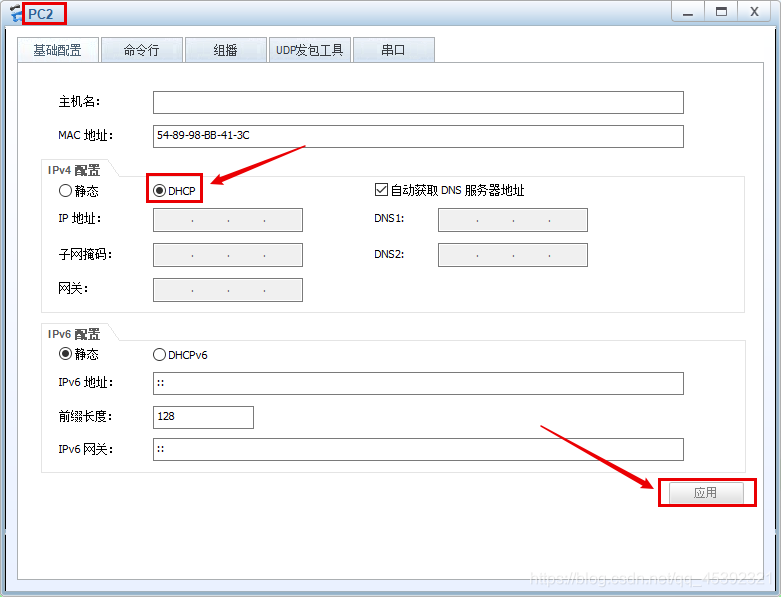
在这里插入图片描述
(3)SW1配置参数
[SW1]vlan batch 10 20
[SW1]interface Ethernet0/0/1
[SW1-Ethernet0/0/1]display this
#
interface Ethernet0/0/1
port link-type access
port default vlan 10
#
return
[SW1-Ethernet0/0/1]
[SW1]interface Ethernet0/0/2
[SW1-Ethernet0/0/2]display this
#
interface Ethernet0/0/2
port link-type access
port default vlan 20
#
return
[SW1-Ethernet0/0/2]quit
[SW1]interface GigabitEthernet 0/0/1
[SW1-GigabitEthernet0/0/1]dis thi
#
interface GigabitEthernet0/0/1
port link-type trunk
undo port trunk allow-pass vlan 1
port trunk allow-pass vlan 10 20
#
return
[SW1-GigabitEthernet0/0/1](4)AR1配置参数(合法路由器)
[AR1]dhcp enable
[AR1]ip pool TV
[AR1-ip-pool-TV]display this
[V200R003C00]
#
ip pool TV
gateway-list 10.1.1.254
network 10.1.1.0 mask 255.255.255.0
excluded-ip-address 10.1.1.1
lease day 2 hour 2 minute 2
dns-list 202.99.99.99
#
return
[AR1-ip-pool-TV]quit
[AR1]ip pool VT
[AR1-ip-pool-VT]dis thi
[V200R003C00]
#
ip pool VT
gateway-list 20.1.1.254
network 20.1.1.0 mask 255.255.255.0
excluded-ip-address 20.1.1.1
lease day 2 hour 2 minute 2
dns-list 202.99.99.99
#
return
[AR1-ip-pool-VT]quit
[AR1]interface GigabitEthernet 0/0/0.1
[AR1-GigabitEthernet0/0/0.1]display this
[V200R003C00]
#
interface GigabitEthernet0/0/0.1
dot1q termination vid 10
ip address 10.1.1.254 255.255.255.0
arp broadcast enable
dhcp select global
#
return
[AR1-GigabitEthernet0/0/0.1]
[AR1-GigabitEthernet0/0/0.2]dis thi
[V200R003C00]
#
interface GigabitEthernet0/0/0.2
dot1q termination vid 20
ip address 20.1.1.254 255.255.255.0
arp broadcast enable
dhcp select global
#
return
[AR1-GigabitEthernet0/0/0.2](5)AR2配置参数(黑客路由器)
[HEIKE]dhcp enable
Info: The operation may take a few seconds. Please wait for a moment.done.
[HEIKE]ip pool IT
Info: It's successful to create an IP address pool.
[HEIKE-ip-pool-IT]gateway-list 1.1.1.254
[HEIKE-ip-pool-IT]network 1.1.1.0 mask 255.255.255.0
[HEIKE-ip-pool-IT]dns-list 202.99.99.99
[HEIKE-ip-pool-IT]lease day 2 hour 2 minute 2
[HEIKE-ip-pool-IT]excluded-ip-address 1.1.1.1
[HEIKE-ip-pool-IT]display this
[V200R003C00]
#
ip pool IT
gateway-list 1.1.1.254
network 1.1.1.0 mask 255.255.255.0
excluded-ip-address 1.1.1.1
lease day 2 hour 2 minute 2
dns-list 202.99.99.99
#
return
[HEIKE]ip pool HR
Info: It's successful to create an IP address pool.
[HEIKE-ip-pool-HR]
[HEIKE-ip-pool-HR] gateway-list 2.2.2.254
[HEIKE-ip-pool-HR]
[HEIKE-ip-pool-HR] network 2.2.2.0 mask 255.255.255.0
[HEIKE-ip-pool-HR]
[HEIKE-ip-pool-HR] excluded-ip-address 2.2.2.2
[HEIKE-ip-pool-HR]
[HEIKE-ip-pool-HR] lease day 2 hour 2 minute 2
[HEIKE-ip-pool-HR]
[HEIKE-ip-pool-HR] dns-list 202.99.99.99
[HEIKE-ip-pool-HR]dis thi
[V200R003C00]
#
ip pool HR
gateway-list 2.2.2.254
network 2.2.2.0 mask 255.255.255.0
excluded-ip-address 2.2.2.2
lease day 2 hour 2 minute 2
dns-list 202.99.99.99
#
return
[HEIKE-ip-pool-HR]quit
[HEIKE]interface GigabitEthernet 0/0/0.1
[HEIKE-GigabitEthernet0/0/0.1]ip address 1.1.1.254 24
[HEIKE-GigabitEthernet0/0/0.1]dot1q termination vid 10
Jul 30 2020 10:42:56-08:00 HEIKE %%01IFNET/4/LINK_STATE(l)[2]:The line protocol
IP on the interface GigabitEthernet0/0/0.1 has entered the UP state.
[HEIKE-GigabitEthernet0/0/0.1]arp broadcast enable
[HEIKE-GigabitEthernet0/0/0.1]dis thi
[V200R003C00]
#
interface GigabitEthernet0/0/0.1
dot1q termination vid 10
ip address 1.1.1.254 255.255.255.0
arp broadcast enable
#
return
[HEIKE-GigabitEthernet0/0/0.1]
[HEIKE]interface GigabitEthernet 0/0/0.2
[HEIKE-GigabitEthernet0/0/0.2]ip address 2.2.2.254 24
[HEIKE-GigabitEthernet0/0/0.2]dot1q termination vid 20
Jul 30 2020 10:44:30-08:00 HEIKE %%01IFNET/4/LINK_STATE(l)[3]:The line protocol
IP on the interface GigabitEthernet0/0/0.2 has entered the UP state.
[HEIKE-GigabitEthernet0/0/0.2]arp broadcast enable
[HEIKE-GigabitEthernet0/0/0.2]dis thi
[V200R003C00]
#
interface GigabitEthernet0/0/0.2
dot1q termination vid 20
ip address 2.2.2.254 255.255.255.0
arp broadcast enable
#
return
# 子接口下启用全局DHCP
[HEIKE-GigabitEthernet0/0/0.2]dhcp select global
[HEIKE-GigabitEthernet0/0/0.2]dis thi
[V200R003C00]
#
interface GigabitEthernet0/0/0.2
dot1q termination vid 20
ip address 2.2.2.254 255.255.255.0
arp broadcast enable
dhcp select global
#
return
[HEIKE-GigabitEthernet0/0/0.2]
[HEIKE]interface GigabitEthernet 0/0/0.1
[HEIKE-GigabitEthernet0/0/0.1]dhcp select global
[HEIKE-GigabitEthernet0/0/0.1]dis thi
[V200R003C00]
#
interface GigabitEthernet0/0/0.1
dot1q termination vid 10
ip address 1.1.1.254 255.255.255.0
arp broadcast enable
dhcp select global
#
return
[HEIKE-GigabitEthernet0/0/0.1]3、防护措施设置
使用DHCP Snooping防范DHCP欺骗攻击
DHCP 欺骗攻击过程: 1.首先攻击者伪装成DHCP客户端,发起大量的DHCP请求(可以用软件实现)。DHCP服务器收到请求后,把IP分配给伪装的DHCP客户端,由于DHCP服务器的IP地址数量是有限的,很快DHCP服务器上地址池的IP就会被消耗完,则DHCP服务器不再为其它客户端分配IP 2.第一步完成后,攻击者这时可以搭建一台DHCP服务器,则客户端的DHCP请求就会到非法的DHCP上请求IP,从而获取一个非法的IP地址。
DHCP Snpooing配置: 1.全局启用dhcp snooping SW1-GigabitEthernet0/0/1 dhcp snooping enable …………………………………………………………………………… 2.将相应的端口(连接合法DHCP服务器的端口)划入trusted SW1-GigabitEthernet0/0/1 dhcp snooping trusted …………………………………………………………………………… 3.SW1全局dhcp snooping和所连接的接口dhcp snooping都要开启 dhcp snooping enable ……………………………………………………………………………… 4.开启dhcp snooping 防护功能时,要先开启DHCP服务(即dhcp enable) dhcp enable dhcp snooping enable
# 防护措施,在交换机的GE 0/0/1上设置参数
[SW1]dhcp enable
Info: The operation may take a few seconds. Please wait for a moment.done.
[SW1]dhcp snooping enable //全局开启dhcp snooping
[SW1]
Jul 30 2020 11:33:38-08:00 SW1 DS/4/DATASYNC_CFGCHANGE:OID 1.3.6.1.4.1.2011.5.25
.191.3.1 configurations have been changed. The current change number is 23, the
change loop count is 0, and the maximum number of records is 4095.
[SW1]interface GigabitEthernet 0/0/1
[SW1-GigabitEthernet0/0/1]dhcp snooping trusted
Jul 30 2020 11:35:18-08:00 SW1 DS/4/DATASYNC_CFGCHANGE:OID 1.3.6.1.4.1.2011.5.25
.191.3.1 configurations have been changed. The current change number is 24, the
change loop count is 0, and the maximum number of records is 4095.
[SW1-GigabitEthernet0/0/1]dis thi
#
interface GigabitEthernet0/0/1
port link-type trunk
undo port trunk allow-pass vlan 1
port trunk allow-pass vlan 10 20
dhcp snooping trusted
#
return
[SW1-GigabitEthernet0/0/1]
[SW1-GigabitEthernet0/0/1]dhcp snooping enable
[SW1-GigabitEthernet0/0/1]dis thi
#
interface GigabitEthernet0/0/1
port link-type trunk
undo port trunk allow-pass vlan 1
port trunk allow-pass vlan 10 20
dhcp snooping enable
dhcp snooping trusted
#
return
[SW1-GigabitEthernet0/0/1]
[SW1]interface Ethernet0/0/3
[SW1-Ethernet0/0/3]dhcp snooping enable
Jul 30 2020 11:39:08-08:00 SW1 DS/4/DATASYNC_CFGCHANGE:OID 1.3.6.1.4.1.2011.5.25
.191.3.1 configurations have been changed. The current change number is 25, the
change loop count is 0, and the maximum number of records is 4095.
[SW1-Ethernet0/0/3]dis thi
#
interface Ethernet0/0/3
port link-type trunk
port trunk allow-pass vlan 10 20
dhcp snooping enable
#
return
[SW1-Ethernet0/0/3]4、PC1 获取DHCP地址
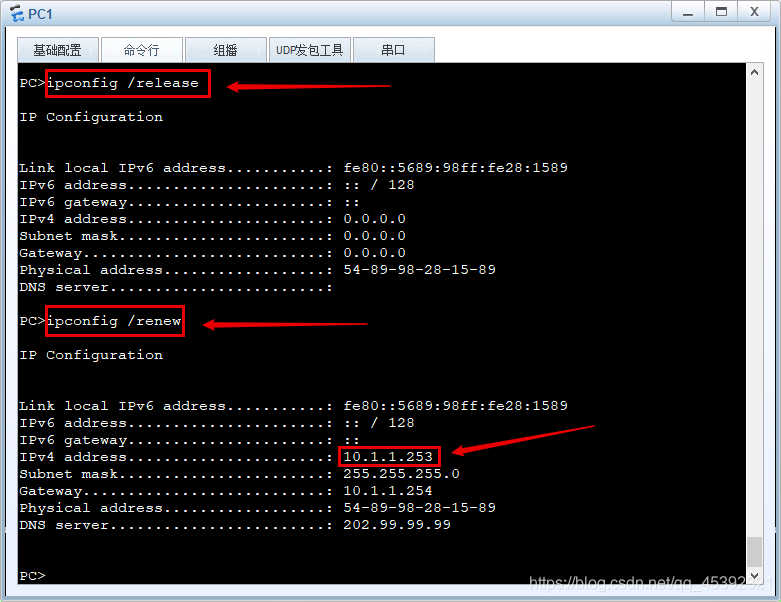
在这里插入图片描述
5、PC2 获取DHCP地址
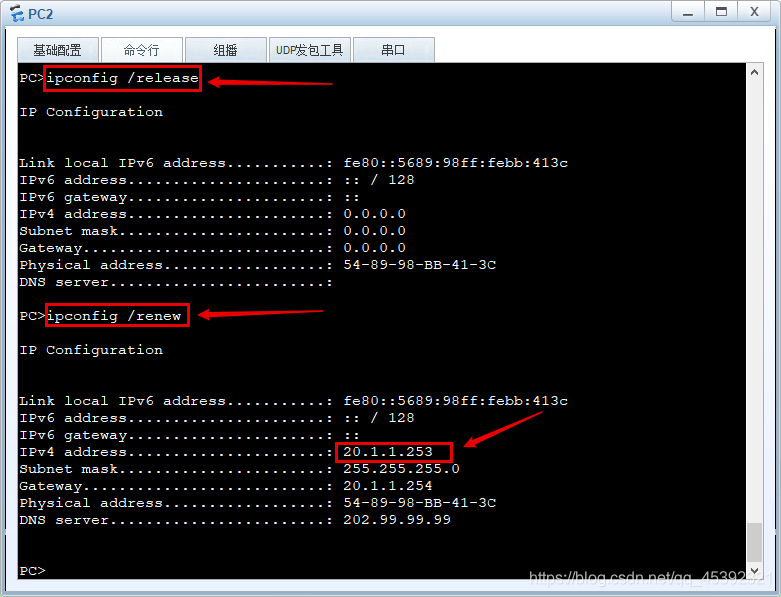
在这里插入图片描述
6、中断合法AR1端口后,验证PC能否正常获取DHCP
当交换机GE 0/0/1的端口与AR1的GE 0/0/0的合法端口通信中断后,Pc1和Pc2重新获取DHCP地址时,无法获取。如图所示。
[AR1]interface GigabitEthernet 0/0/0
[AR1-GigabitEthernet0/0/0]shutdown
Jul 30 2020 12:15:15-08:00 AR1 %%01IFPDT/4/IF_STATE(l)[0]:Interface GigabitEther
net0/0/0 has turned into DOWN state.
[AR1-GigabitEthernet0/0/0]
Jul 30 2020 12:15:15-08:00 AR1 %%01IFNET/4/LINK_STATE(l)[1]:The line protocol IP
on the interface GigabitEthernet0/0/0.1 has entered the DOWN state.
[AR1-GigabitEthernet0/0/0]
Jul 30 2020 12:15:15-08:00 AR1 %%01IFNET/4/LINK_STATE(l)[2]:The line protocol IP
on the interface GigabitEthernet0/0/0.2 has entered the DOWN state.
[AR1-GigabitEthernet0/0/0]
在这里插入图片描述
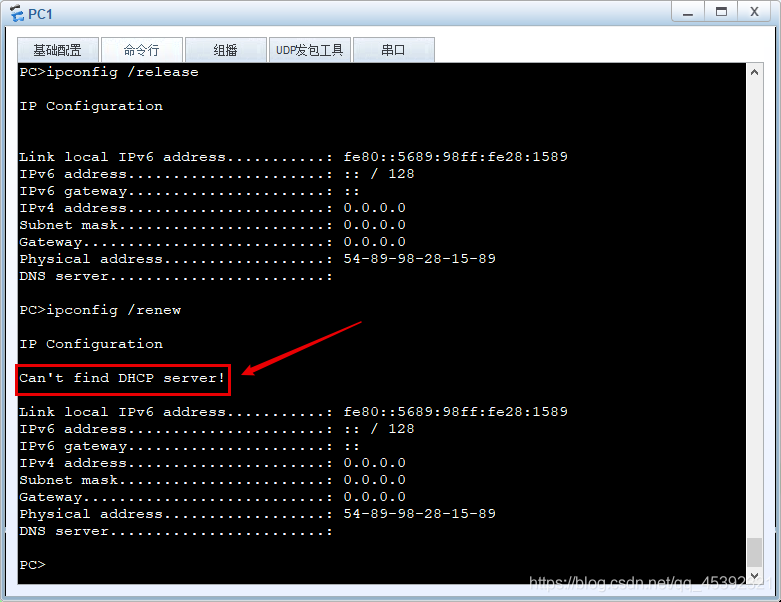
在这里插入图片描述
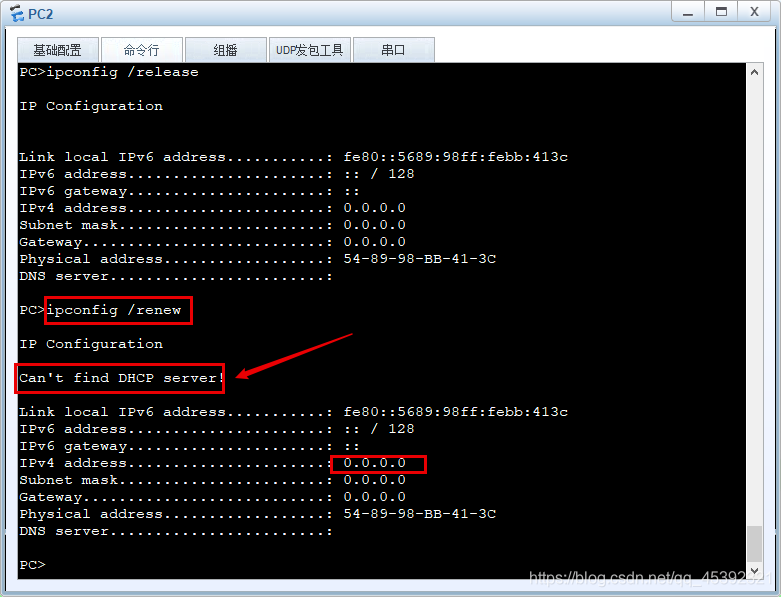
在这里插入图片描述
至此,防护措施已生效。
本文参与 腾讯云自媒体同步曝光计划,分享自作者个人站点/博客。
原始发表:2020-07-30,如有侵权请联系 cloudcommunity@tencent.com 删除
评论
登录后参与评论
推荐阅读
目录
