网络安全实验07 部署防火墙负载分担双击热备
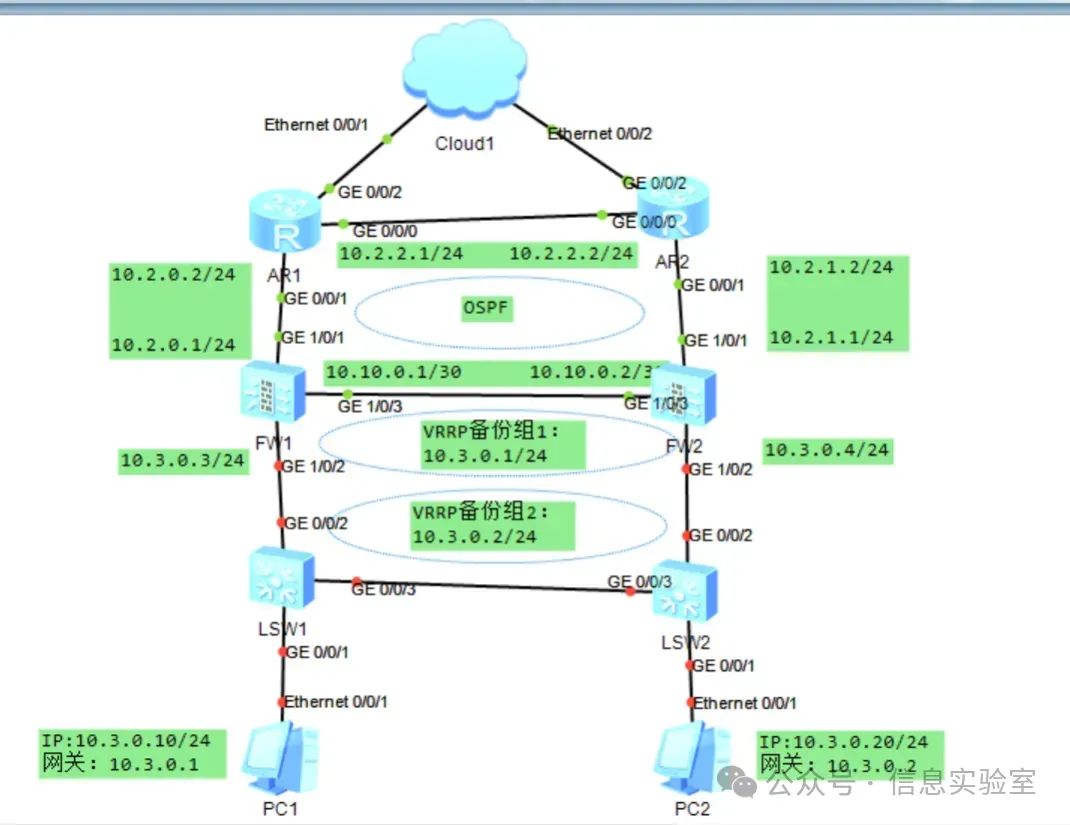
该为某企业组网拓扑,两台防火墙都工作在网络互连层,上行链接路由器,下行连接二层交换机。防火墙与路由器间运行OSPF协议。现在希望两台防火墙以负载分担模式工作。正常情况下,防火墙A和B共同转发流量。当其中一台防火墙出现故障时,另一台防火墙转发全部业务。
一、配置思路
(1)配置防火墙接口IP、路由协议、安全区域,完成网络基本参数配置
(2)配置防火墙双机热备,实现负载分担工作
(3)配置防火墙安全策略,允许内网访问外网
(4)验证调试
二、配置步骤
步骤1:配置防火墙基本参数
(1)接口IP
防火墙A
用户名:admin
原密码:Admin@123
新密码:Huawei@123
system
undo info en
inter g 1/0/1
ip add 10.2.0.1 24
inter g 1/0/2
ip add 10.3.0.3 24
inter g 1/0/3
ip add 10.10.0.1 24
q防火墙B
system
undo info en
inter g 1/0/1
ip add 10.2.1.1 24
inter g 1/0/2
ip add 10.3.0.4 24
inter g 1/0/3
ip add 10.10.0.2 24
q(2)将防火墙接口加入安全区域
防火墙A
firewall zone untrust
add inter g 1/0/1
quit
firewall zone trust
add inter g 1/0/2
quit
firewall zone dmz
add inter g 1/0/3
quit防火墙B
firewall zone untrust
add inter g 1/0/1
quit
firewall zone trust
add inter g 1/0/2
quit
firewall zone dmz
add inter g 1/0/3
quit(3)配置OSPF路由
防火墙A
ospf 1
area 0
network 10.2.0.0 0.0.0.255
network 10.3.0.0 0.0.0.255
quit
quit防火墙B
ospf 1
area 0
network 10.2.0.0 0.0.0.255
network 10.3.0.0 0.0.0.255
quit
quit步骤2:配置双机热备功能
(1)配置VGMP组监控上行业务接口
防火墙A
hrp track interface g 1/0/1防火墙B
hrp track interface g 1/0/1(2)配置VRRP备份组
防火墙A
inter g 1/0/2
vrrp vrid 1 virtual-ip 10.3.0.1 active
vrrp vrid 2 virtual-ip 10.3.0.2 standby
quit防火墙B
inter g 1/0/2
vrrp vrid 1 virtual-ip 10.3.0.1 standby
vrrp vrid 2 virtual-ip 10.3.0.2 active
quit(3)配置会话快速备份功能
防火墙A
hrp mirror session enable防火墙B
hrp mirror session enable(4)指定心跳接口并启用双机热备
防火墙A
hrp inter g 1/0/3 remote 10.10.0.2
hrp enable防火墙B
hrp inter g 1/0/3 remote 10.10.0.1
hrp enable步骤3:配置防火墙安全策略
(1)防火墙A,允许内网主机访问Internet
security-policy
rule name trust_to_untrust
source-zone trust
source-address 10.3.0.0 24
destination-zone untrust
action permit
quit(2)防火墙A,允许防火墙与上行路由器交互OSPF报文
rule name policy_ospf
source-zone local untrust
destination-zone local untrust
service ospf
action permit
quit
firewall packet-filter basic-protocol enable步骤4:配置路由器
(1)接口IP
路由器R1
sys
undo info enable
inter g 0/0/1
ip add 10.2.0.2 24
quit
inter g 0/0/2
ip add 10.2.2.1 24
quit路由器R2
sys
undo info enable
inter g 0/0/1
ip add 10.2.1.2 24
quit
inter g 0/0/2
ip add 10.2.2.2 24
quit(2)配置OSPF路由
路由器R1
ospf 1
area 0
network 10.2.0.0 0.0.0.255
network 10.2.2.0 0.0.0.255
quit
quit路由器R2
ospf 1
area 0
network 10.2.1.0 0.0.0.255
network 10.2.2.0 0.0.0.255
quit
quit步骤5:配置交换机及内网终端
(1)配置交换机1的VLAN
sys
undo info en
vlan batch 3
port-group group-member g 0/0/1 to g 0/0/3
port link-type access
port def vlan 3
quit(2)配置交换机2的VLAN
sys
undo info en
vlan batch 3
port-group group-member g 0/0/1 to g 0/0/3
port link-type access
port def vlan 3
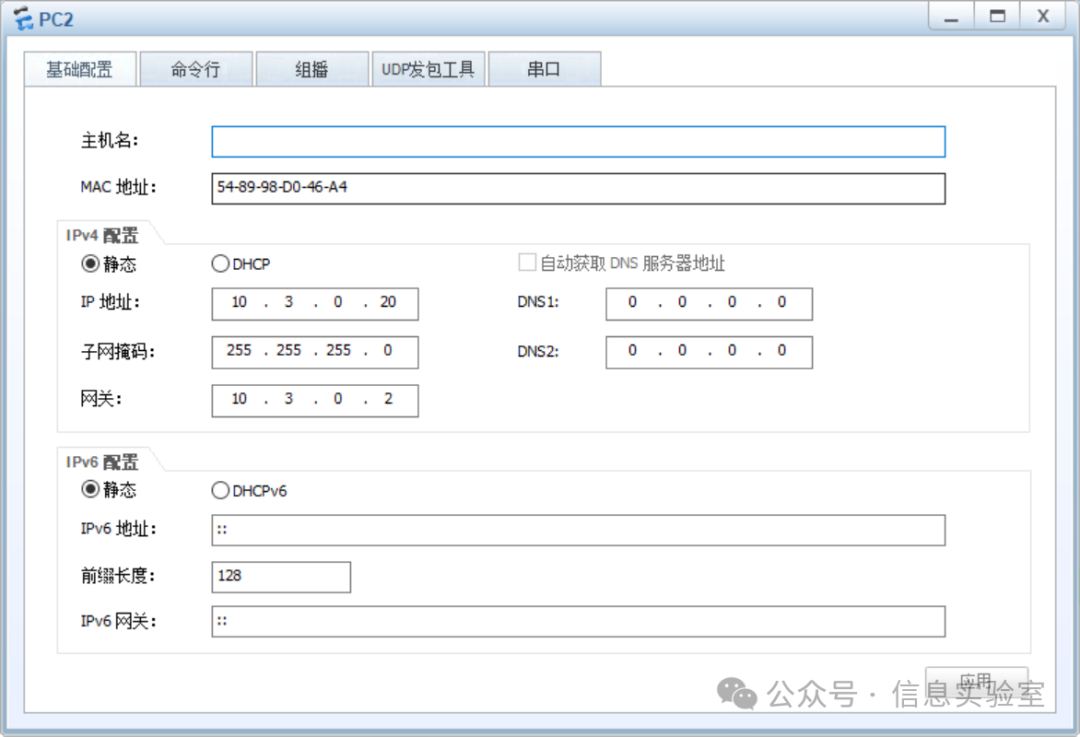
quit(2)配置内网主机的网络参数
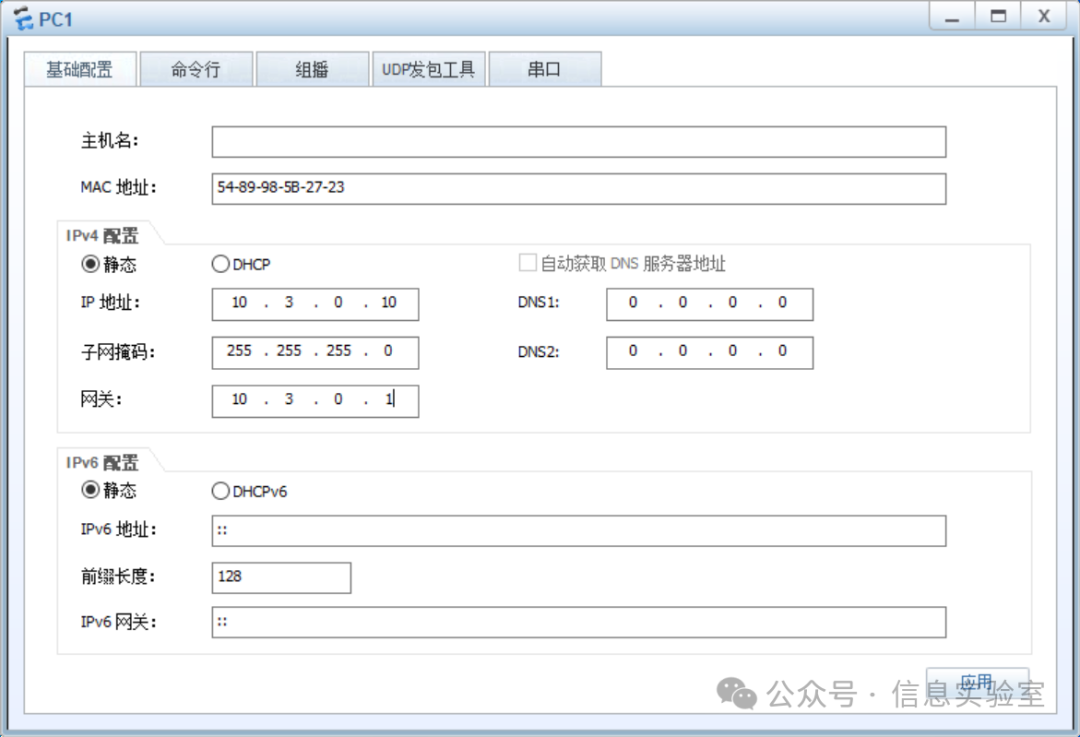
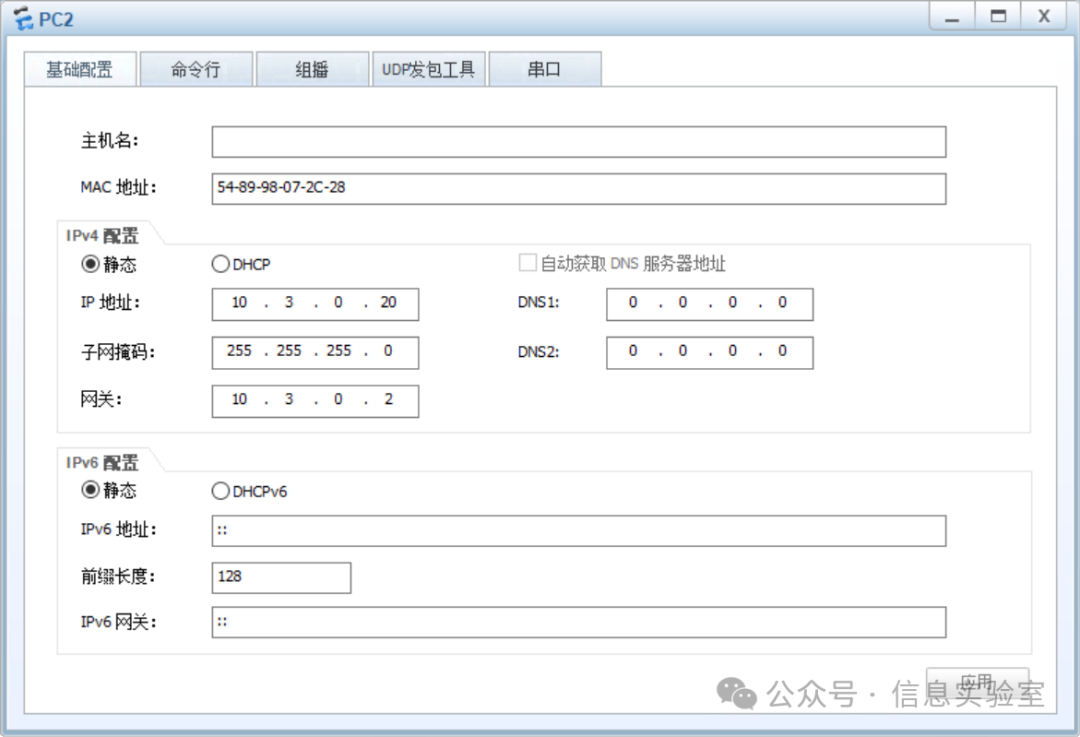
步骤6:验证和调试
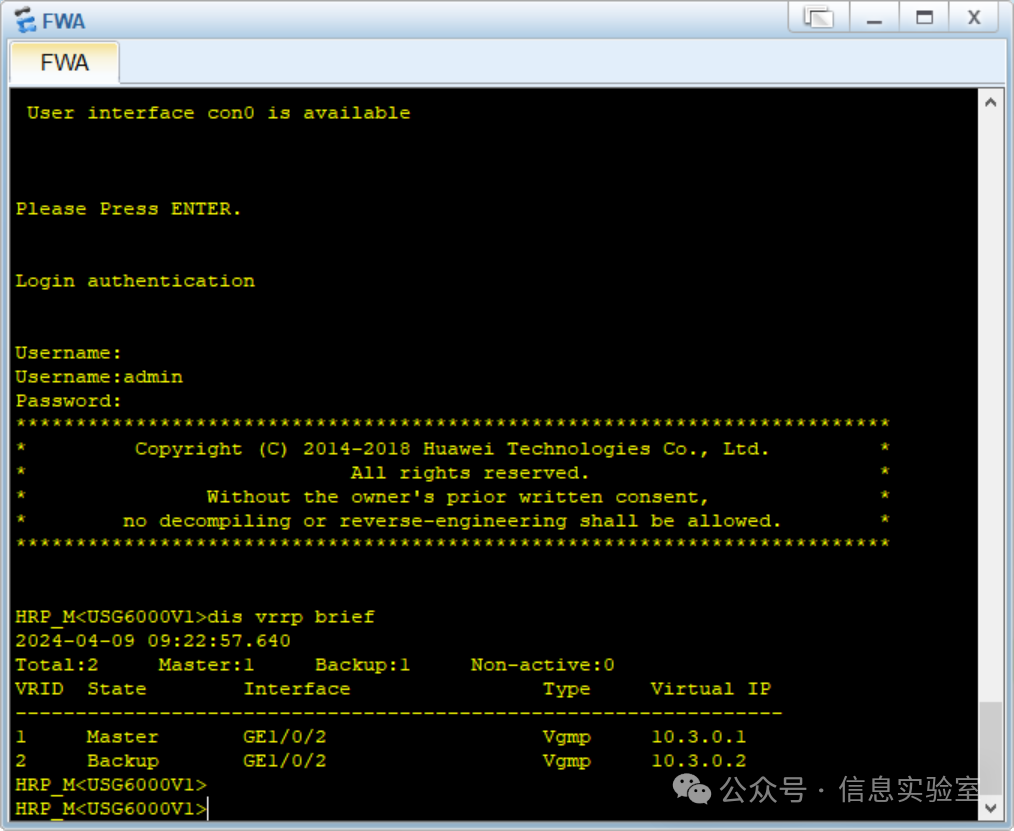
(1)查看VRRP备份组信息
防火墙A
防火墙B
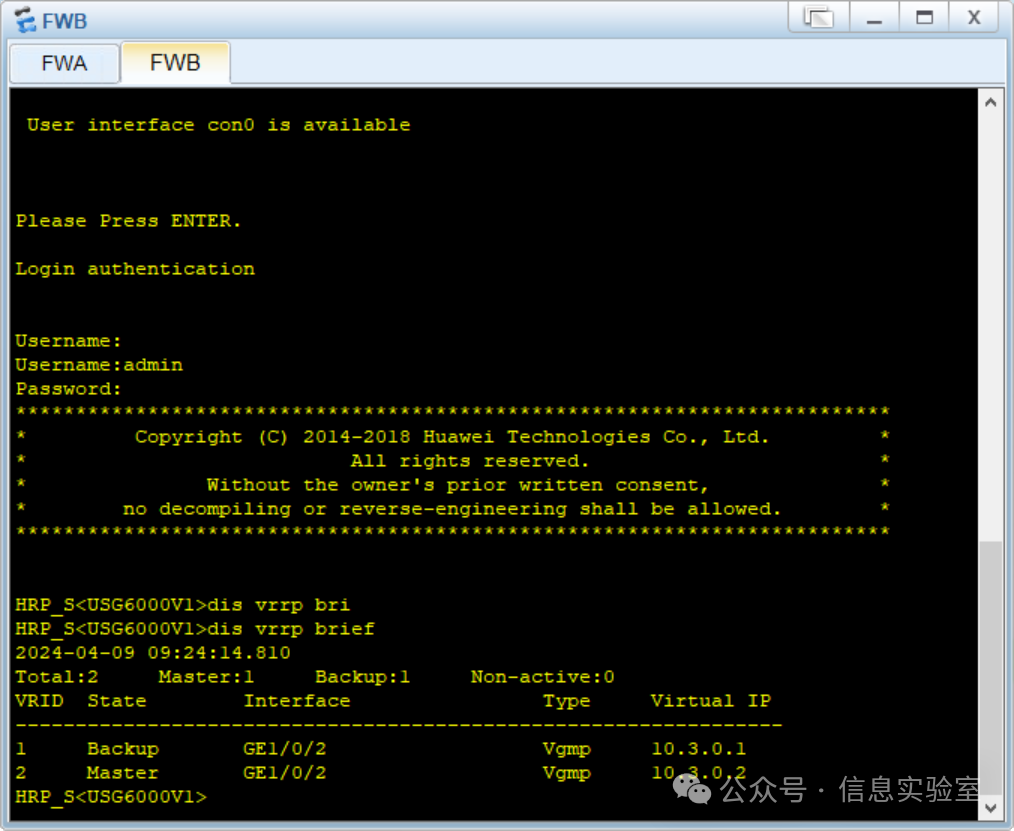
(2)查看VGMP组的状态
防火墙A
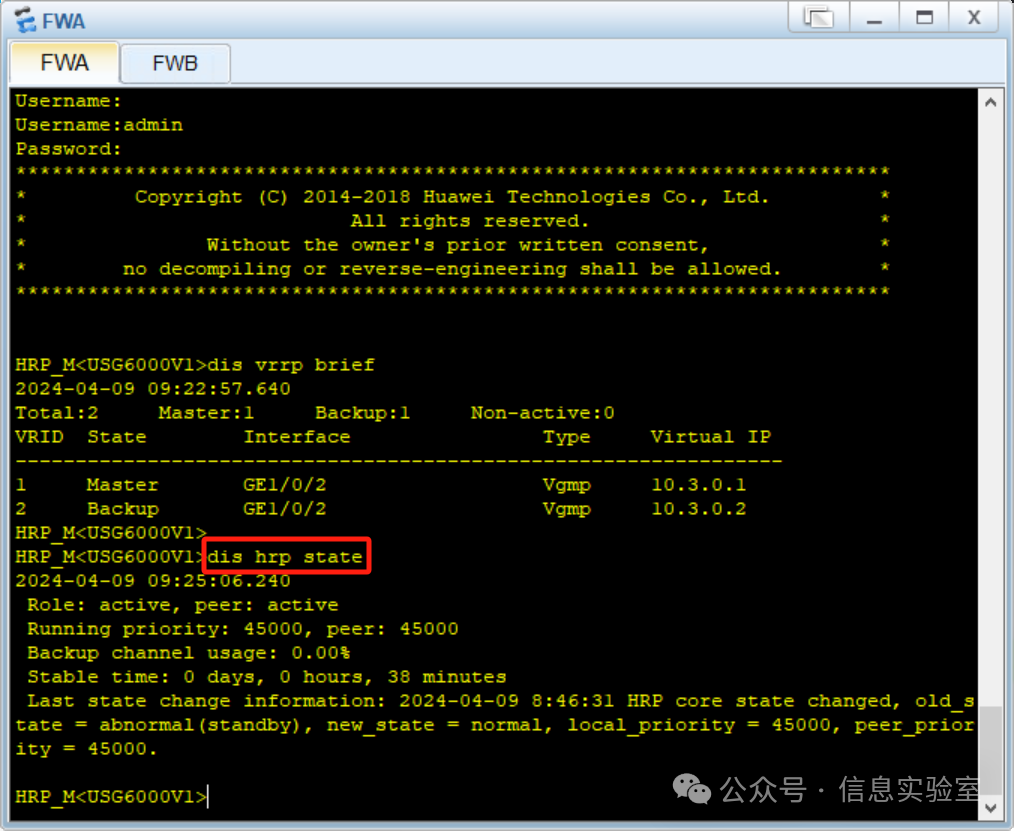
防火墙B
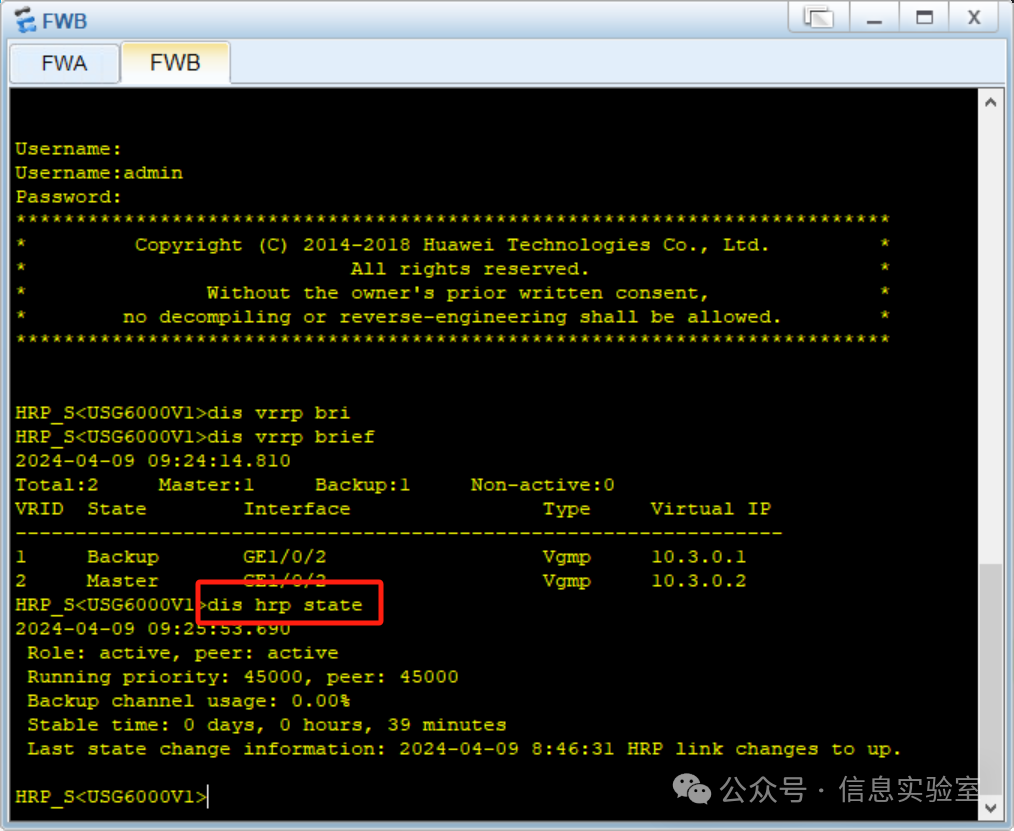
(3)连通性测试
主机1ping路由器AR1(10.2.2.1),主机2ping路由器AR2(10.2.2.2)
# PC1
ping 10.2.2.1
# PC2
ping 10.2.2.2查看会话表
# 防火墙A
display firewall session table
# 防火墙B
display firewall session table (4)故障切换
关闭防火墙A的G1/0/1端口然后观察
# 防火墙A
interface g 1/0/1
shudown
quit
quit
display hrp state
display vrrp brief
# 防火墙B
display hrp state
display vrrp brief
三、各设备完整配置
防火墙A
2024-04-15 02:10:44.500
!Software Version V500R005C10SPC300
#
sysname FW_A
#
l2tp domain suffix-separator @
#
undo info-center enable
#
ipsec sha2 compatible enable
#
undo telnet server enable
undo telnet ipv6 server enable
#
hrp enable
hrp interface GigabitEthernet1/0/3 remote 10.10.0.2
hrp mirror session enable
hrp track interface GigabitEthernet1/0/1
#
firewall packet-filter basic-protocol enable
#
update schedule location-sdb weekly Sun 07:17
#
firewall defend action discard
#
banner enable
#
user-manage web-authentication security port 8887
undo privacy-statement english
undo privacy-statement chinese
page-setting
user-manage security version tlsv1.1 tlsv1.2
password-policy
level high
user-manage single-sign-on ad
user-manage single-sign-on tsm
user-manage single-sign-on radius
user-manage auto-sync online-user
#
web-manager security version tlsv1.1 tlsv1.2
web-manager enable
web-manager security enable
#
firewall dataplane to manageplane application-apperceive default-action drop
#
undo ips log merge enable
#
decoding uri-cache disable
#
update schedule ips-sdb daily 07:09
update schedule av-sdb daily 07:09
update schedule sa-sdb daily 07:09
update schedule cnc daily 07:09
update schedule file-reputation daily 07:09
#
ip vpn-instance default
ipv4-family
#
time-range worktime
period-range 08:00:00 to 18:00:00 working-day
#
ike proposal default
encryption-algorithm aes-256 aes-192 aes-128
dh group14
authentication-algorithm sha2-512 sha2-384 sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
#
aaa
authentication-scheme default
authentication-scheme admin_local
authentication-scheme admin_radius_local
authentication-scheme admin_hwtacacs_local
authentication-scheme admin_ad_local
authentication-scheme admin_ldap_local
authentication-scheme admin_radius
authentication-scheme admin_hwtacacs
authentication-scheme admin_ad
authorization-scheme default
accounting-scheme default
domain default
service-type internetaccess ssl-vpn l2tp ike
internet-access mode password
reference user current-domain
manager-user audit-admin
password cipher @%@%bW:7KIxTyVk^Mo$1^Ob*ot+~.04QY;zMkDa*ADA]|ur=t+Bo@%@%
service-type web terminal
level 15
manager-user api-admin
password cipher @%@%<fPCPdUlC@iYZ/.peCD44N*Y|I)9P5".[S`.k0-!/(~<N*\4@%@%
level 15
manager-user admin
password cipher @%@%TTxY%j,+x8HX<r!b[;i'^~ksRM9S3Lh>K,z"vT;U$_BI~kv^@%@%
service-type web terminal
level 15
role system-admin
role device-admin
role device-admin(monitor)
role audit-admin
bind manager-user audit-admin role audit-admin
bind manager-user admin role system-admin
#
l2tp-group default-lns
#
interface GigabitEthernet0/0/0
undo shutdown
ip binding vpn-instance default
ip address 192.168.0.1 255.255.255.0
alias GE0/METH
#
interface GigabitEthernet1/0/0
undo shutdown
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 10.2.0.1 255.255.255.0
#
interface GigabitEthernet1/0/2
undo shutdown
ip address 10.3.0.3 255.255.255.0
vrrp vrid 1 virtual-ip 10.3.0.1 active
vrrp vrid 2 virtual-ip 10.3.0.2 standby
#
interface GigabitEthernet1/0/3
undo shutdown
ip address 10.10.0.1 255.255.255.0
#
interface GigabitEthernet1/0/4
undo shutdown
#
interface GigabitEthernet1/0/5
undo shutdown
#
interface GigabitEthernet1/0/6
undo shutdown
#
interface Virtual-if0
#
interface NULL0
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/2
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/1
#
firewall zone dmz
set priority 50
add interface GigabitEthernet1/0/3
#
ospf 1
area 0.0.0.0
network 10.2.0.0 0.0.0.255
network 10.3.0.0 0.0.0.255
#
undo ssh server compatible-ssh1x enable
ssh authentication-type default password
ssh server cipher aes256_ctr aes128_ctr
ssh server hmac sha2_256 sha1
ssh client cipher aes256_ctr aes128_ctr
ssh client hmac sha2_256 sha1
#
firewall detect ftp
#
user-interface con 0
authentication-mode aaa
user-interface vty 0 4
authentication-mode aaa
protocol inbound ssh
user-interface vty 16 20
#
pki realm default
#
sa
#
location
#
multi-linkif
mode proportion-of-weight
#
right-manager server-group
#
device-classification
device-group pc
device-group mobile-terminal
device-group undefined-group
#
user-manage server-sync tsm
#
security-policy
rule name trust_to_untrust
source-zone trust
destination-zone untrust
source-address 10.3.0.0 mask 255.255.255.0
action permit
rule name policy_ospf
source-zone local
source-zone untrust
destination-zone local
destination-zone untrust
service ospf
action permit
#
auth-policy
#
traffic-policy
#
policy-based-route
#
nat-policy
#
quota-policy
#
pcp-policy
#
dns-transparent-policy
#
rightm-policy
#
return
防火墙B
2024-04-15 02:12:56.010
!Software Version V500R005C10SPC300
#
sysname FW_B
#
l2tp domain suffix-separator @
#
undo info-center enable
#
ipsec sha2 compatible enable
#
undo telnet server enable
undo telnet ipv6 server enable
#
hrp enable
hrp interface GigabitEthernet1/0/3 remote 10.10.0.1
hrp mirror session enable
hrp track interface GigabitEthernet1/0/1
#
firewall packet-filter basic-protocol enable
#
update schedule location-sdb weekly Sun 06:39
#
firewall defend action discard
#
banner enable
#
user-manage web-authentication security port 8887
undo privacy-statement english
undo privacy-statement chinese
page-setting
user-manage security version tlsv1.1 tlsv1.2
password-policy
level high
user-manage single-sign-on ad
user-manage single-sign-on tsm
user-manage single-sign-on radius
user-manage auto-sync online-user
#
web-manager security version tlsv1.1 tlsv1.2
web-manager enable
web-manager security enable
#
firewall dataplane to manageplane application-apperceive default-action drop
#
undo ips log merge enable
#
decoding uri-cache disable
#
update schedule ips-sdb daily 23:21
update schedule av-sdb daily 23:21
update schedule sa-sdb daily 23:21
update schedule cnc daily 23:21
update schedule file-reputation daily 23:21
#
ip vpn-instance default
ipv4-family
#
time-range worktime
period-range 08:00:00 to 18:00:00 working-day
#
ike proposal default
encryption-algorithm aes-256 aes-192 aes-128
dh group14
authentication-algorithm sha2-512 sha2-384 sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
#
aaa
authentication-scheme default
authentication-scheme admin_local
authentication-scheme admin_radius_local
authentication-scheme admin_hwtacacs_local
authentication-scheme admin_ad_local
authentication-scheme admin_ldap_local
authentication-scheme admin_radius
authentication-scheme admin_hwtacacs
authentication-scheme admin_ad
authorization-scheme default
accounting-scheme default
domain default
service-type internetaccess ssl-vpn l2tp ike
internet-access mode password
reference user current-domain
manager-user audit-admin
password cipher @%@%MsVl1O<XAXq}k~X.B&o:wA[o6*%cXA9qlL/>*C=HhH><A[rw@%@%
service-type web terminal
level 15
manager-user api-admin
password cipher @%@%0du6ZRl-ZQ,4+,D[@ya#w!4@1'4y$S&"tAn.:gRAnBs,!4Cw@%@%
level 15
manager-user admin
password cipher @%@%]iBaC@B4b+\$N,AKymBXU<T}/"o'2X@1z+{8FyYPAGr-<T#U@%@%
service-type web terminal
level 15
role system-admin
role device-admin
role device-admin(monitor)
role audit-admin
bind manager-user audit-admin role audit-admin
bind manager-user admin role system-admin
#
l2tp-group default-lns
#
interface GigabitEthernet0/0/0
undo shutdown
ip binding vpn-instance default
ip address 192.168.0.1 255.255.255.0
alias GE0/METH
#
interface GigabitEthernet1/0/0
undo shutdown
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 10.2.1.1 255.255.255.0
#
interface GigabitEthernet1/0/2
undo shutdown
ip address 10.3.0.4 255.255.255.0
vrrp vrid 1 virtual-ip 10.3.0.1 standby
vrrp vrid 2 virtual-ip 10.3.0.2 active
#
interface GigabitEthernet1/0/3
undo shutdown
ip address 10.10.0.2 255.255.255.252
#
interface GigabitEthernet1/0/4
undo shutdown
#
interface GigabitEthernet1/0/5
undo shutdown
#
interface GigabitEthernet1/0/6
undo shutdown
#
interface Virtual-if0
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/2
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/1
#
firewall zone dmz
set priority 50
add interface GigabitEthernet1/0/3
#
ospf 1
area 0.0.0.0
network 10.2.1.0 0.0.0.255
network 10.3.0.0 0.0.0.255
#
undo ssh server compatible-ssh1x enable
ssh authentication-type default password
ssh server cipher aes256_ctr aes128_ctr
ssh server hmac sha2_256 sha1
ssh client cipher aes256_ctr aes128_ctr
ssh client hmac sha2_256 sha1
#
firewall detect ftp
#
user-interface con 0
authentication-mode aaa
user-interface vty 0 4
authentication-mode aaa
protocol inbound ssh
user-interface vty 16 20
#
pki realm default
#
sa
#
location
#
multi-linkif
mode proportion-of-weight
#
right-manager server-group
#
device-classification
device-group pc
device-group mobile-terminal
device-group undefined-group
#
user-manage server-sync tsm
#
security-policy
rule name trust_to_untrust
source-zone trust
destination-zone untrust
source-address 10.3.0.0 mask 255.255.255.0
action permit
rule name policy_ospf
source-zone local
source-zone untrust
destination-zone local
destination-zone untrust
service ospf
action permit
#
auth-policy
#
traffic-policy
#
policy-based-route
#
nat-policy
#
quota-policy
#
pcp-policy
#
dns-transparent-policy
#
rightm-policy
#
return
路由器AR1
[V200R003C00]
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
undo info-center enable
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
#
interface GigabitEthernet0/0/1
ip address 10.2.0.2 255.255.255.0
#
interface GigabitEthernet0/0/2
ip address 10.2.2.1 255.255.255.0
#
interface NULL0
#
ospf 1
area 0.0.0.0
network 10.2.0.0 0.0.0.255
network 10.2.2.0 0.0.0.255
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
路由器AR2
[V200R003C00]
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
undo info-center enable
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
#
interface GigabitEthernet0/0/1
ip address 10.2.1.2 255.255.255.0
#
interface GigabitEthernet0/0/2
ip address 10.2.2.2 255.255.255.0
#
interface NULL0
#
ospf 1
area 0.0.0.0
network 10.2.1.0 0.0.0.255
network 10.2.2.0 0.0.0.255
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
交换机LSW1
#
sysname Huawei
#
undo info-center enable
#
vlan batch 3
#
cluster enable
ntdp enable
ndp enable
#
drop illegal-mac alarm
#
diffserv domain default
#
drop-profile default
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password simple admin
local-user admin service-type http
#
interface Vlanif1
#
interface MEth0/0/1
#
interface GigabitEthernet0/0/1
port link-type access
port default vlan 3
#
interface GigabitEthernet0/0/2
port link-type access
port default vlan 3
#
interface GigabitEthernet0/0/3
port link-type access
port default vlan 3
#
interface GigabitEthernet0/0/4
#
interface GigabitEthernet0/0/5
#
interface GigabitEthernet0/0/6
#
interface GigabitEthernet0/0/7
#
interface GigabitEthernet0/0/8
#
interface GigabitEthernet0/0/9
#
interface GigabitEthernet0/0/10
#
interface GigabitEthernet0/0/11
#
interface GigabitEthernet0/0/12
#
interface GigabitEthernet0/0/13
#
interface GigabitEthernet0/0/14
#
interface GigabitEthernet0/0/15
#
interface GigabitEthernet0/0/16
#
interface GigabitEthernet0/0/17
#
interface GigabitEthernet0/0/18
#
interface GigabitEthernet0/0/19
#
interface GigabitEthernet0/0/20
#
interface GigabitEthernet0/0/21
#
interface GigabitEthernet0/0/22
#
interface GigabitEthernet0/0/23
#
interface GigabitEthernet0/0/24
#
interface NULL0
#
user-interface con 0
user-interface vty 0 4
#
return
交换机LSW2
#
sysname Huawei
#
undo info-center enable
#
vlan batch 3
#
cluster enable
ntdp enable
ndp enable
#
drop illegal-mac alarm
#
diffserv domain default
#
drop-profile default
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password simple admin
local-user admin service-type http
#
interface Vlanif1
#
interface MEth0/0/1
#
interface GigabitEthernet0/0/1
port link-type access
port default vlan 3
#
interface GigabitEthernet0/0/2
port link-type access
port default vlan 3
#
interface GigabitEthernet0/0/3
port link-type access
port default vlan 3
#
interface GigabitEthernet0/0/4
#
interface GigabitEthernet0/0/5
#
interface GigabitEthernet0/0/6
#
interface GigabitEthernet0/0/7
#
interface GigabitEthernet0/0/8
#
interface GigabitEthernet0/0/9
#
interface GigabitEthernet0/0/10
#
interface GigabitEthernet0/0/11
#
interface GigabitEthernet0/0/12
#
interface GigabitEthernet0/0/13
#
interface GigabitEthernet0/0/14
#
interface GigabitEthernet0/0/15
#
interface GigabitEthernet0/0/16
#
interface GigabitEthernet0/0/17
#
interface GigabitEthernet0/0/18
#
interface GigabitEthernet0/0/19
#
interface GigabitEthernet0/0/20
#
interface GigabitEthernet0/0/21
#
interface GigabitEthernet0/0/22
#
interface GigabitEthernet0/0/23
#
interface GigabitEthernet0/0/24
#
interface NULL0
#
user-interface con 0
user-interface vty 0 4
#
return
PC1
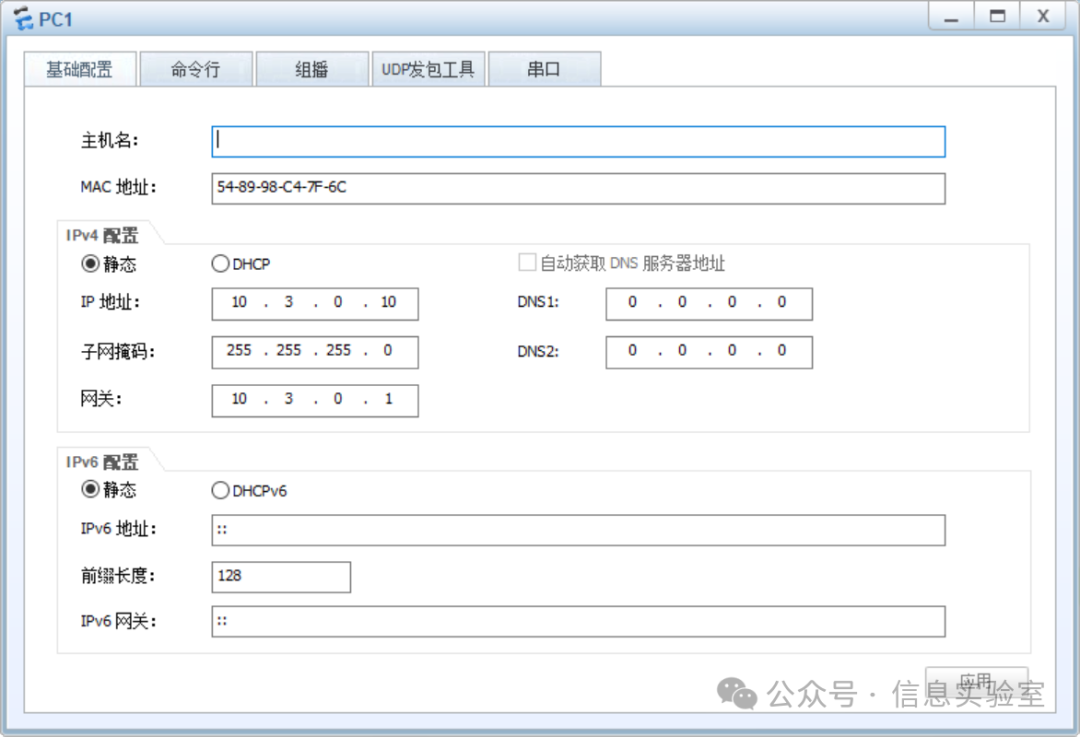
PC2
本文参与 腾讯云自媒体同步曝光计划,分享自微信公众号。
原始发表:2024-04-15,如有侵权请联系 cloudcommunity@tencent.com 删除
评论
登录后参与评论
推荐阅读
目录


