简单实践Radare2
简单实践Radare2
用户1423082
发布于 2024-12-31 18:25:52
发布于 2024-12-31 18:25:52
安装与简介
$ git clone https://github.com/radare/radare2
$ cd radare2
$ sudo sys/install.sh这个软件的优势应该是开源,支持多架构,多系统
实践
rabin2
第一个工具rabin2,这个比readelf,file强大
-I binary info查看binary的信息
# rabin2 -I ./intro
arch x86
binsz 6485
bintype elf
bits 64
canary false
class ELF64
crypto false
endian little
havecode true
intrp /lib64/ld-linux-x86-64.so.2
lang c
linenum true
lsyms true
machine AMD x86-64 architecture
maxopsz 16
minopsz 1
nx true
os linux
pcalign 0
pic true
relocs true
relro partial
rpath NONE
static false
stripped false
subsys linux
va true查看字符串
-z strings (from data section)结果:
# rabin2 -z ./intro
000 0x000006e4 0x000006e4 11 12 (.rodata) ascii Hello World当然查看更多可以下面这两个
-zz strings (from raw bins [e bin.rawstr=1])
-zzz dump raw strings to stdout (for huge files)r2
这个应该是核心工具
启动:
# r2 ./intro分析的话可以输入aa,如果想要更详细,可以aaa,或者aaaa
# r2 ./intro
-- The more 'a' you add after 'aa' the more analysis steps are executed.
[0x00000540]> aa
[x] Analyze all flags starting with sym. and entry0 (aa)
[0x00000540]>分析完我们要去看函数,就用s,s代表就是seek,我们操作文件应该用过fseek
我们jmp到main函数
[0x00000540]> s main
[0x0000064a]>可以看到前面的变了,前面的应该是偏移
当然我们也可以切换回来
[0x0000064a]> s 0x540
[0x00000540]>但现在我们还是看不到代码,还是命令行,我们可以用v切换为显示模式,代表visual mode,有英文详细名词好记
我们输入v就看到了十六进制的界面了
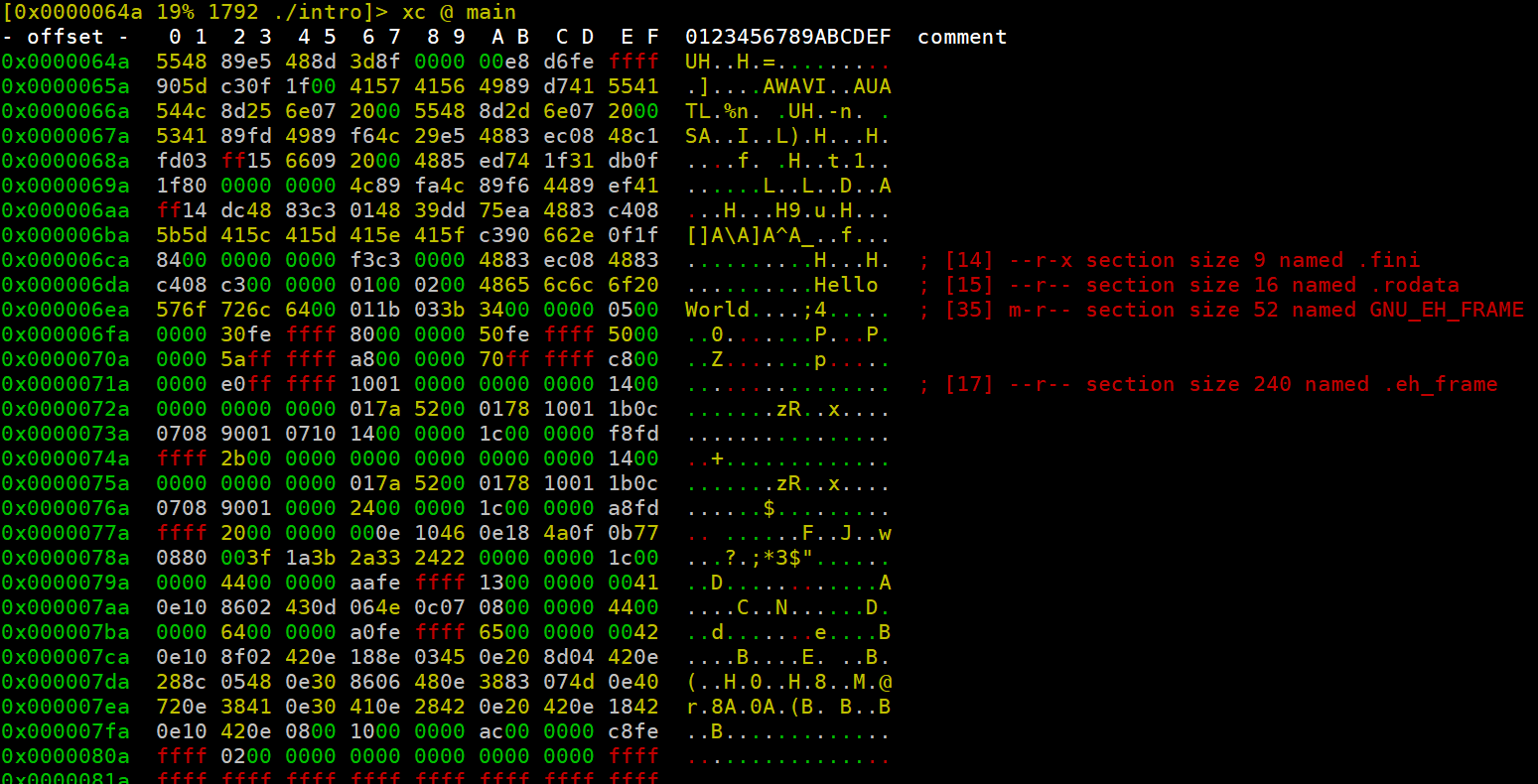
我们这是可以再用p来切换其他模式,我们可以切花到下面的
[0x0000064a 19% 512 ./intro]> pd $r @ main
;-- main:
/ (fcn) sym.main 19
| sym.main ();
| ; DATA XREF from 0x0000055d (entry0)
| 0x0000064a 55 push rbp
| 0x0000064b 4889e5 mov rbp, rsp
| 0x0000064e 488d3d8f0000. lea rdi, str.Hello_World ; 0x6e4 ; "Hello World"
| 0x00000655 e8d6feffff call sym.imp.puts ;[1] ; int puts(const char *s)
| 0x0000065a 90 nop
| 0x0000065b 5d pop rbp
\ 0x0000065c c3 ret
0x0000065d 0f1f00 nop dword [rax]
/ (fcn) sym.__libc_csu_init 101
| sym.__libc_csu_init ();
| ; DATA XREF from 0x00000556 (entry0)
| 0x00000660 4157 push r15
| 0x00000662 4156 push r14
| 0x00000664 4989d7 mov r15, rdx
| 0x00000667 4155 push r13
| 0x00000669 4154 push r12
| 0x0000066b 4c8d256e0720. lea r12, obj.__frame_dummy_init_array_entry ; loc.__init_array_start ; 0x200de0 ; "@\x06"
| 0x00000672 55 push rbp
| 0x00000673 488d2d6e0720. lea rbp, obj.__do_global_dtors_aux_fini_array_entry ; loc.__init_array_end ; 0x200de8
| 0x0000067a 53 push rbx
| 0x0000067b 4189fd mov r13d, edi
| 0x0000067e 4989f6 mov r14, rsi
| 0x00000681 4c29e5 sub rbp, r12
| 0x00000684 4883ec08 sub rsp, 8
| 0x00000688 48c1fd03 sar rbp, 3
| 0x0000068c ff1566092000 call qword sym._init ;[2] ; [0x200ff8:8]=0x500 sym._init
| 0x00000692 4885ed test rbp, rbp如果想后退按esc就行
实战一个crackme
先看一下信息
# rabin2 -I ./crackme
arch x86
binsz 6759
bintype elf
bits 64
canary true
class ELF64
crypto false
endian little
havecode true
intrp /lib64/ld-linux-x86-64.so.2
lang c
linenum true
lsyms true
machine AMD x86-64 architecture
maxopsz 16
minopsz 1
nx true
os linux
pcalign 0
pic true
relocs true
relro partial
rpath NONE
static false
stripped false
subsys linux
va true先运行
# ./crackme
What's the password? 4324
You failed我们之前用-z查看字符串,我们如果只查看字符串而不看地址什么的
-qq show less info (no offset/size for -z for ex.)用-zqq可以显示更少信息
rabin2 -zqq ./crackme
What's the password?
radare2
Congratulations
What's the second password?
What's the third password?
You failed
Flag is: r2{%s %s %s}\n我们可以猜想radare2就是password
# ./crackme
What's the password? radare2
Congratulations
What's the second password?这就是最简单的,不过这还有第二个password呢
我们用r2看看吧
# r2 ./crackme
-- Try pressing the pigeon-shaped button
[0x000006f0]> aaa
[x] Analyze all flags starting with sym. and entry0 (aa)
[x] Analyze len bytes of instructions for references (aar)
[x] Analyze function calls (aac)
[x] Use -AA or aaaa to perform additional experimental analysis.
[x] Constructing a function name for fcn.* and sym.func.* functions (aan)
[0x000006f0]> s main
[0x000007fa]>如果要切换到想ida那样的,就用VV,之后就可以用方向键控制了
我们就可以清晰看到password1了
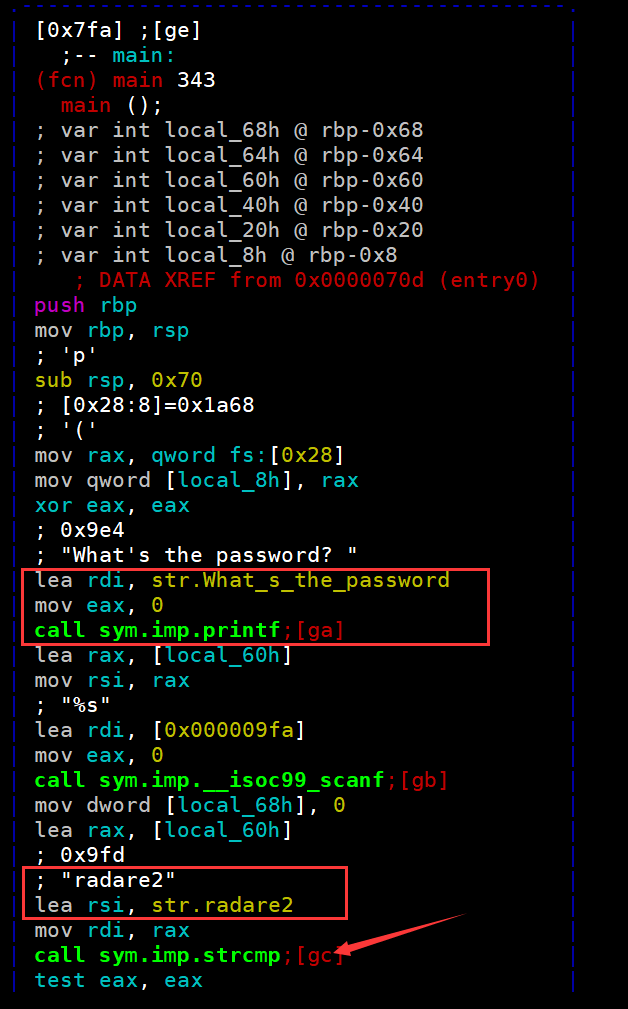
password2是将我们的输入调用atoi(将字符串转化为数字),之后跟0xf比较
那么我们的输入就是15,通过第二关
# ./crackme
What's the password? radare2
Congratulations
What's the second password? 15
Congratulations
What's the third password?接下来看看第三关,这个也是调用atoi,这次是0x539
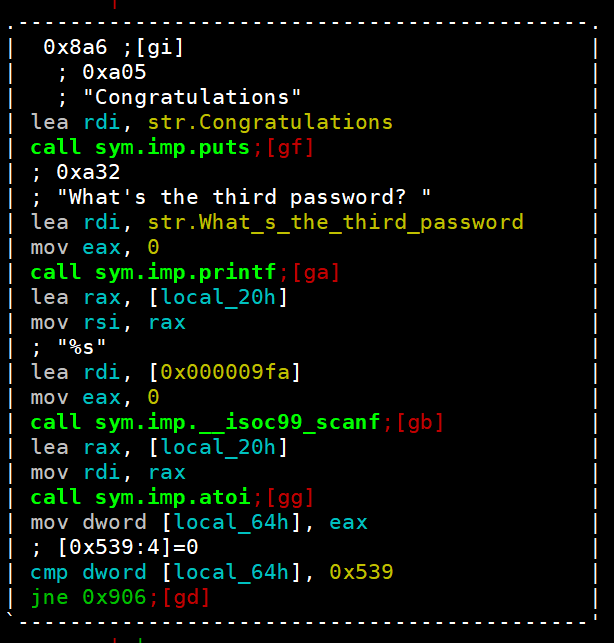
我们是学习,结果不重要,其实这还有个编码转化的工具
base64,hex,raw等都可以,不错
# rax2 -h
Usage: rax2 [options] [expr ...]
=[base] ; rax2 =10 0x46 -> output in base 10
int -> hex ; rax2 10
hex -> int ; rax2 0xa
-int -> hex ; rax2 -77
-hex -> int ; rax2 0xffffffb3
int -> bin ; rax2 b30
int -> ternary ; rax2 t42
bin -> int ; rax2 1010d
ternary -> int ; rax2 1010dt
float -> hex ; rax2 3.33f
hex -> float ; rax2 Fx40551ed8
oct -> hex ; rax2 35o
hex -> oct ; rax2 Ox12 (O is a letter)
bin -> hex ; rax2 1100011b
hex -> bin ; rax2 Bx63
ternary -> hex ; rax2 212t
hex -> ternary ; rax2 Tx23
raw -> hex ; rax2 -S < /binfile
hex -> raw ; rax2 -s 414141
-l ; append newline to output (for -E/-D/-r/..
-b bin -> str ; rax2 -b 01000101 01110110
-B str -> bin ; rax2 -B hello
-d force integer ; rax2 -d 3 -> 3 instead of 0x3
-e swap endianness ; rax2 -e 0x33
-D base64 decode ;
-E base64 encode ;
-f floating point ; rax2 -f 6.3+2.1
-F stdin slurp code hex ; rax2 -F < shellcode.c
-h help ; rax2 -h
-k keep base ; rax2 -k 33+3 -> 36
-K randomart ; rax2 -K 0x34 1020304050
-L bin -> hex(bignum) ; rax2 -L 111111111 # 0x1ff
-n binary number ; rax2 -n 0x1234 # 34120000
-N binary number ; rax2 -N 0x1234 # \x34\x12\x00\x00
-r r2 style output ; rax2 -r 0x1234
-s hexstr -> raw ; rax2 -s 43 4a 50
-S raw -> hexstr ; rax2 -S < /bin/ls > ls.hex
-t tstamp -> str ; rax2 -t 1234567890
-x hash string ; rax2 -x linux osx
-u units ; rax2 -u 389289238 # 317.0M
-w signed word ; rax2 -w 16 0xffff
-v version ; rax2 -v那么第三个password就是1337
# rax2 0x539
1337那最终flag就可以出来了
# ./crackme
What's the password? radare2
Congratulations
What's the second password? 15
Congratulations
What's the third password? 1337
Congratulations
Flag is: r2{radare2 15 1337}reference
https://medium.com/@jacob16682/reverse-engineering-using-radare2-588775ea38d5 https://medium.com/@jacob16682/reverse-engineering-with-radare2-part-2-83b71df7ffe4
本文参与 腾讯云自媒体同步曝光计划,分享自作者个人站点/博客。
原始发表:2018-02-02,如有侵权请联系 cloudcommunity@tencent.com 删除
评论
登录后参与评论
推荐阅读
目录

