针对各种IT系统连接数据库配置文件内容的加密方案
针对各种IT系统连接数据库配置文件内容的加密方案

1. 引言:那些年我们踩过的坑
还记得那个深夜,运维小王因为一个配置文件的明文密码泄露,导致整个生产数据库被"友好访问"的故事吗?或者那次代码提交时,不小心把数据库连接字符串推到了公开仓库的尴尬瞬间?
数据库配置文件就像是我们系统的"身份证",里面包含了连接地址、用户名、密码等敏感信息。如果这些信息被明文存储,那就相当于把家门钥匙放在门垫下面——看似方便,实则危险重重。
2. 现状分析:为什么配置文件需要加密
2.1 常见的安全风险
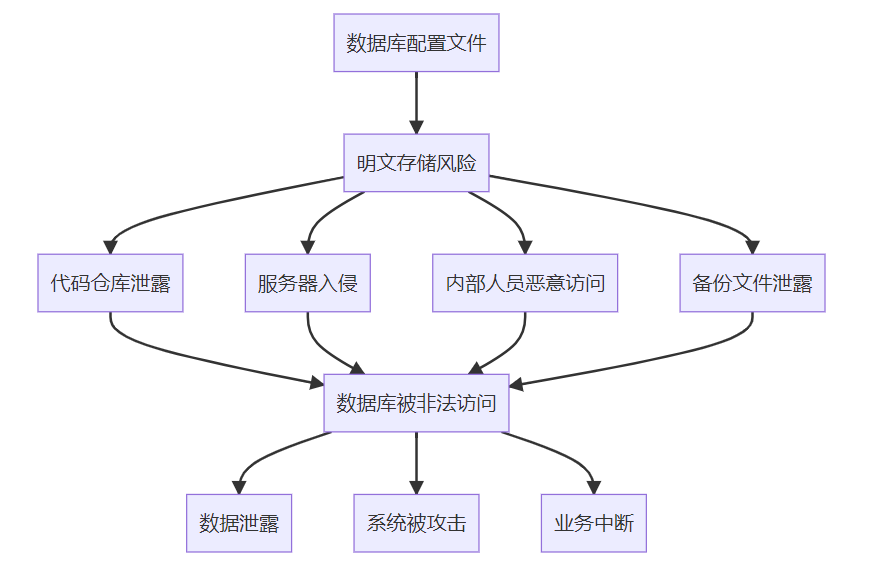
2.2 典型的配置文件示例
大家是不是经常看到这样的配置:
# application.properties - 危险示例
spring.datasource.url=jdbc:mysql://localhost:3306/mydb
spring.datasource.username=root
spring.datasource.password=123456这种明文配置就像是在大街上大喊:“我的密码是123456!”
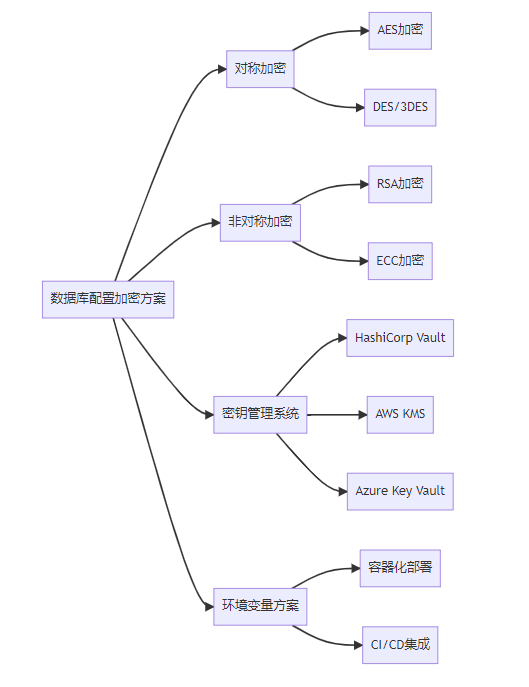
3. 加密方案总览
让我们来看看业界主流的几种加密方案架构:
4. 对称加密方案详解
4.1 AES加密实现
对称加密就像是使用同一把钥匙来锁门和开门,简单粗暴但有效。
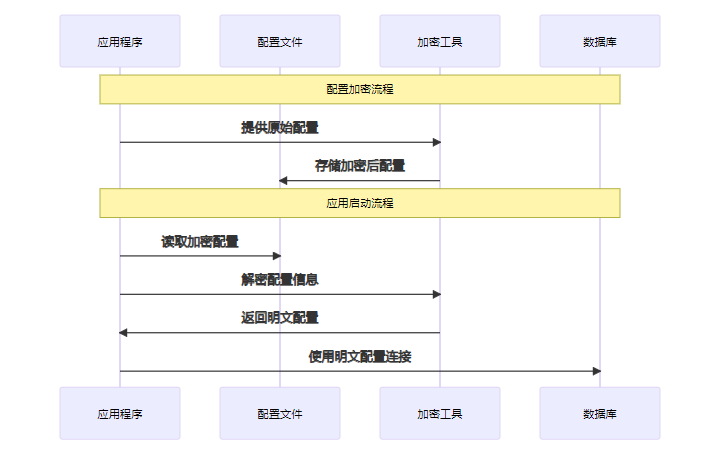
4.2 实现示例
加密工具类:
public class ConfigEncryptor {
private static final String ALGORITHM = "AES/CBC/PKCS5Padding";
private static final String KEY_ALGORITHM = "AES";
public static String encrypt(String plainText, String key) {
try {
SecretKeySpec secretKey = new SecretKeySpec(key.getBytes(), KEY_ALGORITHM);
Cipher cipher = Cipher.getInstance(ALGORITHM);
cipher.init(Cipher.ENCRYPT_MODE, secretKey);
byte[] encrypted = cipher.doFinal(plainText.getBytes());
return Base64.getEncoder().encodeToString(encrypted);
} catch (Exception e) {
throw new RuntimeException("加密失败", e);
}
}
public static String decrypt(String encryptedText, String key) {
// 解密逻辑...
}
}配置文件使用:
# application.properties
spring.datasource.url=jdbc:mysql://localhost:3306/mydb
spring.datasource.username=root
spring.datasource.password=ENC(A1B2C3D4E5F6...)4.3 Spring Boot集成
Spring Boot提供了很方便的加密配置支持:
<dependency>
<groupId>com.github.ulisesbocchio</groupId>
<artifactId>jasypt-spring-boot-starter</artifactId>
<version>3.0.4</version>
</dependency>5. 非对称加密方案
5.1 RSA加密架构
非对称加密就像是一个神奇的邮箱,任何人都可以往里投信(公钥加密),但只有邮箱主人才能取信(私钥解密)。
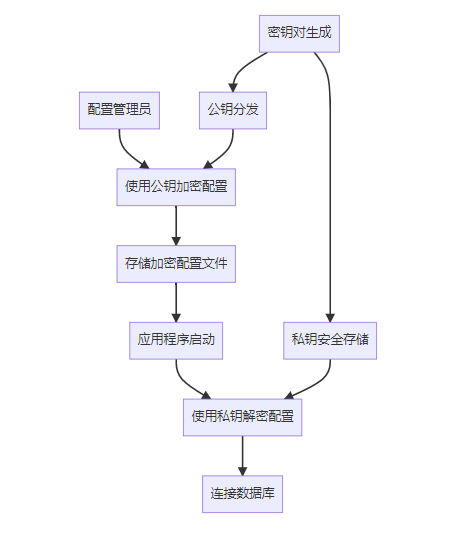
5.2 实施流程
- 密钥对生成
# 生成RSA私钥
openssl genrsa -out private_key.pem 2048
# 提取公钥
openssl rsa -in private_key.pem -pubout -out public_key.pem- 配置加密
# 使用公钥加密数据库密码
echo "mypassword" | openssl rsautl -encrypt -pubin -inkey public_key.pem | base646. 密钥管理系统方案
6.1 HashiCorp Vault架构
Vault就像是一个超级保险柜,专门用来存储各种秘密。
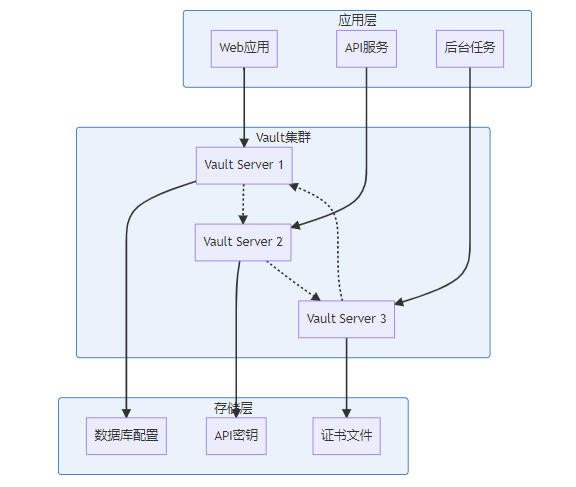
6.2 Vault集成示例
@Configuration
public class VaultConfig {
@Bean
public VaultTemplate vaultTemplate() {
VaultEndpoint endpoint = new VaultEndpoint();
endpoint.setHost("vault.company.com");
endpoint.setPort(8200);
endpoint.setScheme("https");
VaultTemplate template = new VaultTemplate(endpoint,
new TokenAuthentication("your-vault-token"));
return template;
}
}
@Service
public class DatabaseConfigService {
@Autowired
private VaultTemplate vaultTemplate;
public String getDatabasePassword() {
VaultResponse response = vaultTemplate.read("secret/database");
return (String) response.getData().get("password");
}
}7. 环境变量与容器化方案
7.1 容器化部署架构
在容器化时代,我们可以把敏感配置和应用程序彻底分离:
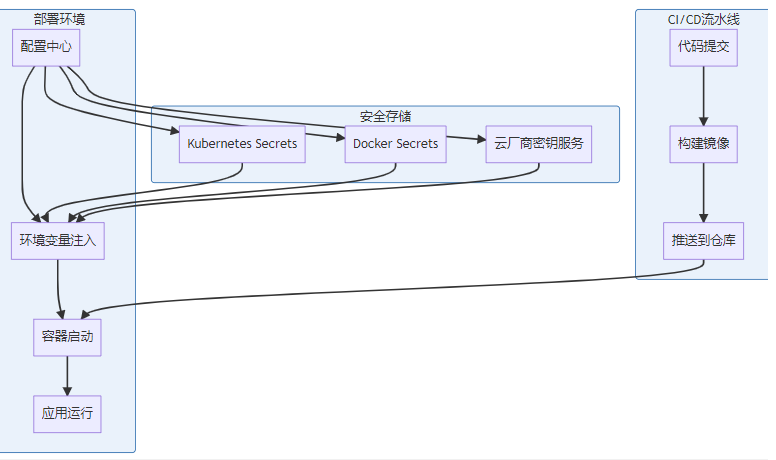
7.2 Docker Compose示例
version: '3.8'
services:
app:
image: myapp:latest
environment:
- DB_HOST=${DB_HOST}
- DB_USER=${DB_USER}
- DB_PASSWORD_FILE=/run/secrets/db_password
secrets:
- db_password
secrets:
db_password:
external: true7.3 Kubernetes配置
apiVersion: v1
kind: Secret
metadata:
name: db-secret
type: Opaque
data:
password: bXlwYXNzd29yZA== # base64编码
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: myapp
spec:
template:
spec:
containers:
- name: app
image: myapp:latest
env:
- name: DB_PASSWORD
valueFrom:
secretKeyRef:
name: db-secret
key: password8. ASP.NET项目专属加密方案
作为.NET生态系统的重要组成部分,ASP.NET Web和ASP.NET Core提供了一些"原汁原味"的配置加密方案。就像微软给我们准备的专属工具箱,用起来那叫一个顺手!
8.1 ASP.NET Web (.NET Framework) 方案
8.1.1 web.config配置文件加密
传统的ASP.NET Web项目使用web.config存储配置,微软提供了内置的加密机制:
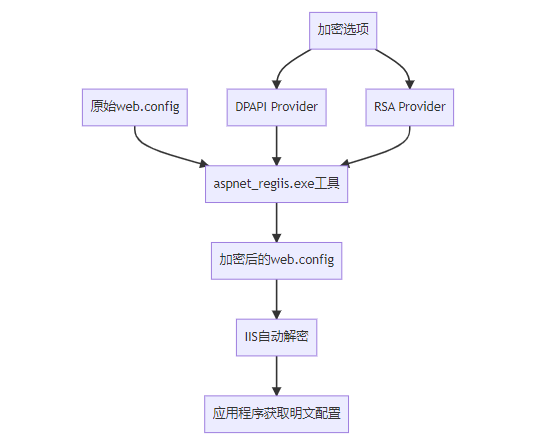
使用aspnet_regiis.exe加密connectionStrings节:
# 加密数据库连接字符串
aspnet_regiis.exe -pef "connectionStrings" "C:\YourWebSite" -prov "DataProtectionConfigurationProvider"
# 或者使用RSA加密
aspnet_regiis.exe -pef "connectionStrings" "C:\YourWebSite" -prov "RsaProtectedConfigurationProvider"加密前的web.config:
<configuration>
<connectionStrings>
<add name="DefaultConnection"
connectionString="Server=localhost;Database=MyDB;User Id=sa;Password=MyPassword123;"
providerName="System.Data.SqlClient" />
</connectionStrings>
</configuration>加密后的web.config:
<configuration>
<connectionStrings configProtectionProvider="DataProtectionConfigurationProvider">
<EncryptedData>
<CipherData>
<CipherValue>AQAAANCMnd8BFdERjHoAwE/Cl+sBAAAA...</CipherValue>
</CipherData>
</EncryptedData>
</connectionStrings>
</configuration>8.1.2 自定义加密配置节
public class EncryptedConnectionSection : ConfigurationSection
{
[ConfigurationProperty("connectionString", IsRequired = true)]
public string ConnectionString
{
get
{
string encrypted = (string)this["connectionString"];
return DecryptConnectionString(encrypted);
}
set { this["connectionString"] = EncryptConnectionString(value); }
}
private string DecryptConnectionString(string encrypted)
{
// 使用AES解密逻辑
return AESHelper.Decrypt(encrypted, GetMachineKey());
}
private string EncryptConnectionString(string plainText)
{
// 使用AES加密逻辑
return AESHelper.Encrypt(plainText, GetMachineKey());
}
private string GetMachineKey()
{
// 从machine.config获取密钥或使用其他安全方式
return ConfigurationManager.AppSettings["EncryptionKey"];
}
}8.1.3 Machine Key配置
<system.web>
<machineKey
validationKey="[128位十六进制密钥]"
decryptionKey="[48位或24位十六进制密钥]"
validation="HMACSHA256"
decryption="AES" />
</system.web>8.2 ASP.NET Core方案
8.2.1 Secret Manager工具(开发环境)
ASP.NET Core的Secret Manager就像是开发者的"小金库",专门用来存储开发阶段的敏感信息:
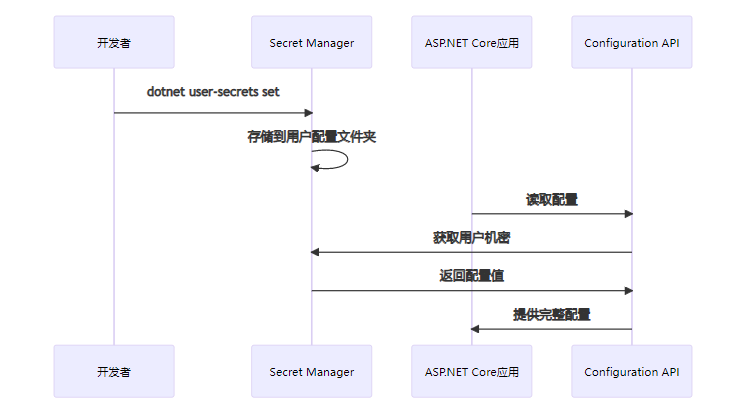
使用Secret Manager:
# 初始化用户机密
dotnet user-secrets init
# 设置数据库连接字符串
dotnet user-secrets set "ConnectionStrings:DefaultConnection" "Server=localhost;Database=MyDB;User Id=sa;Password=MyPassword123;"
# 设置其他敏感配置
dotnet user-secrets set "ApiKeys:ThirdPartyService" "your-secret-api-key"
# 查看所有机密
dotnet user-secrets list在代码中使用:
public class Startup
{
public Startup(IConfiguration configuration)
{
Configuration = configuration;
}
public IConfiguration Configuration { get; }
public void ConfigureServices(IServiceCollection services)
{
// 自动从多个配置源读取,包括用户机密
string connectionString = Configuration.GetConnectionString("DefaultConnection");
services.AddDbContext<ApplicationDbContext>(options =>
options.UseSqlServer(connectionString));
}
}8.2.2 自定义配置加密Provider
public class EncryptedConfigurationProvider : ConfigurationProvider
{
private readonly string _encryptionKey;
private readonly string _configPath;
public EncryptedConfigurationProvider(string configPath, string encryptionKey)
{
_configPath = configPath;
_encryptionKey = encryptionKey;
}
public override void Load()
{
var encryptedContent = File.ReadAllText(_configPath);
var decryptedContent = AESHelper.Decrypt(encryptedContent, _encryptionKey);
var jsonDocument = JsonDocument.Parse(decryptedContent);
Data = ParseJsonElement(jsonDocument.RootElement);
}
private Dictionary<string, string> ParseJsonElement(JsonElement element, string prefix = "")
{
var data = new Dictionary<string, string>();
foreach (var property in element.EnumerateObject())
{
var key = string.IsNullOrEmpty(prefix) ? property.Name : $"{prefix}:{property.Name}";
if (property.Value.ValueKind == JsonValueKind.Object)
{
var nestedData = ParseJsonElement(property.Value, key);
foreach (var item in nestedData)
{
data[item.Key] = item.Value;
}
}
else
{
data[key] = property.Value.ToString();
}
}
return data;
}
}
public class EncryptedConfigurationSource : IConfigurationSource
{
private readonly string _configPath;
private readonly string _encryptionKey;
public EncryptedConfigurationSource(string configPath, string encryptionKey)
{
_configPath = configPath;
_encryptionKey = encryptionKey;
}
public IConfigurationProvider Build(IConfigurationBuilder builder)
{
return new EncryptedConfigurationProvider(_configPath, _encryptionKey);
}
}注册自定义Provider:
public class Program
{
public static void Main(string[] args)
{
CreateHostBuilder(args).Build().Run();
}
public static IHostBuilder CreateHostBuilder(string[] args) =>
Host.CreateDefaultBuilder(args)
.ConfigureAppConfiguration((context, config) =>
{
var encryptionKey = Environment.GetEnvironmentVariable("CONFIG_ENCRYPTION_KEY");
if (!string.IsNullOrEmpty(encryptionKey))
{
config.Add(new EncryptedConfigurationSource("encrypted-config.json", encryptionKey));
}
})
.ConfigureWebHostDefaults(webBuilder =>
{
webBuilder.UseStartup<Startup>();
});
}8.2.3 Azure Key Vault集成
ASP.NET Core与Azure Key Vault的集成简直是"天作之合":
public class Program
{
public static void Main(string[] args)
{
CreateHostBuilder(args).Build().Run();
}
public static IHostBuilder CreateHostBuilder(string[] args) =>
Host.CreateDefaultBuilder(args)
.ConfigureAppConfiguration((context, config) =>
{
if (context.HostingEnvironment.IsProduction())
{
var keyVaultEndpoint = new Uri(Environment.GetEnvironmentVariable("VaultUri"));
config.AddAzureKeyVault(keyVaultEndpoint, new DefaultAzureCredential());
}
})
.ConfigureWebHostDefaults(webBuilder =>
{
webBuilder.UseStartup<Startup>();
});
}8.2.4 配置加密工具类
public static class ConfigurationExtensions
{
public static string GetEncryptedConnectionString(this IConfiguration configuration, string name)
{
var encryptedValue = configuration.GetConnectionString(name);
if (string.IsNullOrEmpty(encryptedValue))
return null;
if (encryptedValue.StartsWith("ENC(") && encryptedValue.EndsWith(")"))
{
var encrypted = encryptedValue.Substring(4, encryptedValue.Length - 5);
var key = configuration["Encryption:Key"];
return AESHelper.Decrypt(encrypted, key);
}
return encryptedValue;
}
public static void AddEncryptedJsonFile(this IConfigurationBuilder builder, string path, string encryptionKey)
{
builder.Add(new EncryptedConfigurationSource(path, encryptionKey));
}
}使用示例:
public void ConfigureServices(IServiceCollection services)
{
// 使用加密的连接字符串
string connectionString = Configuration.GetEncryptedConnectionString("DefaultConnection");
services.AddDbContext<ApplicationDbContext>(options =>
options.UseSqlServer(connectionString));
}8.3 .NET项目配置加密最佳实践
8.3.1 环境分离策略
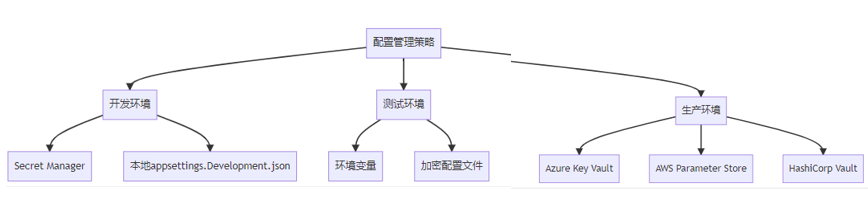
8.3.2 配置文件层级
// appsettings.json (基础配置,不含敏感信息)
{
"Logging": {
"LogLevel": {
"Default": "Information"
}
},
"AllowedHosts": "*",
"ConnectionStrings": {
"DefaultConnection": "ENC(A1B2C3D4E5F6...)"
}
}
// appsettings.Development.json (开发环境覆盖)
{
"ConnectionStrings": {
"DefaultConnection": "Server=localhost;Database=DevDB;Integrated Security=true;"
}
}
// appsettings.Production.json (生产环境覆盖)
{
"ConnectionStrings": {
"DefaultConnection": "UseKeyVault"
}
}8.3.3 配置验证
public class DatabaseOptions
{
public const string SectionName = "Database";
[Required]
public string ConnectionString { get; set; }
[Range(1, 3600)]
public int CommandTimeout { get; set; } = 30;
public bool EnableSensitiveDataLogging { get; set; } = false;
}
// 在Startup.cs中注册和验证
public void ConfigureServices(IServiceCollection services)
{
services.Configure<DatabaseOptions>(Configuration.GetSection(DatabaseOptions.SectionName));
services.AddOptions<DatabaseOptions>()
.Bind(Configuration.GetSection(DatabaseOptions.SectionName))
.ValidateDataAnnotations()
.Validate(options => !string.IsNullOrEmpty(options.ConnectionString),
"数据库连接字符串不能为空");
}9. 最佳实践与注意事项
8.1 安全策略矩阵
方案类型 | 安全等级 | 实施复杂度 | 维护成本 | 适用场景 |
|---|---|---|---|---|
对称加密 | ⭐⭐⭐ | ⭐⭐ | ⭐⭐ | 中小型项目 |
非对称加密 | ⭐⭐⭐⭐ | ⭐⭐⭐ | ⭐⭐⭐ | 高安全要求 |
密钥管理系统 | ⭐⭐⭐⭐⭐ | ⭐⭐⭐⭐ | ⭐⭐⭐⭐ | 企业级应用 |
环境变量 | ⭐⭐⭐ | ⭐ | ⭐ | 容器化部署 |
8.2 关键原则
- 密钥轮换:定期更换加密密钥,就像定期换门锁一样
- 权限最小化:只给需要的人和系统必要的权限
- 审计日志:记录所有敏感操作,做到有迹可循
- 备份策略:确保密钥和配置的安全备份
8.3 实施流程图
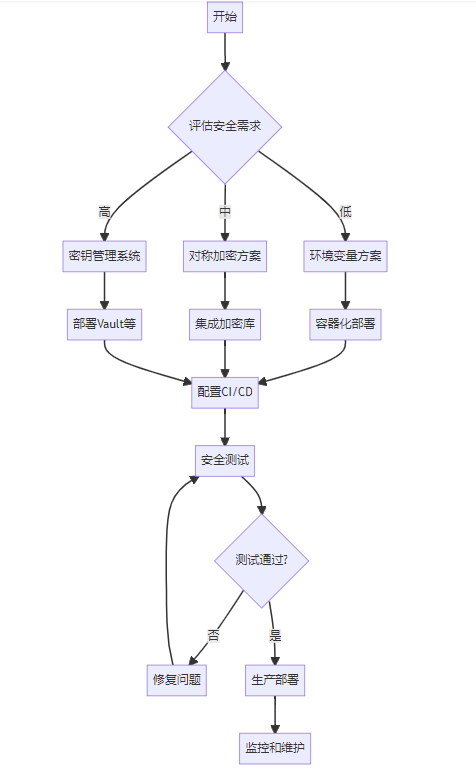
8.4 常见陷阱
- 密钥硬编码:千万别把密钥写死在代码里,这就像把保险柜密码贴在保险柜上
- 权限过大:不要给应用程序不必要的权限,遵循最小权限原则
- 忘记轮换:定期更换密钥,不要让一个密钥用到天荒地老
- 日志泄露:确保敏感信息不会出现在日志文件中
10. 总结
数据库配置文件加密不是一个"可选项",而是现代应用安全的"必需品"。就像我们出门要锁门一样,保护敏感配置信息是每个开发者的基本素养。
选择合适的加密方案需要平衡安全性、复杂性和维护成本。对于大多数项目来说:
- 小型项目:环境变量 + 容器化部署
- 中型项目:对称加密 + 密钥管理
- 大型企业:专业密钥管理系统 + 完整安全策略
- .NET Framework项目:aspnet_regiis.exe + Machine Key配置
- .NET Core项目:Secret Manager (开发) + Azure Key Vault (生产)
- 微服务架构:统一的密钥管理中心 + 服务间加密通信
记住,安全不是一蹴而就的,而是一个持续改进的过程。今天你保护好了配置文件,明天数据库就会感谢你的!
特别提醒.NET开发者:
- 开发环境优先使用Secret Manager,简单安全又方便
- 生产环境强烈推荐Azure Key Vault或其他云服务商的密钥管理服务
- 不要在web.config或appsettings.json中存储明文密码
- 利用好.NET Core的配置系统,它已经为你做了很多安全考虑
💡 小贴士:安全是一场马拉松,不是百米冲刺。持续关注和改进你的安全措施,让黑客们知难而退!
关键词:数据库配置加密、敏感信息保护、密钥管理、安全部署、容器化安全
本文适用于各种编程语言和框架,具体实现可能因技术栈而异。在实施任何安全方案前,请务必在测试环境充分验证。

