PowerHuntShares:一款针对活动目录域安全的分析与审计工具
PowerHuntShares:一款针对活动目录域安全的分析与审计工具

关于PowerHuntShares
PowerHuntShares是一款针对活动目录域安全的分析与审计工具,该工具本质上是一个PowerShell脚本,可以帮助广大研究人员清点、分析和报告加入到活动目录域中计算机上SMB共享上配置的过度权限。在该工具的帮助下,IAM和其他红队研究人员可以更好地了解SMB共享相关的攻击面,并提供相关的安全数据见解,以帮助企业和各大组织以更加安全的方式管理大规模分组共享。
功能介绍
当前版本的PowerHuntShares支持下列功能:
1、使用当前用户上下文、凭据或明文用户/密码进行身份验证; 2、自动发现与活动目录域关联的可访问系统。它还将根据可用的开放端口筛选活动目录中的计算机; 3、以单个计算机、计算机列表或发现的活动目录计算机为目标(默认); 4、使用PowerShell从目标计算机收集SMB共享的ACL信息; 5、支持分析收集到的共享ACL数据; 6、以HTML和CSV文件格式生成过度权限检测详细报告;
SMB共享的ACL分配过多,这是一个系统性问题,也是所有企业和组织都难以应对的攻击面。因此,该项目的目标就是为了解决这个问题,并构建了一个更好的共享收集和数据洞察引擎,以帮助广大研究人员更好地了解活动目录域的安全态势。
工具下载
广大研究人员可以使用下列命令将该项目源码克隆至本地:
git clone https://github.com/NetSPI/PowerHuntShares.git工具配置
下面给出的命令可以帮助我们将将PowerHuntShare加载到当前PowerShell会话中,请注意,每次运行PowerShell时都必须运行其中一个命令,且不是持久化的:
# 绕过执行策略限制
Set-ExecutionPolicy -Scope Process Bypass
# 导入存在于当前目录中的模块
Import-Module .\PowerHuntShares.psm1
# 降低SSL操作登记以支持与github连接
[System.Net.ServicePointManager]::ServerCertificateValidationCallback = {$true}
[Net.ServicePointManager]::SecurityProtocol =[Net.SecurityProtocolType]::Tls12
# 下载并将PowerHuntShares.psm1导入到内存中
IEX(New-Object System.Net.WebClient).DownloadString("https://raw.githubusercontent.com/NetSPI/PowerHuntShares/main/PowerHuntShares.psm1")工具使用样例
注意事项:该工具所有的操作命令需要以非特权域用户运行。
.EXAMPLE 1: 从一个域计算机运行,默认执行活动目录计算机扫描。
PS C:\temp\test> Invoke-HuntSMBShares -Threads 100 -OutputDirectory c:\temp\test
.EXAMPLE 2: 使用其他域凭据从域计算机运行,默认情况下执行活动目录计算机扫描。
PS C:\temp\test> Invoke-HuntSMBShares -Threads 100 -OutputDirectory c:\temp\test -Credentials domain\user
.EXAMPLE 3: 以当前用户身份从域计算机运行,文件中的目标主机每行设置一个。
PS C:\temp\test> Invoke-HuntSMBShares -Threads 100 -OutputDirectory c:\temp\test -HostList c:\temp\hosts.txt
.EXAMPLE 4: 使用凭据从非域计算机运行,默认情况下执行活动目录计算机扫描。
C:\temp\test> runas /netonly /user:domain\user PowerShell.exe
PS C:\temp\test> Import-Module PowerHuntShares.psm1
PS C:\temp\test> Invoke-HuntSMBShares -Threads 100 -RunSpaceTimeOut 10 -OutputDirectory c:\folder\ -DomainController 10.1.1.1 -Credential domain\user
===============================================================
PowerHuntShares
===============================================================
This function automates the following tasks:
o Determine current computer's domain
o Enumerate domain computers
o Filter for computers that respond to ping reqeusts
o Filter for computers that have TCP 445 open and accessible
o Enumerate SMB shares
o Enumerate SMB share permissions
o Identify shares with potentially excessive privielges
o Identify shares that provide reads & write access
o Identify shares thare are high risk
o Identify common share owners, names, & directory listings
o Generate creation, last written, & last accessed timelines
o Generate html summary report and detailed csv files
Note: This can take hours to run in large environments.
---------------------------------------------------------------
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
---------------------------------------------------------------
SHARE DISCOVERY
---------------------------------------------------------------
[*][03/01/2021 09:35] Scan Start
[*][03/01/2021 09:35] Output Directory: c:\temp\smbshares\SmbShareHunt-03012021093504
[*][03/01/2021 09:35] Successful connection to domain controller: dc1.demo.local
[*][03/01/2021 09:35] Performing LDAP query for computers associated with the demo.local domain
[*][03/01/2021 09:35] - 245 computers found
[*][03/01/2021 09:35] Pinging 245 computers
[*][03/01/2021 09:35] - 55 computers responded to ping requests.
[*][03/01/2021 09:35] Checking if TCP Port 445 is open on 55 computers
[*][03/01/2021 09:36] - 49 computers have TCP port 445 open.
[*][03/01/2021 09:36] Getting a list of SMB shares from 49 computers
[*][03/01/2021 09:36] - 217 SMB shares were found.
[*][03/01/2021 09:36] Getting share permissions from 217 SMB shares
[*][03/01/2021 09:37] - 374 share permissions were enumerated.
[*][03/01/2021 09:37] Getting directory listings from 33 SMB shares
[*][03/01/2021 09:37] - Targeting up to 3 nested directory levels
[*][03/01/2021 09:37] - 563 files and folders were enumerated.
[*][03/01/2021 09:37] Identifying potentially excessive share permissions
[*][03/01/2021 09:37] - 33 potentially excessive privileges were found across 12 systems..
[*][03/01/2021 09:37] Scan Complete
---------------------------------------------------------------
SHARE ANALYSIS
---------------------------------------------------------------
[*][03/01/2021 09:37] Analysis Start
[*][03/01/2021 09:37] - 14 shares can be read across 12 systems.
[*][03/01/2021 09:37] - 1 shares can be written to across 1 systems.
[*][03/01/2021 09:37] - 46 shares are considered non-default across 32 systems.
[*][03/01/2021 09:37] - 0 shares are considered high risk across 0 systems
[*][03/01/2021 09:37] - Identified top 5 owners of excessive shares.
[*][03/01/2021 09:37] - Identified top 5 share groups.
[*][03/01/2021 09:37] - Identified top 5 share names.
[*][03/01/2021 09:37] - Identified shares created in last 90 days.
[*][03/01/2021 09:37] - Identified shares accessed in last 90 days.
[*][03/01/2021 09:37] - Identified shares modified in last 90 days.
[*][03/01/2021 09:37] Analysis Complete
---------------------------------------------------------------
SHARE REPORT SUMMARY
---------------------------------------------------------------
[*][03/01/2021 09:37] Domain: demo.local
[*][03/01/2021 09:37] Start time: 03/01/2021 09:35:04
[*][03/01/2021 09:37] End time: 03/01/2021 09:37:27
[*][03/01/2021 09:37] Run time: 00:02:23.2759086
[*][03/01/2021 09:37]
[*][03/01/2021 09:37] COMPUTER SUMMARY
[*][03/01/2021 09:37] - 245 domain computers found.
[*][03/01/2021 09:37] - 55 (22.45%) domain computers responded to ping.
[*][03/01/2021 09:37] - 49 (20.00%) domain computers had TCP port 445 accessible.
[*][03/01/2021 09:37] - 32 (13.06%) domain computers had shares that were non-default.
[*][03/01/2021 09:37] - 12 (4.90%) domain computers had shares with potentially excessive privileges.
[*][03/01/2021 09:37] - 12 (4.90%) domain computers had shares that allowed READ access.
[*][03/01/2021 09:37] - 1 (0.41%) domain computers had shares that allowed WRITE access.
[*][03/01/2021 09:37] - 0 (0.00%) domain computers had shares that are HIGH RISK.
[*][03/01/2021 09:37]
[*][03/01/2021 09:37] SHARE SUMMARY
[*][03/01/2021 09:37] - 217 shares were found. We expect a minimum of 98 shares
[*][03/01/2021 09:37] because 49 systems had open ports and there are typically two default shares.
[*][03/01/2021 09:37] - 46 (21.20%) shares across 32 systems were non-default.
[*][03/01/2021 09:37] - 14 (6.45%) shares across 12 systems are configured with 33 potentially excessive ACLs.
[*][03/01/2021 09:37] - 14 (6.45%) shares across 12 systems allowed READ access.
[*][03/01/2021 09:37] - 1 (0.46%) shares across 1 systems allowed WRITE access.
[*][03/01/2021 09:37] - 0 (0.00%) shares across 0 systems are considered HIGH RISK.
[*][03/01/2021 09:37]
[*][03/01/2021 09:37] SHARE ACL SUMMARY
[*][03/01/2021 09:37] - 374 ACLs were found.
[*][03/01/2021 09:37] - 374 (100.00%) ACLs were associated with non-default shares.
[*][03/01/2021 09:37] - 33 (8.82%) ACLs were found to be potentially excessive.
[*][03/01/2021 09:37] - 32 (8.56%) ACLs were found that allowed READ access.
[*][03/01/2021 09:37] - 1 (0.27%) ACLs were found that allowed WRITE access.
[*][03/01/2021 09:37] - 0 (0.00%) ACLs were found that are associated with HIGH RISK share names.
[*][03/01/2021 09:37]
[*][03/01/2021 09:37] - The 5 most common share names are:
[*][03/01/2021 09:37] - 9 of 14 (64.29%) discovered shares are associated with the top 5 share names.
[*][03/01/2021 09:37] - 4 backup
[*][03/01/2021 09:37] - 2 ssms
[*][03/01/2021 09:37] - 1 test2
[*][03/01/2021 09:37] - 1 test1
[*][03/01/2021 09:37] - 1 users
[*] ----------------------------------------------
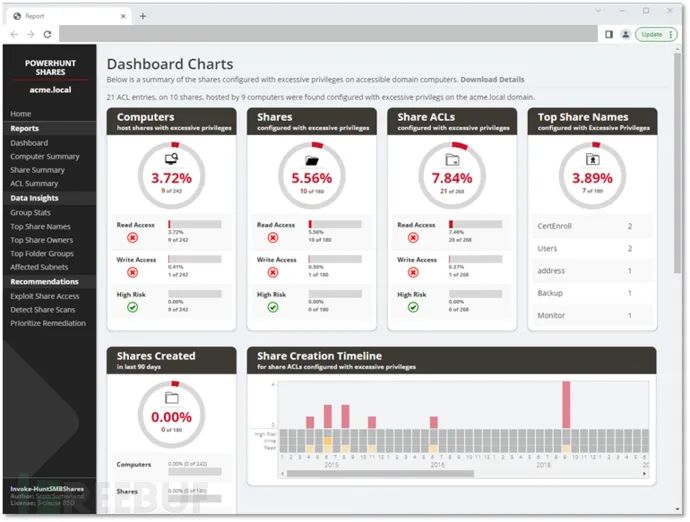
HTML报告样例
许可证协议
本项目的开发与发布遵循BSD3-clause开源许可证协议。
项目地址
PowerHuntShares:https://github.com/NetSPI/PowerHuntShares
参考资料
https://www.netspi.com/blog/technical/network-penetration-testing/network-share-permissions-powerhuntshares/ https://www.youtube.com/watch?v=TtwyQchCz6E https://www.slideshare.net/nullbind/into-the-abyss-evaluating-active-directory-smb-shares-on-scale-secure360-251762721
