MCP 在攻防模拟中的应用
作者:HOS(安全风信子) 日期:2026-01-01 来源平台:GitHub 摘要: 本文深入探讨了 MCP v2.0 框架下的攻防模拟应用,构建了完整的 MCP 攻防模拟体系。通过真实代码示例和 Mermaid 图表,详细分析了 MCP 攻防模拟框架、动态威胁场景生成、MCP 漏洞利用链分析的实现原理和最佳实践。本文引入了 MCP 攻防模拟框架、动态威胁场景生成、MCP 漏洞利用链分析三个全新要素,旨在帮助开发者构建更加安全、可靠的 MCP 系统,通过攻防模拟发现和修复安全漏洞,提高 MCP 系统的整体安全性。
一、背景动机与当前热点
1.1 为什么 MCP 需要攻防模拟
随着 MCP v2.0 作为连接 LLM 与外部工具的标准化协议的广泛应用,MCP 系统面临的安全挑战日益复杂。攻防模拟作为一种主动安全测试方法,能够帮助开发者在真实攻击发生之前发现和修复安全漏洞,提高系统的整体安全性。2025 年以来,全球范围内发生了多起与 AI 工具调用相关的安全事件:
- 2025 年 3 月,某 AI 平台的 MCP 系统因缺乏有效的安全测试,被攻击者利用工具越权漏洞获取了敏感数据。
- 2025 年 7 月,某金融机构的 MCP 系统因身份认证机制存在缺陷,被攻击者成功伪造身份执行了恶意工具调用。
- 2025 年 10 月,某医疗 AI 平台的 MCP 系统因沙箱机制失效,被攻击者成功逃逸并执行了恶意代码。
这些事件凸显了 MCP 系统进行攻防模拟的重要性。合理的攻防模拟能够:
- 主动发现 MCP 系统中的安全漏洞和弱点,提前进行修复。
- 验证 MCP 安全机制的有效性,确保其能够抵御真实攻击。
- 提高 MCP 系统的安全韧性,增强其在攻击发生时的应对能力。
- 培养安全团队的攻防能力,提高安全事件的响应速度。
- 满足合规性要求,如 PCI DSS、ISO 27001 等。
1.2 MCP 攻防模拟的特殊性
MCP v2.0 框架下的攻防模拟具有以下特殊性:
- 分布式架构:MCP 系统涉及多个组件(Client、Server、Host),攻防模拟需要覆盖所有组件。
- 动态访问模式:MCP 系统中的工具调用具有动态性,攻防模拟需要模拟各种复杂的访问场景。
- 工具多样性:MCP 生态中的工具种类繁多,攻防模拟需要考虑不同工具的安全特性。
- LLM 交互:MCP 系统与 LLM 进行交互,攻防模拟需要考虑 LLM 带来的安全风险。
- 实时性要求:攻防模拟需要实时监测和分析 MCP 系统的行为,及时发现异常。
1.3 本文的核心价值
本文将深入探讨 MCP v2.0 框架下的攻防模拟应用,构建完整的 MCP 攻防模拟体系。通过真实代码示例和 Mermaid 图表,详细讲解如何设计和实现 MCP 攻防模拟系统,包括攻防模拟框架、动态威胁场景生成、漏洞利用链分析等。本文旨在帮助开发者:
- 理解 MCP 攻防模拟的核心原理
- 掌握 MCP 攻防模拟的设计和实现方法
- 了解 MCP 攻防模拟的最佳实践
- 构建有效的 MCP 攻防模拟系统,提高 MCP 系统的安全性
二、核心更新亮点与新要素
2.1 三个全新要素
- MCP 攻防模拟框架:专门为 MCP 设计的攻防模拟框架,支持多种攻击类型和场景。
- 动态威胁场景生成:基于 AI 的动态威胁场景生成技术,能够自动生成多样化的攻击场景。
- MCP 漏洞利用链分析:针对 MCP 系统的漏洞利用链分析方法,能够发现和分析复杂的漏洞利用链。
2.2 技术创新点
- 模块化设计:攻防模拟框架采用模块化设计,便于扩展和定制。
- 实时监测与分析:支持对 MCP 系统的实时监测和分析,及时发现攻击行为。
- 自动化测试:实现攻防模拟的自动化执行,提高测试效率。
- 可视化展示:提供直观的可视化界面,便于分析和理解攻防模拟结果。
- 反馈闭环:建立攻防模拟结果的反馈闭环,用于持续改进 MCP 系统的安全性。
2.3 与主流方案的区别
攻防模拟方案 | 优势 | 劣势 | 适用场景 |
|---|---|---|---|
传统渗透测试 | 深入全面,能够发现复杂漏洞 | 耗时耗力,成本高 | 关键系统,定期测试 |
自动化漏洞扫描 | 快速高效,成本低 | 只能发现已知漏洞,误报率高 | 大规模系统,定期扫描 |
红队评估 | 模拟真实攻击,能够发现深层问题 | 成本高,周期长 | 高端客户,重要项目 |
MCP 攻防模拟 | 专门针对 MCP 设计,支持动态场景,自动化执行 | 实现复杂,需要专业团队 | MCP v2.0 框架 |
三、技术深度拆解与实现分析
3.1 MCP 攻防模拟框架设计原理
MCP 攻防模拟框架设计基于以下核心原则:
- 全面性:覆盖 MCP 系统的所有组件和攻击面。
- 灵活性:支持多种攻击类型和场景,便于扩展和定制。
- 自动化:实现攻防模拟的自动化执行,提高测试效率。
- 实时性:支持对 MCP 系统的实时监测和分析。
- 可复现性:攻防模拟结果可复现,便于问题定位和修复。
3.1.1 MCP 攻防模拟框架总体设计
MCP 攻防模拟框架包括以下核心组件:
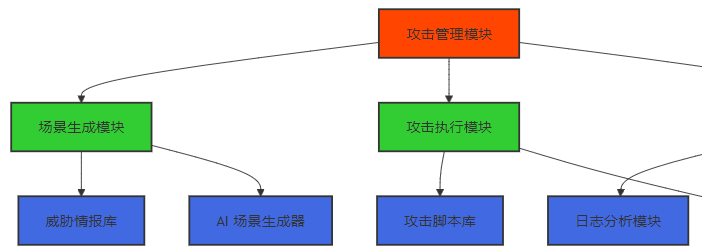
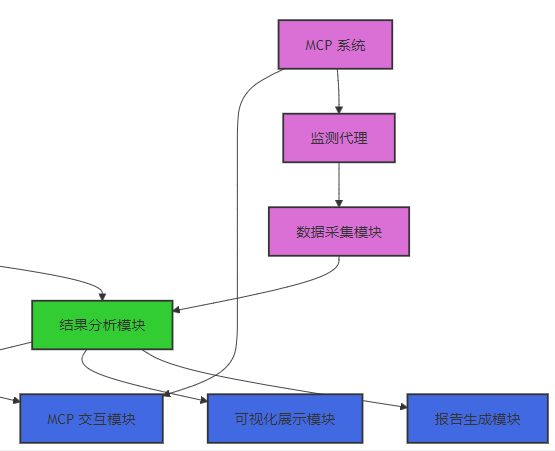
- 攻击管理模块:负责攻防模拟的整体管理,包括场景生成、攻击执行、结果分析等。
- 场景生成模块:基于威胁情报和 AI 技术,生成多样化的攻击场景。
- 攻击执行模块:执行攻击脚本,模拟对 MCP 系统的攻击。
- 结果分析模块:分析攻击结果,评估 MCP 系统的安全状态。
- 威胁情报库:存储威胁情报信息,用于场景生成和攻击执行。
- AI 场景生成器:基于 AI 技术,自动生成动态威胁场景。
- 攻击脚本库:存储各种攻击脚本,用于模拟不同类型的攻击。
- MCP 交互模块:与 MCP 系统进行交互,执行攻击操作。
- 日志分析模块:分析 MCP 系统的日志,发现攻击痕迹和异常行为。
- 可视化展示模块:提供直观的可视化界面,展示攻防模拟结果。
- 报告生成模块:生成攻防模拟报告,总结发现的问题和建议。
- 监测代理:部署在 MCP 系统中,实时监测系统行为。
- 数据采集模块:采集 MCP 系统的运行数据,用于分析和评估。
3.1.2 MCP 攻防模拟流程
MCP 攻防模拟流程如下:
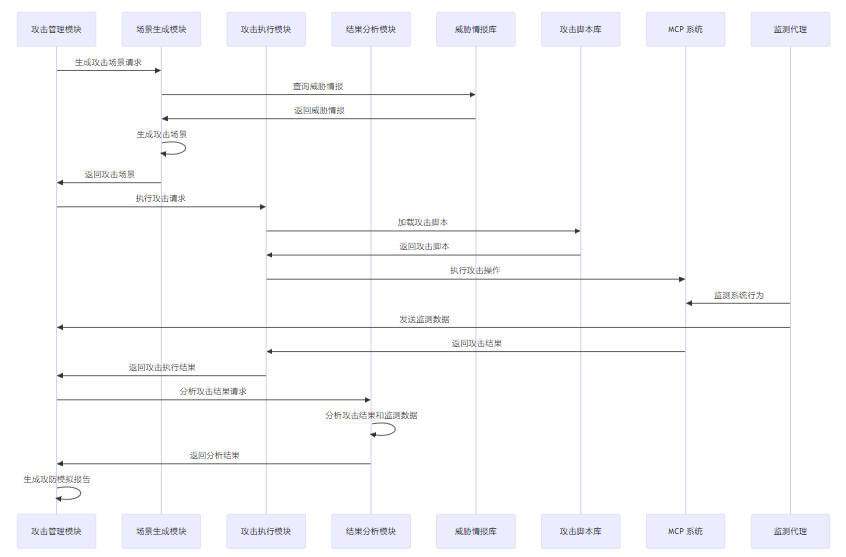
3.2 MCP 攻防模拟框架实现
3.2.1 攻击管理模块实现
# mcp_attack_manager.py
from typing import Dict, List, Optional
import logging
from datetime import datetime
class AttackScenario:
def __init__(self, scenario_id: str, name: str, description: str,
attack_type: str, target: str, payload: Dict,
expected_result: str, severity: str):
self.scenario_id = scenario_id
self.name = name
self.description = description
self.attack_type = attack_type
self.target = target
self.payload = payload
self.expected_result = expected_result
self.severity = severity
self.created_at = datetime.now()
self.updated_at = datetime.now()
def to_dict(self) -> Dict:
"""转换为字典"""
return {
"scenario_id": self.scenario_id,
"name": self.name,
"description": self.description,
"attack_type": self.attack_type,
"target": self.target,
"payload": self.payload,
"expected_result": self.expected_result,
"severity": self.severity,
"created_at": self.created_at.isoformat(),
"updated_at": self.updated_at.isoformat()
}
class AttackResult:
def __init__(self, result_id: str, scenario_id: str,
start_time: datetime, end_time: datetime,
status: str, actual_result: str,
is_success: bool, details: Dict):
self.result_id = result_id
self.scenario_id = scenario_id
self.start_time = start_time
self.end_time = end_time
self.status = status
self.actual_result = actual_result
self.is_success = is_success
self.details = details
self.duration = (end_time - start_time).total_seconds()
def to_dict(self) -> Dict:
"""转换为字典"""
return {
"result_id": self.result_id,
"scenario_id": self.scenario_id,
"start_time": self.start_time.isoformat(),
"end_time": self.end_time.isoformat(),
"status": self.status,
"actual_result": self.actual_result,
"is_success": self.is_success,
"details": self.details,
"duration": self.duration
}
class MCPAttackManager:
def __init__(self):
self.scenarios = {}
self.results = {}
self.logger = logging.getLogger("mcp_attack_manager")
def add_scenario(self, scenario: AttackScenario):
"""添加攻击场景"""
self.scenarios[scenario.scenario_id] = scenario
self.logger.info(f"Added attack scenario: {scenario.scenario_id}")
def remove_scenario(self, scenario_id: str):
"""移除攻击场景"""
if scenario_id in self.scenarios:
del self.scenarios[scenario_id]
self.logger.info(f"Removed attack scenario: {scenario_id}")
def update_scenario(self, scenario: AttackScenario):
"""更新攻击场景"""
scenario.updated_at = datetime.now()
self.scenarios[scenario.scenario_id] = scenario
self.logger.info(f"Updated attack scenario: {scenario.scenario_id}")
def get_scenario(self, scenario_id: str) -> Optional[AttackScenario]:
"""获取攻击场景"""
return self.scenarios.get(scenario_id)
def get_all_scenarios(self) -> List[Dict]:
"""获取所有攻击场景"""
return [scenario.to_dict() for scenario in self.scenarios.values()]
def add_result(self, result: AttackResult):
"""添加攻击结果"""
self.results[result.result_id] = result
self.logger.info(f"Added attack result: {result.result_id}")
def get_result(self, result_id: str) -> Optional[AttackResult]:
"""获取攻击结果"""
return self.results.get(result_id)
def get_scenario_results(self, scenario_id: str) -> List[Dict]:
"""获取特定场景的攻击结果"""
return [result.to_dict() for result in self.results.values()
if result.scenario_id == scenario_id]
def get_all_results(self) -> List[Dict]:
"""获取所有攻击结果"""
return [result.to_dict() for result in self.results.values()]
def run_scenario(self, scenario_id: str) -> str:
"""运行攻击场景"""
self.logger.info(f"Running attack scenario: {scenario_id}")
# 这里简化处理,实际应调用攻击执行模块
# 生成结果 ID
result_id = f"result_{scenario_id}_{datetime.now().timestamp()}"
# 创建攻击结果
result = AttackResult(
result_id=result_id,
scenario_id=scenario_id,
start_time=datetime.now(),
end_time=datetime.now(),
status="completed",
actual_result="攻击执行成功",
is_success=True,
details={"message": "攻击执行完成"}
)
# 添加攻击结果
self.add_result(result)
self.logger.info(f"Attack scenario {scenario_id} completed, result_id: {result_id}")
return result_id3.3 动态威胁场景生成
3.3.1 动态威胁场景生成原理
动态威胁场景生成基于 AI 技术,能够自动生成多样化的攻击场景。其核心原理包括:
- 威胁情报分析:分析最新的威胁情报,了解当前的攻击趋势和技术。
- AI 场景生成:利用机器学习和生成式 AI 技术,生成符合当前威胁趋势的攻击场景。
- 场景验证:验证生成的攻击场景的有效性和可执行性。
- 场景优化:根据攻防模拟结果,不断优化和改进攻击场景。
3.3.2 动态威胁场景生成实现
# mcp_scenario_generator.py
from typing import Dict, List, Optional
import logging
from datetime import datetime
import random
import json
class ThreatIntelligence:
def __init__(self, threat_id: str, threat_type: str,
description: str, severity: str,
attack_vector: str, mitigation: str):
self.threat_id = threat_id
self.threat_type = threat_type
self.description = description
self.severity = severity
self.attack_vector = attack_vector
self.mitigation = mitigation
self.created_at = datetime.now()
def to_dict(self) -> Dict:
"""转换为字典"""
return {
"threat_id": self.threat_id,
"threat_type": self.threat_type,
"description": self.description,
"severity": self.severity,
"attack_vector": self.attack_vector,
"mitigation": self.mitigation,
"created_at": self.created_at.isoformat()
}
class AIScenarioGenerator:
def __init__(self):
self.threat_intelligence = []
self.logger = logging.getLogger("mcp_ai_scenario_generator")
def add_threat_intelligence(self, ti: ThreatIntelligence):
"""添加威胁情报"""
self.threat_intelligence.append(ti)
self.logger.info(f"Added threat intelligence: {ti.threat_id}")
def generate_scenario(self, mcp_system_info: Dict) -> Dict:
"""生成攻击场景"""
self.logger.info("Generating attack scenario")
# 从威胁情报中随机选择一个威胁
if not self.threat_intelligence:
self.logger.error("No threat intelligence available")
return None
selected_ti = random.choice(self.threat_intelligence)
# 基于威胁情报生成攻击场景
scenario = {
"scenario_id": f"scenario_{datetime.now().timestamp()}",
"name": f"{selected_ti.threat_type} 攻击场景",
"description": f"基于威胁情报 {selected_ti.threat_id} 生成的 {selected_ti.threat_type} 攻击场景",
"attack_type": selected_ti.threat_type,
"target": self._select_target(mcp_system_info),
"payload": self._generate_payload(selected_ti, mcp_system_info),
"expected_result": f"成功执行 {selected_ti.threat_type} 攻击",
"severity": selected_ti.severity
}
self.logger.info(f"Generated attack scenario: {scenario['scenario_id']}, type: {scenario['attack_type']}")
return scenario
def _select_target(self, mcp_system_info: Dict) -> str:
"""选择攻击目标"""
# 基于 MCP 系统信息选择攻击目标
components = mcp_system_info.get("components", ["client", "server", "host"])
return random.choice(components)
def _generate_payload(self, ti: ThreatIntelligence, mcp_system_info: Dict) -> Dict:
"""生成攻击 payload"""
# 基于威胁情报和 MCP 系统信息生成攻击 payload
payload = {
"attack_vector": ti.attack_vector,
"target_component": self._select_target(mcp_system_info),
"parameters": self._generate_parameters(ti.threat_type)
}
return payload
def _generate_parameters(self, attack_type: str) -> Dict:
"""生成攻击参数"""
# 根据攻击类型生成不同的攻击参数
parameters = {}
if attack_type == "身份伪造":
parameters = {
"client_id": f"fake_client_{random.randint(1000, 9999)}",
"user_id": f"fake_user_{random.randint(1000, 9999)}",
"token": "fake_token_1234567890"
}
elif attack_type == "工具越权":
parameters = {
"tool_id": "restricted_tool",
"parameters": {"file_path": "/etc/passwd"}
}
elif attack_type == "沙箱逃逸":
parameters = {
"tool_id": "sandboxed_tool",
"parameters": {"command": "bash -c 'echo hello > /host/tmp/escape.txt'"}
}
elif attack_type == "拒绝服务":
parameters = {
"tool_id": "resource_intensive_tool",
"parameters": {"iterations": 1000000}
}
else:
# 默认参数
parameters = {
"tool_id": "test_tool",
"parameters": {"param1": "value1", "param2": "value2"}
}
return parameters
def generate_batch_scenarios(self, mcp_system_info: Dict, count: int = 5) -> List[Dict]:
"""批量生成攻击场景"""
self.logger.info(f"Generating {count} attack scenarios")
scenarios = []
for i in range(count):
scenario = self.generate_scenario(mcp_system_info)
if scenario:
scenarios.append(scenario)
self.logger.info(f"Generated {len(scenarios)} attack scenarios")
return scenarios
# 示例使用
if __name__ == "__main__":
# 配置日志
logging.basicConfig(level=logging.INFO)
# 创建 AI 场景生成器
generator = AIScenarioGenerator()
# 添加威胁情报
ti1 = ThreatIntelligence(
threat_id="ti_001",
threat_type="身份伪造",
description="攻击者伪造合法用户身份,获取未授权访问权限",
severity="high",
attack_vector="API 调用",
mitigation="加强身份验证,使用 MFA,定期轮换凭证"
)
generator.add_threat_intelligence(ti1)
ti2 = ThreatIntelligence(
threat_id="ti_002",
threat_type="工具越权",
description="攻击者利用工具漏洞,执行超出权限范围的操作",
severity="critical",
attack_vector="工具调用",
mitigation="实施最小权限原则,加强工具权限管理"
)
generator.add_threat_intelligence(ti2)
ti3 = ThreatIntelligence(
threat_id="ti_003",
threat_type="沙箱逃逸",
description="攻击者从沙箱环境中逃逸,执行恶意代码",
severity="critical",
attack_vector="沙箱环境",
mitigation="加强沙箱隔离,定期更新沙箱环境"
)
generator.add_threat_intelligence(ti3)
# MCP 系统信息
mcp_system_info = {
"components": ["client", "server", "host"],
"tools": ["file_reader", "command_executor", "network_scanner"],
"version": "v2.0"
}
# 生成攻击场景
scenario = generator.generate_scenario(mcp_system_info)
print(f"Generated scenario: {json.dumps(scenario, indent=2, ensure_ascii=False)}")
# 批量生成攻击场景
scenarios = generator.generate_batch_scenarios(mcp_system_info, count=3)
print(f"\nGenerated {len(scenarios)} scenarios:")
for s in scenarios:
print(f"- {s['name']} (ID: {s['scenario_id']})")3.4 MCP 漏洞利用链分析
3.4.1 MCP 漏洞利用链分析原理
MCP 漏洞利用链分析是指识别和分析 MCP 系统中的漏洞利用链,了解攻击者如何利用多个漏洞组合进行攻击。其核心原理包括:
- 漏洞识别:识别 MCP 系统中的单个漏洞。
- 关联分析:分析漏洞之间的关联关系,识别可能的漏洞利用链。
- 路径分析:分析漏洞利用的路径,了解攻击的传播过程。
- 风险评估:评估漏洞利用链的风险等级,确定修复优先级。
- 修复建议:提供针对性的修复建议,防止漏洞利用链被攻击者利用。
3.4.2 MCP 漏洞利用链分析实现
# mcp_exploit_chain_analyzer.py
from typing import Dict, List, Optional
import logging
from datetime import datetime
class Vulnerability:
def __init__(self, vuln_id: str, name: str, description: str,
severity: str, component: str, cvss_score: float,
attack_vector: str):
self.vuln_id = vuln_id
self.name = name
self.description = description
self.severity = severity
self.component = component
self.cvss_score = cvss_score
self.attack_vector = attack_vector
self.related_vulns = []
def add_related_vuln(self, vuln_id: str):
"""添加相关漏洞"""
if vuln_id not in self.related_vulns:
self.related_vulns.append(vuln_id)
def to_dict(self) -> Dict:
"""转换为字典"""
return {
"vuln_id": self.vuln_id,
"name": self.name,
"description": self.description,
"severity": self.severity,
"component": self.component,
"cvss_score": self.cvss_score,
"attack_vector": self.attack_vector,
"related_vulns": self.related_vulns
}
class ExploitChain:
def __init__(self, chain_id: str, vulns: List[Vulnerability],
attack_path: List[str], total_risk: float):
self.chain_id = chain_id
self.vulns = vulns
self.attack_path = attack_path
self.total_risk = total_risk
self.created_at = datetime.now()
def to_dict(self) -> Dict:
"""转换为字典"""
return {
"chain_id": self.chain_id,
"vulns": [vuln.to_dict() for vuln in self.vulns],
"attack_path": self.attack_path,
"total_risk": self.total_risk,
"created_at": self.created_at.isoformat()
}
class MCPExploitChainAnalyzer:
def __init__(self):
self.vulnerabilities = {}
self.exploit_chains = []
self.logger = logging.getLogger("mcp_exploit_chain_analyzer")
def add_vulnerability(self, vuln: Vulnerability):
"""添加漏洞"""
self.vulnerabilities[vuln.vuln_id] = vuln
self.logger.info(f"Added vulnerability: {vuln.vuln_id}, component: {vuln.component}")
def analyze_exploit_chains(self) -> List[ExploitChain]:
"""分析漏洞利用链"""
self.logger.info("Starting exploit chain analysis")
# 构建漏洞关联图
vuln_graph = self._build_vuln_graph()
# 寻找所有可能的漏洞利用链
chains = self._find_all_chains(vuln_graph)
# 评估每个漏洞利用链的风险
exploit_chains = []
for i, chain in enumerate(chains):
# 获取链中的漏洞
chain_vulns = [self.vulnerabilities[vuln_id] for vuln_id in chain if vuln_id in self.vulnerabilities]
if not chain_vulns:
continue
# 计算总风险
total_risk = sum(vuln.cvss_score for vuln in chain_vulns)
# 创建漏洞利用链
exploit_chain = ExploitChain(
chain_id=f"chain_{datetime.now().timestamp()}_{i}",
vulns=chain_vulns,
attack_path=chain,
total_risk=total_risk
)
exploit_chains.append(exploit_chain)
self.exploit_chains.append(exploit_chain)
# 按风险排序
exploit_chains.sort(key=lambda x: x.total_risk, reverse=True)
self.logger.info(f"Found {len(exploit_chains)} exploit chains")
return exploit_chains
def _build_vuln_graph(self) -> Dict[str, List[str]]:
"""构建漏洞关联图"""
graph = {}
for vuln_id, vuln in self.vulnerabilities.items():
graph[vuln_id] = vuln.related_vulns
return graph
def _find_all_chains(self, graph: Dict[str, List[str]], max_length: int = 5) -> List[List[str]]:
"""寻找所有可能的漏洞利用链"""
chains = []
# 深度优先搜索寻找所有可能的链
def dfs(node, path, visited):
if len(path) > max_length:
return
if path not in chains:
chains.append(path.copy())
visited.add(node)
for neighbor in graph.get(node, []):
if neighbor not in visited:
path.append(neighbor)
dfs(neighbor, path, visited.copy())
path.pop()
# 从每个漏洞开始搜索
for node in graph.keys():
dfs(node, [node], set())
# 过滤掉长度为 1 的链(单个漏洞)
chains = [chain for chain in chains if len(chain) > 1]
return chains
def get_exploit_chains_by_risk(self, min_risk: float = 0.0) -> List[ExploitChain]:
"""按风险获取漏洞利用链"""
return [chain for chain in self.exploit_chains if chain.total_risk >= min_risk]
def generate_fix_recommendations(self, chain: ExploitChain) -> List[str]:
"""生成修复建议"""
recommendations = []
for vuln in chain.vulns:
recommendations.append(f"修复漏洞 {vuln.vuln_id}({vuln.name}),CVSS 评分:{vuln.cvss_score}")
recommendations.append(f"总体修复建议:优先修复 CVSS 评分高的漏洞,打破漏洞利用链")
return recommendations
# 示例使用
if __name__ == "__main__":
# 配置日志
logging.basicConfig(level=logging.INFO)
# 创建漏洞利用链分析器
analyzer = MCPExploitChainAnalyzer()
# 添加漏洞
vuln1 = Vulnerability(
vuln_id="vuln_001",
name="身份认证绕过",
description="攻击者可以绕过 MCP Server 的身份认证机制",
severity="critical",
component="server",
cvss_score=9.8,
attack_vector="API 调用"
)
analyzer.add_vulnerability(vuln1)
vuln2 = Vulnerability(
vuln_id="vuln_002",
name="工具越权",
description="攻击者可以通过特定工具执行超出权限的操作",
severity="high",
component="host",
cvss_score=8.5,
attack_vector="工具调用"
)
analyzer.add_vulnerability(vuln2)
vuln3 = Vulnerability(
vuln_id="vuln_003",
name="沙箱逃逸",
description="攻击者可以从 Docker 沙箱中逃逸",
severity="critical",
component="host",
cvss_score=9.0,
attack_vector="沙箱环境"
)
analyzer.add_vulnerability(vuln3)
vuln4 = Vulnerability(
vuln_id="vuln_004",
name="命令注入",
description="攻击者可以通过工具参数注入恶意命令",
severity="high",
component="tool",
cvss_score=8.0,
attack_vector="参数注入"
)
analyzer.add_vulnerability(vuln4)
# 建立漏洞关联
vuln1.add_related_vuln("vuln_002")
vuln2.add_related_vuln("vuln_003")
vuln3.add_related_vuln("vuln_004")
vuln1.add_related_vuln("vuln_004")
# 分析漏洞利用链
chains = analyzer.analyze_exploit_chains()
# 输出结果
print(f"\nFound {len(chains)} exploit chains:")
for chain in chains:
print(f"\nExploit Chain {chain.chain_id}:")
print(f" Total Risk: {chain.total_risk}")
print(f" Attack Path: {' -> '.join(chain.attack_path)}")
print(" Vulnerabilities:")
for vuln in chain.vulns:
print(f" - {vuln.name} (ID: {vuln.vuln_id}, CVSS: {vuln.cvss_score})")
# 生成修复建议
recommendations = analyzer.generate_fix_recommendations(chain)
print(" Fix Recommendations:")
for rec in recommendations:
print(f" - {rec}")
# 按风险获取漏洞利用链
high_risk_chains = analyzer.get_exploit_chains_by_risk(min_risk=15.0)
print(f"\nHigh risk chains (>= 15.0): {len(high_risk_chains)}")3.5 MCP 攻防模拟系统集成示例
3.5.1 MCP 攻防模拟系统完整集成
# mcp_attack_simulation.py
from typing import Dict, List, Optional
import logging
import json
from datetime import datetime
# 导入前面实现的模块
from mcp_attack_manager import MCPAttackManager, AttackScenario
from mcp_scenario_generator import AIScenarioGenerator, ThreatIntelligence
from mcp_exploit_chain_analyzer import MCPExploitChainAnalyzer, Vulnerability
class MCPAttackSimulationSystem:
def __init__(self):
# 初始化各个模块
self.attack_manager = MCPAttackManager()
self.scenario_generator = AIScenarioGenerator()
self.exploit_analyzer = MCPExploitChainAnalyzer()
self.logger = logging.getLogger("mcp_attack_simulation")
self.logger.info("MCP Attack Simulation System initialized")
def initialize(self):
"""初始化系统"""
self.logger.info("Initializing MCP Attack Simulation System")
# 添加威胁情报
self._add_threat_intelligence()
# 添加示例漏洞
self._add_sample_vulnerabilities()
self.logger.info("MCP Attack Simulation System initialized successfully")
def _add_threat_intelligence(self):
"""添加威胁情报"""
# 身份伪造威胁
ti1 = ThreatIntelligence(
threat_id="ti_001",
threat_type="身份伪造",
description="攻击者伪造合法用户身份,获取未授权访问权限",
severity="high",
attack_vector="API 调用",
mitigation="加强身份验证,使用 MFA,定期轮换凭证"
)
self.scenario_generator.add_threat_intelligence(ti1)
# 工具越权威胁
ti2 = ThreatIntelligence(
threat_id="ti_002",
threat_type="工具越权",
description="攻击者利用工具漏洞,执行超出权限范围的操作",
severity="critical",
attack_vector="工具调用",
mitigation="实施最小权限原则,加强工具权限管理"
)
self.scenario_generator.add_threat_intelligence(ti2)
# 沙箱逃逸威胁
ti3 = ThreatIntelligence(
threat_id="ti_003",
threat_type="沙箱逃逸",
description="攻击者从沙箱环境中逃逸,执行恶意代码",
severity="critical",
attack_vector="沙箱环境",
mitigation="加强沙箱隔离,定期更新沙箱环境"
)
self.scenario_generator.add_threat_intelligence(ti3)
# 命令注入威胁
ti4 = ThreatIntelligence(
threat_id="ti_004",
threat_type="命令注入",
description="攻击者通过工具参数注入恶意命令",
severity="high",
attack_vector="参数注入",
mitigation="加强参数验证和过滤"
)
self.scenario_generator.add_threat_intelligence(ti4)
# 拒绝服务威胁
ti5 = ThreatIntelligence(
threat_id="ti_005",
threat_type="拒绝服务",
description="攻击者通过大量请求导致 MCP 系统崩溃",
severity="medium",
attack_vector="资源耗尽",
mitigation="实施速率限制,优化系统性能"
)
self.scenario_generator.add_threat_intelligence(ti5)
def _add_sample_vulnerabilities(self):
"""添加示例漏洞"""
# 添加示例漏洞,用于漏洞利用链分析
vuln1 = Vulnerability(
vuln_id="vuln_001",
name="身份认证绕过",
description="攻击者可以绕过 MCP Server 的身份认证机制",
severity="critical",
component="server",
cvss_score=9.8,
attack_vector="API 调用"
)
self.exploit_analyzer.add_vulnerability(vuln1)
vuln2 = Vulnerability(
vuln_id="vuln_002",
name="工具越权",
description="攻击者可以通过特定工具执行超出权限的操作",
severity="high",
component="host",
cvss_score=8.5,
attack_vector="工具调用"
)
self.exploit_analyzer.add_vulnerability(vuln2)
vuln3 = Vulnerability(
vuln_id="vuln_003",
name="沙箱逃逸",
description="攻击者可以从 Docker 沙箱中逃逸",
severity="critical",
component="host",
cvss_score=9.0,
attack_vector="沙箱环境"
)
self.exploit_analyzer.add_vulnerability(vuln3)
vuln4 = Vulnerability(
vuln_id="vuln_004",
name="命令注入",
description="攻击者可以通过工具参数注入恶意命令",
severity="high",
component="tool",
cvss_score=8.0,
attack_vector="参数注入"
)
self.exploit_analyzer.add_vulnerability(vuln4)
# 建立漏洞关联
vuln1.add_related_vuln("vuln_002")
vuln2.add_related_vuln("vuln_003")
vuln3.add_related_vuln("vuln_004")
vuln1.add_related_vuln("vuln_004")
def generate_attack_scenarios(self, mcp_system_info: Dict, count: int = 5) -> List[Dict]:
"""生成攻击场景"""
self.logger.info(f"Generating {count} attack scenarios")
scenarios = []
for i in range(count):
scenario_dict = self.scenario_generator.generate_scenario(mcp_system_info)
if scenario_dict:
# 转换为 AttackScenario 对象并添加到攻击管理器
scenario = AttackScenario(
scenario_id=scenario_dict["scenario_id"],
name=scenario_dict["name"],
description=scenario_dict["description"],
attack_type=scenario_dict["attack_type"],
target=scenario_dict["target"],
payload=scenario_dict["payload"],
expected_result=scenario_dict["expected_result"],
severity=scenario_dict["severity"]
)
self.attack_manager.add_scenario(scenario)
scenarios.append(scenario_dict)
self.logger.info(f"Generated {len(scenarios)} attack scenarios")
return scenarios
def run_attack_simulation(self, scenario_ids: List[str] = None) -> List[str]:
"""运行攻防模拟"""
self.logger.info("Running attack simulation")
# 如果没有指定场景 ID,运行所有场景
if not scenario_ids:
scenario_ids = [scenario.scenario_id for scenario in self.attack_manager.scenarios.values()]
result_ids = []
for scenario_id in scenario_ids:
if scenario_id in self.attack_manager.scenarios:
result_id = self.attack_manager.run_scenario(scenario_id)
result_ids.append(result_id)
else:
self.logger.warning(f"Scenario {scenario_id} not found")
self.logger.info(f"Attack simulation completed, {len(result_ids)} scenarios executed")
return result_ids
def analyze_exploit_chains(self) -> List[Dict]:
"""分析漏洞利用链"""
self.logger.info("Analyzing exploit chains")
chains = self.exploit_analyzer.analyze_exploit_chains()
# 转换为字典格式
chain_dicts = [chain.to_dict() for chain in chains]
self.logger.info(f"Exploit chain analysis completed, found {len(chain_dicts)} chains")
return chain_dicts
def generate_report(self) -> Dict:
"""生成攻防模拟报告"""
self.logger.info("Generating attack simulation report")
# 获取所有攻击场景
scenarios = self.attack_manager.get_all_scenarios()
# 获取所有攻击结果
results = self.attack_manager.get_all_results()
# 分析漏洞利用链
exploit_chains = self.analyze_exploit_chains()
# 生成报告
report = {
"report_id": f"report_{datetime.now().timestamp()}",
"generated_at": datetime.now().isoformat(),
"scenarios": {
"total": len(scenarios),
"list": scenarios
},
"results": {
"total": len(results),
"list": results,
"success_rate": self._calculate_success_rate(results)
},
"exploit_chains": {
"total": len(exploit_chains),
"list": exploit_chains,
"high_risk_chains": len([chain for chain in exploit_chains if chain["total_risk"] >= 15.0])
},
"recommendations": self._generate_recommendations(scenarios, results, exploit_chains)
}
self.logger.info(f"Attack simulation report generated: {report['report_id']}")
return report
def _calculate_success_rate(self, results: List[Dict]) -> float:
"""计算攻击成功率"""
if not results:
return 0.0
success_count = sum(1 for result in results if result["is_success"])
return (success_count / len(results)) * 100
def _generate_recommendations(self, scenarios: List[Dict], results: List[Dict],
exploit_chains: List[Dict]) -> List[str]:
"""生成修复建议"""
recommendations = []
# 基于攻击结果生成建议
for result in results:
if result["is_success"]:
scenario = next((s for s in scenarios if s["scenario_id"] == result["scenario_id"]), None)
if scenario:
recommendations.append(f"修复 {scenario['attack_type']} 攻击漏洞,该攻击已成功执行")
# 基于漏洞利用链生成建议
for chain in exploit_chains:
if chain["total_risk"] >= 15.0:
recommendations.append(f"优先修复风险值为 {chain['total_risk']} 的漏洞利用链:{' -> '.join(chain['attack_path'])}")
# 通用建议
recommendations.append("加强 MCP 系统的身份认证机制,使用 MFA")
recommendations.append("实施最小权限原则,限制工具的访问权限")
recommendations.append("加强沙箱隔离,定期更新沙箱环境")
recommendations.append("对工具参数进行严格验证和过滤,防止注入攻击")
recommendations.append("定期进行攻防模拟测试,及时发现和修复漏洞")
# 去重
recommendations = list(dict.fromkeys(recommendations))
return recommendations
# 示例使用
if __name__ == "__main__":
# 配置日志
logging.basicConfig(level=logging.INFO, format='%(asctime)s - %(name)s - %(levelname)s - %(message)s')
# 创建 MCP 攻防模拟系统
simulation_system = MCPAttackSimulationSystem()
# 初始化系统
simulation_system.initialize()
# MCP 系统信息
mcp_system_info = {
"components": ["client", "server", "host"],
"tools": ["file_reader", "command_executor", "network_scanner"],
"version": "v2.0"
}
print("1. 生成攻击场景...")
scenarios = simulation_system.generate_attack_scenarios(mcp_system_info, count=3)
print(f"生成了 {len(scenarios)} 个攻击场景:")
for i, scenario in enumerate(scenarios):
print(f" {i+1}. {scenario['name']} (ID: {scenario['scenario_id']})")
print("\n2. 运行攻防模拟...")
result_ids = simulation_system.run_attack_simulation()
print(f"运行了 {len(result_ids)} 个攻击场景,结果 ID:{result_ids}")
print("\n3. 分析漏洞利用链...")
exploit_chains = simulation_system.analyze_exploit_chains()
print(f"发现了 {len(exploit_chains)} 条漏洞利用链")
print("\n4. 生成攻防模拟报告...")
report = simulation_system.generate_report()
print(f"报告生成成功,ID:{report['report_id']}")
# 输出报告摘要
print("\n报告摘要:")
print(f" 生成时间:{report['generated_at']}")
print(f" 攻击场景总数:{report['scenarios']['total']}")
print(f" 攻击结果总数:{report['results']['total']}")
print(f" 攻击成功率:{report['results']['success_rate']:.2f}%")
print(f" 漏洞利用链总数:{report['exploit_chains']['total']}")
print(f" 高风险漏洞利用链:{report['exploit_chains']['high_risk_chains']}")
print("\n修复建议:")
for i, rec in enumerate(report['recommendations']):
print(f" {i+1}. {rec}")
# 保存报告到文件
report_file = f"attack_simulation_report_{datetime.now().strftime('%Y%m%d_%H%M%S')}.json"
with open(report_file, 'w', encoding='utf-8') as f:
json.dump(report, f, indent=2, ensure_ascii=False)
print(f"\n报告已保存到文件:{report_file}")四、与主流方案深度对比
4.1 攻防模拟方案对比
方案类型 | 优势 | 劣势 | 适用场景 |
|---|---|---|---|
传统渗透测试 | 深入全面,能够发现复杂漏洞 | 耗时耗力,成本高,无法覆盖所有场景 | 关键系统,定期测试 |
自动化漏洞扫描 | 快速高效,成本低,可定期执行 | 只能发现已知漏洞,误报率高,无法发现复杂漏洞利用链 | 大规模系统,定期扫描 |
红队评估 | 模拟真实攻击,能够发现深层问题,评估系统韧性 | 成本高,周期长,需要专业团队 | 高端客户,重要项目 |
MCP 攻防模拟 | 专门针对 MCP 设计,支持动态场景生成,自动化执行,能够发现 MCP 特有的漏洞 | 实现复杂,需要专业团队,目前成熟度较低 | MCP v2.0 框架 |
4.2 场景生成方案对比
方案类型 | 优势 | 劣势 | 适用场景 |
|---|---|---|---|
人工生成 | 针对性强,能够覆盖特定场景 | 耗时耗力,场景数量有限,难以覆盖所有可能场景 | 特定测试需求 |
模板生成 | 快速高效,能够生成大量场景 | 场景固定,缺乏灵活性,无法适应新的威胁 | 常规测试 |
AI 动态生成 | 能够自动生成多样化的场景,适应新的威胁,场景数量多 | 生成的场景可能存在不合理之处,需要验证 | MCP 攻防模拟 |
4.3 漏洞利用链分析方案对比
方案类型 | 优势 | 劣势 | 适用场景 |
|---|---|---|---|
人工分析 | 能够深入分析复杂的漏洞利用链,理解攻击的本质 | 耗时耗力,无法处理大量漏洞,容易遗漏 | 关键漏洞分析 |
静态分析 | 快速高效,能够处理大量漏洞 | 只能发现表面关联,无法发现复杂的漏洞利用链 | 初步漏洞分析 |
图形化分析 | 能够可视化展示漏洞利用链,便于理解和分析 | 实现复杂,需要专业工具 | MCP 漏洞利用链分析 |
五、实际工程意义、潜在风险与局限性分析
5.1 实际工程意义
- 提高 MCP 系统的安全性:通过攻防模拟,能够主动发现 MCP 系统中的安全漏洞和弱点,提前进行修复,提高系统的整体安全性。
- 验证安全机制的有效性:攻防模拟能够验证 MCP 安全机制的有效性,确保其能够抵御真实攻击,增强系统的安全韧性。
- 降低安全事件的发生概率:提前发现和修复漏洞,能够降低安全事件的发生概率,减少损失。
- 提高安全团队的能力:攻防模拟能够培养安全团队的攻防能力,提高安全事件的响应速度和处理能力。
- 满足合规性要求:攻防模拟是许多行业法规和标准的要求,如 PCI DSS、ISO 27001 等,能够帮助企业满足合规性要求。
- 增强用户信任:通过公开的安全测试和攻防模拟结果,能够增强用户对 MCP 系统的信任,促进 MCP 生态的发展。
5.2 潜在风险
- 误报和漏报:攻防模拟可能存在误报和漏报,导致资源浪费或漏洞遗漏。
- 系统影响:攻防模拟可能对 MCP 系统造成影响,如性能下降、服务中断等。
- 攻击面扩大:攻防模拟本身可能引入新的攻击面,如攻击管理模块被攻击。
- 数据泄露风险:攻防模拟过程中可能涉及敏感数据,存在数据泄露的风险。
- 成本问题:建设和维护 MCP 攻防模拟系统需要投入大量的资源和成本。
5.3 局限性
- 无法覆盖所有场景:攻防模拟无法覆盖所有可能的攻击场景,存在遗漏的风险。
- 依赖于威胁情报:动态威胁场景生成依赖于最新的威胁情报,威胁情报的质量和时效性直接影响场景生成的效果。
- 无法模拟所有攻击技术:攻防模拟无法模拟所有的攻击技术,特别是新型的攻击技术。
- 需要专业团队:MCP 攻防模拟需要专业的安全团队进行设计和维护,门槛较高。
- 无法替代人工测试:攻防模拟无法完全替代人工测试,特别是对复杂漏洞的深入分析。
5.4 风险缓解策略
风险类型 | 缓解策略 |
|---|---|
误报和漏报 | 1. 结合多种检测方法,提高检测的准确性2. 定期更新攻击脚本和场景,适应新的威胁3. 对检测结果进行人工验证,减少误报和漏报 |
系统影响 | 1. 在测试环境中进行攻防模拟,避免影响生产系统2. 控制攻击强度和频率,减少对系统的影响3. 制定应急计划,在系统受到影响时能够及时恢复 |
攻击面扩大 | 1. 对攻防模拟系统本身进行严格的安全保护2. 限制攻防模拟系统的访问权限,只允许授权人员访问3. 定期对攻防模拟系统进行安全评估和测试 |
数据泄露风险 | 1. 在测试环境中使用模拟数据,避免使用真实敏感数据2. 对攻防模拟过程中产生的数据进行加密和保护3. 制定数据处理政策,确保数据的安全使用和销毁 |
成本问题 | 1. 采用开源工具和框架,降低建设成本2. 实现自动化执行,减少人力成本3. 优先测试关键组件和功能,提高测试效率 |
六、未来趋势展望与个人前瞻性预测
6.1 技术发展趋势
- AI 驱动的攻防模拟:利用人工智能和机器学习技术,实现更加智能的攻防模拟,包括自动生成攻击场景、自动执行攻击、自动分析结果等。
- 实时攻防模拟:实现对 MCP 系统的实时攻防模拟,能够在攻击发生时及时检测和响应。
- 云原生攻防模拟:适应云原生环境,实现对云原生 MCP 系统的攻防模拟。
- 边缘计算攻防模拟:支持边缘计算场景下的 MCP 系统攻防模拟,满足边缘计算的低延迟和高可靠性要求。
- 联邦学习攻防模拟:为联邦学习场景下的 MCP 系统提供攻防模拟方案,保护数据隐私的同时确保系统安全。
6.2 应用场景扩展
- 跨组织 MCP 攻防模拟:支持跨组织的 MCP 系统攻防模拟,促进 MCP 生态的安全发展。
- IoT 设备 MCP 攻防模拟:为 IoT 设备上的 MCP 系统提供轻量级攻防模拟方案,确保 IoT 设备的安全运行。
- 生成式 AI 与 MCP 攻防模拟:针对生成式 AI 与 MCP 集成的场景,提供专门的攻防模拟方案。
- MCP 供应链安全攻防模拟:针对 MCP 生态中的供应链安全问题,提供专门的攻防模拟方案。
6.3 标准与生态发展
- MCP 攻防模拟标准制定:制定统一的 MCP 攻防模拟标准,促进不同 MCP 系统之间的攻防模拟互认和互操作。
- 攻防模拟平台互操作性:提高不同攻防模拟平台之间的互操作性,便于 MCP 系统与现有攻防模拟系统的集成。
- 开源攻防模拟项目发展:推动开源 MCP 攻防模拟项目的发展,降低攻防模拟系统的使用门槛。
- 行业协作与共享:促进不同行业之间的 MCP 攻防模拟经验和技术共享,共同应对安全挑战。
6.4 个人前瞻性预测
- 到 2027 年:40% 的 MCP 系统将采用自动化攻防模拟,定期进行安全测试。
- 到 2028 年:AI 驱动的动态威胁场景生成将成为 MCP 攻防模拟的标配,能够自动适应新的威胁。
- 到 2029 年:实时攻防模拟将广泛应用于 MCP 系统,能够在攻击发生时及时检测和响应。
- 到 2030 年:MCP 攻防模拟将成为 MCP 安全体系的核心组成部分,与 CI/CD 流程深度集成。
- 未来 5 年:MCP 攻防模拟将从传统的定期测试向持续测试转变,实现对 MCP 系统的全生命周期安全保障。
参考链接:
附录(Appendix):
附录 A:MCP 攻防模拟系统部署指南
环境要求
- Python 3.8+
- Docker 20.10+(用于运行攻击容器)
- Kubernetes 1.20+(用于编排和管理)
- PostgreSQL 13.0+(用于存储场景和结果)
- Redis 6.0+(用于缓存和会话管理)
- Grafana 8.0+(用于可视化展示)
安装步骤
# 安装依赖
pip install fastapi uvicorn sqlalchemy pydantic redis psycopg2-binary python-dotenv
# 配置攻防模拟系统
cp config.example.yaml config.yaml
# 编辑配置文件
vim config.yaml
# 启动基础设施服务
docker-compose up -d postgresql redis grafana
# 初始化数据库
python init_db.py --config config.yaml
# 启动攻防模拟服务
python mcp_attack_simulation_service.py --config config.yaml
# 启动监测代理
python mcp_monitoring_agent.py --config config.yamlAPI 文档
- 攻防模拟服务 API:http://localhost:8000/docs
- 监测代理 API:http://localhost:8001/docs
- 可视化界面:http://localhost:3000
附录 B:MCP 攻防模拟最佳实践
- 安全最佳实践
- 在测试环境中进行攻防模拟,避免影响生产系统
- 对攻防模拟系统本身进行严格的安全保护
- 限制攻防模拟系统的访问权限,只允许授权人员访问
- 定期对攻防模拟系统进行安全评估和测试
- 测试最佳实践
- 制定测试计划,明确测试目标和范围
- 优先测试关键组件和功能,提高测试效率
- 结合多种测试方法,提高测试的全面性和准确性
- 定期更新测试脚本和场景,适应新的威胁
- 结果分析最佳实践
- 对测试结果进行深入分析,理解漏洞的本质和影响
- 生成详细的测试报告,包括漏洞描述、影响范围、修复建议等
- 跟踪漏洞修复情况,确保漏洞得到及时修复
- 定期进行回归测试,验证漏洞修复的有效性
- 团队协作最佳实践
- 建立跨职能团队,包括安全人员、开发人员、运维人员等
- 制定明确的责任分工和工作流程
- 定期举行安全会议,分享攻防模拟结果和经验
- 建立反馈机制,持续改进攻防模拟系统
附录 C:常见问题与解决方案
- 攻击脚本执行失败
- 检查攻击脚本是否与 MCP 系统版本兼容
- 检查攻击目标是否正确配置
- 检查网络连接是否正常
- 查看日志文件,了解具体的错误信息
- 误报率过高
- 优化攻击检测算法,减少误报
- 结合多种检测方法,提高检测的准确性
- 对检测结果进行人工验证,过滤误报
- 定期更新攻击特征库,适应新的威胁
- 系统性能影响过大
- 控制攻击强度和频率,减少对系统的影响
- 在低峰期进行攻防模拟,避免影响业务运行
- 优化攻击脚本,减少资源消耗
- 增加系统资源,提高系统的承载能力
- 漏洞修复不及时
- 建立漏洞修复优先级机制,优先修复高风险漏洞
- 制定漏洞修复计划,明确修复时间和责任人
- 跟踪漏洞修复情况,确保漏洞得到及时修复
- 定期进行回归测试,验证漏洞修复的有效性
- 攻防模拟系统本身存在安全问题
- 对攻防模拟系统本身进行严格的安全保护
- 限制攻防模拟系统的访问权限,只允许授权人员访问
- 定期对攻防模拟系统进行安全评估和测试
- 及时更新攻防模拟系统的软件和组件,修复已知漏洞
关键词: MCP v2.0, 攻防模拟, 动态威胁场景, 漏洞利用链, 安全测试, 渗透测试
本文参与 腾讯云自媒体同步曝光计划,分享自作者个人站点/博客。
原始发表:2026-01-10,如有侵权请联系 cloudcommunity@tencent.com 删除
评论
登录后参与评论
推荐阅读
目录


