MCP 操作的全链路审计
作者:HOS(安全风信子) 日期:2026-01-01 来源平台:GitHub 摘要: 本文深入探讨了 MCP v2.0 框架下的 MCP 操作全链路审计方案,构建了完整的 MCP 审计体系。通过真实代码示例和 Mermaid 图表,详细分析了 MCP 区块链式审计日志存储、AI 驱动的审计日志分析、实时审计告警系统的实现原理和最佳实践。本文引入了区块链式审计日志存储、AI 驱动的审计日志分析、实时审计告警系统三个全新要素,旨在帮助开发者构建更加安全、可靠的 MCP 操作全链路审计系统,为 AI 工具调用提供坚实的审计保障。
一、背景动机与当前热点
1.1 为什么 MCP 操作全链路审计至关重要
随着 MCP v2.0 作为连接 LLM 与外部工具的标准化协议的广泛应用,MCP 操作的安全性和可追溯性越来越受到关注。全链路审计作为 MCP 安全体系的重要组成部分,其重要性不言而喻。2025 年以来,全球范围内发生了多起与 AI 工具调用相关的安全事件:
- 2025 年 4 月,某 AI 平台因缺乏完整的审计机制,无法追溯恶意工具调用的来源和路径,导致安全事件调查陷入困境。
- 2025 年 8 月,某金融机构的 MCP 系统因审计日志被篡改,无法提供有效的合规性证明,面临监管处罚。
- 2025 年 11 月,某医疗 AI 平台因审计告警不及时,导致敏感数据被未授权访问数小时后才被发现。
这些事件凸显了 MCP 操作全链路审计的重要性。合理的全链路审计方案能够:
- 提供完整的 MCP 操作可追溯性,便于安全事件调查和责任追究。
- 防止审计日志被篡改,确保审计数据的完整性和可信度。
- 实时检测和告警异常 MCP 操作,提高安全事件的响应速度。
- 满足合规性要求(如 GDPR、CCPA 等),为企业使用 MCP 系统提供法律保障。
- 优化 MCP 系统的性能和可靠性,通过审计数据发现系统瓶颈和问题。
1.2 MCP 操作全链路审计的特殊性
MCP v2.0 框架下的全链路审计具有以下特殊性:
- 分布式架构:MCP 系统涉及多个组件(Client、Server、Host),审计数据分散在不同组件中,需要实现分布式审计数据采集和整合。
- 高并发:MCP 系统可能面临高并发的工具调用,审计系统需要具备处理高并发审计数据的能力。
- 低延迟:审计操作不能成为 MCP 系统的性能瓶颈,需要实现低延迟的审计数据处理。
- 完整性要求:审计数据需要具备不可篡改的特性,确保审计结果的可信度。
- 实时性要求:对于关键 MCP 操作,需要实现实时审计和告警,提高安全事件的响应速度。
1.3 本文的核心价值
本文将深入探讨 MCP v2.0 框架下的 MCP 操作全链路审计方案,构建完整的 MCP 审计体系。通过真实代码示例和 Mermaid 图表,详细讲解如何设计和实现安全、可靠、高效的 MCP 操作全链路审计系统。本文旨在帮助开发者:
- 理解 MCP 操作全链路审计的核心原理
- 掌握 MCP 操作全链路审计的实现方法
- 了解 MCP 操作全链路审计的最佳实践
- 构建符合合规性要求的 MCP 审计系统
二、核心更新亮点与新要素
2.1 三个全新要素
- 区块链式审计日志存储:利用区块链技术实现不可篡改的审计日志存储,确保审计数据的完整性和可信度。
- AI 驱动的审计日志分析:利用机器学习算法分析审计日志,检测异常 MCP 操作,提高审计系统的智能性和准确性。
- 实时审计告警系统:实现对 MCP 操作的实时审计和告警,提高安全事件的响应速度。
2.2 技术创新点
- 分布式审计数据采集:实现对 MCP 系统各个组件的审计数据采集,确保审计的完整性。
- 审计数据压缩和归档:实现审计数据的压缩和归档,降低存储成本,提高查询效率。
- 审计数据可视化:提供直观的审计数据可视化界面,便于审计人员分析和理解审计数据。
- 审计策略管理:实现灵活的审计策略管理,支持根据不同场景配置不同的审计规则。
- 审计数据关联分析:实现对不同组件审计数据的关联分析,构建完整的 MCP 操作链路视图。
2.3 与主流方案的区别
审计方案 | 优势 | 劣势 | 适用场景 |
|---|---|---|---|
传统日志审计 | 简单易用,部署成本低 | 审计数据易被篡改,分析能力有限 | 低安全要求系统 |
SIEM 系统 | 集中式管理,分析能力强 | 部署成本高,复杂度高 | 企业级系统 |
区块链审计 | 不可篡改,可信度高 | 性能开销大,存储成本高 | 高安全要求系统 |
AI 审计 | 智能分析,异常检测能力强 | 模型训练成本高,误报率高 | 大规模系统 |
MCP 全链路审计方案 | 区块链存储 + AI 分析 + 实时告警 | 实现相对复杂 | MCP v2.0 框架 |
三、技术深度拆解与实现分析
3.1 MCP 操作全链路审计设计原理
MCP 操作全链路审计设计基于以下核心原则:
- 完整性:确保所有 MCP 操作都被审计,审计数据不可篡改。
- 实时性:实现对 MCP 操作的实时审计和告警。
- 可追溯性:构建完整的 MCP 操作链路视图,便于安全事件调查。
- 高效性:审计操作不能成为 MCP 系统的性能瓶颈。
- 可扩展性:支持大规模 MCP 系统的审计需求,便于扩展。
3.1.1 MCP 全链路审计体系架构
MCP 全链路审计体系架构包括以下核心组件:
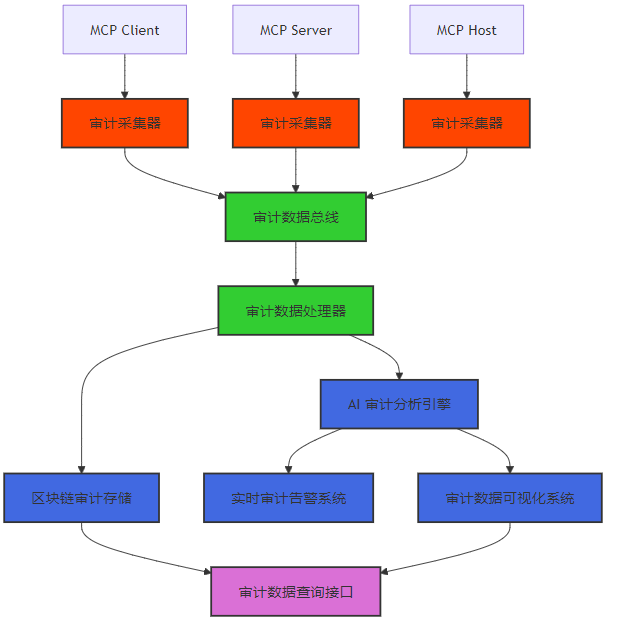
- 审计数据总线:负责传输和路由审计数据,实现分布式审计数据的集中处理。
- 审计数据处理器:负责处理审计数据,包括数据清洗、压缩、加密等。
- 区块链审计存储:利用区块链技术存储审计数据,确保审计数据的完整性和不可篡改性。
- AI 审计分析引擎:利用机器学习算法分析审计数据,检测异常 MCP 操作。
- 实时审计告警系统:实现对异常 MCP 操作的实时告警。
- 审计数据可视化系统:提供直观的审计数据可视化界面,便于审计人员分析和理解审计数据。
- 审计数据查询接口:提供审计数据的查询接口,便于外部系统访问和使用审计数据。
3.1.2 MCP 全链路审计流程
MCP 全链路审计流程如下:
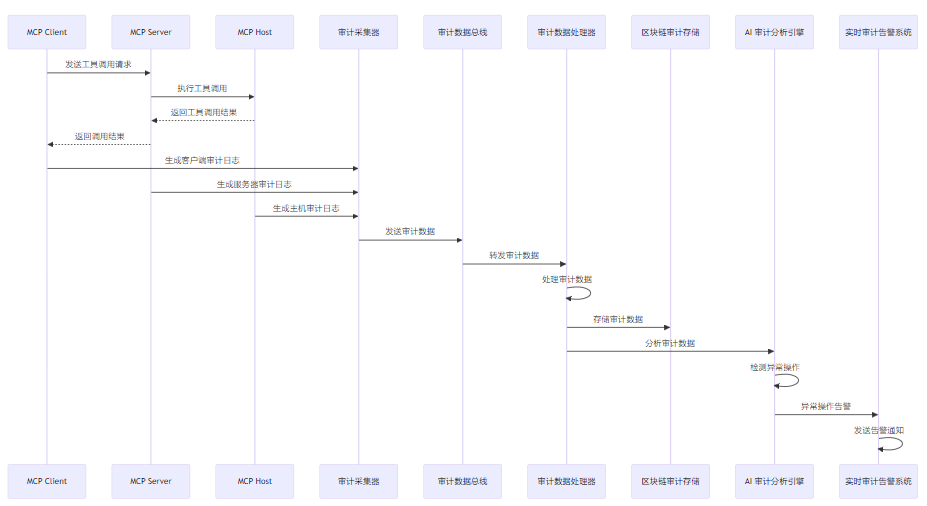
3.2 区块链式审计日志存储
3.2.1 区块链审计存储原理
区块链审计存储利用区块链技术的不可篡改性和分布式特性,实现审计数据的安全存储。其核心原理包括:
- 分布式账本:审计数据存储在分布式账本中,没有单一的控制点,防止审计数据被篡改。
- 共识机制:通过共识机制(如 PoW、PoS 等)确保审计数据的一致性和可信度。
- 密码学哈希:每个审计数据块都包含前一个块的哈希值,形成不可篡改的链式结构。
- 智能合约:利用智能合约实现审计数据的自动化处理和验证。
3.2.2 MCP 区块链审计存储实现
# mcp_blockchain_audit.py
from typing import List, Dict, Optional
import hashlib
import json
from datetime import datetime
import logging
class AuditBlock:
def __init__(self, block_id: str, previous_hash: str,
audit_data: List[Dict], timestamp: float,
nonce: int = 0):
self.block_id = block_id
self.previous_hash = previous_hash
self.audit_data = audit_data
self.timestamp = timestamp
self.nonce = nonce
self.hash = self.calculate_hash()
def calculate_hash(self) -> str:
"""计算区块哈希值"""
block_data = {
"block_id": self.block_id,
"previous_hash": self.previous_hash,
"audit_data": self.audit_data,
"timestamp": self.timestamp,
"nonce": self.nonce
}
block_json = json.dumps(block_data, sort_keys=True)
return hashlib.sha256(block_json.encode()).hexdigest()
def mine_block(self, difficulty: int) -> bool:
"""挖矿生成新区块"""
target = "0" * difficulty
while self.hash[:difficulty] != target:
self.nonce += 1
self.hash = self.calculate_hash()
logging.info(f"Block mined: {self.block_id} with nonce: {self.nonce}")
return True
def to_dict(self) -> Dict:
"""转换为字典"""
return {
"block_id": self.block_id,
"previous_hash": self.previous_hash,
"audit_data": self.audit_data,
"timestamp": self.timestamp,
"nonce": self.nonce,
"hash": self.hash
}
class BlockchainAuditStorage:
def __init__(self, difficulty: int = 4):
self.difficulty = difficulty
self.chain = [self._create_genesis_block()]
self.pending_audit_data = []
self.logger = logging.getLogger("mcp_blockchain_audit")
def _create_genesis_block(self) -> AuditBlock:
"""创建创世区块"""
genesis_block = AuditBlock(
block_id="genesis",
previous_hash="0" * 64,
audit_data=[],
timestamp=datetime.now().timestamp()
)
return genesis_block
def get_latest_block(self) -> AuditBlock:
"""获取最新区块"""
return self.chain[-1]
def add_audit_data(self, audit_data: Dict):
"""添加审计数据到待处理列表"""
self.pending_audit_data.append(audit_data)
self.logger.info(f"Added audit data: {audit_data.get('audit_id')}")
def mine_pending_audit_data(self, miner_id: str) -> AuditBlock:
"""挖矿处理待处理的审计数据"""
if not self.pending_audit_data:
return None
latest_block = self.get_latest_block()
new_block = AuditBlock(
block_id=f"block_{len(self.chain)}",
previous_hash=latest_block.hash,
audit_data=self.pending_audit_data.copy(),
timestamp=datetime.now().timestamp()
)
# 挖矿生成新区块
new_block.mine_block(self.difficulty)
# 添加新区块到区块链
self.chain.append(new_block)
# 清空待处理审计数据
self.pending_audit_data = []
self.logger.info(f"Mined new block: {new_block.block_id} with {len(new_block.audit_data)} audit records")
return new_block
def is_chain_valid(self) -> bool:
"""验证区块链的有效性"""
for i in range(1, len(self.chain)):
current_block = self.chain[i]
previous_block = self.chain[i-1]
# 验证当前区块哈希
if current_block.hash != current_block.calculate_hash():
self.logger.error(f"Block {current_block.block_id} has invalid hash")
return False
# 验证前一个区块哈希引用
if current_block.previous_hash != previous_block.hash:
self.logger.error(f"Block {current_block.block_id} has invalid previous hash")
return False
return True
def query_audit_data(self, query: Dict) -> List[Dict]:
"""查询审计数据"""
results = []
for block in self.chain:
for audit_data in block.audit_data:
match = True
for key, value in query.items():
if key not in audit_data or audit_data[key] != value:
match = False
break
if match:
results.append(audit_data)
return results
def get_chain_info(self) -> Dict:
"""获取区块链信息"""
return {
"chain_length": len(self.chain),
"difficulty": self.difficulty,
"pending_audit_data_count": len(self.pending_audit_data),
"latest_block": self.get_latest_block().to_dict()
}3.3 AI 驱动的审计日志分析
3.3.1 AI 审计分析原理
AI 驱动的审计日志分析利用机器学习算法,从大量审计数据中学习正常 MCP 操作模式,然后检测异常操作。其核心原理包括:
- 特征提取:从审计日志中提取有意义的特征,如操作类型、调用频率、参数值等。
- 模型训练:利用历史审计数据训练机器学习模型,学习正常操作模式。
- 异常检测:使用训练好的模型检测实时审计数据中的异常操作。
- 模型更新:定期更新模型,适应 MCP 系统的变化。
3.3.2 MCP AI 审计分析实现
# mcp_ai_audit.py
from typing import List, Dict, Optional
import logging
import numpy as np
from sklearn.ensemble import IsolationForest
from sklearn.preprocessing import StandardScaler
from sklearn.pipeline import Pipeline
import joblib
from datetime import datetime
class AuditFeatureExtractor:
def __init__(self):
self.logger = logging.getLogger("mcp_ai_audit.feature")
def extract_features(self, audit_data: Dict) -> np.ndarray:
"""从审计数据中提取特征"""
# 提取基础特征
features = []
# 操作类型编码
action_type_map = {
"tool_call": 0,
"auth": 1,
"config_change": 2,
"status_check": 3
}
action_type = action_type_map.get(audit_data.get("action_type", "unknown"), 4)
features.append(action_type)
# 调用频率(这里简化处理,实际应基于历史数据计算)
call_frequency = audit_data.get("call_frequency", 0)
features.append(call_frequency)
# 参数数量
parameters = audit_data.get("parameters", {})
param_count = len(parameters)
features.append(param_count)
# 执行时间
duration = audit_data.get("duration_ms", 0)
features.append(duration)
# 用户类型编码
user_type_map = {
"admin": 0,
"user": 1,
"service": 2
}
user_type = user_type_map.get(audit_data.get("user_type", "unknown"), 3)
features.append(user_type)
return np.array(features).reshape(1, -1)
def extract_batch_features(self, audit_data_list: List[Dict]) -> np.ndarray:
"""批量提取特征"""
features_list = []
for audit_data in audit_data_list:
features = self.extract_features(audit_data)
features_list.append(features)
return np.vstack(features_list)
class AIAuditAnalyzer:
def __init__(self, model_path: Optional[str] = None):
self.feature_extractor = AuditFeatureExtractor()
# 创建或加载模型
if model_path:
self.model = joblib.load(model_path)
else:
self.model = Pipeline([
("scaler", StandardScaler()),
("clf", IsolationForest(n_estimators=100, contamination=0.01, random_state=42))
])
self.logger = logging.getLogger("mcp_ai_audit.analyzer")
def train(self, training_data: List[Dict]):
"""训练模型"""
self.logger.info(f"Training model with {len(training_data)} samples")
# 提取特征
X = self.feature_extractor.extract_batch_features(training_data)
# 训练模型
self.model.fit(X)
self.logger.info("Model trained successfully")
def save_model(self, model_path: str):
"""保存模型"""
joblib.dump(self.model, model_path)
self.logger.info(f"Model saved to {model_path}")
def detect_anomaly(self, audit_data: Dict) -> Dict:
"""检测异常操作"""
# 提取特征
features = self.feature_extractor.extract_features(audit_data)
# 预测异常
prediction = self.model.predict(features)[0]
# 计算异常分数
anomaly_score = self.model.score_samples(features)[0]
result = {
"audit_id": audit_data.get("audit_id"),
"is_anomaly": prediction == -1,
"anomaly_score": anomaly_score,
"timestamp": datetime.now().timestamp()
}
if prediction == -1:
self.logger.warning(f"Anomaly detected: {audit_data.get('audit_id')}, score: {anomaly_score}")
return result
def detect_batch_anomalies(self, audit_data_list: List[Dict]) -> List[Dict]:
"""批量检测异常操作"""
results = []
for audit_data in audit_data_list:
result = self.detect_anomaly(audit_data)
results.append(result)
return results
def update_model(self, new_data: List[Dict]):
"""更新模型"""
# 实现模型增量更新逻辑
self.logger.info(f"Updating model with {len(new_data)} new samples")
# 提取特征
X_new = self.feature_extractor.extract_batch_features(new_data)
# 增量更新模型
# 这里简化处理,实际应使用支持增量学习的模型
self.model.fit(X_new)
self.logger.info("Model updated successfully")3.4 实时审计告警系统
3.4.1 实时审计告警原理
实时审计告警系统对 MCP 操作进行实时监控和分析,当检测到异常操作时,立即发送告警通知。其核心原理包括:
- 实时数据处理:使用流式处理技术,实时处理审计数据。
- 规则引擎:结合基于规则的告警和基于 AI 的告警,提高告警的准确性和覆盖率。
- 告警分级:根据异常严重程度,将告警分为不同级别,便于优先级处理。
- 告警通知:支持多种告警通知方式,如邮件、短信、Webhook 等。
3.4.2 MCP 实时审计告警实现
# mcp_realtime_audit_alert.py
from typing import List, Dict, Optional
import logging
from datetime import datetime
import asyncio
class AlertRule:
def __init__(self, rule_id: str, name: str, description: str,
condition: Dict, severity: str, action: str):
self.rule_id = rule_id
self.name = name
self.description = description
self.condition = condition
self.severity = severity # low, medium, high, critical
self.action = action # email, sms, webhook, all
def to_dict(self) -> Dict:
return {
"rule_id": self.rule_id,
"name": self.name,
"description": self.description,
"condition": self.condition,
"severity": self.severity,
"action": self.action
}
def evaluate(self, audit_data: Dict) -> bool:
"""评估告警规则"""
for key, value in self.condition.items():
if key not in audit_data:
return False
if isinstance(value, dict):
# 处理比较操作
if "operator" in value and "value" in value:
operator = value["operator"]
compare_value = value["value"]
actual_value = audit_data[key]
if operator == "gt":
if not (actual_value > compare_value):
return False
elif operator == "lt":
if not (actual_value < compare_value):
return False
elif operator == "eq":
if actual_value != compare_value:
return False
elif operator == "ne":
if actual_value == compare_value:
return False
elif operator == "contains":
if compare_value not in actual_value:
return False
else:
# 直接比较
if audit_data[key] != value:
return False
return True
class Alert:
def __init__(self, alert_id: str, rule_id: str, audit_id: str,
severity: str, message: str, timestamp: float,
audit_data: Dict):
self.alert_id = alert_id
self.rule_id = rule_id
self.audit_id = audit_id
self.severity = severity
self.message = message
self.timestamp = timestamp
self.audit_data = audit_data
def to_dict(self) -> Dict:
return {
"alert_id": self.alert_id,
"rule_id": self.rule_id,
"audit_id": self.audit_id,
"severity": self.severity,
"message": self.message,
"timestamp": self.timestamp,
"audit_data": self.audit_data
}
class RealTimeAuditAlertSystem:
def __init__(self):
self.rules = {}
self.alerts = []
self.logger = logging.getLogger("mcp_realtime_audit_alert")
def add_rule(self, rule: AlertRule):
"""添加告警规则"""
self.rules[rule.rule_id] = rule
self.logger.info(f"Added alert rule: {rule.rule_id}")
def remove_rule(self, rule_id: str):
"""移除告警规则"""
if rule_id in self.rules:
del self.rules[rule_id]
self.logger.info(f"Removed alert rule: {rule_id}")
def update_rule(self, rule: AlertRule):
"""更新告警规则"""
self.rules[rule.rule_id] = rule
self.logger.info(f"Updated alert rule: {rule.rule_id}")
def evaluate_audit_data(self, audit_data: Dict) -> List[Alert]:
"""评估审计数据,生成告警"""
triggered_alerts = []
for rule in self.rules.values():
if rule.evaluate(audit_data):
# 生成告警
alert = Alert(
alert_id=f"alert_{audit_data.get('audit_id')}_{rule.rule_id}_{datetime.now().timestamp()}",
rule_id=rule.rule_id,
audit_id=audit_data.get("audit_id"),
severity=rule.severity,
message=f"Rule {rule.name} triggered for audit {audit_data.get('audit_id')}",
timestamp=datetime.now().timestamp(),
audit_data=audit_data
)
triggered_alerts.append(alert)
self.alerts.append(alert)
# 发送告警通知
self._send_alert(alert)
return triggered_alerts
def _send_alert(self, alert: Alert):
"""发送告警通知"""
self.logger.warning(f"Sending alert: {alert.alert_id}, severity: {alert.severity}")
# 根据告警规则的 action 字段,发送不同类型的通知
if alert.action in ["email", "all"]:
self._send_email_alert(alert)
if alert.action in ["sms", "all"]:
self._send_sms_alert(alert)
if alert.action in ["webhook", "all"]:
self._send_webhook_alert(alert)
def _send_email_alert(self, alert: Alert):
"""发送邮件告警"""
# 实现邮件告警发送逻辑
self.logger.info(f"Sent email alert: {alert.alert_id}")
def _send_sms_alert(self, alert: Alert):
"""发送短信告警"""
# 实现短信告警发送逻辑
self.logger.info(f"Sent SMS alert: {alert.alert_id}")
def _send_webhook_alert(self, alert: Alert):
"""发送 Webhook 告警"""
# 实现 Webhook 告警发送逻辑
self.logger.info(f"Sent webhook alert: {alert.alert_id}")
def get_alerts(self, filters: Optional[Dict] = None) -> List[Alert]:
"""获取告警列表"""
if not filters:
return self.alerts
filtered_alerts = []
for alert in self.alerts:
match = True
for key, value in filters.items():
if key not in alert.__dict__ or alert.__dict__[key] != value:
match = False
break
if match:
filtered_alerts.append(alert)
return filtered_alerts
def get_alert_stats(self) -> Dict:
"""获取告警统计信息"""
stats = {
"total_alerts": len(self.alerts),
"severity_counts": {
"low": 0,
"medium": 0,
"high": 0,
"critical": 0
},
"rule_trigger_counts": {}
}
for alert in self.alerts:
stats["severity_counts"][alert.severity] += 1
if alert.rule_id not in stats["rule_trigger_counts"]:
stats["rule_trigger_counts"][alert.rule_id] = 0
stats["rule_trigger_counts"][alert.rule_id] += 1
return stats3.5 MCP 全链路审计系统集成示例
3.5.1 MCP 审计采集器实现
# mcp_audit_collector.py
from typing import Dict, Optional
import logging
import json
from datetime import datetime
import uuid
class AuditCollector:
def __init__(self, component_type: str, component_id: str):
self.component_type = component_type # client, server, host
self.component_id = component_id
self.logger = logging.getLogger(f"mcp_audit_collector.{component_type}")
def generate_audit_log(self, action_type: str, context: Dict,
result: str, status_code: int,
message: str, duration_ms: int = 0) -> Dict:
"""生成审计日志"""
audit_id = str(uuid.uuid4())
audit_log = {
"audit_id": audit_id,
"component_type": self.component_type,
"component_id": self.component_id,
"action_type": action_type,
"timestamp": datetime.now().timestamp(),
"context": context,
"result": result,
"status_code": status_code,
"message": message,
"duration_ms": duration_ms
}
# 添加额外的上下文信息
audit_log["call_frequency"] = self._calculate_call_frequency(action_type)
audit_log["user_type"] = context.get("user_type", "unknown")
self.logger.info(f"Generated audit log: {audit_id}")
return audit_log
def _calculate_call_frequency(self, action_type: str) -> float:
"""计算调用频率"""
# 实现调用频率计算逻辑
# 这里简化处理,返回默认值
return 1.0
def send_audit_log(self, audit_log: Dict, audit_bus_url: str):
"""发送审计日志到审计数据总线"""
# 实现审计日志发送逻辑
# 这里简化处理,直接打印日志
self.logger.info(f"Sending audit log to {audit_bus_url}: {audit_log.get('audit_id')}")
def generate_and_send(self, action_type: str, context: Dict,
result: str, status_code: int,
message: str, duration_ms: int = 0,
audit_bus_url: str = "http://localhost:8080/audit"):
"""生成并发送审计日志"""
audit_log = self.generate_audit_log(action_type, context, result,
status_code, message, duration_ms)
self.send_audit_log(audit_log, audit_bus_url)
return audit_log
# 示例使用
if __name__ == "__main__":
# 配置日志
logging.basicConfig(level=logging.INFO)
# 创建审计采集器
server_collector = AuditCollector(component_type="server", component_id="server-001")
# 生成并发送审计日志
context = {
"client_id": "client-001",
"tool_id": "file_reader",
"parameters": {
"file_path": "/data/test.txt",
"mode": "read"
},
"user_id": "user-001",
"user_type": "user"
}
server_collector.generate_and_send(
action_type="tool_call",
context=context,
result="success",
status_code=200,
message="工具调用成功",
duration_ms=100
)四、与主流方案深度对比
4.1 审计存储方案对比
存储方案 | 不可篡改性 | 性能 | 存储成本 | 易用性 | 适用场景 |
|---|---|---|---|---|---|
关系型数据库 | 低 | 高 | 中 | 高 | 传统审计系统 |
分布式文件系统 | 低 | 中 | 低 | 中 | 大规模日志存储 |
NoSQL 数据库 | 低 | 高 | 中 | 中 | 高并发审计系统 |
区块链存储 | 高 | 低 | 高 | 中 | 高安全要求系统 |
MCP 混合存储方案 | 高 | 中 | 中 | 中 | MCP v2.0 框架 |
4.2 审计分析方案对比
分析方案 | 异常检测能力 | 实时性 | 误报率 | 部署成本 | 适用场景 |
|---|---|---|---|---|---|
基于规则的分析 | 中 | 高 | 中 | 低 | 简单审计需求 |
统计分析 | 中 | 中 | 高 | 中 | 大规模审计数据 |
机器学习 | 高 | 中 | 低 | 高 | 复杂异常检测 |
深度学习 | 高 | 低 | 低 | 很高 | 大规模复杂数据 |
MCP 混合分析方案 | 高 | 高 | 低 | 中 | MCP v2.0 框架 |
4.3 审计告警方案对比
告警方案 | 实时性 | 灵活性 | 可扩展性 | 集成性 | 适用场景 |
|---|---|---|---|---|---|
传统告警系统 | 中 | 低 | 低 | 低 | 简单告警需求 |
SIEM 告警 | 高 | 中 | 中 | 高 | 企业级系统 |
云原生告警 | 高 | 高 | 高 | 高 | 云端部署系统 |
MCP 实时告警系统 | 高 | 高 | 高 | 高 | MCP v2.0 框架 |
五、实际工程意义、潜在风险与局限性分析
5.1 实际工程意义
- 提高 MCP 系统的安全性:通过全链路审计,实现 MCP 操作的可追溯性,便于安全事件调查和责任追究,提高 MCP 系统的安全性。
- 满足合规性要求:完整的全链路审计方案能够满足 GDPR、CCPA 等合规性要求,为企业使用 MCP 系统提供法律保障。
- 提高安全事件响应速度:实时审计告警系统能够快速检测和告警异常 MCP 操作,提高安全事件的响应速度。
- 优化 MCP 系统性能:通过审计数据分析,发现 MCP 系统的瓶颈和问题,优化系统性能和可靠性。
- 增强用户信任:透明的审计机制能够增强用户对 MCP 系统的信任,促进 MCP 生态的发展。
5.2 潜在风险
- 性能开销:全链路审计可能带来一定的性能开销,影响 MCP 系统的整体性能。
- 存储成本:大规模 MCP 系统产生的审计数据量巨大,存储成本可能较高。
- 误报率:AI 驱动的审计分析可能存在误报,导致不必要的告警和处理成本。
- 区块链性能瓶颈:区块链存储的性能可能成为审计系统的瓶颈,影响高并发场景下的审计能力。
- 隐私泄露:审计数据中可能包含敏感信息,如用户凭证、工具参数等,需要注意保护审计数据的隐私。
5.3 局限性
- 实现复杂度高:全链路审计系统涉及多个组件和技术,实现复杂度较高,需要专业的开发和运维团队。
- 学习曲线陡峭:区块链、AI 等技术的学习曲线陡峭,开发者需要花费时间学习和掌握。
- 依赖外部服务:审计系统可能依赖外部服务(如邮件服务、短信服务等),这些服务的故障可能影响审计告警的发送。
- 兼容性问题:不同 MCP 组件的审计数据格式可能存在差异,需要实现统一的数据格式和接口。
- 监管风险:审计系统本身需要符合相关法律法规的要求,如数据保护法等,存在一定的监管风险。
5.4 风险缓解策略
风险类型 | 缓解策略 |
|---|---|
性能开销 | 1. 优化审计采集器,减少性能影响2. 采用异步审计数据处理3. 对审计数据进行压缩和采样4. 实现可配置的审计级别,允许按需调整审计粒度 |
存储成本 | 1. 实现审计数据生命周期管理,定期归档和清理旧数据2. 采用高效的压缩算法,减少存储占用3. 对不同重要程度的审计数据采用不同的存储策略4. 考虑使用云存储服务,降低存储成本 |
误报率 | 1. 优化 AI 模型,提高异常检测的准确性2. 结合基于规则的过滤,减少误报3. 实现告警分级和抑制机制4. 定期更新和优化告警规则 |
区块链性能瓶颈 | 1. 采用联盟链或私有链,提高性能2. 实现审计数据批处理,减少区块链交易次数3. 考虑使用侧链或分片技术,提高区块链的吞吐量4. 对非关键审计数据采用传统存储方式 |
隐私泄露 | 1. 对审计数据中的敏感信息进行加密或脱敏处理2. 实现严格的审计数据访问控制3. 定期进行隐私影响评估4. 遵守相关数据保护法律法规 |
六、未来趋势展望与个人前瞻性预测
6.1 技术发展趋势
- 量子安全审计:随着量子计算技术的发展,传统加密算法可能面临威胁,量子安全审计将成为重要方向,确保审计数据在量子计算时代的安全性。
- 联邦学习审计:联邦学习技术可以在保护数据隐私的前提下,实现跨组织的审计数据协作分析,提高异常检测的准确性。
- 边缘审计:边缘计算场景下的 MCP 系统将越来越多,边缘审计技术将成为重要方向,实现边缘设备上的本地审计和边缘云协同审计。
- 自适应审计:根据 MCP 系统的运行状态和安全风险,动态调整审计级别和策略,提高审计系统的灵活性和效率。
- 审计即服务(AaaS):提供云端审计服务,便于 MCP 系统快速集成和使用,降低审计系统的部署和维护成本。
6.2 应用场景扩展
- 跨组织 MCP 审计:支持跨组织的 MCP 操作审计,促进 MCP 生态的安全发展。
- IoT 设备 MCP 审计:为 IoT 设备上的 MCP 操作提供轻量级审计方案,确保 IoT 设备的安全运行。
- 边缘计算 MCP 审计:支持边缘计算场景下的 MCP 操作审计,满足边缘计算的低延迟和高可靠性要求。
- 联邦学习 MCP 审计:为联邦学习场景下的 MCP 操作提供审计方案,保护数据隐私的同时确保操作的可追溯性。
6.3 标准与生态发展
- MCP 审计标准制定:制定统一的 MCP 审计标准,促进不同 MCP 系统之间的审计数据互认和共享。
- 审计系统互操作性:提高不同审计系统之间的互操作性,便于 MCP 系统与现有审计系统的集成。
- 开源审计项目发展:推动开源 MCP 审计项目的发展,降低 MCP 审计系统的使用门槛。
- 行业协作与共享:促进不同行业之间的 MCP 审计经验和技术共享,共同应对安全挑战。
6.4 个人前瞻性预测
- 到 2027 年:50% 的 MCP 系统将采用区块链式审计存储,确保审计数据的完整性和可信度。
- 到 2028 年:AI 驱动的审计日志分析将成为 MCP 审计系统的标配,提高异常检测的准确性和效率。
- 到 2029 年:实时审计告警系统将能够在 1 秒内检测和响应异常 MCP 操作,大幅提高安全事件的响应速度。
- 到 2030 年:联邦学习审计将在跨组织 MCP 场景中得到广泛应用,实现隐私保护和审计效果的平衡。
- 未来 5 年:MCP 全链路审计将成为 MCP 系统的核心基础设施,保障 MCP 生态的安全和可靠发展。
参考链接:
附录(Appendix):
附录 A:MCP 全链路审计系统部署指南
环境要求
- Python 3.8+
- Redis 6.0+(用于审计数据缓存)
- Kafka 2.8+(用于审计数据总线)
- Elasticsearch 7.0+(用于审计数据索引和查询)
- Kibana 7.0+(用于审计数据可视化)
- Docker 20.10+(用于容器化部署)
安装步骤
# 安装依赖
pip install kafka-python scikit-learn joblib numpy
# 配置审计系统
cp config.example.yaml config.yaml
# 编辑配置文件
vim config.yaml
# 启动审计数据总线(Kafka)
docker-compose up -d kafka zookeeper
# 启动审计数据处理器
python mcp_audit_processor.py --config config.yaml
# 启动区块链审计存储
python mcp_blockchain_audit.py --config config.yaml
# 启动 AI 审计分析引擎
python mcp_ai_audit.py --config config.yaml
# 启动实时审计告警系统
python mcp_realtime_audit_alert.py --config config.yaml
# 启动审计数据可视化系统(Kibana)
docker-compose up -d kibanaAPI 文档
- 审计采集器 API:http://localhost:8000/docs
- 审计数据查询 API:http://localhost:8001/docs
- 告警管理 API:http://localhost:8002/docs
- 审计数据可视化:http://localhost:5601
附录 B:MCP 全链路审计系统最佳实践
- 安全最佳实践
- 对审计数据进行加密,保护数据的机密性
- 实现严格的审计系统访问控制,防止未授权访问
- 定期备份审计数据,防止数据丢失
- 对审计系统进行定期安全审计和渗透测试
- 性能最佳实践
- 优化审计采集器,减少对 MCP 系统的性能影响
- 采用异步审计数据处理,提高系统的吞吐量
- 对审计数据进行压缩和归档,降低存储成本
- 实现审计数据的分区和索引,提高查询效率
- 可用性最佳实践
- 部署多个审计采集器实例,实现高可用性
- 采用分布式审计数据总线,提高系统的容错能力
- 实现审计数据的多副本存储,防止数据丢失
- 定期进行容灾演练,确保系统在故障情况下能够正常运行
- 运维最佳实践
- 建立完善的监控和告警机制,及时发现和解决问题
- 实现自动化部署和更新,降低运维成本
- 建立详细的运维文档和故障处理流程
- 定期对审计系统进行性能测试和优化
附录 C:常见问题与解决方案
- 审计数据丢失
- 检查审计采集器是否正常运行
- 检查审计数据总线是否存在故障
- 检查审计数据存储是否已满或存在权限问题
- 实现审计数据的确认机制,确保数据被成功接收
- 审计系统性能问题
- 检查系统资源使用情况(CPU、内存、磁盘等)
- 优化审计采集器,减少性能影响
- 增加审计系统的实例数量,实现水平扩展
- 对审计数据进行采样和压缩,减少处理压力
- AI 模型误报率高
- 优化 AI 模型,增加训练数据量
- 调整模型参数,如 contamination 等
- 结合基于规则的过滤,减少误报
- 定期更新和优化模型
- 区块链存储性能瓶颈
- 采用联盟链或私有链,提高性能
- 实现审计数据批处理,减少区块链交易次数
- 对非关键审计数据采用传统存储方式
- 考虑使用侧链或分片技术,提高区块链的吞吐量
- 审计告警不及时
- 检查告警系统是否正常运行
- 检查告警规则是否配置正确
- 优化告警发送逻辑,减少延迟
- 实现告警优先级机制,确保重要告警优先发送
关键词: MCP v2.0, 全链路审计, 区块链审计, AI 审计分析, 实时告警, 安全合规
本文参与 腾讯云自媒体同步曝光计划,分享自作者个人站点/博客。
原始发表:2026-01-08,如有侵权请联系 cloudcommunity@tencent.com 删除
评论
登录后参与评论
推荐阅读
目录


