015_具身人工智能的安全防护体系:多层次防御与主动响应策略
015_具身人工智能的安全防护体系:多层次防御与主动响应策略

安全风信子
发布于 2025-11-19 13:13:31
发布于 2025-11-19 13:13:31
引言
在2025年的今天,具身人工智能(Embodied AI)已经深入各行各业,从工业生产、医疗健康到智能交通,它们在物理世界中执行着越来越复杂的任务。然而,随着具身AI系统与人类和环境的交互日益密切,其安全风险也随之增加。单一的安全措施已无法应对复杂多变的威胁环境,建立多层次、全方位的安全防护体系成为当务之急。
本文将深入探讨具身人工智能的安全防护体系,从多层次防御架构设计、主动响应策略、实时监控机制到实战案例分析,为构建可靠的具身AI安全防护系统提供全面指导。我们将特别关注如何整合物理安全与网络安全,如何实现主动威胁检测与响应,以及如何在保证安全性的同时维持系统性能。
具身AI安全防护体系的核心维度
具身AI安全防护体系:
┌───────────────┐ ┌───────────────┐ ┌───────────────┐
│ 预防层 │ │ 检测层 │ │ 响应层 │
│ │ │ │ │ │
│ •安全设计 │ │ •异常检测 │ │ •应急响应 │
│ •访问控制 │ │ •入侵检测 │ │ •恢复机制 │
│ •加密保护 │ │ •异常行为分析 │ │ •事后分析 │
└────────┬──────┘ └────────┬──────┘ └────────┬──────┘
│ │ │
▼ ▼ ▼
┌─────────────────────────────────────────────────────────┐
│ 持续改进循环 │
│ │
│ •安全审计 •漏洞管理 •威胁情报 •安全更新 │
└─────────────────────────────────────────────────────────┘第一章:具身人工智能的多层次防御架构
1.1 物理安全层
物理安全是具身AI系统安全的第一道防线,直接关系到硬件组件的完整性和可用性:
硬件防护设计
具身AI系统的硬件防护应当从设计阶段就开始考虑:
- 防篡改设计:使用防篡改传感器、密封外壳和物理锁,防止未经授权的硬件修改
- 防侧信道攻击:屏蔽电磁辐射,减少功耗波动,防止通过侧信道获取敏感信息
- 冗余设计:关键组件冗余配置,确保单点故障不影响整体系统安全
- 安全启动:实现安全启动流程,确保硬件和固件未被篡改
硬件防篡改技术对比:
技术类型 | 防护能力 | 实施难度 | 成本影响 | 适用场景 |
|---|---|---|---|---|
物理密封 | 中等 | 低 | 低 | 普通商业设备 |
防篡改传感器 | 高 | 中等 | 中等 | 高价值设备 |
芯片级防篡改 | 非常高 | 高 | 高 | 关键基础设施 |
光学防篡改 | 高 | 中等 | 中等 | 安全敏感应用 |
环境安全监控
具身AI系统的运行环境监控对于早期发现物理威胁至关重要:
# 环境安全监控系统
class EnvironmentalSecurityMonitor:
def __init__(self):
self.sensors = {
'temperature': {'threshold': (0, 40), 'alert_level': 'warning', 'reading': None},
'humidity': {'threshold': (20, 80), 'alert_level': 'warning', 'reading': None},
'vibration': {'threshold': (0, 10), 'alert_level': 'warning', 'reading': None},
'power_quality': {'threshold': (198, 242), 'alert_level': 'critical', 'reading': None},
'motion': {'threshold': False, 'alert_level': 'warning', 'reading': None},
'sound': {'threshold': (0, 70), 'alert_level': 'warning', 'reading': None}
}
self.alerts = []
self.monitoring_active = True
def collect_sensor_data(self):
"""收集环境传感器数据"""
if not self.monitoring_active:
return {'status': 'inactive', 'message': 'Monitoring is disabled'}
# 在实际系统中,这里会从真实传感器获取数据
# 模拟传感器数据采集
for sensor_name in self.sensors:
self.sensors[sensor_name]['reading'] = self._simulate_sensor_reading(sensor_name)
return {'status': 'success', 'collected_at': datetime.now().isoformat()}
def analyze_environmental_security(self):
"""分析环境安全状态,检测异常"""
current_alerts = []
security_status = 'normal'
for sensor_name, sensor_data in self.sensors.items():
if sensor_data['reading'] is None:
continue
# 检查传感器读数是否超出阈值
is_breach, breach_type = self._check_threshold_breach(sensor_name, sensor_data)
if is_breach:
alert = self._generate_environmental_alert(
sensor_name,
sensor_data['reading'],
sensor_data['threshold'],
sensor_data['alert_level'],
breach_type
)
current_alerts.append(alert)
# 更新整体安全状态
if sensor_data['alert_level'] == 'critical':
security_status = 'critical'
elif sensor_data['alert_level'] == 'warning' and security_status != 'critical':
security_status = 'warning'
# 更新警报列表
self.alerts = current_alerts
return {
'security_status': security_status,
'alerts': current_alerts,
'timestamp': datetime.now().isoformat(),
'sensor_readings': {k: v['reading'] for k, v in self.sensors.items()}
}
def generate_physical_security_report(self):
"""生成物理安全状态报告"""
# 确保已收集最新数据
self.collect_sensor_data()
analysis_result = self.analyze_environmental_security()
# 生成综合报告
report = {
'report_id': f"PHYS-{datetime.now().strftime('%Y%m%d')}-{str(len(self.alerts)).zfill(4)}",
'generated_at': datetime.now().isoformat(),
'security_summary': analysis_result['security_status'],
'active_alerts_count': len(analysis_result['alerts']),
'sensor_health': self._assess_sensor_health(),
'environmental_readings': analysis_result['sensor_readings'],
'detailed_alerts': analysis_result['alerts'],
'recommended_actions': self._generate_recommendations(analysis_result['security_status'])
}
return report
def set_threshold(self, sensor_name, threshold):
"""设置传感器阈值"""
if sensor_name not in self.sensors:
return {'status': 'error', 'message': f'Sensor {sensor_name} not found'}
self.sensors[sensor_name]['threshold'] = threshold
return {'status': 'success', 'message': f'Threshold updated for {sensor_name}'}1.2 网络安全层
随着具身AI系统的网络化和互联化,网络安全已成为安全防护体系的重要组成部分:
网络架构安全设计
具身AI系统的网络架构应当采用分层防御和隔离设计:
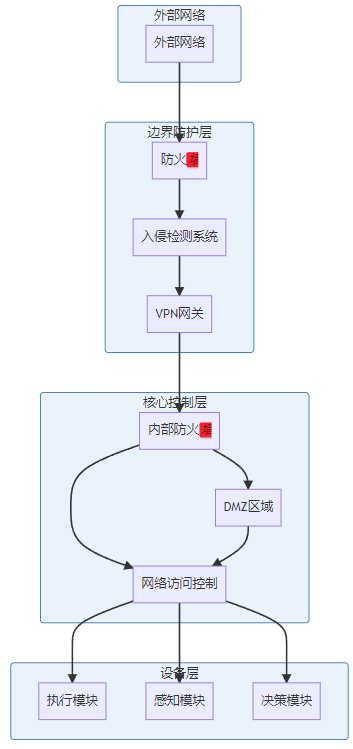
通信安全机制
具身AI系统组件间的通信安全对于防止数据泄露和控制劫持至关重要:
- 端到端加密:采用TLS 1.3或更高版本,确保通信内容安全
- 证书管理:实施严格的证书颁发、验证和吊销机制
- 安全协议:使用经过安全审计的通信协议,避免协议漏洞
- 流量加密:所有网络流量加密,防止中间人攻击
- 认证授权:基于零信任架构,实施组件间的严格认证
# 安全通信框架
class SecureCommunicationFramework:
def __init__(self, config):
self.config = config
self.certificates = {}
self.active_connections = {}
self.security_events = []
def initialize_certificates(self):
"""初始化和加载通信证书"""
# 加载或生成证书
for component in self.config['components']:
cert_path = component.get('cert_path')
key_path = component.get('key_path')
if cert_path and key_path:
# 加载现有证书
cert = self._load_certificate(cert_path, key_path)
else:
# 生成新证书
cert = self._generate_certificate(component['name'])
self.certificates[component['name']] = cert
return {'status': 'success', 'message': 'Certificates initialized'}
def establish_secure_connection(self, source, destination, connection_type):
"""建立安全连接"""
# 验证源和目标组件
if source not in self.certificates or destination not in self.certificates:
return {'status': 'error', 'message': 'Invalid component(s)'}
# 验证连接类型
if connection_type not in self.config['allowed_connections']:
return {'status': 'error', 'message': 'Connection type not allowed'}
# 建立安全通道
secure_channel = self._create_secure_channel(
source,
destination,
self.certificates[source],
self.certificates[destination]
)
# 记录连接
connection_id = f"CONN-{datetime.now().strftime('%Y%m%d%H%M%S')}-{random.randint(1000, 9999)}"
self.active_connections[connection_id] = {
'source': source,
'destination': destination,
'type': connection_type,
'channel': secure_channel,
'established_at': datetime.now().isoformat(),
'last_activity': datetime.now().isoformat()
}
# 记录安全事件
self._log_security_event('connection_established', connection_id)
return {
'status': 'success',
'connection_id': connection_id,
'message': f'Secure connection established from {source} to {destination}'
}
def send_encrypted_message(self, connection_id, message):
"""发送加密消息"""
# 验证连接
if connection_id not in self.active_connections:
return {'status': 'error', 'message': 'Connection not found'}
connection = self.active_connections[connection_id]
# 加密消息
encrypted_message = self._encrypt_message(
message,
connection['channel']
)
# 添加消息完整性校验
integrity_protected_message = self._add_integrity_protection(encrypted_message)
# 发送消息
send_result = self._transmit_message(
connection['destination'],
integrity_protected_message,
connection['channel']
)
if send_result['status'] == 'success':
# 更新连接活动时间
connection['last_activity'] = datetime.now().isoformat()
# 记录安全事件
self._log_security_event('message_sent', connection_id)
return send_result
def verify_message_authenticity(self, message, sender_info):
"""验证消息的真实性和完整性"""
# 检查发送者身份
if sender_info['id'] not in self.certificates:
return {'status': 'error', 'message': 'Unknown sender'}
# 验证消息完整性
integrity_result = self._verify_integrity(message, sender_info)
if not integrity_result['valid']:
return {
'status': 'error',
'message': 'Integrity verification failed',
'reason': integrity_result['reason']
}
# 解密消息
decrypted_message = self._decrypt_message(
message['content'],
self.certificates[sender_info['id']]
)
return {
'status': 'success',
'authenticity': 'verified',
'decrypted_message': decrypted_message,
'sender': sender_info['id']
}
def monitor_network_security(self):
"""监控网络安全状态"""
# 检查异常连接
suspicious_connections = self._detect_suspicious_connections()
# 检查通信异常
communication_anomalies = self._detect_communication_anomalies()
# 检查证书状态
certificate_issues = self._check_certificate_status()
# 生成安全报告
security_report = {
'report_id': f"NETSEC-{datetime.now().strftime('%Y%m%d')}-{str(len(self.security_events)).zfill(4)}",
'timestamp': datetime.now().isoformat(),
'active_connections': len(self.active_connections),
'suspicious_connections': suspicious_connections,
'communication_anomalies': communication_anomalies,
'certificate_issues': certificate_issues,
'security_recommendations': self._generate_security_recommendations(
suspicious_connections,
communication_anomalies,
certificate_issues
)
}
return security_report1.3 应用安全层
应用安全层关注具身AI系统的软件和算法层面的安全防护:
代码安全与审计
确保具身AI系统的代码安全是应用安全的基础:
- 安全编码实践:遵循OWASP等安全编码标准
- 静态代码分析:使用工具自动检测代码漏洞
- 代码审计:定期进行人工代码安全审计
- 依赖管理:定期更新第三方库,修复已知漏洞
- 安全测试:实施全面的安全测试策略
模型安全与防护
具身AI系统的机器学习模型需要特殊的安全防护措施:
# 模型安全防护框架
class ModelSecurityFramework:
def __init__(self, model_registry):
self.model_registry = model_registry
self.security_checks = []
self.model_versions = {}
def register_model(self, model, model_info):
"""注册新模型,进行安全检查"""
# 生成模型ID
model_id = f"MODEL-{datetime.now().strftime('%Y%m%d')}-{str(len(self.model_versions)).zfill(4)}"
# 进行模型安全检查
security_assessment = self._perform_model_security_assessment(model, model_info)
if security_assessment['status'] == 'failed':
return {
'status': 'error',
'message': 'Model failed security assessment',
'issues': security_assessment['issues']
}
# 为模型添加安全元数据
secure_model = self._add_security_metadata(model, model_info, security_assessment)
# 注册模型
self.model_versions[model_id] = {
'model': secure_model,
'info': model_info,
'security_assessment': security_assessment,
'registered_at': datetime.now().isoformat(),
'version': model_info.get('version', '1.0.0'),
'status': 'active'
}
return {
'status': 'success',
'model_id': model_id,
'security_score': security_assessment['score']
}
def verify_model_integrity(self, model_id, current_model_hash):
"""验证模型完整性"""
if model_id not in self.model_versions:
return {'status': 'error', 'message': 'Model not found'}
registered_model = self.model_versions[model_id]
expected_hash = self._calculate_model_hash(registered_model['model'])
integrity_check = {
'model_id': model_id,
'expected_hash': expected_hash,
'actual_hash': current_model_hash,
'is_intact': expected_hash == current_model_hash,
'verified_at': datetime.now().isoformat()
}
if not integrity_check['is_intact']:
# 记录模型篡改事件
self._log_model_tampering_event(model_id, expected_hash, current_model_hash)
return integrity_check
def protect_model_against_adversarial_attacks(self, model_id):
"""增强模型对抗对抗性攻击的能力"""
if model_id not in self.model_versions:
return {'status': 'error', 'message': 'Model not found'}
model_info = self.model_versions[model_id]
model = model_info['model']
# 应用防御技术
protected_model = self._apply_defensive_techniques(model, model_info['info']['task_type'])
# 评估防御效果
defense_evaluation = self._evaluate_defense_effectiveness(model, protected_model)
# 更新模型
updated_model_id = f"{model_id}-DEFENDED-{datetime.now().strftime('%Y%m%d%H%M')}"
self.model_versions[updated_model_id] = {
'model': protected_model,
'info': model_info['info'],
'security_assessment': defense_evaluation,
'registered_at': datetime.now().isoformat(),
'version': model_info['info'].get('version', '1.0.0') + '-defended',
'status': 'active',
'parent_model': model_id
}
return {
'status': 'success',
'protected_model_id': updated_model_id,
'defense_effectiveness': defense_evaluation['effectiveness'],
'defense_techniques_applied': defense_evaluation['techniques']
}
def detect_model_drift(self, model_id, new_data):
"""检测模型漂移,识别模型性能下降"""
if model_id not in self.model_versions:
return {'status': 'error', 'message': 'Model not found'}
model = self.model_versions[model_id]['model']
# 进行模型漂移检测
drift_detection = self._perform_drift_detection(model, new_data)
return drift_detection
def generate_model_security_report(self, model_id):
"""生成模型安全报告"""
if model_id not in self.model_versions:
return {'status': 'error', 'message': 'Model not found'}
model_info = self.model_versions[model_id]
# 收集安全信息
security_report = {
'report_id': f"MODELSEC-{datetime.now().strftime('%Y%m%d')}-{model_id}",
'generated_at': datetime.now().isoformat(),
'model_id': model_id,
'model_info': model_info['info'],
'security_assessment': model_info['security_assessment'],
'current_status': model_info['status'],
'adversarial_robustness': self._assess_adversarial_robustness(model_id),
'privacy_analysis': self._analyze_privacy_issues(model_id),
'recommendations': self._generate_model_security_recommendations(model_info)
}
return security_report1.4 数据安全层
数据安全是具身AI系统安全的核心,涉及数据的收集、存储、处理和传输的全生命周期安全:
数据加密与保护
具身AI系统处理的敏感数据需要全面的加密保护:
- 存储加密:静态数据加密,保护存储的敏感信息
- 传输加密:确保数据在传输过程中的安全性
- 处理加密:考虑使用同态加密等技术保护处理中的数据
- 密钥管理:建立安全的密钥生成、分发、更新和销毁机制
隐私保护技术
具身AI系统需要采用先进的隐私保护技术,平衡数据利用与隐私保护:
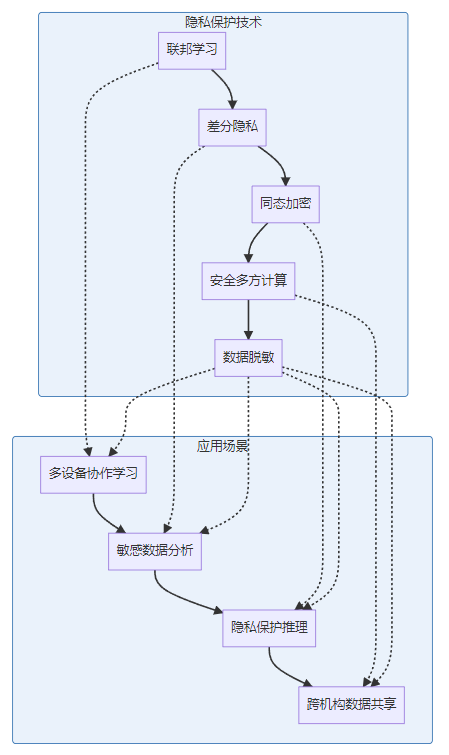
第二章:具身人工智能的主动响应策略
2.1 威胁检测机制
主动威胁检测是安全响应的前提,需要建立多层次、多维度的检测体系:
实时异常检测
实时异常检测能够及时发现具身AI系统的异常行为:
# 实时异常检测系统
class RealTimeAnomalyDetector:
def __init__(self, system_components):
self.components = system_components
self.baseline_behaviors = {}
self.anomaly_detection_models = {}
self.detection_history = []
def establish_baseline(self, component_id, training_data, baseline_type='statistical'):
"""为系统组件建立行为基线"""
if component_id not in self.components:
return {'status': 'error', 'message': f'Component {component_id} not found'}
# 根据基线类型选择建立方法
if baseline_type == 'statistical':
baseline = self._establish_statistical_baseline(training_data)
elif baseline_type == 'ml_based':
baseline = self._establish_ml_baseline(training_data)
elif baseline_type == 'hybrid':
baseline = self._establish_hybrid_baseline(training_data)
else:
return {'status': 'error', 'message': f'Unknown baseline type: {baseline_type}'}
# 存储基线
self.baseline_behaviors[component_id] = {
'baseline': baseline,
'type': baseline_type,
'established_at': datetime.now().isoformat(),
'training_data_size': len(training_data)
}
# 训练异常检测模型
detection_model = self._train_detection_model(training_data, baseline)
self.anomaly_detection_models[component_id] = detection_model
return {
'status': 'success',
'component_id': component_id,
'baseline_type': baseline_type,
'baseline_quality': self._evaluate_baseline_quality(baseline, training_data)
}
def detect_anomalies(self, component_id, real_time_data):
"""检测实时数据流中的异常"""
if component_id not in self.components:
return {'status': 'error', 'message': f'Component {component_id} not found'}
if component_id not in self.baseline_behaviors:
return {'status': 'error', 'message': f'No baseline established for {component_id}'}
baseline = self.baseline_behaviors[component_id]
detection_model = self.anomaly_detection_models[component_id]
# 执行异常检测
anomalies = self._execute_anomaly_detection(
real_time_data,
baseline['baseline'],
detection_model,
baseline['type']
)
# 评估异常严重性
for anomaly in anomalies:
anomaly['severity'] = self._assess_anomaly_severity(anomaly, component_id)
anomaly['timestamp'] = datetime.now().isoformat()
# 记录检测结果
detection_record = {
'component_id': component_id,
'timestamp': datetime.now().isoformat(),
'data_points_analyzed': len(real_time_data),
'anomalies_detected': len(anomalies),
'anomalies': anomalies
}
self.detection_history.append(detection_record)
return detection_record
def correlate_anomalies(self, time_window='5m'):
"""跨组件关联异常,识别系统性威胁"""
# 获取指定时间窗口内的检测记录
recent_detections = self._get_recent_detections(time_window)
# 按时间和类型对异常进行分组
grouped_anomalies = self._group_anomalies_by_time_and_type(recent_detections)
# 执行异常关联分析
correlated_threats = self._identify_correlated_threats(grouped_anomalies)
return {
'correlation_time_window': time_window,
'timestamp': datetime.now().isoformat(),
'detections_analyzed': len(recent_detections),
'correlated_threats': correlated_threats,
'threat_assessment': self._assess_threats_severity(correlated_threats)
}
def update_detection_models(self, component_id, new_training_data):
"""更新异常检测模型,适应系统行为变化"""
if component_id not in self.components:
return {'status': 'error', 'message': f'Component {component_id} not found'}
if component_id not in self.baseline_behaviors:
return {'status': 'error', 'message': f'No baseline established for {component_id}'}
baseline_info = self.baseline_behaviors[component_id]
# 重新训练或更新检测模型
updated_model = self._update_detection_model(
self.anomaly_detection_models[component_id],
new_training_data,
baseline_info['baseline'],
baseline_info['type']
)
# 更新模型
self.anomaly_detection_models[component_id] = updated_model
# 评估更新后的模型性能
model_performance = self._evaluate_model_performance(
updated_model,
new_training_data,
baseline_info['baseline']
)
return {
'status': 'success',
'component_id': component_id,
'model_updated_at': datetime.now().isoformat(),
'performance_metrics': model_performance
}
def generate_anomaly_detection_report(self, time_period='24h'):
"""生成异常检测报告"""
# 获取指定时间段内的检测历史
detection_period = self._get_detection_period(time_period)
# 汇总异常检测统计
anomaly_stats = self._aggregate_anomaly_statistics(detection_period)
# 分析异常趋势
anomaly_trends = self._analyze_anomaly_trends(detection_period)
# 生成报告
report = {
'report_id': f"ANOMALY-{datetime.now().strftime('%Y%m%d')}-{str(len(self.detection_history)).zfill(4)}",
'generated_at': datetime.now().isoformat(),
'time_period': time_period,
'summary_statistics': anomaly_stats,
'component_performance': self._evaluate_component_performance(detection_period),
'anomaly_trends': anomaly_trends,
'recommendations': self._generate_detection_recommendations(anomaly_stats, anomaly_trends)
}
return report2.2 安全响应自动化
安全响应自动化能够提高响应速度,减少人为错误,确保安全事件得到及时处理:
响应策略引擎
安全响应策略引擎根据安全事件的类型、级别和上下文,自动执行相应的响应措施:
# 安全响应策略引擎
class SecurityResponseEngine:
def __init__(self, system_components):
self.components = system_components
self.response_policies = {}
self.response_history = []
self.active_incidents = {}
def define_response_policy(self, event_type, severity, response_actions):
"""定义安全事件响应策略"""
policy_id = f"POLICY-{event_type}-{severity}-{datetime.now().strftime('%Y%m%d%H%M')}"
# 验证响应动作的有效性
validated_actions = []
for action in response_actions:
if self._validate_response_action(action):
validated_actions.append(action)
# 存储响应策略
self.response_policies[policy_id] = {
'event_type': event_type,
'severity': severity,
'response_actions': validated_actions,
'defined_at': datetime.now().isoformat(),
'status': 'active'
}
return {
'status': 'success',
'policy_id': policy_id,
'validated_actions': len(validated_actions),
'event_type': event_type,
'severity': severity
}
def process_security_event(self, security_event):
"""处理安全事件,执行相应的响应措施"""
# 确定事件类型和严重性
event_type = security_event['type']
severity = self._assess_event_severity(security_event)
# 创建安全事件记录
incident_id = self._create_security_incident(security_event, event_type, severity)
# 查找匹配的响应策略
matching_policies = self._find_matching_policies(event_type, severity)
# 执行响应措施
response_results = []
for policy in matching_policies:
policy_actions = self.response_policies[policy]['response_actions']
for action in policy_actions:
action_result = self._execute_response_action(action, security_event, incident_id)
response_results.append(action_result)
# 更新事件状态
self._update_incident_status(incident_id, 'responding', response_results)
# 记录响应历史
response_record = {
'incident_id': incident_id,
'event_type': event_type,
'severity': severity,
'response_timestamp': datetime.now().isoformat(),
'response_actions': response_results,
'matched_policies': matching_policies
}
self.response_history.append(response_record)
return {
'status': 'responding',
'incident_id': incident_id,
'response_actions_executed': len(response_results),
'matched_policies': matching_policies
}
def escalate_security_incident(self, incident_id, escalation_level):
"""升级安全事件,执行更高级别的响应措施"""
if incident_id not in self.active_incidents:
return {'status': 'error', 'message': f'Incident {incident_id} not found'}
incident = self.active_incidents[incident_id]
# 验证升级级别
if not self._validate_escalation_level(escalation_level, incident['severity']):
return {'status': 'error', 'message': f'Invalid escalation level: {escalation_level}'}
# 查找升级响应策略
escalation_policies = self._find_escalation_policies(
incident['event_type'],
escalation_level
)
# 执行升级响应措施
escalation_results = []
for policy in escalation_policies:
policy_actions = self.response_policies[policy]['response_actions']
for action in policy_actions:
action_result = self._execute_response_action(action, incident['details'], incident_id)
escalation_results.append(action_result)
# 更新事件状态
self._update_incident_status(incident_id, 'escalated', escalation_results)
# 更新事件严重性
incident['severity'] = escalation_level
return {
'status': 'escalated',
'incident_id': incident_id,
'new_severity_level': escalation_level,
'escalation_actions_executed': len(escalation_results)
}
def resolve_security_incident(self, incident_id, resolution_details):
"""解决安全事件,关闭事件记录"""
if incident_id not in self.active_incidents:
return {'status': 'error', 'message': f'Incident {incident_id} not found'}
incident = self.active_incidents[incident_id]
# 验证系统状态是否安全
if not self._verify_system_secure(incident['affected_components']):
return {'status': 'error', 'message': 'System not in secure state, cannot resolve'}
# 更新事件状态
resolution_record = {
'resolution_time': datetime.now().isoformat(),
'resolution_details': resolution_details,
'resolution_type': self._determine_resolution_type(resolution_details),
'verified_secure': True
}
incident['status'] = 'resolved'
incident['resolution'] = resolution_record
incident['resolved_at'] = datetime.now().isoformat()
# 从活跃事件中移除
resolved_incident = self.active_incidents.pop(incident_id)
# 记录事件总结
self._log_incident_summary(resolved_incident)
return {
'status': 'resolved',
'incident_id': incident_id,
'resolution_time': resolution_record['resolution_time'],
'incident_duration': self._calculate_incident_duration(resolved_incident)
}
def generate_incident_response_report(self, incident_id=None, time_period='7d'):
"""生成安全事件响应报告"""
if incident_id:
# 生成单个事件的报告
if incident_id not in self.response_history:
return {'status': 'error', 'message': f'Incident {incident_id} not found in history'}
incident_data = self._retrieve_incident_data(incident_id)
report = self._generate_single_incident_report(incident_data)
else:
# 生成时间段内的报告
time_range = self._get_time_range(time_period)
incidents_in_period = self._get_incidents_in_time_range(time_range)
report = self._generate_periodic_incident_report(incidents_in_period, time_period)
return report自动防御措施
具身AI系统可以实施多种自动防御措施,及时应对安全威胁:
防御措施 | 触发条件 | 实施方式 | 预期效果 | 适用场景 |
|---|---|---|---|---|
隔离受感染组件 | 检测到组件异常行为 | 网络隔离、功能隔离 | 防止威胁扩散 | 组件级安全事件 |
安全模式切换 | 检测到高级威胁 | 切换到安全运行模式 | 确保系统安全运行 | 系统级安全事件 |
自动补丁安装 | 发现已知漏洞 | 自动下载并应用补丁 | 修复安全漏洞 | 已知漏洞响应 |
流量过滤 | 检测到异常流量 | 启动流量过滤规则 | 阻止恶意流量 | 网络攻击防护 |
安全状态重置 | 严重安全事件后 | 恢复到已知安全状态 | 消除持续威胁 | 严重入侵响应 |
2.3 自适应安全防护
自适应安全防护能够根据环境变化和威胁情况,动态调整安全策略和措施:
动态安全策略调整
根据系统状态、环境变化和威胁情报,动态调整安全策略:
# 自适应安全策略管理器
class AdaptiveSecurityPolicyManager:
def __init__(self, system_state_monitor, threat_intelligence_source):
self.system_state = system_state_monitor
self.threat_intel = threat_intelligence_source
self.security_policies = {}
self.policy_history = []
self.adaptation_rules = []
def define_adaptation_rule(self, condition, policy_changes):
"""定义安全策略自适应规则"""
rule_id = f"RULE-{datetime.now().strftime('%Y%m%d%H%M%S')}-{random.randint(1000, 9999)}"
# 验证条件和策略变更
validated_condition = self._validate_adaptation_condition(condition)
validated_changes = self._validate_policy_changes(policy_changes)
# 存储自适应规则
self.adaptation_rules.append({
'rule_id': rule_id,
'condition': validated_condition,
'policy_changes': validated_changes,
'created_at': datetime.now().isoformat(),
'status': 'active'
})
return {
'status': 'success',
'rule_id': rule_id,
'message': 'Adaptation rule defined successfully'
}
def evaluate_adaptation_conditions(self):
"""评估所有自适应规则的条件,识别需要应用的规则"""
applicable_rules = []
# 获取当前系统状态
current_state = self.system_state.get_current_state()
# 获取最新威胁情报
latest_threats = self.threat_intel.get_latest_threats()
# 评估每个规则
for rule in self.adaptation_rules:
if rule['status'] != 'active':
continue
condition_met = self._evaluate_condition(
rule['condition'],
current_state,
latest_threats
)
if condition_met:
applicable_rules.append(rule)
return {
'timestamp': datetime.now().isoformat(),
'system_state_summary': self._summarize_system_state(current_state),
'relevant_threats': self._identify_relevant_threats(latest_threats, current_state),
'applicable_rules': [r['rule_id'] for r in applicable_rules],
'rules_details': applicable_rules
}
def adapt_security_policies(self):
"""根据适用规则调整安全策略"""
# 评估适用规则
evaluation_result = self.evaluate_adaptation_conditions()
policy_changes = []
# 应用每个适用规则
for rule in evaluation_result['rules_details']:
# 记录当前策略状态
policy_snapshot = self._take_policy_snapshot()
# 应用策略变更
for change in rule['policy_changes']:
change_result = self._apply_policy_change(change)
if change_result['status'] == 'success':
policy_changes.append(change_result)
# 记录策略适应历史
self._log_policy_adaptation(
rule['rule_id'],
policy_snapshot,
policy_changes,
evaluation_result['system_state_summary'],
evaluation_result['relevant_threats']
)
return {
'status': 'completed',
'adaptation_timestamp': datetime.now().isoformat(),
'rules_applied': evaluation_result['applicable_rules'],
'policy_changes_executed': len(policy_changes),
'system_state': evaluation_result['system_state_summary']
}
def optimize_security_policies(self):
"""优化安全策略,平衡安全性和系统性能"""
# 获取当前系统性能数据
performance_data = self.system_state.get_performance_metrics()
# 分析安全策略对性能的影响
policy_impact = self._analyze_policy_performance_impact(performance_data)
# 识别可优化的策略
optimizable_policies = self._identify_optimizable_policies(policy_impact)
# 应用优化
optimization_results = []
for policy in optimizable_policies:
optimization = self._optimize_policy(policy, policy_impact[policy['policy_id']])
if optimization['status'] == 'success':
optimization_results.append(optimization)
return {
'status': 'completed',
'optimization_timestamp': datetime.now().isoformat(),
'policies_optimized': len(optimization_results),
'performance_improvement': self._calculate_performance_improvement(optimization_results),
'security_impact': self._assess_security_impact(optimization_results)
}
def generate_adaptation_report(self, time_period='7d'):
"""生成安全策略自适应报告"""
# 获取指定时间段内的适应历史
time_range = self._get_time_range(time_period)
adaptation_history = self._get_adaptation_history(time_range)
# 分析适应模式
adaptation_patterns = self._analyze_adaptation_patterns(adaptation_history)
# 评估适应有效性
effectiveness = self._evaluate_adaptation_effectiveness(adaptation_history)
# 生成报告
report = {
'report_id': f"ADAPT-{datetime.now().strftime('%Y%m%d')}-{str(len(self.policy_history)).zfill(4)}",
'generated_at': datetime.now().isoformat(),
'time_period': time_period,
'adaptation_summary': {
'total_adaptations': len(adaptation_history),
'rules_triggered': self._count_rule_triggers(adaptation_history),
'policies_changed': self._count_policy_changes(adaptation_history)
},
'adaptation_patterns': adaptation_patterns,
'effectiveness_metrics': effectiveness,
'recommendations': self._generate_adaptation_recommendations(adaptation_patterns, effectiveness)
}
return report第三章:具身人工智能的安全监控与态势感知
3.1 安全监控系统
全面的安全监控系统能够实时掌握具身AI系统的安全状态,及时发现潜在威胁:
统一监控平台
构建统一的安全监控平台,整合各组件的安全信息:
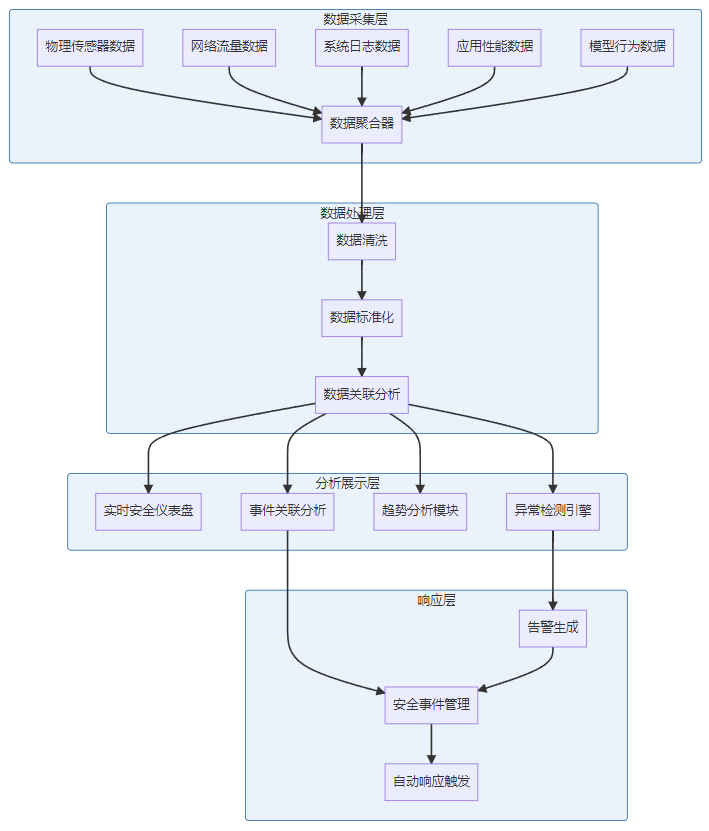
关键监控指标
具身AI系统的安全监控需要关注多维度的关键指标:
监控维度 | 关键指标 | 预警阈值 | 监控频率 | 安全意义 |
|---|---|---|---|---|
硬件健康 | CPU温度、内存使用率、电源状态 | 根据设备规格 | 1分钟 | 早期发现硬件故障 |
网络安全 | 异常连接数、流量模式变化、加密状态 | 基线偏差20% | 实时 | 检测网络攻击 |
系统行为 | 进程活动、权限变更、文件操作 | 基于历史行为 | 实时 | 检测系统入侵 |
模型性能 | 预测准确率变化、推理时间、输入异常 | 准确率下降5% | 每次推理 | 检测模型篡改 |
安全策略 | 策略执行状态、违规次数 | 任何违规 | 实时 | 确保策略合规 |
3.2 安全态势感知
安全态势感知能够提供具身AI系统安全状态的整体视图,帮助理解安全威胁的全貌和演变趋势:
威胁情报整合
整合内部和外部威胁情报,提升威胁检测和响应能力:
# 安全态势感知系统
class SecuritySituationAwarenessSystem:
def __init__(self, data_sources):
self.data_sources = data_sources
self.situation_data = {}
self.threat_intelligence = {}
self.visualization_data = {}
def collect_situation_data(self):
"""收集多源态势感知数据"""
collected_data = {}
for source_id, source_config in self.data_sources.items():
try:
# 从数据源收集数据
source_data = self._collect_from_source(source_id, source_config)
collected_data[source_id] = {
'data': source_data,
'timestamp': datetime.now().isoformat(),
'status': 'success'
}
except Exception as e:
collected_data[source_id] = {
'error': str(e),
'timestamp': datetime.now().isoformat(),
'status': 'error'
}
# 更新态势数据
self.situation_data = collected_data
return {
'status': 'completed',
'collected_at': datetime.now().isoformat(),
'sources_count': len(collected_data),
'successful_sources': sum(1 for s in collected_data.values() if s['status'] == 'success')
}
def integrate_threat_intelligence(self):
"""整合威胁情报数据"""
threat_intel = {
'internal_threats': self._collect_internal_threats(),
'external_threats': self._collect_external_threats(),
'industry_alarms': self._collect_industry_alarms(),
'vulnerability_data': self._collect_vulnerability_data()
}
# 整合和关联威胁情报
integrated_intel = self._integrate_and_correlate_threats(threat_intel)
# 更新威胁情报
self.threat_intelligence = integrated_intel
return {
'status': 'completed',
'integration_time': datetime.now().isoformat(),
'threat_sources': len(threat_intel),
'relevant_threats': len(integrated_intel['prioritized_threats'])
}
def assess_security_situation(self):
"""评估当前安全态势"""
# 确保有最新数据
self.collect_situation_data()
self.integrate_threat_intelligence()
# 分析系统状态
system_status = self._analyze_system_status(self.situation_data)
# 评估威胁级别
threat_assessment = self._assess_threat_level(self.threat_intelligence, system_status)
# 识别关键风险
key_risks = self._identify_key_risks(system_status, threat_assessment)
# 综合态势评估
situation_assessment = {
'timestamp': datetime.now().isoformat(),
'overall_status': self._determine_overall_status(system_status, threat_assessment),
'system_health': system_status,
'threat_level': threat_assessment,
'key_risks': key_risks,
'risk_factors': self._analyze_risk_factors(key_risks)
}
# 更新可视化数据
self.visualization_data = self._prepare_visualization_data(situation_assessment)
return situation_assessment
def predict_security_trends(self, time_horizon='24h'):
"""预测安全趋势,提前识别潜在风险"""
# 获取历史态势数据
historical_data = self._get_historical_situation_data()
# 分析趋势模式
trend_patterns = self._analyze_trend_patterns(historical_data)
# 预测未来态势
predicted_situation = self._predict_future_situation(
historical_data,
trend_patterns,
time_horizon
)
# 识别潜在风险事件
potential_events = self._identify_potential_risk_events(predicted_situation)
return {
'prediction_time': datetime.now().isoformat(),
'time_horizon': time_horizon,
'predicted_situation': predicted_situation,
'potential_events': potential_events,
'confidence_level': self._calculate_prediction_confidence(trend_patterns)
}
def generate_situation_report(self, report_type='current'):
"""生成安全态势报告"""
if report_type == 'current':
# 生成当前态势报告
situation_assessment = self.assess_security_situation()
report = self._generate_current_situation_report(situation_assessment)
elif report_type == 'trend':
# 生成趋势分析报告
historical_data = self._get_historical_situation_data()
report = self._generate_trend_analysis_report(historical_data)
elif report_type == 'prediction':
# 生成预测报告
prediction = self.predict_security_trends()
report = self._generate_prediction_report(prediction)
else:
return {'status': 'error', 'message': f'Unknown report type: {report_type}'}
return report态势可视化
通过直观的可视化方式展示安全态势,帮助安全人员快速理解和响应:
- 安全仪表盘:实时展示关键安全指标和状态
- 威胁地图:可视化威胁来源和影响范围
- 事件时间线:展示安全事件的发生和发展过程
- 关联分析图:展示安全事件之间的关联关系
- 风险热图:直观展示系统各部分的风险分布
3.3 安全日志管理
完善的安全日志管理对于事件追溯、审计和分析至关重要:
日志收集与存储
全面收集和安全存储具身AI系统的各类安全日志:
# 安全日志管理系统
class SecurityLogManager:
def __init__(self, log_config):
self.config = log_config
self.log_sources = {}
self.log_storage = self._initialize_log_storage()
self.log_processors = []
def register_log_source(self, source_id, source_config):
"""注册日志源"""
# 验证日志源配置
validated_config = self._validate_source_config(source_config)
# 注册日志源
self.log_sources[source_id] = {
'config': validated_config,
'status': 'active',
'registered_at': datetime.now().isoformat()
}
# 初始化日志收集器
self._initialize_log_collector(source_id, validated_config)
return {
'status': 'success',
'source_id': source_id,
'message': 'Log source registered successfully'
}
def collect_logs(self):
"""收集所有注册日志源的日志"""
collection_results = {}
total_logs = 0
for source_id, source_info in self.log_sources.items():
if source_info['status'] != 'active':
continue
try:
# 收集日志
logs = self._collect_source_logs(source_id, source_info['config'])
# 处理日志
processed_logs = self._process_logs(logs, source_id)
# 存储日志
storage_result = self._store_logs(processed_logs, source_id)
total_logs += len(processed_logs)
collection_results[source_id] = {
'status': 'success',
'logs_collected': len(logs),
'logs_processed': len(processed_logs),
'storage_result': storage_result
}
except Exception as e:
collection_results[source_id] = {
'status': 'error',
'error': str(e)
}
return {
'collection_time': datetime.now().isoformat(),
'sources_collected': len(collection_results),
'total_logs_processed': total_logs,
'source_results': collection_results
}
def search_logs(self, query_parameters):
"""搜索日志"""
# 验证查询参数
validated_query = self._validate_query_parameters(query_parameters)
# 构建查询
search_query = self._build_search_query(validated_query)
# 执行搜索
search_results = self._execute_log_search(search_query)
# 分页和格式化结果
formatted_results = self._format_search_results(
search_results,
validated_query.get('page', 1),
validated_query.get('page_size', 100)
)
return {
'search_time': datetime.now().isoformat(),
'query': validated_query,
'total_results': search_results['total_count'],
'page': validated_query.get('page', 1),
'page_size': validated_query.get('page_size', 100),
'results': formatted_results
}
def analyze_logs(self, analysis_type, parameters):
"""分析日志,识别模式和异常"""
# 验证分析参数
validated_params = self._validate_analysis_parameters(analysis_type, parameters)
# 根据分析类型执行不同的分析
if analysis_type == 'pattern_detection':
analysis_results = self._detect_log_patterns(validated_params)
elif analysis_type == 'anomaly_detection':
analysis_results = self._detect_log_anomalies(validated_params)
elif analysis_type == 'correlation_analysis':
analysis_results = self._correlate_log_events(validated_params)
else:
return {'status': 'error', 'message': f'Unknown analysis type: {analysis_type}'}
return {
'analysis_time': datetime.now().isoformat(),
'analysis_type': analysis_type,
'parameters': validated_params,
'results': analysis_results
}
def generate_log_report(self, report_config):
"""生成日志分析报告"""
# 验证报告配置
validated_config = self._validate_report_config(report_config)
# 获取报告所需的日志数据
log_data = self._retrieve_report_logs(validated_config)
# 分析日志数据
report_analysis = self._analyze_report_logs(log_data, validated_config)
# 生成报告内容
report_content = self._generate_report_content(report_analysis, validated_config)
# 格式化报告
formatted_report = self._format_report(report_content, validated_config.get('format', 'json'))
return {
'report_id': f"LOGREP-{datetime.now().strftime('%Y%m%d')}-{random.randint(1000, 9999)}",
'generated_at': datetime.now().isoformat(),
'report_config': validated_config,
'report': formatted_report
}第四章:案例研究与实战指南
4.1 工业机器人安全防护案例
某汽车制造企业的工业机器人安全防护体系建设案例:
挑战与解决方案:
- 多层次安全威胁
- 问题:工业机器人面临物理攻击、网络攻击和内部威胁等多层次威胁
- 解决方案:实施物理隔离、网络分段、访问控制等多层次防御措施
- 安全与生产效率平衡
- 问题:过于严格的安全措施可能影响生产效率
- 解决方案:采用风险分级的自适应安全策略,根据风险级别动态调整安全措施
- 实时响应需求
- 问题:工业环境中安全事件需要快速响应,避免生产中断
- 解决方案:部署自动化安全响应系统,关键安全事件自动隔离受影响设备
实施成效:
- 安全事件检测时间从平均45分钟减少到3分钟
- 安全事件响应时间从平均2小时减少到15分钟
- 生产中断时间减少65%
- 安全合规性评分提高到98%
4.2 医疗机器人安全防护实践
某医院智能手术机器人安全防护体系建设实践:
医疗机器人安全防护实施路线:
阶段一:基础安全建设(1-2个月)
- 全面风险评估
- 建立基础安全策略
- 部署基本防护措施
- 安全意识培训
阶段二:纵深防御体系(2-3个月)
- 网络分段与隔离
- 加密通信实施
- 访问控制加固
- 异常检测系统部署
阶段三:主动防御能力(2-3个月)
- 自动化响应系统
- 安全态势感知平台
- 威胁情报整合
- 定期安全演练
阶段四:持续改进(持续进行)
- 安全评估与审计
- 威胁模型更新
- 安全措施优化
- 应急响应演练关键成功因素:
- 合规优先:严格遵循医疗设备安全法规和标准
- 人员培训:建立全面的安全意识培训体系
- 定期测试:定期进行安全评估和渗透测试
- 持续监控:实施24/7安全监控
- 应急准备:建立完善的应急响应流程
4.3 自动驾驶汽车安全架构
某自动驾驶公司的安全架构设计与实践:
多层次安全架构:
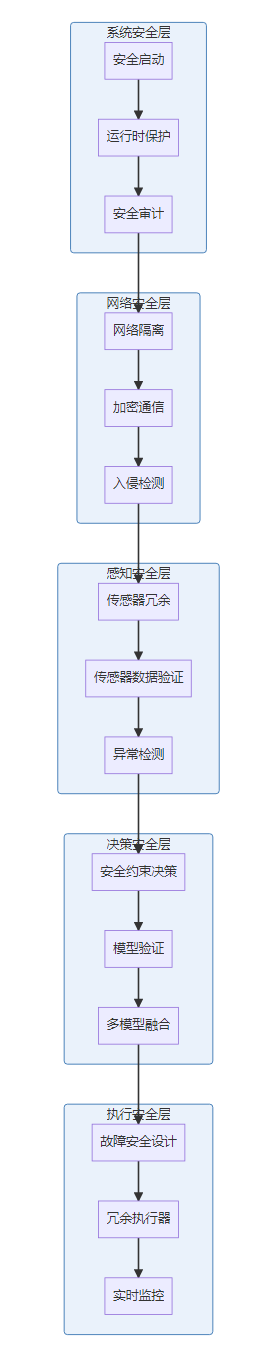
实践经验分享:
- 安全设计原则
- 故障安全设计:任何故障都导向安全状态
- 防御纵深:多层防御,单点故障不影响整体安全
- 冗余设计:关键功能冗余实现
- 最小权限:严格限制各组件权限
- 安全测试方法
- 模拟攻击测试:模拟各类安全威胁
- 边缘情况测试:测试极端条件下的系统表现
- 故障注入测试:测试系统故障恢复能力
- 红队演练:定期进行全面安全评估
第五章:互动问答:具身AI安全防护的未来
**问题1:随着量子计算技术的发展,具身AI系统的加密机制面临哪些挑战?我们应该如何提前布局量子安全防护?“”"
**问题2:具身AI系统的自主决策能力越来越强,这对传统的安全审计和责任认定带来了什么挑战?我们需要建立什么样的新型安全治理机制?“”"
**问题3:在复杂多变的环境中,具身AI系统如何实现动态的安全策略调整,在保证安全性的同时不影响系统的灵活性和适应性?“”"
**问题4:随着具身AI系统在关键基础设施中的广泛应用,如何建立国家级的具身AI安全防护体系,确保国家关键基础设施的安全?“”"
结论
具身人工智能的安全防护是一个复杂而系统的工程,需要从多层次防御架构、主动响应策略、实时监控机制等多个维度进行全面设计和实施。本文详细探讨了具身AI系统的安全防护体系,包括物理安全层、网络安全层、应用安全层和数据安全层的防御策略,以及威胁检测、安全响应自动化和自适应安全防护等主动响应机制。
我们认为,构建有效的具身AI安全防护体系需要遵循以下核心原则:
- 防御纵深:采用多层次、多维度的防御措施,形成纵深防御体系
- 主动防御:从被动防御转向主动检测和响应,提前识别和应对威胁
- 自适应调整:根据环境变化和威胁情况,动态调整安全策略和措施
- 持续监控:建立全面的安全监控和态势感知系统,实时掌握安全状态
- 快速响应:建立自动化的安全响应机制,提高响应速度和准确性
未来,随着具身AI技术的不断发展和应用场景的不断扩展,安全威胁也将变得更加复杂和多样化。我们需要持续关注技术发展趋势,不断更新和完善安全防护体系,同时加强行业合作和信息共享,共同应对具身AI安全挑战。
最终,我们的目标是构建一个安全、可靠、可信的具身AI系统,使其能够在为人类社会创造价值的同时,最大限度地降低安全风险,保障人类和环境的安全。
本文参与 腾讯云自媒体同步曝光计划,分享自作者个人站点/博客。
原始发表:2025-11-12,如有侵权请联系 cloudcommunity@tencent.com 删除
评论
登录后参与评论
推荐阅读
目录

