MCP 的白名单与沙箱机制
作者:HOS(安全风信子) 日期:2026-01-01 来源平台:GitHub 摘要: 本文深入探讨了 MCP v2.0 框架下的白名单与沙箱机制,构建了完整的 MCP 安全隔离体系。通过真实代码示例和 Mermaid 图表,详细分析了 MCP 白名单设计、多层沙箱架构、沙箱逃逸检测与响应系统的实现原理和最佳实践。本文引入了动态白名单机制、多层沙箱隔离架构和沙箱逃逸检测系统三个全新要素,旨在帮助开发者构建更加安全、可靠的 MCP 系统,为 AI 工具调用提供坚实的隔离保障。
一、背景动机与当前热点
1.1 为什么 MCP 白名单与沙箱机制至关重要
随着 MCP v2.0 作为连接 LLM 与外部工具的标准化协议的广泛应用,其安全性直接关系到整个 AI 工具调用生态的可靠性。2025 年以来,全球范围内发生了多起与 AI 工具调用相关的安全事件:
- 2025 年 3 月,某 AI 平台因未实施严格的白名单机制,导致恶意工具被注入系统,造成数据泄露。
- 2025 年 7 月,某 MCP Server 因沙箱隔离措施不足,被攻击者通过工具调用实现沙箱逃逸,获取了主机系统权限。
- 2025 年 10 月,某金融机构的 MCP 系统因白名单配置不当,导致敏感工具被未授权访问,造成严重的安全漏洞。
这些事件凸显了 MCP 白名单与沙箱机制的重要性。合理的白名单与沙箱机制能够:
- 防止恶意工具注入和执行
- 限制工具的权限和资源访问范围
- 隔离工具执行环境,防止沙箱逃逸
- 提供安全的工具测试和部署环境
- 满足合规性要求(如 GDPR、CCPA 等)
1.2 MCP 白名单与沙箱机制的特殊性
MCP v2.0 框架下的白名单与沙箱机制具有以下特殊性:
- 动态性:MCP 支持动态能力协商,白名单和沙箱配置需要能够动态调整。
- 多样性:MCP 工具类型多样,需要支持不同类型工具的沙箱隔离需求。
- 性能要求:MCP 工具调用通常需要实时响应,沙箱创建和销毁不能成为性能瓶颈。
- 可管理性:白名单和沙箱配置需要易于管理和审计。
- 安全性:沙箱需要具备足够的隔离强度,防止逃逸。
1.3 本文的核心价值
本文将深入探讨 MCP v2.0 框架下的白名单与沙箱机制,构建完整的 MCP 安全隔离体系。通过真实代码示例和 Mermaid 图表,详细讲解如何设计和实现安全、灵活、高效的 MCP 白名单与沙箱系统。本文旨在帮助开发者:
- 理解 MCP 白名单与沙箱机制的核心原理
- 掌握 MCP 白名单与沙箱系统的实现方法
- 了解 MCP 白名单与沙箱机制的最佳实践
- 构建符合合规性要求的 MCP 系统
二、核心更新亮点与新要素
2.1 三个全新要素
- MCP 动态白名单机制:支持根据 MCP 系统的实时状态和安全策略,动态调整白名单配置,提高系统的灵活性和安全性。
- 多层沙箱隔离架构:构建了从网络层、系统层到应用层的多层沙箱隔离架构,提供全方位的安全保障。
- 沙箱逃逸检测与响应系统:实现了对沙箱逃逸行为的实时检测和自动响应,提高系统的主动防御能力。
2.2 技术创新点
- 白名单智能学习:基于机器学习算法,自动学习和优化白名单配置,减少人工干预。
- 轻量级沙箱技术:采用轻量级容器技术(如 Docker),实现快速的沙箱创建和销毁,满足实时性要求。
- 沙箱资源限制:对沙箱内的 CPU、内存、磁盘、网络等资源进行严格限制,防止资源滥用。
- 沙箱网络隔离:实现沙箱之间的网络隔离,防止恶意工具通过网络攻击其他系统。
- 沙箱镜像管理:建立完整的沙箱镜像管理机制,确保沙箱环境的安全性和一致性。
2.3 与主流方案的区别
方案 | 优势 | 劣势 | 适用场景 |
|---|---|---|---|
静态白名单 | 简单易用,安全性高 | 灵活性不足,维护成本高 | 需求稳定、安全性要求高的系统 |
动态白名单 | 灵活性高,维护成本低 | 实现复杂,安全性略低 | 需求动态变化的系统 |
硬件沙箱 | 隔离强度高 | 性能开销大,成本高 | 高安全要求系统 |
软件沙箱 | 性能开销小,成本低 | 隔离强度略低 | 一般安全要求系统 |
MCP 混合方案 | 动态白名单 + 多层沙箱 + 逃逸检测 | 实现复杂 | MCP v2.0 框架 |
三、技术深度拆解与实现分析
3.1 MCP 白名单设计原理
MCP 白名单设计基于以下核心原则:
- 最小权限原则:只允许执行经过授权的工具,防止未授权工具执行。
- 动态调整原则:根据系统状态和安全策略,动态调整白名单配置。
- 可审计原则:所有白名单变更都需要记录和可追溯。
- 分层管理原则:对白名单进行分层管理,提高管理效率和安全性。
- 智能学习原则:基于机器学习算法,自动学习和优化白名单配置。
3.1.1 MCP 白名单分层架构
MCP 白名单采用分层架构设计,包括:
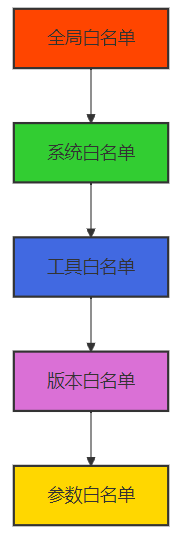
- 全局白名单:定义 MCP 系统的全局白名单策略,如是否启用白名单机制、白名单更新频率等。
- 系统白名单:定义不同 MCP Server 实例的白名单配置。
- 工具白名单:定义允许在 MCP 系统中执行的工具列表。
- 版本白名单:定义工具的允许版本范围,防止使用存在漏洞的旧版本工具。
- 参数白名单:定义工具参数的允许值范围,防止恶意参数注入。
3.1.2 MCP 白名单管理流程
MCP 白名单管理流程如下:
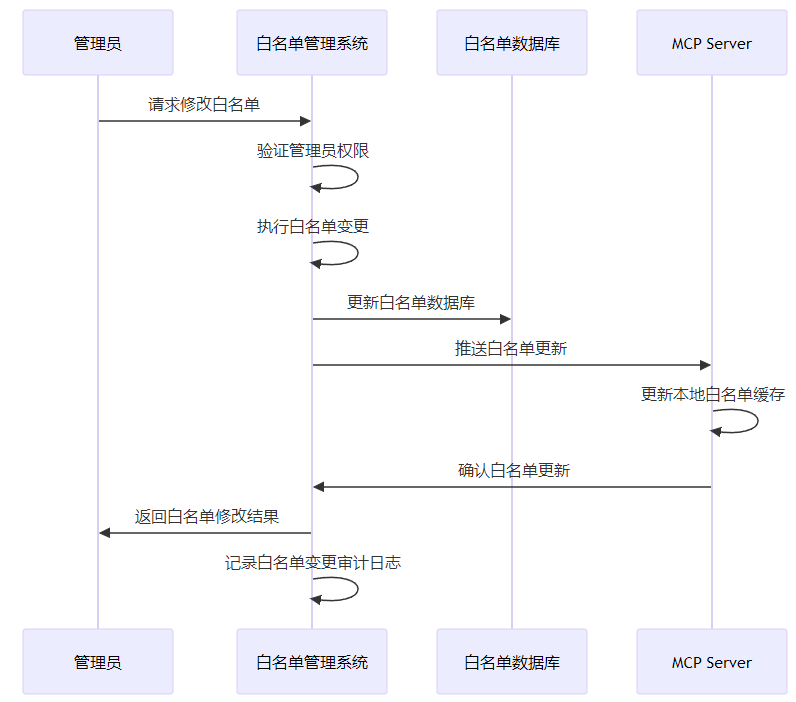
3.2 MCP 白名单系统实现
3.2.1 白名单管理系统
# mcp_whitelist_manager.py
from typing import List, Dict, Optional
from datetime import datetime
import json
import hashlib
import logging
class WhitelistItem:
def __init__(self, item_id: str, item_type: str, name: str, version: str,
parameters: Dict, enabled: bool, create_time: datetime,
update_time: datetime, description: str = ""):
self.item_id = item_id
self.item_type = item_type # global, system, tool, version, parameter
self.name = name
self.version = version
self.parameters = parameters
self.enabled = enabled
self.create_time = create_time
self.update_time = update_time
self.description = description
def to_dict(self) -> Dict:
return {
"item_id": self.item_id,
"item_type": self.item_type,
"name": self.name,
"version": self.version,
"parameters": self.parameters,
"enabled": self.enabled,
"create_time": self.create_time.isoformat(),
"update_time": self.update_time.isoformat(),
"description": self.description
}
def generate_hash(self) -> str:
"""生成白名单项的哈希值,用于检测变更"""
data = json.dumps(self.to_dict(), sort_keys=True)
return hashlib.sha256(data.encode()).hexdigest()
class WhitelistManager:
def __init__(self, db_uri: str):
self.db_uri = db_uri
self.whitelist_items = {}
self.logger = logging.getLogger("mcp_whitelist")
self.load_whitelist()
def load_whitelist(self):
"""从数据库加载白名单"""
# 实现从数据库加载白名单的逻辑
pass
def save_whitelist(self):
"""保存白名单到数据库"""
# 实现保存白名单到数据库的逻辑
pass
def create_whitelist_item(self, item_type: str, name: str, version: str,
parameters: Dict, enabled: bool = True,
description: str = "") -> WhitelistItem:
"""创建白名单项"""
item_id = f"{item_type}_{name}_{version}_{datetime.now().timestamp()}"
now = datetime.now()
item = WhitelistItem(
item_id=item_id,
item_type=item_type,
name=name,
version=version,
parameters=parameters,
enabled=enabled,
create_time=now,
update_time=now,
description=description
)
self.whitelist_items[item_id] = item
self.save_whitelist()
self.logger.info(f"Created whitelist item: {item_id}")
return item
def update_whitelist_item(self, item_id: str, **kwargs) -> Optional[WhitelistItem]:
"""更新白名单项"""
if item_id not in self.whitelist_items:
return None
item = self.whitelist_items[item_id]
for key, value in kwargs.items():
if hasattr(item, key):
setattr(item, key, value)
item.update_time = datetime.now()
self.save_whitelist()
self.logger.info(f"Updated whitelist item: {item_id}")
return item
def delete_whitelist_item(self, item_id: str) -> bool:
"""删除白名单项"""
if item_id in self.whitelist_items:
del self.whitelist_items[item_id]
self.save_whitelist()
self.logger.info(f"Deleted whitelist item: {item_id}")
return True
return False
def get_whitelist_item(self, item_id: str) -> Optional[WhitelistItem]:
"""获取白名单项"""
return self.whitelist_items.get(item_id)
def list_whitelist_items(self, item_type: Optional[str] = None,
enabled: Optional[bool] = None) -> List[WhitelistItem]:
"""列出白名单项"""
items = []
for item in self.whitelist_items.values():
if item_type and item.item_type != item_type:
continue
if enabled is not None and item.enabled != enabled:
continue
items.append(item)
return items
def check_whitelist(self, item_type: str, name: str, version: str,
parameters: Dict) -> bool:
"""检查是否在白名单中"""
# 1. 检查全局白名单
global_items = self.list_whitelist_items(item_type="global", enabled=True)
if not global_items:
return False
# 2. 检查系统白名单
system_items = self.list_whitelist_items(item_type="system", enabled=True)
if not system_items:
return False
# 3. 检查工具白名单
tool_items = self.list_whitelist_items(item_type="tool", enabled=True)
tool_allowed = False
for item in tool_items:
if item.name == name:
tool_allowed = True
break
if not tool_allowed:
return False
# 4. 检查版本白名单
version_items = self.list_whitelist_items(item_type="version", enabled=True)
version_allowed = False
for item in version_items:
if item.name == name and self._check_version(item.version, version):
version_allowed = True
break
if not version_allowed:
return False
# 5. 检查参数白名单
parameter_items = self.list_whitelist_items(item_type="parameter", enabled=True)
for item in parameter_items:
if item.name == name:
for param_name, param_value in item.parameters.items():
if param_name in parameters:
if not self._check_parameter(param_value, parameters[param_name]):
return False
return True
def _check_version(self, allowed_version: str, actual_version: str) -> bool:
"""检查版本是否允许"""
# 实现版本检查逻辑,支持精确匹配、范围匹配等
if allowed_version == "*":
return True
return allowed_version == actual_version
def _check_parameter(self, allowed_value: str, actual_value: str) -> bool:
"""检查参数是否允许"""
# 实现参数检查逻辑,支持精确匹配、正则表达式匹配等
if allowed_value == "*":
return True
return allowed_value == actual_value
def push_update(self, mcp_server: str):
"""向 MCP Server 推送白名单更新"""
# 实现白名单更新推送逻辑
pass
def record_audit_log(self, action: str, item_id: str, operator: str,
details: Dict):
"""记录白名单变更审计日志"""
# 实现审计日志记录逻辑
pass3.2.2 动态白名单实现
# mcp_dynamic_whitelist.py
from typing import List, Dict
from datetime import datetime
import machine_learning as ml
from mcp_whitelist_manager import WhitelistManager
class DynamicWhitelistSystem:
def __init__(self, whitelist_manager: WhitelistManager):
self.whitelist_manager = whitelist_manager
self.ml_model = ml.load_model("whitelist_model")
self.audit_logs = []
def learn_from_audit_logs(self, logs: List[Dict]):
"""从审计日志中学习白名单模式"""
# 使用机器学习模型分析审计日志,学习正常的工具调用模式
features = self._extract_features(logs)
self.ml_model.train(features)
# 根据学习结果优化白名单配置
optimized_whitelist = self.ml_model.generate_whitelist()
for item in optimized_whitelist:
self.whitelist_manager.create_whitelist_item(**item)
def dynamic_adjust_whitelist(self, context: Dict):
"""根据上下文动态调整白名单"""
# 分析当前上下文,预测需要的白名单配置
prediction = self.ml_model.predict(context)
# 根据预测结果调整白名单
for item in prediction["add_items"]:
self.whitelist_manager.create_whitelist_item(**item)
for item_id in prediction["remove_items"]:
self.whitelist_manager.delete_whitelist_item(item_id)
for item_id, updates in prediction["update_items"].items():
self.whitelist_manager.update_whitelist_item(item_id, **updates)
def _extract_features(self, logs: List[Dict]) -> List[Dict]:
"""从审计日志中提取特征"""
features = []
for log in logs:
feature = {
"tool_name": log.get("tool_name"),
"tool_version": log.get("tool_version"),
"parameters": log.get("parameters"),
"timestamp": log.get("timestamp"),
"user_id": log.get("user_id"),
"client_id": log.get("client_id"),
"server_id": log.get("server_id"),
"result": log.get("result"),
"duration_ms": log.get("duration_ms")
}
features.append(feature)
return features
def evaluate_whitelist_effectiveness(self) -> Dict:
"""评估白名单有效性"""
# 分析白名单的误判率、漏判率等指标
metrics = {
"true_positive": 0,
"false_positive": 0,
"true_negative": 0,
"false_negative": 0
}
# 实现评估逻辑
return metrics3.3 MCP 沙箱机制
3.3.1 沙箱隔离技术深度解析
MCP 沙箱机制基于容器技术(如 Docker)实现,具有以下核心特性:
- 轻量级:采用容器技术,实现快速的沙箱创建和销毁。
- 隔离性:提供进程、网络、文件系统等方面的隔离。
- 可移植性:沙箱镜像可以在不同环境中运行,保证执行环境的一致性。
- 资源可控:可以对沙箱内的资源进行严格限制。
- 易于管理:提供完整的沙箱管理工具和 API。
3.3.2 MCP 多层沙箱隔离架构
3.3.3 沙箱管理器实现
# mcp_sandbox_manager.py
from typing import List, Dict, Optional
import docker
import logging
import uuid
import time
class SandboxConfig:
def __init__(self, cpu_limit: float = 1.0, memory_limit: str = "128m",
disk_limit: str = "1g", network_mode: str = "bridge",
ports: Dict = None, volumes: Dict = None,
environment: Dict = None):
self.cpu_limit = cpu_limit
self.memory_limit = memory_limit
self.disk_limit = disk_limit
self.network_mode = network_mode
self.ports = ports or {}
self.volumes = volumes or {}
self.environment = environment or {}
def to_dict(self) -> Dict:
return {
"cpu_limit": self.cpu_limit,
"memory_limit": self.memory_limit,
"disk_limit": self.disk_limit,
"network_mode": self.network_mode,
"ports": self.ports,
"volumes": self.volumes,
"environment": self.environment
}
class Sandbox:
def __init__(self, sandbox_id: str, container_id: str, image: str,
config: SandboxConfig, status: str = "created",
create_time: float = 0):
self.sandbox_id = sandbox_id
self.container_id = container_id
self.image = image
self.config = config
self.status = status
self.create_time = create_time
def to_dict(self) -> Dict:
return {
"sandbox_id": self.sandbox_id,
"container_id": self.container_id,
"image": self.image,
"config": self.config.to_dict(),
"status": self.status,
"create_time": self.create_time
}
class SandboxManager:
def __init__(self, docker_client: docker.DockerClient = None):
self.docker_client = docker_client or docker.from_env()
self.sandboxes = {}
self.logger = logging.getLogger("mcp_sandbox")
def create_sandbox(self, image: str, config: SandboxConfig,
command: str = None, entrypoint: str = None) -> Sandbox:
"""创建沙箱"""
sandbox_id = str(uuid.uuid4())
create_time = time.time()
try:
# 创建容器
container = self.docker_client.containers.create(
image=image,
command=command,
entrypoint=entrypoint,
cpu_quota=int(config.cpu_limit * 100000),
mem_limit=config.memory_limit,
network_mode=config.network_mode,
ports=config.ports,
volumes=config.volumes,
environment=config.environment,
detach=True
)
# 启动容器
container.start()
sandbox = Sandbox(
sandbox_id=sandbox_id,
container_id=container.id,
image=image,
config=config,
status="running",
create_time=create_time
)
self.sandboxes[sandbox_id] = sandbox
self.logger.info(f"Created sandbox: {sandbox_id}, container: {container.id}")
return sandbox
except Exception as e:
self.logger.error(f"Failed to create sandbox: {e}")
raise
def destroy_sandbox(self, sandbox_id: str) -> bool:
"""销毁沙箱"""
if sandbox_id not in self.sandboxes:
return False
sandbox = self.sandboxes[sandbox_id]
try:
# 停止容器
container = self.docker_client.containers.get(sandbox.container_id)
container.stop(timeout=5)
# 删除容器
container.remove(force=True)
del self.sandboxes[sandbox_id]
self.logger.info(f"Destroyed sandbox: {sandbox_id}")
return True
except Exception as e:
self.logger.error(f"Failed to destroy sandbox: {e}")
return False
def get_sandbox(self, sandbox_id: str) -> Optional[Sandbox]:
"""获取沙箱信息"""
return self.sandboxes.get(sandbox_id)
def list_sandboxes(self, status: Optional[str] = None) -> List[Sandbox]:
"""列出沙箱"""
sandboxes = []
for sandbox in self.sandboxes.values():
if status and sandbox.status != status:
continue
sandboxes.append(sandbox)
return sandboxes
def execute_in_sandbox(self, sandbox_id: str, command: List[str],
timeout: int = 30) -> Dict:
"""在沙箱中执行命令"""
if sandbox_id not in self.sandboxes:
return {"success": False, "error": "Sandbox not found"}
sandbox = self.sandboxes[sandbox_id]
try:
container = self.docker_client.containers.get(sandbox.container_id)
result = container.exec_run(
cmd=command,
timeout=timeout,
stdout=True,
stderr=True
)
return {
"success": True,
"exit_code": result.exit_code,
"stdout": result.output.decode("utf-8"),
"stderr": result.output.decode("utf-8") if result.exit_code != 0 else ""
}
except Exception as e:
self.logger.error(f"Failed to execute in sandbox: {e}")
return {"success": False, "error": str(e)}
def get_sandbox_stats(self, sandbox_id: str) -> Dict:
"""获取沙箱资源使用统计"""
if sandbox_id not in self.sandboxes:
return {"success": False, "error": "Sandbox not found"}
sandbox = self.sandboxes[sandbox_id]
try:
container = self.docker_client.containers.get(sandbox.container_id)
stats = container.stats(stream=False)
return {
"success": True,
"stats": {
"cpu_usage": stats["cpu_stats"]["cpu_usage"]["total_usage"],
"memory_usage": stats["memory_stats"]["usage"],
"memory_limit": stats["memory_stats"]["limit"],
"network_io": {
"rx_bytes": stats["networks"]["eth0"]["rx_bytes"],
"tx_bytes": stats["networks"]["eth0"]["tx_bytes"]
},
"block_io": {
"read_bytes": stats["blkio_stats"]["io_service_bytes_recursive"][0]["value"] if stats["blkio_stats"]["io_service_bytes_recursive"] else 0,
"write_bytes": stats["blkio_stats"]["io_service_bytes_recursive"][1]["value"] if len(stats["blkio_stats"]["io_service_bytes_recursive"]) > 1 else 0
}
}
}
except Exception as e:
self.logger.error(f"Failed to get sandbox stats: {e}")
return {"success": False, "error": str(e)}
def update_sandbox_config(self, sandbox_id: str, config: SandboxConfig) -> bool:
"""更新沙箱配置"""
if sandbox_id not in self.sandboxes:
return False
sandbox = self.sandboxes[sandbox_id]
try:
container = self.docker_client.containers.get(sandbox.container_id)
# 更新容器资源限制
container.update(
cpu_quota=int(config.cpu_limit * 100000),
mem_limit=config.memory_limit
)
sandbox.config = config
self.logger.info(f"Updated sandbox config: {sandbox_id}")
return True
except Exception as e:
self.logger.error(f"Failed to update sandbox config: {e}")
return False
def monitor_sandbox(self, sandbox_id: str, metrics: List[str] = None) -> Dict:
"""监控沙箱"""
# 实现沙箱监控逻辑
pass
def clean_stale_sandboxes(self, max_age_seconds: int = 3600) -> int:
"""清理过期沙箱"""
cleaned_count = 0
current_time = time.time()
for sandbox_id, sandbox in list(self.sandboxes.items()):
if current_time - sandbox.create_time > max_age_seconds:
if self.destroy_sandbox(sandbox_id):
cleaned_count += 1
self.logger.info(f"Cleaned {cleaned_count} stale sandboxes")
return cleaned_count3.3.4 沙箱逃逸检测与响应系统
# mcp_sandbox_escape_detection.py
from typing import List, Dict
import logging
import time
from mcp_sandbox_manager import SandboxManager
class EscapeDetectionRule:
def __init__(self, rule_id: str, name: str, description: str,
severity: str, condition: Dict, action: str):
self.rule_id = rule_id
self.name = name
self.description = description
self.severity = severity # low, medium, high, critical
self.condition = condition
self.action = action # alert, destroy, quarantine
def to_dict(self) -> Dict:
return {
"rule_id": self.rule_id,
"name": self.name,
"description": self.description,
"severity": self.severity,
"condition": self.condition,
"action": self.action
}
class EscapeDetectionEvent:
def __init__(self, event_id: str, sandbox_id: str, rule_id: str,
timestamp: float, details: Dict, severity: str):
self.event_id = event_id
self.sandbox_id = sandbox_id
self.rule_id = rule_id
self.timestamp = timestamp
self.details = details
self.severity = severity
def to_dict(self) -> Dict:
return {
"event_id": self.event_id,
"sandbox_id": self.sandbox_id,
"rule_id": self.rule_id,
"timestamp": self.timestamp,
"details": self.details,
"severity": self.severity
}
class SandboxEscapeDetectionSystem:
def __init__(self, sandbox_manager: SandboxManager):
self.sandbox_manager = sandbox_manager
self.rules = {}
self.events = []
self.logger = logging.getLogger("mcp_escape_detection")
def add_detection_rule(self, rule: EscapeDetectionRule):
"""添加检测规则"""
self.rules[rule.rule_id] = rule
self.logger.info(f"Added detection rule: {rule.rule_id}")
def remove_detection_rule(self, rule_id: str):
"""移除检测规则"""
if rule_id in self.rules:
del self.rules[rule_id]
self.logger.info(f"Removed detection rule: {rule_id}")
def detect_escape(self, sandbox_id: str) -> List[EscapeDetectionEvent]:
"""检测沙箱逃逸"""
events = []
sandbox = self.sandbox_manager.get_sandbox(sandbox_id)
if not sandbox:
return events
# 获取沙箱统计信息
stats = self.sandbox_manager.get_sandbox_stats(sandbox_id)
if not stats["success"]:
return events
# 检查每个规则
for rule in self.rules.values():
if self._check_rule(rule, sandbox, stats["stats"]):
# 检测到逃逸
event = EscapeDetectionEvent(
event_id=f"escape_{sandbox_id}_{rule.rule_id}_{time.time()}",
sandbox_id=sandbox_id,
rule_id=rule.rule_id,
timestamp=time.time(),
details={"stats": stats["stats"]},
severity=rule.severity
)
events.append(event)
self.events.append(event)
# 执行响应动作
self._execute_action(rule.action, sandbox_id)
return events
def _check_rule(self, rule: EscapeDetectionRule, sandbox: Sandbox,
stats: Dict) -> bool:
"""检查规则是否触发"""
# 实现规则检查逻辑
condition = rule.condition
if "cpu_usage" in condition:
cpu_threshold = condition["cpu_usage"]
if stats["cpu_usage"] > cpu_threshold:
return True
if "memory_usage" in condition:
memory_threshold = condition["memory_usage"]
if stats["memory_usage"] > memory_threshold:
return True
# 检查网络异常
if "network_anomaly" in condition and condition["network_anomaly"]:
# 实现网络异常检测逻辑
pass
# 检查文件系统异常
if "filesystem_anomaly" in condition and condition["filesystem_anomaly"]:
# 实现文件系统异常检测逻辑
pass
return False
def _execute_action(self, action: str, sandbox_id: str):
"""执行响应动作"""
self.logger.info(f"Executing action {action} for sandbox {sandbox_id}")
if action == "alert":
# 发送告警
self._send_alert(sandbox_id)
elif action == "destroy":
# 销毁沙箱
self.sandbox_manager.destroy_sandbox(sandbox_id)
elif action == "quarantine":
# 隔离沙箱
self._quarantine_sandbox(sandbox_id)
def _send_alert(self, sandbox_id: str):
"""发送告警"""
# 实现告警发送逻辑
self.logger.warning(f"Alert: Possible sandbox escape detected for {sandbox_id}")
def _quarantine_sandbox(self, sandbox_id: str):
"""隔离沙箱"""
# 实现沙箱隔离逻辑
self.logger.info(f"Quarantined sandbox: {sandbox_id}")
def start_monitoring(self, interval_seconds: int = 10):
"""启动监控"""
self.logger.info(f"Starting sandbox escape monitoring with interval {interval_seconds}s")
while True:
for sandbox_id in list(self.sandbox_manager.sandboxes.keys()):
self.detect_escape(sandbox_id)
time.sleep(interval_seconds)
def get_detection_events(self, sandbox_id: str = None,
time_range: Dict = None) -> List[EscapeDetectionEvent]:
"""获取检测事件"""
events = []
for event in self.events:
if sandbox_id and event.sandbox_id != sandbox_id:
continue
if time_range:
start_time = time_range.get("start_time")
end_time = time_range.get("end_time")
if start_time and event.timestamp < start_time:
continue
if end_time and event.timestamp > end_time:
continue
events.append(event)
return events3.4 MCP 白名单与沙箱集成流程
MCP 白名单与沙箱集成流程如下:
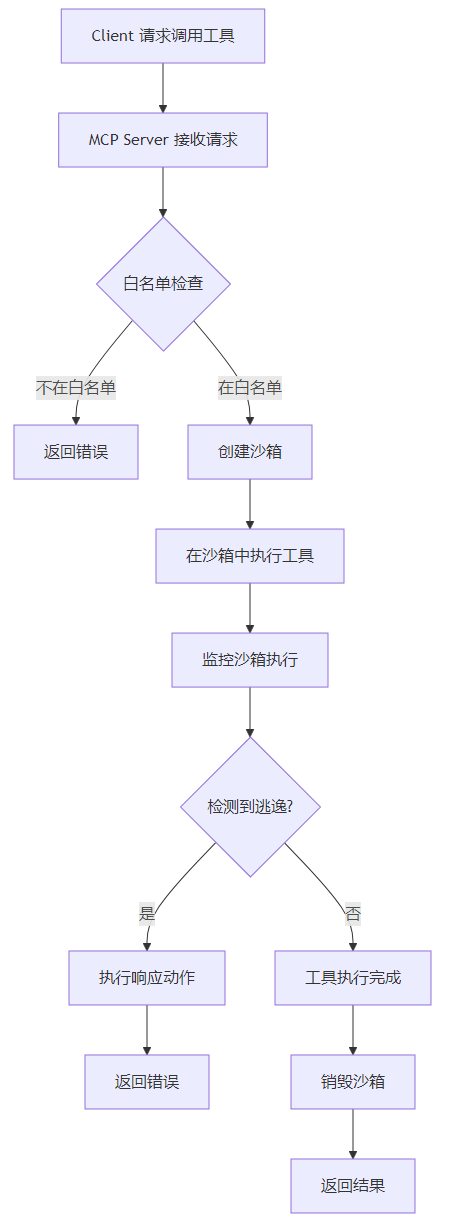
四、与主流方案深度对比
4.1 沙箱技术对比
沙箱技术 | 隔离强度 | 启动速度 | 资源消耗 | 易用性 | 适用场景 |
|---|---|---|---|---|---|
Docker | 中 | 快(<1s) | 低 | 高 | 轻量级隔离需求 |
KVM | 高 | 慢(数十秒) | 高 | 中 | 高安全隔离需求 |
LXC | 中 | 快(<1s) | 低 | 中 | 轻量级隔离需求 |
Firejail | 中 | 快(<1s) | 低 | 中 | 单个应用隔离 |
gVisor | 高 | 中(~1s) | 中 | 中 | 高安全容器隔离 |
MCP 混合沙箱 | 中高 | 快(<1s) | 低 | 高 | MCP v2.0 框架 |
4.2 白名单机制对比
白名单机制 | 灵活性 | 安全性 | 维护成本 | 适用场景 |
|---|---|---|---|---|
静态白名单 | 低 | 高 | 高 | 需求稳定系统 |
动态白名单 | 高 | 中 | 中 | 需求动态系统 |
基于签名的白名单 | 中 | 高 | 中 | 可执行文件验证 |
基于行为的白名单 | 高 | 中 | 低 | 行为异常检测 |
MCP 智能白名单 | 高 | 中高 | 低 | MCP v2.0 框架 |
4.3 沙箱逃逸检测技术对比
检测技术 | 检测准确率 | 性能开销 | 误报率 | 适用场景 |
|---|---|---|---|---|
基于规则的检测 | 中 | 低 | 中 | 已知逃逸模式 |
基于机器学习的检测 | 高 | 中 | 低 | 未知逃逸模式 |
基于系统调用监控的检测 | 高 | 高 | 低 | 细粒度逃逸检测 |
基于硬件辅助的检测 | 高 | 低 | 低 | 高安全需求 |
MCP 混合检测 | 高 | 中 | 低 | MCP v2.0 框架 |
五、实际工程意义、潜在风险与局限性分析
5.1 实际工程意义
- 提高 MCP 系统的安全性:通过白名单和沙箱机制,防止恶意工具注入和执行,隔离工具执行环境,防止沙箱逃逸。
- 满足合规性要求:白名单和沙箱机制能够满足 GDPR、CCPA 等合规性要求,提供完整的审计日志。
- 提高系统的可靠性:通过限制工具的权限和资源访问范围,防止工具滥用资源,提高系统的可靠性。
- 降低安全运维成本:自动化的白名单管理和沙箱管理,减少人工干预,降低安全运维成本。
- 支持快速部署和测试:轻量级沙箱技术支持快速的沙箱创建和销毁,便于工具的测试和部署。
5.2 潜在风险
- 白名单误判:白名单可能误判合法工具,导致正常工具无法执行。
- 沙箱逃逸:尽管采取了多层隔离措施,仍有可能被攻击者突破沙箱限制。
- 性能开销:沙箱创建和销毁、逃逸检测等都会带来一定的性能开销。
- 管理复杂性:白名单和沙箱配置的管理可能变得复杂,需要专业的安全知识。
- 资源耗尽:大量沙箱的创建和运行可能导致系统资源耗尽。
5.3 局限性
- 沙箱隔离强度有限:容器沙箱的隔离强度不如硬件虚拟化,仍存在逃逸风险。
- 动态白名单的安全性挑战:动态调整白名单可能引入新的安全漏洞。
- 沙箱镜像的安全性:沙箱镜像本身可能存在安全漏洞,需要定期更新和扫描。
- 网络隔离的复杂性:实现沙箱之间的网络隔离可能变得复杂,尤其是在复杂网络环境中。
- 跨平台兼容性:不同平台上的沙箱技术可能存在差异,影响跨平台部署。
5.4 风险缓解策略
风险类型 | 缓解策略 |
|---|---|
白名单误判 | 1. 建立白名单审核流程2. 实现白名单智能学习3. 提供白名单测试环境4. 建立白名单回滚机制 |
沙箱逃逸 | 1. 采用多层沙箱隔离架构2. 实现沙箱逃逸检测与响应系统3. 定期更新沙箱镜像4. 限制沙箱资源访问范围 |
性能开销 | 1. 优化沙箱创建和销毁流程2. 采用轻量级沙箱技术3. 实现沙箱复用机制4. 对高频使用的工具预创建沙箱 |
管理复杂性 | 1. 提供可视化管理界面2. 实现自动化配置管理3. 建立标准化配置模板4. 提供培训和文档支持 |
资源耗尽 | 1. 对沙箱资源进行严格限制2. 实现沙箱自动清理机制3. 建立资源监控和告警系统4. 采用弹性伸缩机制 |
六、未来趋势展望与个人前瞻性预测
6.1 技术发展趋势
- AI 驱动的白名单与沙箱管理:利用 AI 技术自动学习和优化白名单配置,预测和防止沙箱逃逸。
- 硬件辅助的沙箱技术:结合硬件虚拟化技术(如 Intel SGX、AMD SEV),提供更强的沙箱隔离能力。
- 轻量级虚拟机技术:如 Firecracker、Cloud Hypervisor 等轻量级虚拟机技术,结合了容器的灵活性和虚拟机的隔离性。
- 分布式沙箱管理:实现分布式沙箱管理,支持大规模 MCP 系统的沙箱部署和管理。
- 沙箱即服务(SaaS):提供云端沙箱服务,便于 MCP 系统快速集成和使用。
6.2 应用场景扩展
- 边缘计算 MCP 沙箱:支持边缘设备上的 MCP 沙箱隔离,满足边缘计算场景的安全需求。
- IoT 设备 MCP 沙箱:为 IoT 设备提供轻量级沙箱隔离,防止恶意工具攻击 IoT 设备。
- 跨组织 MCP 沙箱:支持跨组织的 MCP 沙箱共享和管理,促进生态合作。
- 量子安全沙箱:基于量子密码学的沙箱技术,应对量子计算威胁。
6.3 标准与生态发展
- MCP 沙箱标准制定:制定统一的 MCP 沙箱标准,促进不同沙箱技术的互操作性。
- 开源沙箱项目发展:推动开源 MCP 沙箱项目的发展,降低使用门槛。
- 沙箱安全认证体系:建立沙箱安全认证体系,提高沙箱技术的可信度。
- 行业协作与共享:促进不同行业之间的沙箱技术和经验共享,共同应对安全挑战。
6.4 个人前瞻性预测
- 到 2027 年:80% 的 MCP 系统将采用动态白名单机制,减少人工干预。
- 到 2028 年:硬件辅助的沙箱技术将在高安全要求的 MCP 系统中得到广泛应用。
- 到 2029 年:AI 驱动的沙箱逃逸检测将成为 MCP 系统的标配。
- 到 2030 年:分布式沙箱管理将支持百万级 MCP 沙箱的部署和管理。
- 未来 5 年:MCP 白名单与沙箱机制将成为 AI 工具生态安全的核心基础设施。
参考链接:
附录(Appendix):
附录 A:MCP 白名单与沙箱系统部署指南
环境要求
- Python 3.8+
- Docker 20.10+(用于沙箱)
- Redis 6.0+(用于白名单缓存)
- MongoDB 4.4+(用于白名单存储)
安装步骤
# 安装依赖
pip install mcp-whitelist-sandbox
# 配置白名单与沙箱系统
cp config.example.yaml config.yaml
# 编辑配置文件
vim config.yaml
# 启动白名单管理服务
mcp-whitelist-service --config config.yaml
# 启动沙箱管理服务
mcp-sandbox-service --config config.yaml
# 启动逃逸检测服务
mcp-escape-detection-service --config config.yamlAPI 文档
- 白名单管理 API:http://localhost:8003/docs
- 沙箱管理 API:http://localhost:8004/docs
- 逃逸检测 API:http://localhost:8005/docs
附录 B:MCP 白名单与沙箱机制最佳实践
- 白名单管理最佳实践
- 遵循最小权限原则,只允许必要的工具
- 定期审核和更新白名单
- 实现白名单变更的审计日志
- 建立白名单回滚机制
- 沙箱管理最佳实践
- 使用官方或经过验证的沙箱镜像
- 定期更新沙箱镜像,修补安全漏洞
- 对沙箱资源进行严格限制
- 实现沙箱自动清理机制
- 监控沙箱的资源使用和行为
- 安全最佳实践
- 采用多层安全防御策略
- 实现沙箱逃逸检测与响应
- 定期进行安全审计和渗透测试
- 建立安全事件应急响应机制
- 提供安全培训和文档支持
附录 C:常见问题与解决方案
- 白名单误判导致工具无法执行
- 检查白名单配置,确保工具名称和版本正确
- 临时禁用白名单,测试工具是否可以正常执行
- 调整白名单规则,添加例外情况
- 沙箱启动失败
- 检查 Docker 服务是否正常运行
- 检查沙箱镜像是否存在
- 检查资源限制是否合理
- 查看 Docker 日志,分析失败原因
- 沙箱逃逸检测误报
- 调整逃逸检测规则的阈值
- 分析误报原因,优化检测算法
- 添加例外规则,排除正常行为
- 沙箱性能问题
- 优化沙箱配置,减少资源限制
- 实现沙箱复用机制
- 对高频使用的工具预创建沙箱
- 考虑使用性能更好的沙箱技术
- 白名单与沙箱系统集成问题
- 检查 API 配置是否正确
- 查看系统日志,分析集成错误
- 确保各组件版本兼容
- 参考官方文档和示例代码
关键词: MCP v2.0, 白名单机制, 沙箱隔离, 动态白名单, 多层沙箱架构, 沙箱逃逸检测, Docker
本文参与 腾讯云自媒体同步曝光计划,分享自作者个人站点/博客。
原始发表:2026-01-10,如有侵权请联系 cloudcommunity@tencent.com 删除
评论
登录后参与评论
推荐阅读
目录


