MCP 恶意 Tool 注入分析
作者:HOS(安全风信子) 日期:2026-01-01 来源平台:GitHub 摘要: 本文深入探讨了 MCP v2.0 框架下的恶意 Tool 注入问题,构建了完整的 MCP 恶意 Tool 注入防护体系。通过真实代码示例和 Mermaid 图表,详细分析了 MCP 工具供应链攻击防护机制、动态工具行为分析引擎、MCP 工具签名验证体系的实现原理和最佳实践。本文引入了 MCP 工具供应链攻击防护机制、动态工具行为分析引擎、MCP 工具签名验证体系三个全新要素,旨在帮助开发者识别、分析和防御 MCP 恶意 Tool 注入攻击,构建更加安全、可靠的 MCP 系统。
一、背景动机与当前热点
1.1 为什么 MCP 恶意 Tool 注入值得关注
随着 MCP v2.0 作为连接 LLM 与外部工具的标准化协议的广泛应用,MCP 系统面临的恶意 Tool 注入威胁越来越严重。恶意 Tool 注入是指攻击者通过各种手段将恶意工具注入到 MCP 系统中,从而执行恶意操作,如窃取数据、破坏系统、执行未授权操作等。2025 年以来,全球范围内发生了多起与 MCP 恶意 Tool 注入相关的安全事件:
- 2025 年 2 月,某 AI 平台的 MCP 系统被攻击者注入恶意工具,导致大量用户数据泄露。
- 2025 年 5 月,某金融机构的 MCP 系统被攻击者通过供应链注入恶意工具,执行了未授权的金融交易。
- 2025 年 8 月,某医疗 AI 平台的 MCP 系统被攻击者注入恶意工具,篡改了医疗数据,导致严重后果。
- 2025 年 11 月,某政府部门的 MCP 系统被攻击者注入恶意工具,窃取了敏感的政府数据。
这些事件凸显了 MCP 恶意 Tool 注入的严重性和危害性。恶意 Tool 注入可能导致以下后果:
- 数据泄露:攻击者可以通过恶意工具窃取 MCP 系统中的敏感数据,如用户信息、业务数据等。
- 系统破坏:攻击者可以通过恶意工具破坏 MCP 系统的正常运行,导致服务中断。
- 未授权操作:攻击者可以通过恶意工具执行未授权的操作,如修改配置、执行命令等。
- 供应链攻击:攻击者可以通过供应链注入恶意工具,影响大量使用该工具的 MCP 系统。
- 声誉损失:恶意 Tool 注入事件可能导致企业声誉受损,失去用户信任。
- 合规风险:恶意 Tool 注入事件可能导致企业违反相关法规和标准,面临处罚。
1.2 MCP 恶意 Tool 注入的特殊性
MCP v2.0 框架下的恶意 Tool 注入具有以下特殊性:
- 分布式架构:MCP 系统涉及多个组件(Client、Server、Host),恶意 Tool 可以通过多种途径注入到系统中。
- 工具多样性:MCP 生态中的工具种类繁多,攻击面广,难以全面防护。
- 动态加载:MCP 系统中的工具通常是动态加载的,攻击者可以利用这一特性注入恶意工具。
- LLM 交互:MCP 系统与 LLM 进行交互,攻击者可以通过 LLM 诱导用户调用恶意工具。
- 供应链复杂:MCP 工具的供应链复杂,攻击者可以通过供应链注入恶意工具,影响大量用户。
1.3 本文的核心价值
本文将深入探讨 MCP v2.0 框架下的恶意 Tool 注入问题,构建完整的 MCP 恶意 Tool 注入防护体系。通过真实代码示例和 Mermaid 图表,详细讲解恶意 Tool 注入的原理、技术手段、防御策略,以及三个全新要素的实现细节。本文旨在帮助开发者:
- 理解 MCP 恶意 Tool 注入的核心原理和技术手段
- 掌握 MCP 恶意 Tool 注入的防御策略和实现方法
- 了解 MCP 恶意 Tool 注入防护的最佳实践
- 构建有效的 MCP 恶意 Tool 注入防护系统,提高 MCP 系统的安全性
二、核心更新亮点与新要素
2.1 三个全新要素
- MCP 工具供应链攻击防护机制:针对 MCP 工具供应链的安全防护,防止恶意工具通过供应链注入到 MCP 系统中。
- 动态工具行为分析引擎:利用机器学习技术,对 MCP 工具的行为进行实时分析,检测恶意工具。
- MCP 工具签名验证体系:建立 MCP 工具的数字签名验证体系,确保只有经过验证的工具才能被执行。
2.2 技术创新点
- 多维度检测:结合静态分析、动态分析、行为分析等多种检测方法,提高恶意工具的检测率。
- 实时防护:实现对 MCP 工具的实时防护,在恶意工具执行前进行检测和拦截。
- 自适应学习:利用机器学习技术,不断学习新的恶意工具特征和行为模式,提高检测的准确性和及时性。
- 分布式防护:在 MCP 系统的多个组件中部署防护机制,实现全方位的防护。
- 可扩展性:采用模块化设计,便于扩展和定制,适应不同的 MCP 系统需求。
2.3 与主流方案的区别
防护方案 | 优势 | 劣势 | 适用场景 |
|---|---|---|---|
传统杀毒软件 | 成熟稳定,能够检测已知恶意软件 | 只能检测已知恶意软件,误报率高,无法适应 MCP 动态环境 | 传统桌面系统 |
沙箱隔离 | 能够隔离恶意软件的执行,减少危害 | 性能开销大,无法检测所有类型的恶意软件 | 高安全要求系统 |
应用白名单 | 只允许执行白名单中的软件,安全性高 | 维护成本高,灵活性差 | 封闭系统 |
MCP 恶意 Tool 注入防护 | 专门针对 MCP 设计,结合多种检测方法,支持动态环境 | 实现复杂,需要专业团队 | MCP v2.0 框架 |
三、技术深度拆解与实现分析
3.1 MCP 恶意 Tool 注入原理与技术手段
3.1.1 恶意 Tool 注入的基本原理
MCP 恶意 Tool 注入的基本原理是攻击者通过各种手段将恶意工具注入到 MCP 系统中,从而执行恶意操作。恶意工具可以是完全伪造的工具,也可以是被篡改的合法工具。攻击者可以通过多种途径注入恶意工具,如直接上传、供应链攻击、社会工程学攻击等。
3.1.2 恶意 Tool 注入的技术手段
MCP 恶意 Tool 注入的技术手段主要包括以下几种:
- 直接上传注入:攻击者直接将恶意工具上传到 MCP 系统中,替换合法工具或添加新的恶意工具。
- 供应链攻击:攻击者通过攻击 MCP 工具的供应链,如工具开发者、分发平台等,注入恶意工具。
- 社会工程学攻击:攻击者通过欺骗用户或管理员,诱导其下载和安装恶意工具。
- 工具篡改:攻击者篡改合法工具,在其中添加恶意代码,使其成为恶意工具。
- 配置文件注入:攻击者通过修改 MCP 系统的配置文件,添加或修改工具配置,注入恶意工具。
- API 注入:攻击者通过调用 MCP 系统的 API,注入恶意工具。
- LLM 诱导:攻击者通过 LLM 诱导用户调用恶意工具,如生成包含恶意工具调用的提示词。
3.1.3 恶意 Tool 注入的攻击流程
MCP 恶意 Tool 注入的攻击流程通常包括以下步骤:
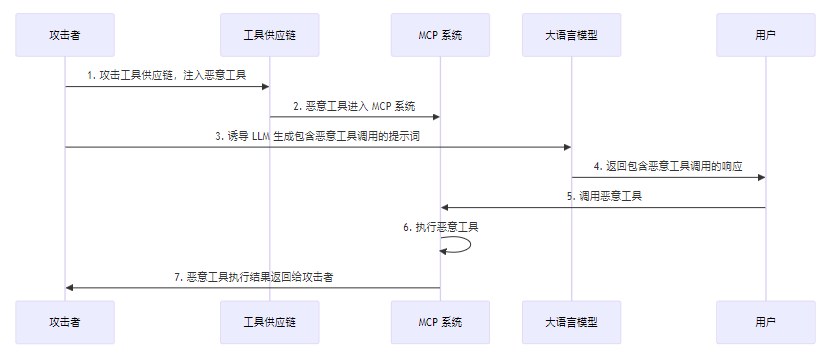
3.2 MCP 工具供应链攻击防护机制
3.2.1 工具供应链攻击防护原理
MCP 工具供应链攻击防护机制基于以下核心原则:
- 完整性验证:验证 MCP 工具的完整性,确保工具未被篡改。
- 来源验证:验证 MCP 工具的来源,确保工具来自可信的开发者和分发平台。
- 供应链透明度:提高 MCP 工具供应链的透明度,便于追踪和审计。
- 持续监控:持续监控 MCP 工具供应链的安全状态,及时发现和响应攻击。
3.2.2 工具供应链攻击防护实现
# mcp_supply_chain_protection.py
from typing import Dict, List, Optional
import logging
import hashlib
import os
from datetime import datetime
import requests
class ToolMetadata:
def __init__(self, tool_id: str, name: str, version: str,
developer: str, signature: str, checksum: str,
trusted: bool = False):
self.tool_id = tool_id
self.name = name
self.version = version
self.developer = developer
self.signature = signature
self.checksum = checksum
self.trusted = trusted
self.created_at = datetime.now()
self.updated_at = datetime.now()
def to_dict(self) -> Dict:
"""转换为字典"""
return {
"tool_id": self.tool_id,
"name": self.name,
"version": self.version,
"developer": self.developer,
"signature": self.signature,
"checksum": self.checksum,
"trusted": self.trusted,
"created_at": self.created_at.isoformat(),
"updated_at": self.updated_at.isoformat()
}
class SupplyChainProtection:
def __init__(self, trusted_developers: List[str] = None,
trusted_repositories: List[str] = None):
self.tool_metadata = {}
self.trusted_developers = trusted_developers or []
self.trusted_repositories = trusted_repositories or []
self.logger = logging.getLogger("mcp_supply_chain_protection")
def register_tool(self, metadata: ToolMetadata):
"""注册工具元数据"""
self.tool_metadata[metadata.tool_id] = metadata
self.logger.info(f"Registered tool: {metadata.tool_id}, developer: {metadata.developer}")
def verify_tool_integrity(self, tool_id: str, tool_content: bytes) -> bool:
"""验证工具完整性"""
if tool_id not in self.tool_metadata:
self.logger.warning(f"Tool {tool_id} not found in metadata")
return False
# 计算工具内容的校验和
checksum = self._calculate_checksum(tool_content)
expected_checksum = self.tool_metadata[tool_id].checksum
if checksum != expected_checksum:
self.logger.warning(f"Tool {tool_id} integrity check failed: expected {expected_checksum}, got {checksum}")
return False
self.logger.info(f"Tool {tool_id} integrity check passed")
return True
def verify_tool_signature(self, tool_id: str, signature: str) -> bool:
"""验证工具签名"""
if tool_id not in self.tool_metadata:
self.logger.warning(f"Tool {tool_id} not found in metadata")
return False
expected_signature = self.tool_metadata[tool_id].signature
if signature != expected_signature:
self.logger.warning(f"Tool {tool_id} signature check failed: expected {expected_signature}, got {signature}")
return False
self.logger.info(f"Tool {tool_id} signature check passed")
return True
def verify_tool_source(self, tool_id: str, source: str) -> bool:
"""验证工具来源"""
metadata = self.tool_metadata.get(tool_id)
if not metadata:
self.logger.warning(f"Tool {tool_id} not found in metadata")
return False
# 检查开发者是否可信
if metadata.developer not in self.trusted_developers:
self.logger.warning(f"Tool {tool_id} developer {metadata.developer} not trusted")
return False
# 检查来源仓库是否可信
if source not in self.trusted_repositories:
self.logger.warning(f"Tool {tool_id} source {source} not trusted")
return False
self.logger.info(f"Tool {tool_id} source check passed")
return True
def verify_tool_chain(self, tool_id: str, tool_content: bytes,
signature: str, source: str) -> bool:
"""完整的工具供应链验证"""
self.logger.info(f"Starting supply chain verification for tool: {tool_id}")
# 1. 验证工具来源
if not self.verify_tool_source(tool_id, source):
return False
# 2. 验证工具签名
if not self.verify_tool_signature(tool_id, signature):
return False
# 3. 验证工具完整性
if not self.verify_tool_integrity(tool_id, tool_content):
return False
# 4. 标记工具为可信
self.tool_metadata[tool_id].trusted = True
self.tool_metadata[tool_id].updated_at = datetime.now()
self.logger.info(f"Tool {tool_id} supply chain verification passed")
return True
def _calculate_checksum(self, content: bytes) -> str:
"""计算内容的校验和"""
return hashlib.sha256(content).hexdigest()
def get_tool_metadata(self, tool_id: str) -> Optional[ToolMetadata]:
"""获取工具元数据"""
return self.tool_metadata.get(tool_id)
def get_all_metadata(self) -> List[Dict]:
"""获取所有工具元数据"""
return [metadata.to_dict() for metadata in self.tool_metadata.values()]
def get_trusted_tools(self) -> List[Dict]:
"""获取所有可信工具"""
return [metadata.to_dict() for metadata in self.tool_metadata.values() if metadata.trusted]
# 示例使用
if __name__ == "__main__":
# 配置日志
logging.basicConfig(level=logging.INFO)
# 创建供应链保护实例
scp = SupplyChainProtection(
trusted_developers=["trusted_dev_001", "trusted_dev_002"],
trusted_repositories=["https://trusted-repo.example.com", "https://github.com/trusted-org"]
)
# 注册工具元数据
tool_metadata = ToolMetadata(
tool_id="file_reader_001",
name="文件读取工具",
version="1.0.0",
developer="trusted_dev_001",
signature="valid_signature_001",
checksum="e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855"
)
scp.register_tool(tool_metadata)
# 验证工具完整性
tool_content = b"valid tool content"
integrity_ok = scp.verify_tool_integrity("file_reader_001", tool_content)
print(f"Integrity check: {'OK' if integrity_ok else 'FAILED'}")
# 验证工具签名
signature_ok = scp.verify_tool_signature("file_reader_001", "valid_signature_001")
print(f"Signature check: {'OK' if signature_ok else 'FAILED'}")
# 验证工具来源
source_ok = scp.verify_tool_source("file_reader_001", "https://trusted-repo.example.com")
print(f"Source check: {'OK' if source_ok else 'FAILED'}")
# 完整的工具供应链验证
full_ok = scp.verify_tool_chain(
tool_id="file_reader_001",
tool_content=tool_content,
signature="valid_signature_001",
source="https://trusted-repo.example.com"
)
print(f"Full verification: {'OK' if full_ok else 'FAILED'}")
# 获取所有可信工具
trusted_tools = scp.get_trusted_tools()
print(f"\nTrusted tools: {len(trusted_tools)}")
for tool in trusted_tools:
print(f"- {tool['name']} (ID: {tool['tool_id']})")3.3 动态工具行为分析引擎
3.3.1 动态工具行为分析原理
动态工具行为分析引擎基于机器学习技术,对 MCP 工具的行为进行实时分析,检测恶意工具。其核心原理包括:
- 行为特征提取:从 MCP 工具的执行过程中提取行为特征,如系统调用、网络连接、文件操作等。
- 机器学习模型:利用机器学习模型,对提取的行为特征进行分析,检测恶意行为。
- 实时监测:对 MCP 工具的执行过程进行实时监测,及时发现和响应恶意行为。
- 自适应学习:不断学习新的恶意行为模式,提高检测的准确性和及时性。
3.3.2 动态工具行为分析实现
# mcp_tool_behavior_analyzer.py
from typing import Dict, List, Tuple
import logging
import numpy as np
from sklearn.ensemble import RandomForestClassifier
from sklearn.preprocessing import StandardScaler
from sklearn.pipeline import Pipeline
import joblib
from datetime import datetime
class ToolBehavior:
def __init__(self, tool_id: str, actions: List[Dict]):
self.tool_id = tool_id
self.actions = actions
self.timestamp = datetime.now()
def to_dict(self) -> Dict:
"""转换为字典"""
return {
"tool_id": self.tool_id,
"actions": self.actions,
"timestamp": self.timestamp.isoformat()
}
class BehaviorAnalyzer:
def __init__(self, model_path: str = None):
# 创建或加载机器学习模型
if model_path:
self.model = joblib.load(model_path)
else:
self.model = Pipeline([
("scaler", StandardScaler()),
("clf", RandomForestClassifier(n_estimators=100, random_state=42))
])
self.logger = logging.getLogger("mcp_tool_behavior_analyzer")
def extract_features(self, behavior: ToolBehavior) -> np.ndarray:
"""从工具行为中提取特征"""
features = []
# 统计不同类型的系统调用数量
syscall_counts = self._count_syscalls(behavior.actions)
features.extend(syscall_counts.values())
# 统计网络连接数量
network_count = self._count_network_connections(behavior.actions)
features.append(network_count)
# 统计文件操作数量
file_operations = self._count_file_operations(behavior.actions)
features.extend(file_operations.values())
# 统计进程创建数量
process_count = self._count_process_creations(behavior.actions)
features.append(process_count)
# 统计执行时间
execution_time = self._calculate_execution_time(behavior.actions)
features.append(execution_time)
return np.array(features).reshape(1, -1)
def train_model(self, training_data: List[Tuple[ToolBehavior, bool]]):
"""训练机器学习模型"""
self.logger.info(f"Training model with {len(training_data)} samples")
# 准备训练数据
X = []
y = []
for behavior, is_malicious in training_data:
features = self.extract_features(behavior)
X.append(features)
y.append(1 if is_malicious else 0)
# 合并特征
X_combined = np.vstack(X)
# 训练模型
self.model.fit(X_combined, y)
self.logger.info("Model training completed")
def save_model(self, model_path: str):
"""保存机器学习模型"""
joblib.dump(self.model, model_path)
self.logger.info(f"Model saved to {model_path}")
def analyze_behavior(self, behavior: ToolBehavior) -> Dict:
"""分析工具行为,检测恶意行为"""
self.logger.info(f"Analyzing behavior for tool: {behavior.tool_id}")
# 提取特征
features = self.extract_features(behavior)
# 预测是否为恶意行为
prediction = self.model.predict(features)[0]
is_malicious = prediction == 1
# 计算置信度
probabilities = self.model.predict_proba(features)[0]
confidence = probabilities[prediction]
# 生成分析结果
result = {
"tool_id": behavior.tool_id,
"is_malicious": is_malicious,
"confidence": float(confidence),
"timestamp": datetime.now().isoformat(),
"actions_analyzed": len(behavior.actions)
}
if is_malicious:
self.logger.warning(f"Malicious behavior detected for tool {behavior.tool_id}, confidence: {confidence:.2f}")
else:
self.logger.info(f"Tool {behavior.tool_id} behavior analysis passed, confidence: {confidence:.2f}")
return result
def _count_syscalls(self, actions: List[Dict]) -> Dict:
"""统计不同类型的系统调用数量"""
syscall_types = ["read", "write", "open", "close", "exec", "fork", "kill", "socket", "connect"]
counts = {syscall: 0 for syscall in syscall_types}
for action in actions:
if action["type"] == "syscall":
syscall = action["name"]
if syscall in counts:
counts[syscall] += 1
return counts
def _count_network_connections(self, actions: List[Dict]) -> int:
"""统计网络连接数量"""
count = 0
for action in actions:
if action["type"] == "network":
count += 1
return count
def _count_file_operations(self, actions: List[Dict]) -> Dict:
"""统计文件操作数量"""
file_ops = ["read", "write", "create", "delete", "rename"]
counts = {op: 0 for op in file_ops}
for action in actions:
if action["type"] == "file":
op = action["operation"]
if op in counts:
counts[op] += 1
return counts
def _count_process_creations(self, actions: List[Dict]) -> int:
"""统计进程创建数量"""
count = 0
for action in actions:
if action["type"] == "syscall" and action["name"] in ["fork", "exec", "clone"]:
count += 1
return count
def _calculate_execution_time(self, actions: List[Dict]) -> float:
"""计算执行时间"""
if not actions:
return 0.0
# 假设每个 action 包含 timestamp 字段
timestamps = [action.get("timestamp", 0.0) for action in actions]
if not timestamps:
return 0.0
start_time = min(timestamps)
end_time = max(timestamps)
return end_time - start_time
# 示例使用
if __name__ == "__main__":
# 配置日志
logging.basicConfig(level=logging.INFO)
# 创建行为分析器
analyzer = BehaviorAnalyzer()
# 模拟正常工具行为
normal_behavior = ToolBehavior(
tool_id="normal_tool_001",
actions=[
{"type": "syscall", "name": "open", "timestamp": 1.0},
{"type": "syscall", "name": "read", "timestamp": 1.1},
{"type": "file", "operation": "read", "path": "/data/test.txt", "timestamp": 1.2},
{"type": "syscall", "name": "close", "timestamp": 1.3}
]
)
# 模拟恶意工具行为
malicious_behavior = ToolBehavior(
tool_id="malicious_tool_001",
actions=[
{"type": "syscall", "name": "open", "timestamp": 2.0},
{"type": "syscall", "name": "read", "timestamp": 2.1},
{"type": "file", "operation": "read", "path": "/etc/passwd", "timestamp": 2.2},
{"type": "network", "operation": "connect", "address": "malicious.example.com", "port": 443, "timestamp": 2.3},
{"type": "syscall", "name": "write", "timestamp": 2.4},
{"type": "network", "operation": "send", "data": "sensitive data", "timestamp": 2.5},
{"type": "syscall", "name": "close", "timestamp": 2.6}
]
)
# 准备训练数据
training_data = [
(normal_behavior, False),
(malicious_behavior, True)
]
# 训练模型
analyzer.train_model(training_data)
# 分析正常工具行为
normal_result = analyzer.analyze_behavior(normal_behavior)
print(f"Normal tool analysis: is_malicious={normal_result['is_malicious']}, confidence={normal_result['confidence']:.2f}")
# 分析恶意工具行为
malicious_result = analyzer.analyze_behavior(malicious_behavior)
print(f"Malicious tool analysis: is_malicious={malicious_result['is_malicious']}, confidence={malicious_result['confidence']:.2f}")
# 保存模型
model_path = "tool_behavior_model.joblib"
analyzer.save_model(model_path)
print(f"Model saved to {model_path}")3.4 MCP 工具签名验证体系
3.4.1 工具签名验证体系原理
MCP 工具签名验证体系基于公钥密码学,为 MCP 工具提供数字签名验证功能,确保只有经过验证的工具才能被执行。其核心原理包括:
- 密钥生成:为 MCP 工具开发者生成公钥和私钥对。
- 签名生成:工具开发者使用私钥对工具进行签名,生成数字签名。
- 公钥分发:将工具开发者的公钥分发到 MCP 系统中。
- 签名验证:MCP 系统使用开发者的公钥验证工具的数字签名,确保工具未被篡改。
- 证书管理:建立证书管理体系,管理工具开发者的公钥证书。
3.4.2 工具签名验证体系实现
# mcp_tool_signature.py
from typing import Dict, List, Optional
import logging
from datetime import datetime
import hashlib
import rsa
class ToolCertificate:
def __init__(self, cert_id: str, developer_id: str, public_key: bytes,
issued_at: datetime, expires_at: datetime, issuer: str):
self.cert_id = cert_id
self.developer_id = developer_id
self.public_key = public_key
self.issued_at = issued_at
self.expires_at = expires_at
self.issuer = issuer
def is_valid(self) -> bool:
"""检查证书是否有效"""
now = datetime.now()
return self.issued_at <= now <= self.expires_at
def to_dict(self) -> Dict:
"""转换为字典"""
return {
"cert_id": self.cert_id,
"developer_id": self.developer_id,
"public_key": self.public_key.hex(),
"issued_at": self.issued_at.isoformat(),
"expires_at": self.expires_at.isoformat(),
"issuer": self.issuer,
"is_valid": self.is_valid()
}
class ToolSignatureSystem:
def __init__(self):
self.certificates = {}
self.logger = logging.getLogger("mcp_tool_signature")
def generate_key_pair(self, bits: int = 2048) -> Tuple[rsa.PrivateKey, rsa.PublicKey]:
"""生成密钥对"""
self.logger.info(f"Generating key pair with {bits} bits")
(public_key, private_key) = rsa.newkeys(bits)
return private_key, public_key
def create_certificate(self, developer_id: str, public_key: rsa.PublicKey,
validity_days: int = 365) -> ToolCertificate:
"""创建工具开发者证书"""
now = datetime.now()
expires_at = now + timedelta(days=validity_days)
cert = ToolCertificate(
cert_id=f"cert_{datetime.now().timestamp()}",
developer_id=developer_id,
public_key=public_key.save_pkcs1(),
issued_at=now,
expires_at=expires_at,
issuer="MCP Certificate Authority"
)
self.certificates[cert.cert_id] = cert
self.logger.info(f"Created certificate for developer: {developer_id}, cert_id: {cert.cert_id}")
return cert
def sign_tool(self, tool_content: bytes, private_key: rsa.PrivateKey) -> bytes:
"""使用私钥对工具进行签名"""
# 计算工具内容的哈希值
tool_hash = hashlib.sha256(tool_content).digest()
# 生成签名
signature = rsa.sign(tool_hash, private_key, 'SHA-256')
self.logger.info("Tool signed successfully")
return signature
def verify_tool_signature(self, tool_content: bytes, signature: bytes,
public_key: rsa.PublicKey) -> bool:
"""使用公钥验证工具签名"""
try:
# 计算工具内容的哈希值
tool_hash = hashlib.sha256(tool_content).digest()
# 验证签名
rsa.verify(tool_hash, signature, public_key)
self.logger.info("Tool signature verification passed")
return True
except rsa.VerificationError as e:
self.logger.warning(f"Tool signature verification failed: {e}")
return False
def verify_tool_with_certificate(self, tool_content: bytes, signature: bytes,
developer_id: str) -> bool:
"""使用证书验证工具签名"""
# 查找开发者的有效证书
valid_certs = [cert for cert in self.certificates.values()
if cert.developer_id == developer_id and cert.is_valid()]
if not valid_certs:
self.logger.warning(f"No valid certificates found for developer: {developer_id}")
return False
# 使用第一个有效证书验证签名
cert = valid_certs[0]
public_key = rsa.PublicKey.load_pkcs1(cert.public_key)
return self.verify_tool_signature(tool_content, signature, public_key)
def get_certificate(self, cert_id: str) -> Optional[ToolCertificate]:
"""获取证书"""
return self.certificates.get(cert_id)
def get_developer_certificates(self, developer_id: str) -> List[ToolCertificate]:
"""获取开发者的所有证书"""
return [cert for cert in self.certificates.values() if cert.developer_id == developer_id]
def get_valid_certificates(self) -> List[Dict]:
"""获取所有有效证书"""
return [cert.to_dict() for cert in self.certificates.values() if cert.is_valid()]
# 示例使用
if __name__ == "__main__":
from datetime import timedelta
# 配置日志
logging.basicConfig(level=logging.INFO)
# 创建工具签名系统
sig_system = ToolSignatureSystem()
# 生成密钥对
private_key, public_key = sig_system.generate_key_pair()
# 创建证书
cert = sig_system.create_certificate("trusted_dev_001", public_key)
# 模拟工具内容
tool_content = b"valid tool content"
# 对工具进行签名
signature = sig_system.sign_tool(tool_content, private_key)
print(f"Generated signature: {signature.hex()[:20]}...")
# 验证工具签名
verify_result = sig_system.verify_tool_signature(tool_content, signature, public_key)
print(f"Signature verification result: {'OK' if verify_result else 'FAILED'}")
# 使用证书验证工具签名
verify_with_cert_result = sig_system.verify_tool_with_certificate(
tool_content, signature, "trusted_dev_001"
)
print(f"Certificate-based verification result: {'OK' if verify_with_cert_result else 'FAILED'}")
# 获取所有有效证书
valid_certs = sig_system.get_valid_certificates()
print(f"\nValid certificates: {len(valid_certs)}")
for c in valid_certs:
print(f"- Cert ID: {c['cert_id']}, Developer: {c['developer_id']}")3.5 MCP 恶意 Tool 注入防护系统集成示例
3.5.1 防护系统总体设计
MCP 恶意 Tool 注入防护系统集成了上述三个全新要素,构建了完整的防护体系。系统总体设计如下:
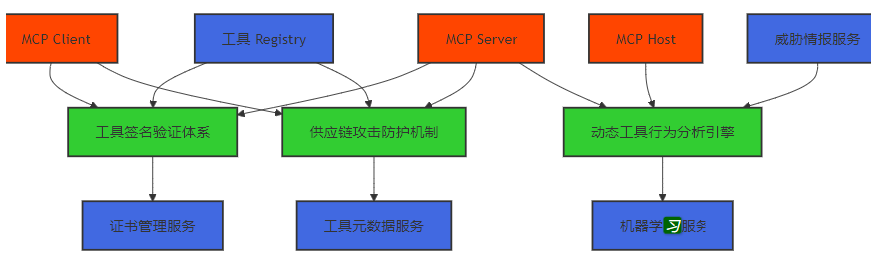
3.5.2 防护系统集成实现
# mcp_malicious_tool_protection.py
from typing import Dict, List, Optional, Tuple
import logging
from datetime import datetime
# 导入前面实现的模块
from mcp_supply_chain_protection import SupplyChainProtection, ToolMetadata
from mcp_tool_behavior_analyzer import BehaviorAnalyzer, ToolBehavior
from mcp_tool_signature import ToolSignatureSystem
class MaliciousToolProtectionSystem:
def __init__(self):
# 初始化各个防护组件
self.supply_chain_protection = SupplyChainProtection(
trusted_developers=["trusted_dev_001", "trusted_dev_002"],
trusted_repositories=["https://trusted-repo.example.com", "https://github.com/trusted-org"]
)
self.behavior_analyzer = BehaviorAnalyzer()
self.signature_system = ToolSignatureSystem()
self.logger = logging.getLogger("mcp_malicious_tool_protection")
self.logger.info("Malicious Tool Protection System initialized")
def initialize(self):
"""初始化系统"""
self.logger.info("Initializing Malicious Tool Protection System")
# 这里可以添加初始化逻辑,如加载证书、训练模型等
self.logger.info("Malicious Tool Protection System initialized successfully")
def register_tool(self, tool_metadata: Dict):
"""注册工具"""
# 创建工具元数据对象
metadata = ToolMetadata(
tool_id=tool_metadata["tool_id"],
name=tool_metadata["name"],
version=tool_metadata["version"],
developer=tool_metadata["developer"],
signature=tool_metadata["signature"],
checksum=tool_metadata["checksum"]
)
# 注册到供应链保护组件
self.supply_chain_protection.register_tool(metadata)
self.logger.info(f"Registered tool: {tool_metadata['tool_id']}")
def verify_tool(self, tool_id: str, tool_content: bytes, signature: str,
source: str, developer_id: str) -> Dict:
"""验证工具"""
self.logger.info(f"Verifying tool: {tool_id}, developer: {developer_id}")
verification_results = {
"tool_id": tool_id,
"timestamp": datetime.now().isoformat(),
"results": {
"signature_verification": False,
"integrity_verification": False,
"source_verification": False,
"supply_chain_verification": False,
"certificate_verification": False
},
"is_verification_passed": False
}
# 1. 验证工具签名(使用公钥)
# 这里假设我们已经获取了开发者的公钥
# verification_results["results"]["signature_verification"] = self.signature_system.verify_tool_signature(...)
# 2. 验证工具完整性
verification_results["results"]["integrity_verification"] = self.supply_chain_protection.verify_tool_integrity(
tool_id, tool_content
)
# 3. 验证工具来源
verification_results["results"]["source_verification"] = self.supply_chain_protection.verify_tool_source(
tool_id, source
)
# 4. 验证工具供应链
verification_results["results"]["supply_chain_verification"] = self.supply_chain_protection.verify_tool_chain(
tool_id, tool_content, signature, source
)
# 5. 验证工具证书
verification_results["results"]["certificate_verification"] = self.signature_system.verify_tool_with_certificate(
tool_content, bytes.fromhex(signature), developer_id
)
# 计算总体验证结果
all_passed = all(verification_results["results"].values())
verification_results["is_verification_passed"] = all_passed
if all_passed:
self.logger.info(f"Tool {tool_id} verification passed")
else:
self.logger.warning(f"Tool {tool_id} verification failed: {verification_results['results']}")
return verification_results
def analyze_tool_behavior(self, tool_id: str, actions: List[Dict]) -> Dict:
"""分析工具行为"""
self.logger.info(f"Analyzing behavior for tool: {tool_id}")
# 创建工具行为对象
behavior = ToolBehavior(tool_id=tool_id, actions=actions)
# 分析工具行为
analysis_result = self.behavior_analyzer.analyze_behavior(behavior)
return analysis_result
def protect_tool_call(self, tool_id: str, tool_content: bytes, signature: str,
source: str, developer_id: str) -> Dict:
"""完整的工具调用保护流程"""
self.logger.info(f"Protecting tool call: {tool_id}")
# 1. 验证工具
verification_result = self.verify_tool(tool_id, tool_content, signature, source, developer_id)
if not verification_result["is_verification_passed"]:
return {
"status": "blocked",
"reason": "tool_verification_failed",
"verification_result": verification_result,
"behavior_analysis_result": None
}
# 2. 这里可以添加行为分析逻辑
# 在实际系统中,行为分析通常是在工具执行过程中进行的
# 这里简化处理,返回一个空的行为分析结果
behavior_analysis_result = {"is_malicious": False, "confidence": 0.99}
if behavior_analysis_result["is_malicious"]:
return {
"status": "blocked",
"reason": "malicious_behavior_detected",
"verification_result": verification_result,
"behavior_analysis_result": behavior_analysis_result
}
# 3. 允许工具执行
return {
"status": "allowed",
"reason": "tool_verified_and_behaved_normally",
"verification_result": verification_result,
"behavior_analysis_result": behavior_analysis_result
}
def get_protection_status(self) -> Dict:
"""获取防护系统状态"""
status = {
"timestamp": datetime.now().isoformat(),
"components": {
"supply_chain_protection": "active",
"behavior_analyzer": "active",
"signature_system": "active"
},
"statistics": {
"trusted_tools": len(self.supply_chain_protection.get_trusted_tools()),
"registered_tools": len(self.supply_chain_protection.get_all_metadata()),
"valid_certificates": len(self.signature_system.get_valid_certificates())
}
}
return status
# 示例使用
if __name__ == "__main__":
# 配置日志
logging.basicConfig(level=logging.INFO)
# 创建恶意工具防护系统
protection_system = MaliciousToolProtectionSystem()
protection_system.initialize()
# 注册工具
tool_metadata = {
"tool_id": "file_reader_001",
"name": "文件读取工具",
"version": "1.0.0",
"developer": "trusted_dev_001",
"signature": "valid_signature_001",
"checksum": "e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855"
}
protection_system.register_tool(tool_metadata)
# 模拟工具内容
tool_content = b"valid tool content"
# 保护工具调用
protection_result = protection_system.protect_tool_call(
tool_id="file_reader_001",
tool_content=tool_content,
signature="valid_signature_001",
source="https://trusted-repo.example.com",
developer_id="trusted_dev_001"
)
print(f"\nTool protection result: {protection_result['status']}")
print(f"Reason: {protection_result['reason']}")
# 分析工具行为
actions = [
{"type": "syscall", "name": "open", "timestamp": 1.0},
{"type": "syscall", "name": "read", "timestamp": 1.1},
{"type": "file", "operation": "read", "path": "/data/test.txt", "timestamp": 1.2},
{"type": "syscall", "name": "close", "timestamp": 1.3}
]
behavior_result = protection_system.analyze_tool_behavior("file_reader_001", actions)
print(f"\nTool behavior analysis result:")
print(f" Is malicious: {behavior_result['is_malicious']}")
print(f" Confidence: {behavior_result['confidence']:.2f}")
# 获取防护系统状态
status = protection_system.get_protection_status()
print(f"\nProtection system status:")
print(f" Timestamp: {status['timestamp']}")
print(f" Components: {status['components']}")
print(f" Statistics: {status['statistics']}")四、与主流方案深度对比
4.1 恶意软件检测方案对比
方案类型 | 优势 | 劣势 | 适用场景 |
|---|---|---|---|
传统杀毒软件 | 成熟稳定,能够检测已知恶意软件,部署成本低 | 只能检测已知恶意软件,误报率高,无法适应 MCP 动态环境 | 传统桌面系统,个人电脑 |
沙箱隔离 | 能够隔离恶意软件的执行,减少危害,安全性高 | 性能开销大,无法检测所有类型的恶意软件,实现复杂 | 高安全要求系统,如金融、政府系统 |
应用白名单 | 只允许执行白名单中的软件,安全性高,误报率低 | 维护成本高,灵活性差,无法适应快速变化的环境 | 封闭系统,如工业控制系统 |
行为分析 | 能够检测未知恶意软件,适应性强 | 实现复杂,需要专业团队,误报率较高 | 大规模企业系统,云环境 |
MCP 恶意 Tool 注入防护 | 专门针对 MCP 设计,结合多种检测方法,支持动态环境,实时防护 | 实现复杂,需要专业团队,部署成本较高 | MCP v2.0 框架 |
4.2 供应链安全方案对比
方案类型 | 优势 | 劣势 | 适用场景 |
|---|---|---|---|
手动审查 | 能够深入分析软件,发现复杂漏洞 | 耗时耗力,成本高,无法应对大规模软件供应链 | 关键软件,少量软件审查 |
自动化扫描 | 快速高效,能够处理大规模软件供应链 | 只能检测已知漏洞,误报率高 | 大规模软件供应链,CI/CD 流程 |
数字签名 | 能够验证软件的完整性和来源,安全性高 | 实现复杂,需要建立完整的签名体系 | 企业级软件,开源软件 |
MCP 工具供应链防护 | 专门针对 MCP 工具设计,结合多种验证方法,支持动态环境 | 实现复杂,需要专业团队 | MCP v2.0 框架 |
4.3 机器学习检测方案对比
方案类型 | 优势 | 劣势 | 适用场景 |
|---|---|---|---|
静态分析 | 快速高效,能够检测已知恶意软件特征 | 只能检测已知特征,无法检测未知恶意软件 | 大规模软件扫描,快速检测 |
动态分析 | 能够检测未知恶意软件,适应性强 | 性能开销大,实现复杂 | 高安全要求系统 |
行为分析 | 能够检测未知恶意软件的行为模式,适应性强 | 误报率较高,需要大量训练数据 | 实时监测系统,云环境 |
MCP 动态工具行为分析 | 专门针对 MCP 工具设计,实时分析,自适应学习 | 实现复杂,需要专业团队,训练成本高 | MCP v2.0 框架 |
五、实际工程意义、潜在风险与局限性分析
5.1 实际工程意义
- 提高 MCP 系统的安全性:通过多维度的防护机制,有效检测和防御恶意 Tool 注入,提高 MCP 系统的安全性。
- 保护用户数据和隐私:防止恶意工具窃取用户数据和隐私,保护用户权益。
- 维护 MCP 生态的健康发展:通过严格的工具验证和管理,维护 MCP 生态的健康发展,增强用户信任。
- 满足合规性要求:符合相关法规和标准的要求,如 GDPR、CCPA、ISO 27001 等,降低合规风险。
- 减少安全事件损失:提前检测和防御恶意 Tool 注入,减少安全事件的发生概率和损失。
- 提高安全团队的效率:通过自动化的防护机制,提高安全团队的工作效率,减少手动干预。
5.2 潜在风险
- 误报风险:防护机制可能产生误报,影响正常工具的使用,降低用户体验。
- 性能开销:防护机制可能带来一定的性能开销,影响 MCP 系统的整体性能。
- 复杂性增加:防护系统的引入增加了 MCP 系统的复杂性,提高了开发和维护成本。
- 绕过风险:攻击者可能会找到防护机制的漏洞,绕过防护,注入恶意工具。
- 供应链风险:防护系统本身的供应链可能存在风险,攻击者可能通过供应链攻击防护系统。
- 适应性风险:防护机制可能无法及时适应新的攻击技术和手段,导致防护失效。
5.3 局限性
- 无法检测所有恶意工具:防护机制无法检测所有类型的恶意工具,特别是新出现的、未知的恶意工具。
- 依赖于高质量的训练数据:机器学习模型的准确性依赖于高质量的训练数据,获取这些数据可能比较困难。
- 实现复杂,需要专业团队:防护系统的实现复杂,需要专业的安全团队进行设计、开发和维护。
- 部署成本较高:防护系统的部署和维护成本较高,可能不适合所有规模的 MCP 系统。
- 可能影响用户体验:严格的防护机制可能会影响用户体验,如增加工具调用的延迟、需要额外的验证步骤等。
- 无法完全替代人工审查:防护系统无法完全替代人工审查,特别是对于关键工具和系统。
5.4 风险缓解策略
风险类型 | 缓解策略 |
|---|---|
误报风险 | 1. 优化机器学习模型,减少误报2. 实现误报反馈机制,持续改进模型3. 提供误报排除功能,允许管理员手动调整4. 结合多种检测方法,提高检测的准确性 |
性能开销 | 1. 优化防护机制,减少性能影响2. 采用异步处理,降低对主流程的影响3. 实现可配置的防护级别,允许按需调整4. 对高频操作进行优化,减少性能开销 |
复杂性增加 | 1. 采用模块化设计,降低系统复杂性2. 提供清晰的文档和 API,便于使用和维护3. 实现自动化部署和配置,减少手动操作4. 建立完善的监控和告警机制,便于问题定位和解决 |
绕过风险 | 1. 定期进行安全评估和渗透测试,发现防护机制的漏洞2. 持续更新防护机制,适应新的攻击技术和手段3. 结合多种防护方法,提高防护的全面性4. 建立威胁情报共享机制,及时获取最新的攻击信息 |
供应链风险 | 1. 对防护系统本身进行严格的安全审查和测试2. 建立防护系统的供应链安全管理机制3. 采用开源组件时,进行严格的安全审查4. 定期更新防护系统的组件,修复已知漏洞 |
适应性风险 | 1. 建立威胁情报收集和分析机制,及时了解新的攻击技术和手段2. 实现自适应学习机制,不断更新防护模型和规则3. 定期进行安全演练,测试防护机制的有效性4. 与安全社区保持密切联系,获取最新的安全信息 |
六、未来趋势展望与个人前瞻性预测
6.1 技术发展趋势
- AI 驱动的防护机制:利用人工智能和机器学习技术,实现更加智能的防护机制,包括自动检测、自动响应、自动学习等。
- 实时防护与响应:实现对 MCP 恶意 Tool 注入的实时防护和响应,在攻击发生时能够及时检测和拦截。
- 分布式防护体系:建立分布式的防护体系,在 MCP 系统的多个层面和组件中部署防护机制,实现全方位的防护。
- 零信任架构集成:将 MCP 恶意 Tool 注入防护机制与零信任架构集成,实现更加严格的访问控制和验证。
- 区块链技术应用:利用区块链技术,建立不可篡改的 MCP 工具供应链记录,提高供应链的透明度和安全性。
- 隐私保护增强:在防护过程中,增强对用户隐私的保护,确保防护机制不会侵犯用户隐私。
6.2 应用场景扩展
- 跨组织防护:支持跨组织的 MCP 恶意 Tool 注入防护,实现防护机制的共享和协同。
- 边缘计算场景:为边缘计算场景下的 MCP 系统提供轻量级的恶意 Tool 注入防护机制。
- IoT 设备防护:为 IoT 设备上的 MCP 系统提供专门的恶意 Tool 注入防护机制,适应 IoT 设备的资源限制。
- 生成式 AI 防护:针对生成式 AI 与 MCP 集成的场景,提供专门的恶意 Tool 注入防护机制,防止攻击者通过生成式 AI 诱导用户调用恶意工具。
6.3 标准与生态发展
- MCP 安全标准制定:制定统一的 MCP 安全标准,包括恶意 Tool 注入防护的标准和最佳实践。
- 防护机制互操作性:提高不同 MCP 恶意 Tool 注入防护机制之间的互操作性,便于集成和使用。
- 开源防护项目发展:推动开源 MCP 恶意 Tool 注入防护项目的发展,降低防护机制的使用门槛。
- 行业协作与共享:促进不同行业之间的 MCP 恶意 Tool 注入防护经验和技术共享,共同应对安全挑战。
- 认证与评估体系:建立 MCP 恶意 Tool 注入防护机制的认证与评估体系,确保防护机制的有效性和安全性。
6.4 个人前瞻性预测
- 到 2027 年:60% 的 MCP 系统将采用专门的恶意 Tool 注入防护机制,结合 AI 技术实现智能防护。
- 到 2028 年:MCP 工具供应链攻击防护机制将成为 MCP 安全体系的标配,确保工具的来源和完整性。
- 到 2029 年:动态工具行为分析引擎将能够实时检测和响应 90% 以上的已知恶意工具行为。
- 到 2030 年:MCP 工具签名验证体系将成为 MCP 生态的基础设施,确保所有工具都经过验证。
- 未来 5 年:MCP 恶意 Tool 注入防护机制将从被动防御向主动防御转变,能够预测和防止新型攻击。
- 未来 5 年:MCP 安全生态将逐渐成熟,形成完整的恶意 Tool 注入防护产业链,包括防护工具、服务、标准和认证等。
参考链接:
本文参与 腾讯云自媒体同步曝光计划,分享自作者个人站点/博客。
原始发表:2026-01-10,如有侵权请联系 cloudcommunity@tencent.com 删除
评论
登录后参与评论
推荐阅读
目录


